Network intrusion detection method based on machine learning
A network intrusion detection and machine learning technology, applied in machine learning, instruments, computer components, etc., can solve the problems of immature accuracy and detection speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] In order to make the present invention more obvious and comprehensible, preferred embodiments are described in detail below with reference to the accompanying drawings.
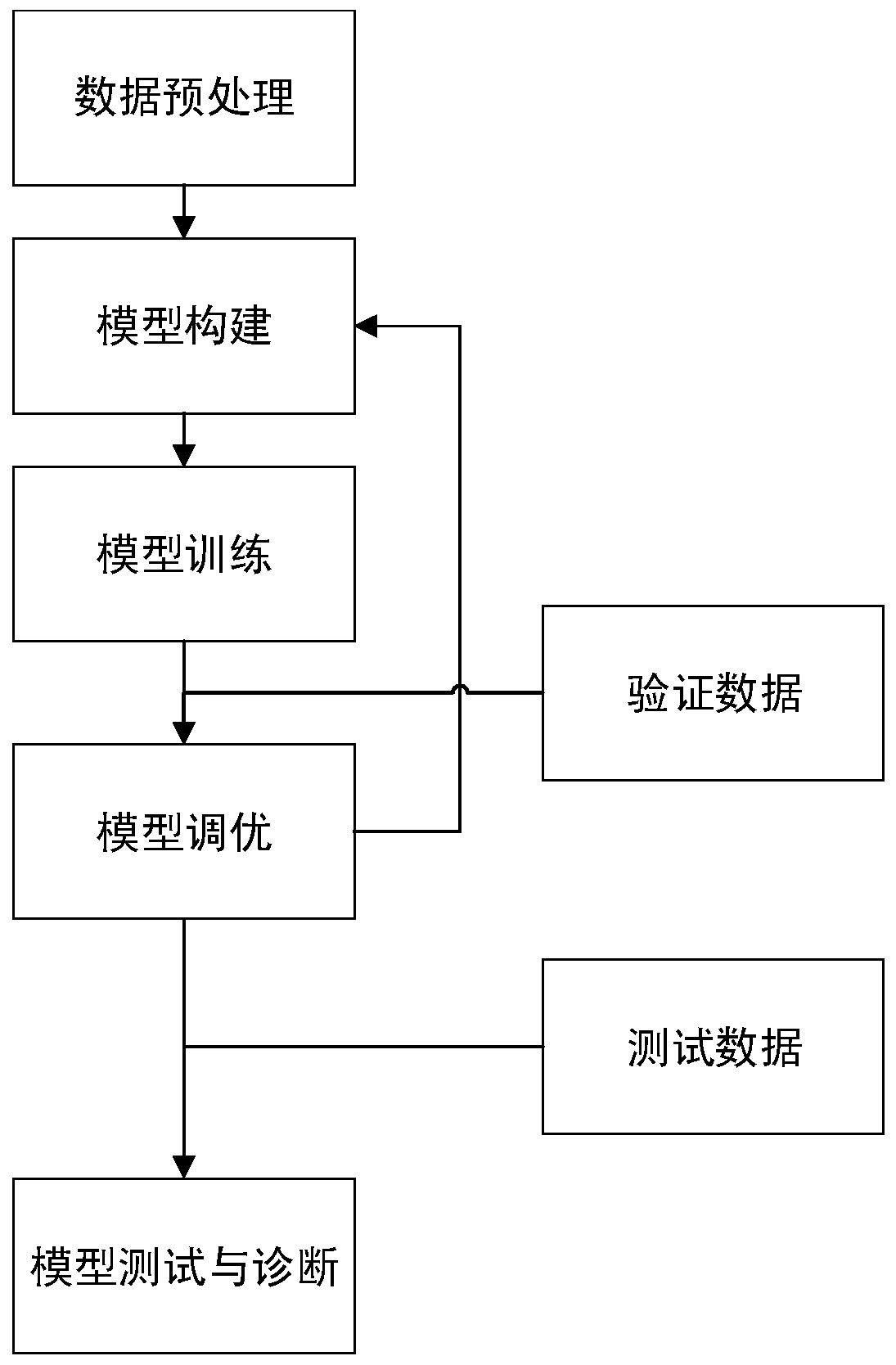
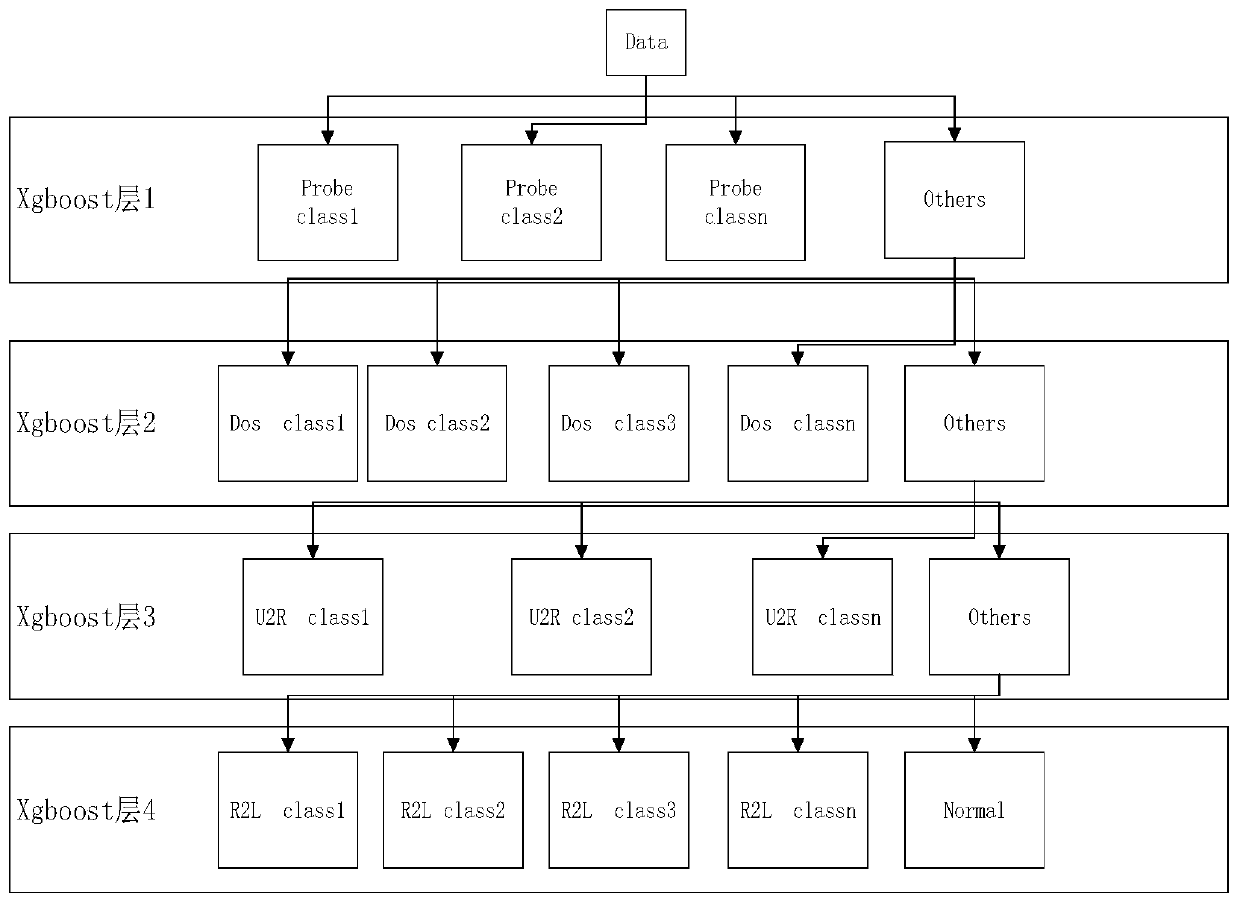
[0067] like figure 1 As shown, the present invention provides a network intrusion detection method based on machine learning, which specifically includes the following steps:
