Lawful interception security
A lawful interception and randomness technology, applied in the security field, which can solve the problems of high national security risk and service suspension of cloud service providers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
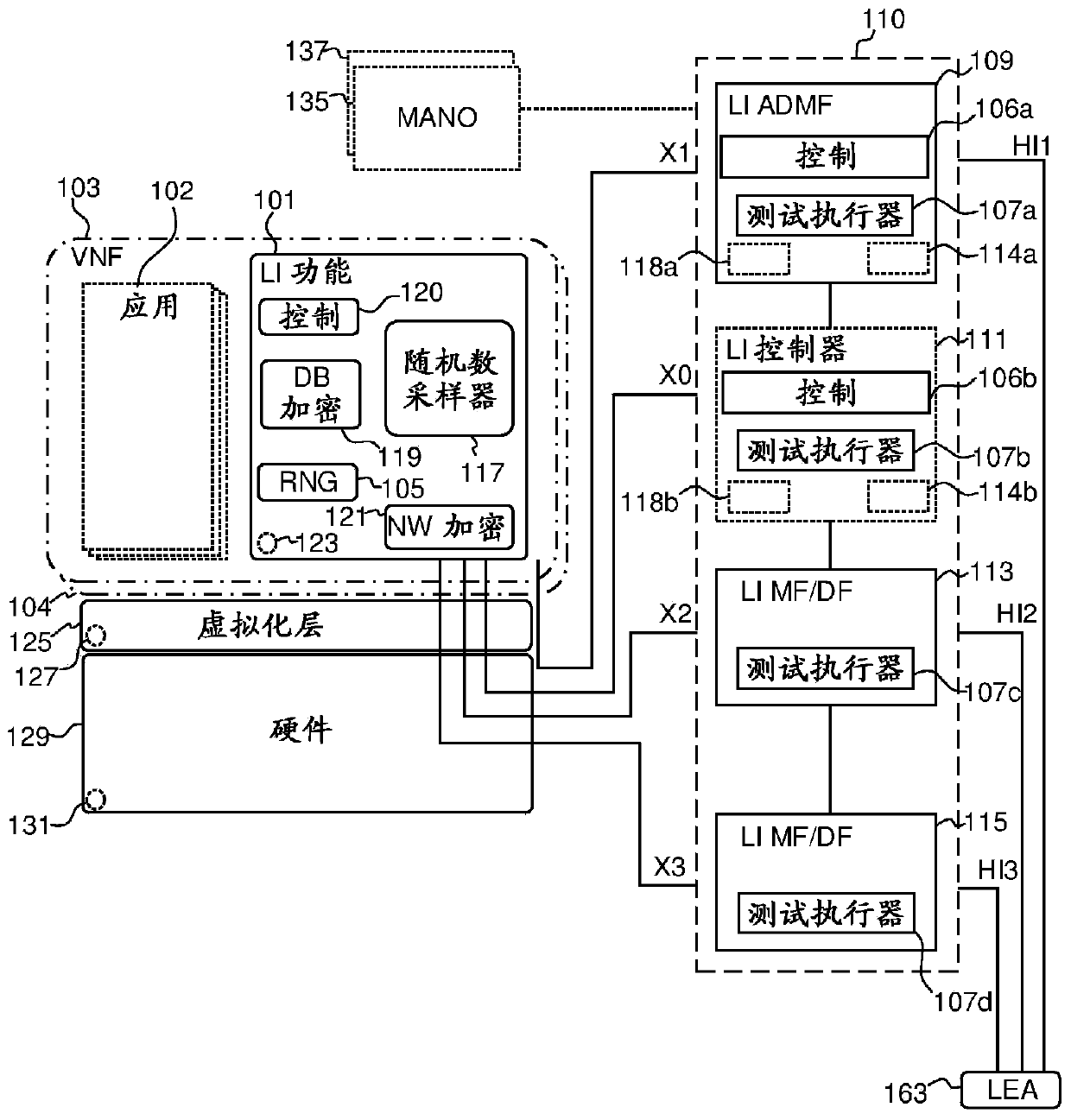
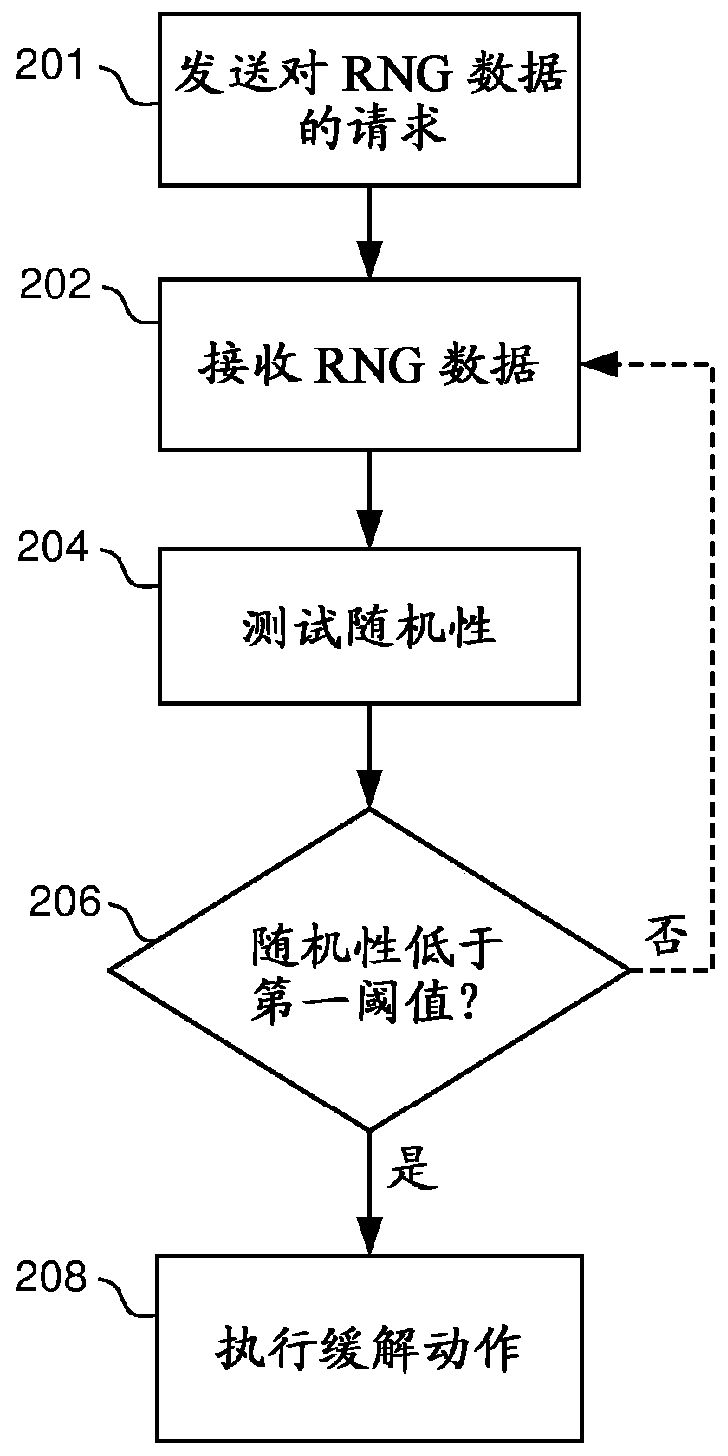
[0034] first go to Figure 1a and Figure 1b, an embodiment of the present disclosure includes a first LI function 110 and a second LI function 101 that operate together to implement LI, as will be described in detail below. LI, as known to those skilled in the art, is a process in which a communication network operator shall provide access to intercepted