Electronic credential security event fusion analysis method
A security event and analysis method technology, applied in the field of fusion analysis of electronic credential security events, can solve the problems of various forms and massive abnormal data analysis, and achieve accurate results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
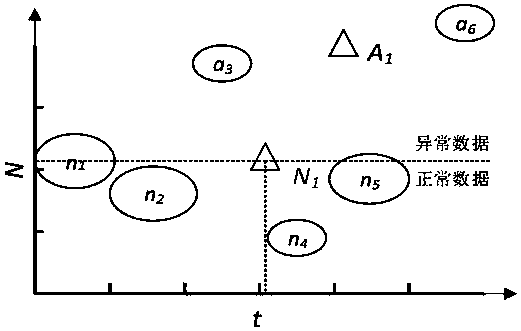
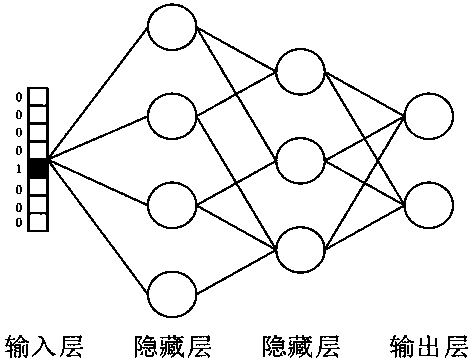
[0033] A fusion analysis method for electronic credential security events, such as figure 1 , 2 Shown include the following steps:
[0034] S101: data collection;
[0035] S102: data preprocessing;
[0036] S103: feature extraction;
[0037] S104: Fusion computing;
[0038] S105: result output;
[0039] The S104 step includes security event research and judgment and association relationship learning. The security event research and judgment uses the Kmeans clustering algorithm to obtain the alert threshold for security incidents of enterprises or users, and the association relationship learning uses the Skip-gram model to train abnormal behavior corresponding codes. After obtaining the word vectors of abnormal behavior, the cosine similarity is used to calculate the similarity between word vectors, and then the correlation similarity between enterprises and users can be obtained.
[0040] Further, in the step S101, the data acquisition uses sensors to collect analog info...
Embodiment 2
[0048]A fusion analysis method for electronic credential security events. On the basis of Embodiment 1, more specifically, abnormal behaviors of electronic credential are diverse and changeable. For example, there are abnormal behaviors such as multiple password attempts in electronic credential password services. There are abnormal behaviors such as repeated reimbursement of services, abnormal behaviors such as over-limit invoices, super-type invoices, issuance of wrong content or parameter invoices, invalid or red-red invoice reimbursement, over-limit reimbursement and other abnormal behaviors in approved services, wrong reimbursement, false invoice reimbursement, and modification Abnormal behaviors such as invoice reimbursement, other platform invoice reimbursement, system counterfeiting, abnormal circulation, etc., enterprise / personal application systems have abnormal behaviors such as issuing a large number of invoices in a short period of time, issuing a large number of la...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com