Routing implementation method and device for peer-to-peer network, equipment and medium
A technology of peer-to-peer network and implementation method, which is applied in the direction of data exchange network, digital transmission system, electrical components, etc., which can solve the problems of reduced message sending, increased message sending, and broadcast sending of messages, etc., so as to improve stability and increase the difficulty of doing evil , the effect of reducing the impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
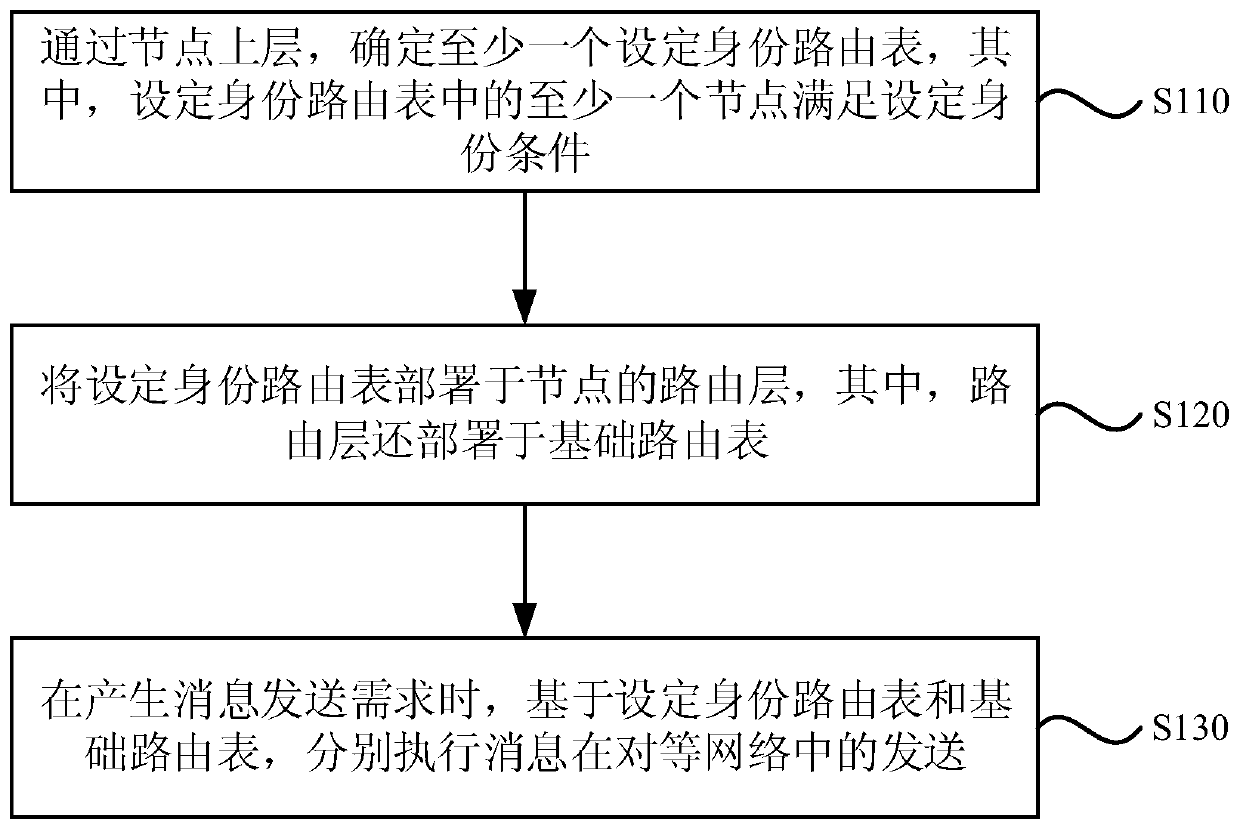
[0026] figure 1 It is a flow chart of a peer-to-peer network routing implementation method provided by Embodiment 1 of the present invention. This embodiment is applicable to the technical solution of message routing by setting multiple routing tables in the peer-to-peer network, and this technical solution is especially applicable In a weakly centralized peer-to-peer network, such as a blockchain network with specific identity nodes. The so-called weak centralization means that each node in the peer-to-peer network has different priority communication requirements in message communication due to differences in functional identities. The method can be executed by a peer-to-peer network routing implementation device, which is implemented by software and / or hardware, and is specifically configured in a computer device carrying a P2P network node.
[0027] Such as figure 1 A peer-to-peer network routing implementation method is shown, which is executed by a peer-to-peer network...
