Power consumption attack method and system for DES algorithm L register flipping
A power consumption attack and register technology, which is applied in encryption devices with shift registers/memory, transmission systems, digital transmission systems, etc., can solve the problems of low accuracy of DES hardware module security evaluation, low signal-to-noise ratio, and Low-level problems, to improve the accuracy of security evaluation, enhance the effect, and improve the effect of SNR
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
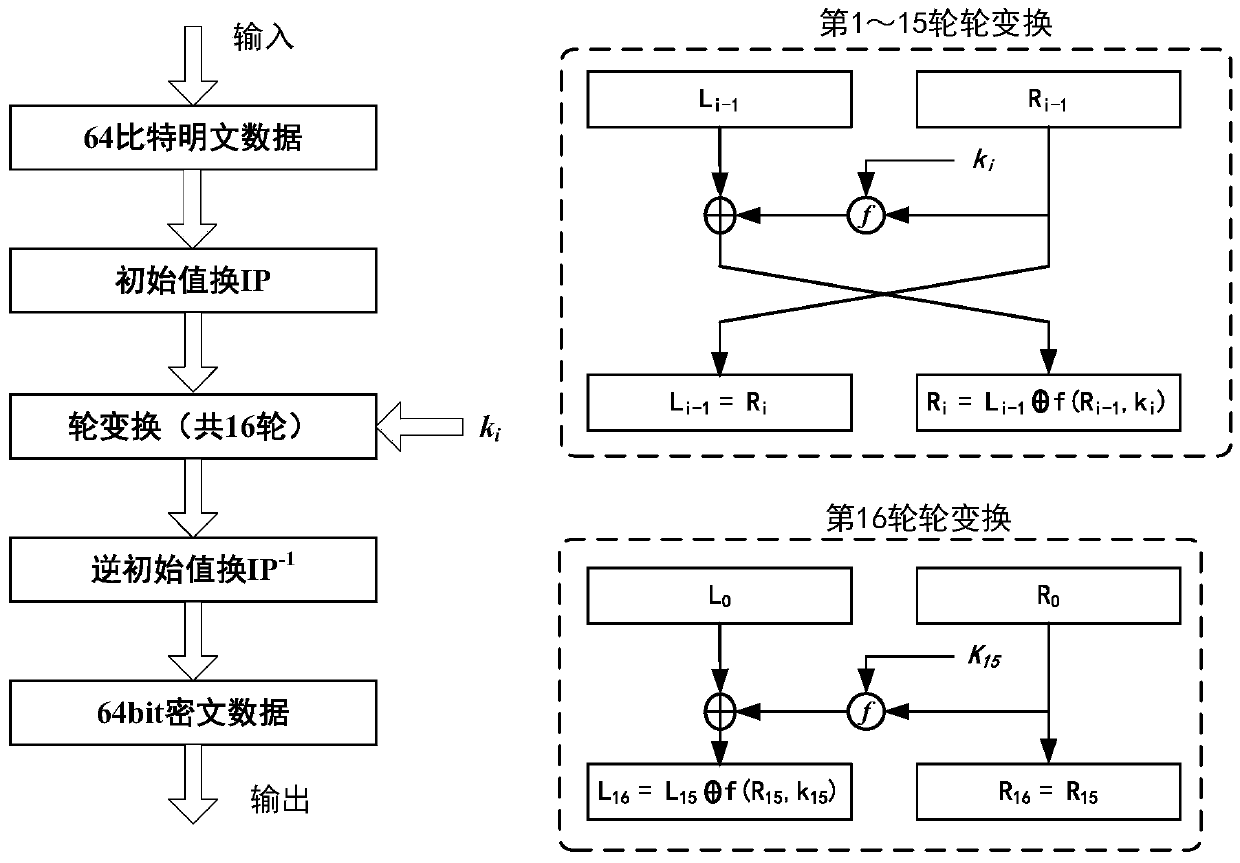
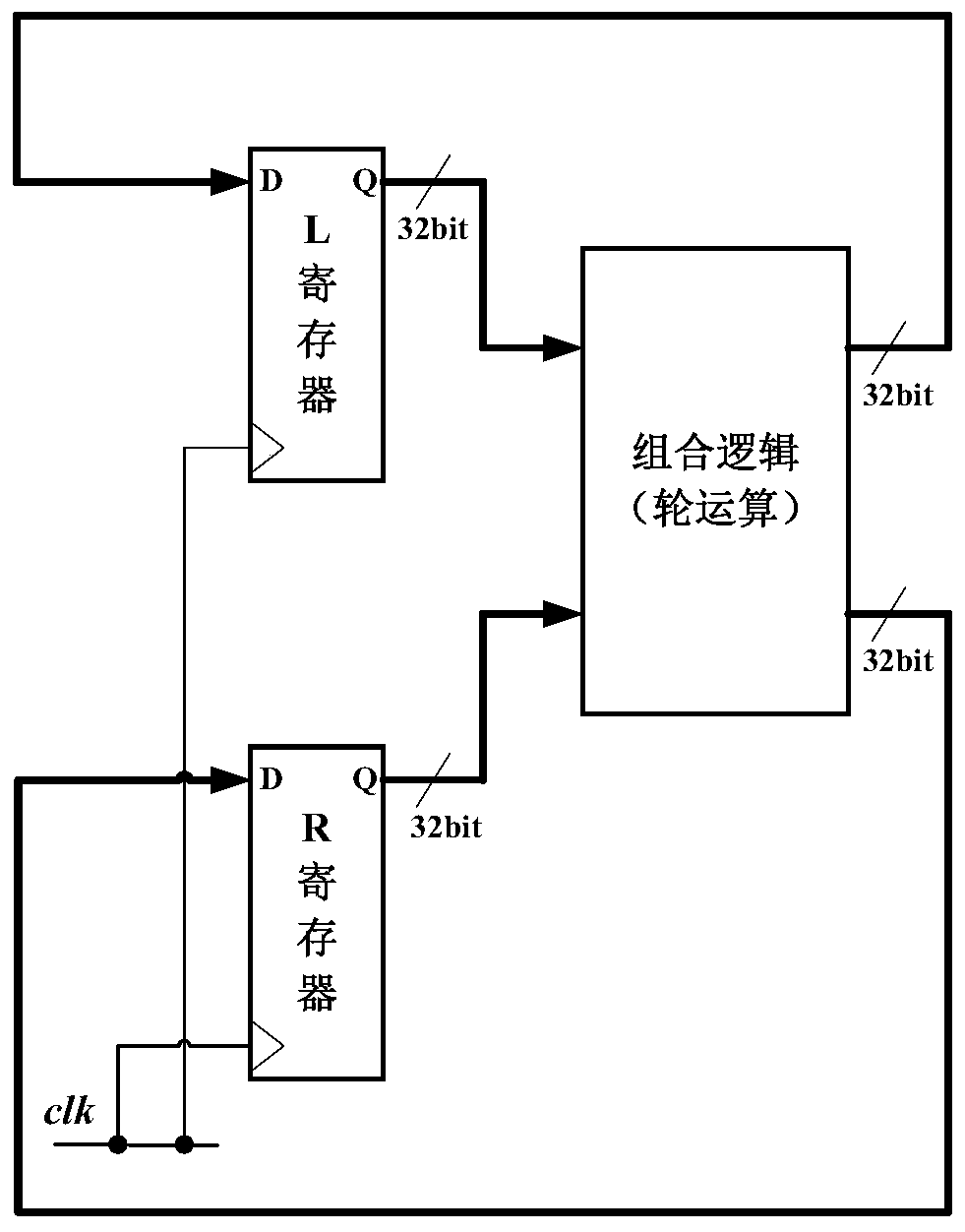
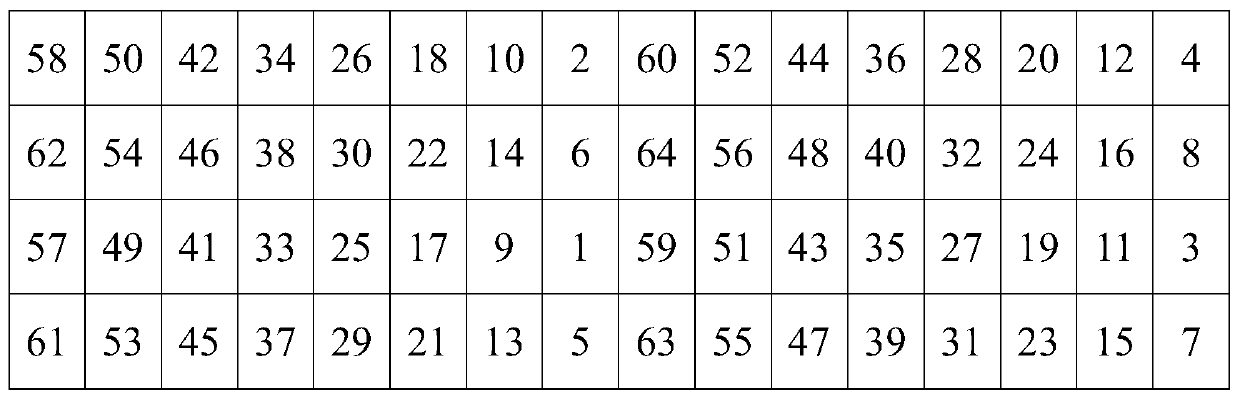
[0044] see figure 1 As shown, the embodiment of the present invention provides a power consumption attack method for DES algorithm L register flipping, including the following steps:
[0045] Use RNG (Random Numeral Generator, Random Number Generator) to generate multiple 32-bit random numbers R, and generate corresponding plaintext according to each random number R. The plaintext satisfies the requirements of the DES algorithm. When the key is fixed, enter the plaintext, the first round The output of an L register is equal to its input. Usually, RNG generates a pseudo-random number or a sequence value calculated by a complex method, so a different seed value is required for each operation. Different seed values result in different sequence values. So it's a true random number
[0046]On the premise of the fixed key of the DES algorithm,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com