Dynamic security detection method for Kubernetes cloud native application
A native application and dynamic security technology, applied in the field of cloud native security, can solve the problems of Kubernetes security research lagging behind, no Kubernetes, etc., to reduce application risks and ensure system security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The specific implementation of the invention will be further described below in conjunction with the accompanying drawings.
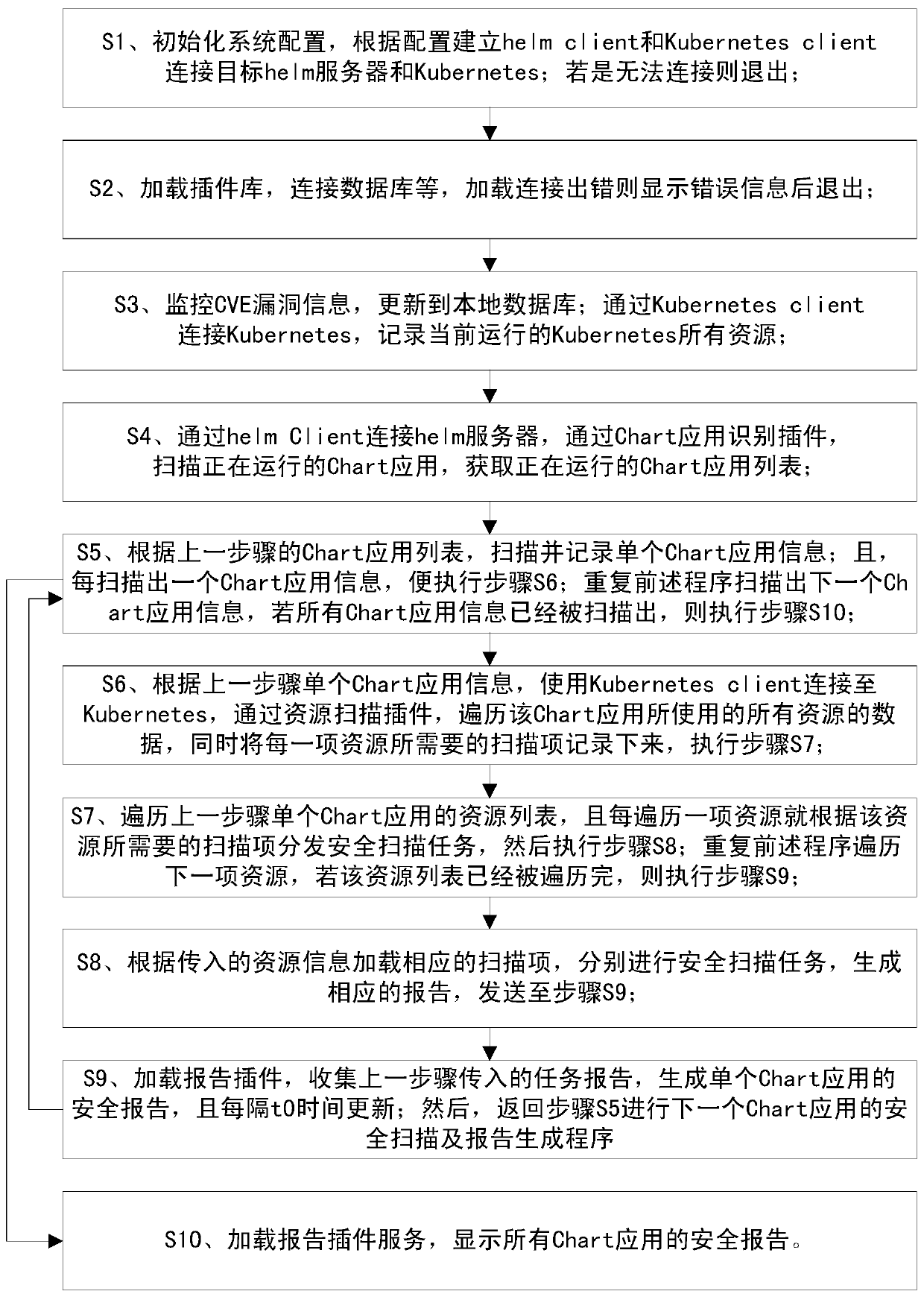
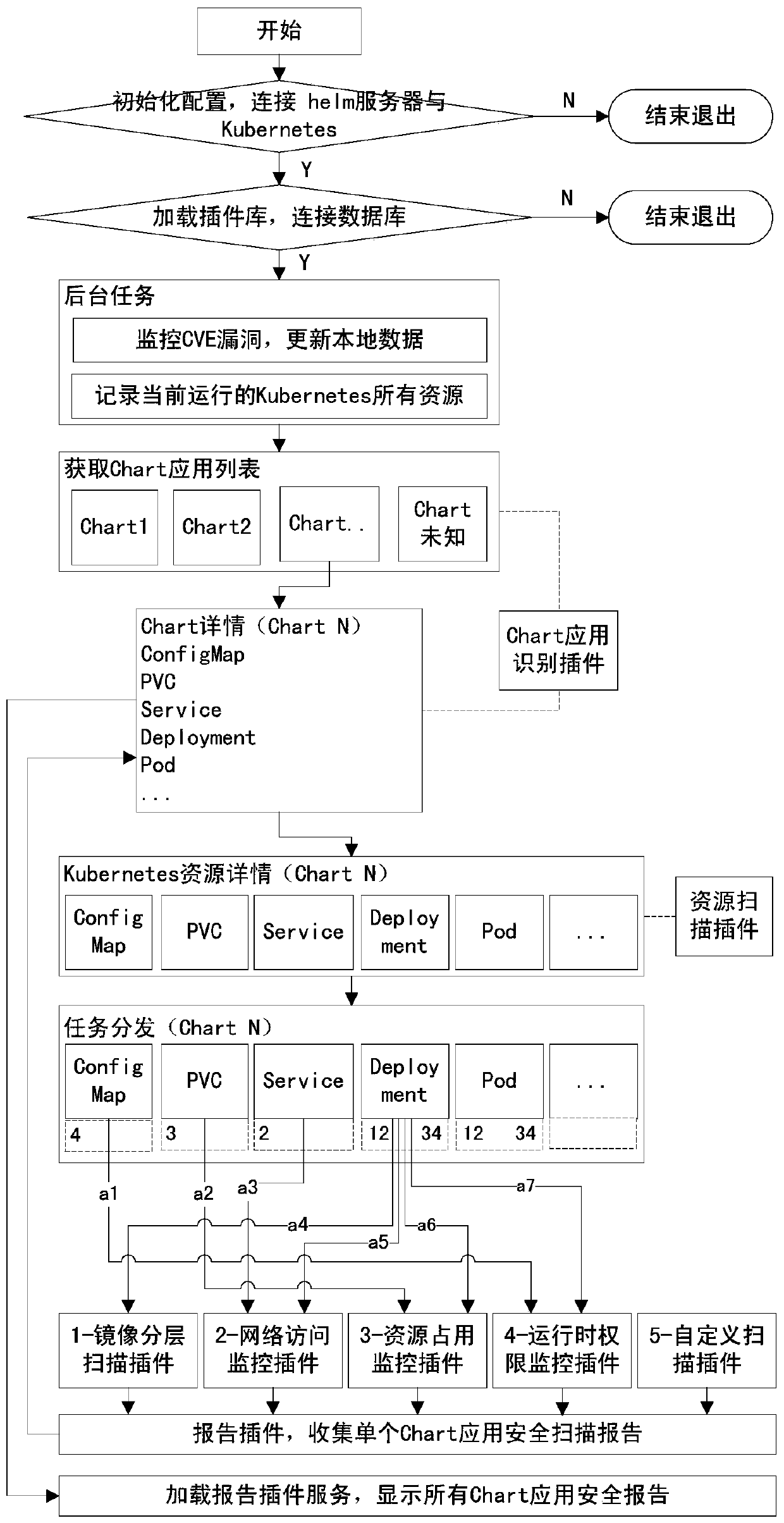
[0035] Such as figure 1 As shown, a dynamic security detection method for Kubernetes cloud-native applications includes the following steps:
[0036] Step S1, initialize the system configuration, establish a helm client and a Kubernetes client according to the configuration to connect to the target helm server and Kubernetes; if the connection fails, exit.
[0037] Step S2, load the plug-in library, and connect to the database; if there is an error in loading and connecting, display an error message and exit.
[0038] Step S3, monitor the CVE vulnerability information, and update the vulnerability information to the local database; connect to Kubernetes through Kubernetesclient, and record all the resources of the currently running Kubernetes.
[0039] Step S4, connect to the helm server through the helm client, scan the running Chart applicati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com