Embodiment 2
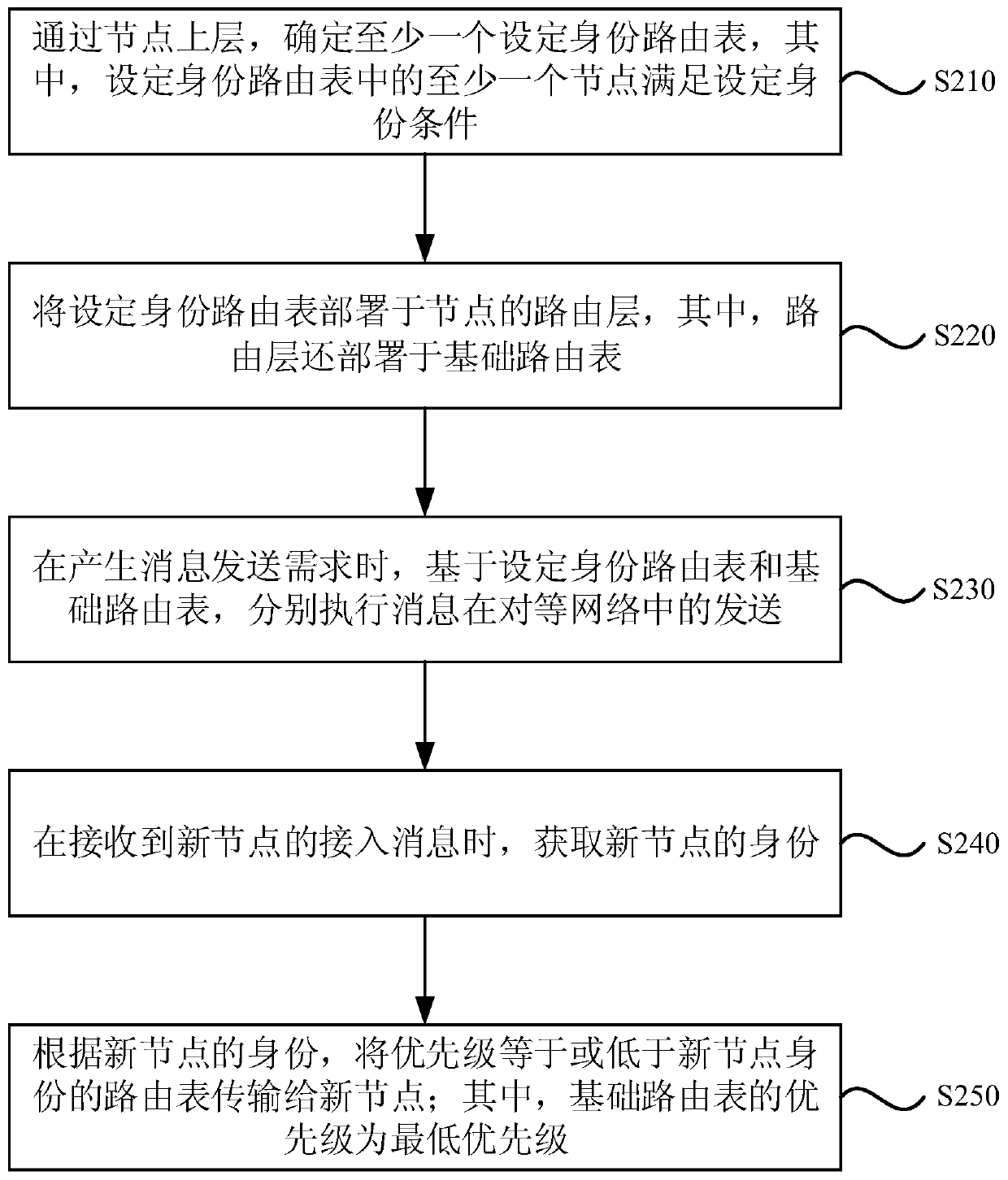
[0058] figure 2 It is a flowchart of a peer-to-peer network routing implementation method in Embodiment 2 of the present invention, and this embodiment of the present invention is embodied on the basis of the technical solutions of the foregoing embodiments.
[0059] Wherein, the routing implementation method of the peer-to-peer network provided in this embodiment also includes:
[0060] Obtain the identity of the new node when receiving the access message of the new node;
[0061] According to the identity of the new node, the routing table whose priority is equal to or lower than the identity of the new node is transmitted to the new node; wherein, the priority of the basic routing table is the lowest priority.
[0062] Such as figure 2 A routing implementation method for a peer-to-peer network is shown, which specifically includes the following operations:
[0063] S210. Determine at least one set-identity routing table through the upper layer of the node, wherein at l...