communication content (CC) and interception-related information of mobile targets and target-related services on behalf of law enforcement agencies (LEA) (IRI) (for example, call forwarding). The LEA provides the network operator with interception requests (eg legal authorization or guarantee).
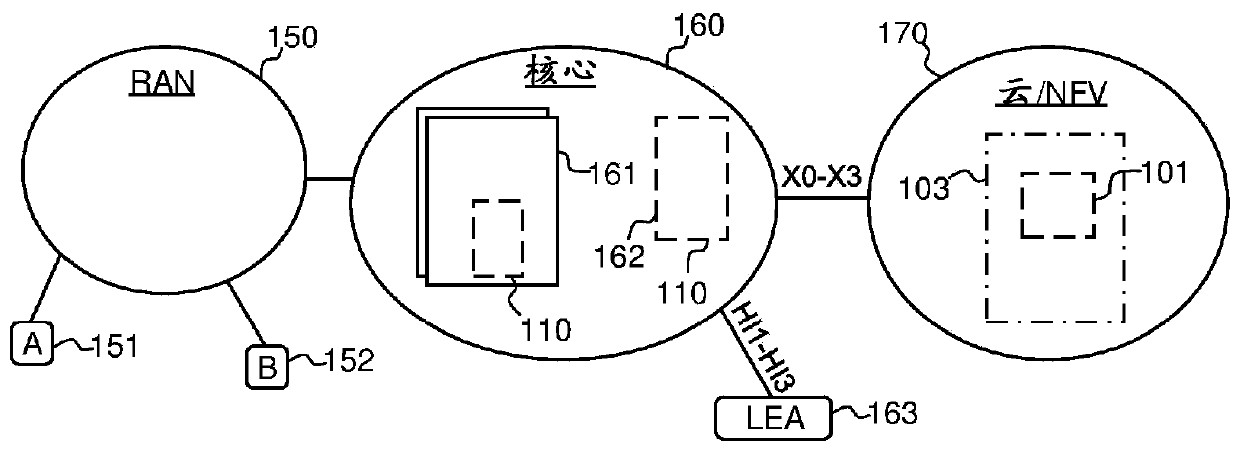
[0035] refer to Figure 1b In the interconnection network schematically exemplified in , a first communication entity A 151 and a second communication entity B 151 communicate via a radio access network (RAN) 150 connected to a core network 160 . RAN 150 and core network 160 may be operated by a communication network operator that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com