[0068] 1. Data preprocessing.
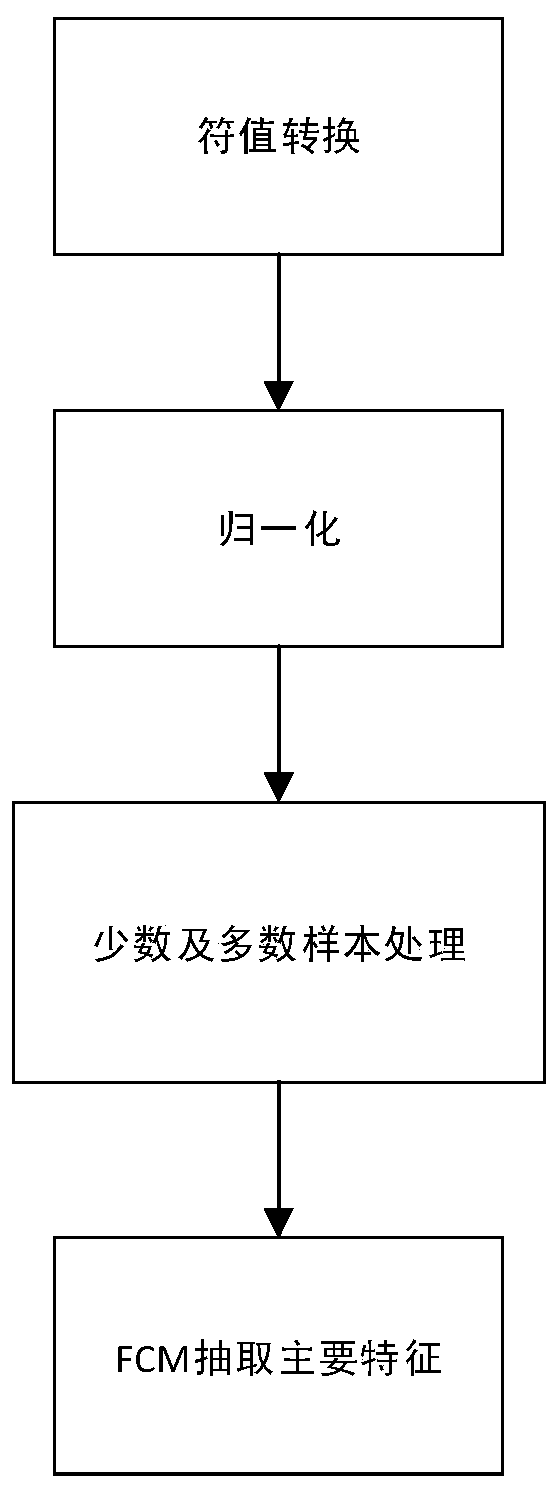
[0069] Take 20% of the KDD99 dataset as the training set. Random sampling Since there are various types of data in the original data, it is necessary to perform symbol-value conversion and normalization of the data to change the features into the range of 0 to 1; due to too many redundant features, it has an impact on the final modeling , also affects the training speed; because the number of samples of some types is too small, it will bring great difficulties to the classification and recognition, so a small number of samples should be amplified.
[0070] The process of data preprocessing is a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com