Embodiment 3
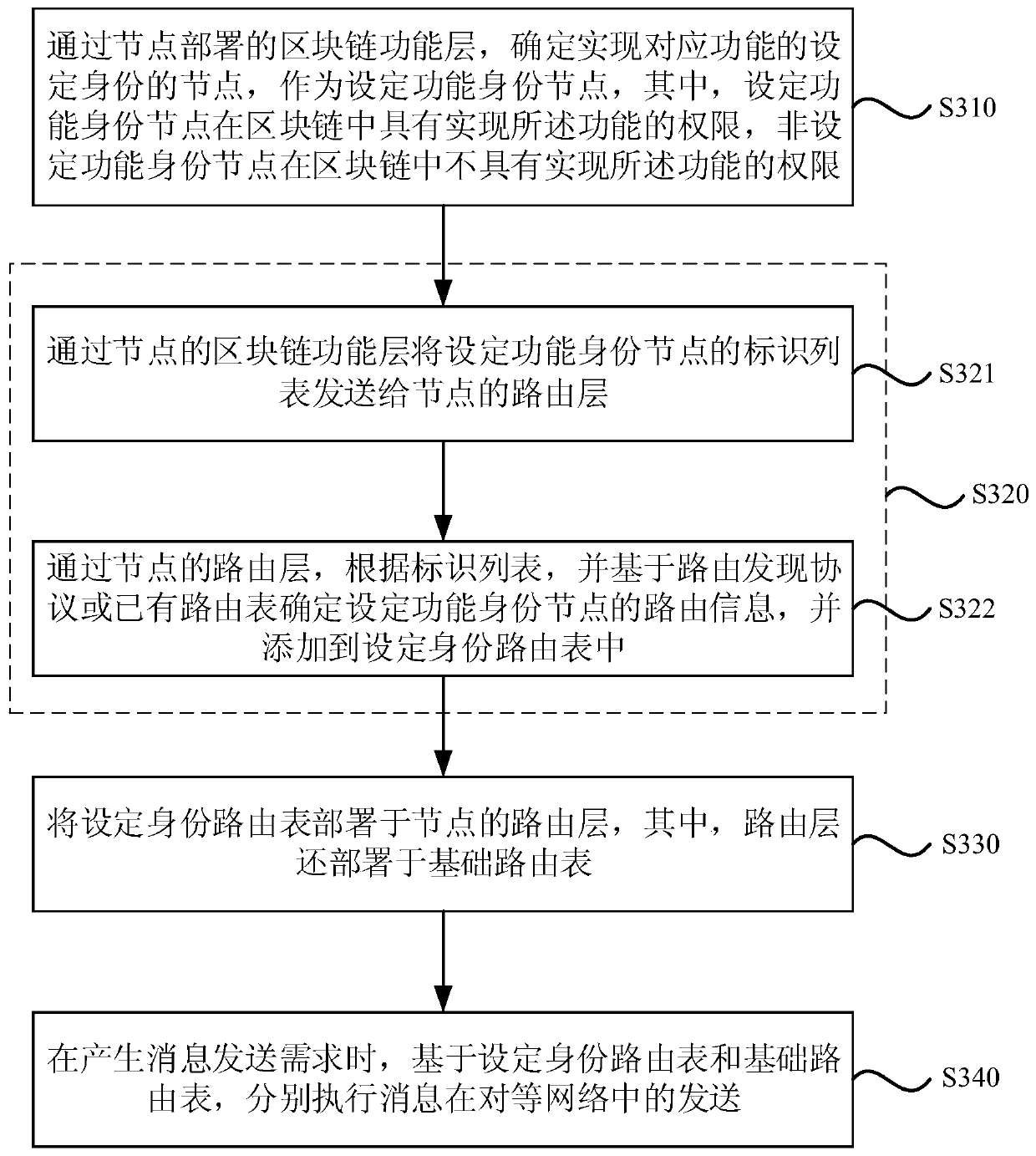
[0078] image 3 It is a flowchart of a peer-to-peer network routing implementation method in Embodiment 3 of the present invention, and this embodiment of the present invention is embodied on the basis of the technical solutions of the foregoing embodiments.
[0079] Among them, the blockchain system data is deployed in each node of the peer-to-peer network, that is, the peer-to-peer network node in this embodiment is a blockchain node, and then, at least one set identity routing table will be determined through the upper layer of the node, specifically for:
[0080] Through the blockchain function layer deployed by the nodes, determine the node that realizes the set identity of the corresponding function, and as the set function identity node, add the routing information of the set function identity node to the set identity routing table, among which, set The functional identity node has the authority to realize the function in the blockchain, and the non-set functional iden...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com