Mobile application security evaluation method based on comment data
A mobile application and security technology, applied in special data processing applications, electronic digital data processing, text database query, etc., can solve the problems of difficult to obtain program code, difficult to analyze and evaluate results, and difficult for users to understand, so as to reduce the burden on users. , the effect of improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] In order to facilitate the understanding of those skilled in the art, the present invention will be further described below with reference to the embodiments and the accompanying drawings, and the contents mentioned in the embodiments are not intended to limit the present invention.
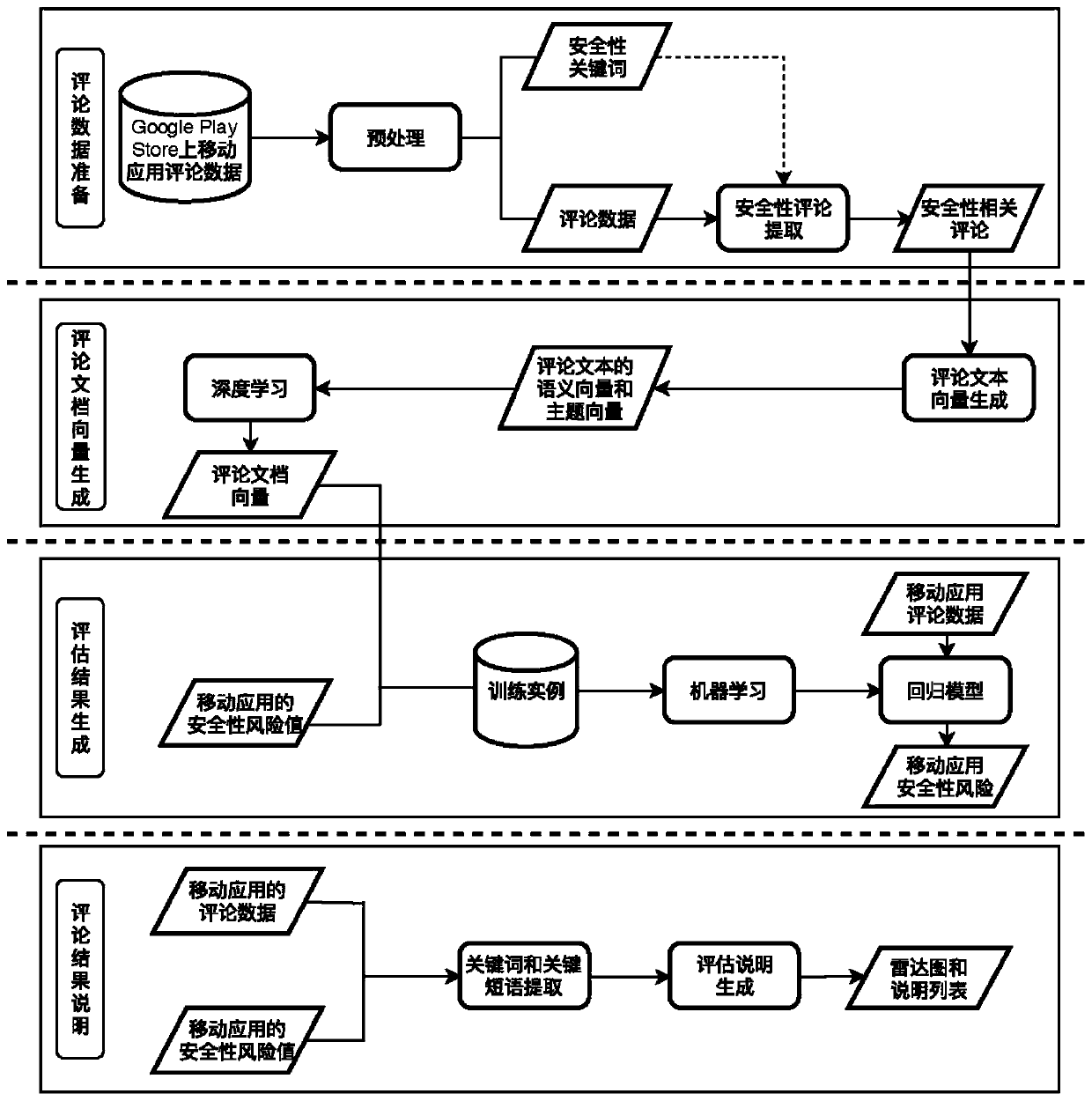
[0033] refer to figure 1 As shown, a method for evaluating mobile application security based on review data of the present invention includes the following steps:
[0034] Step 1) Acquisition of security review data: collect review data of mobile applications, perform preprocessing and keyword extraction on review data, and filter keywords to construct a security keyword database; build security-related comments according to the security keyword database dataset; where,
[0035] 11) Use crawler to crawl the review data of 200 mobile applications from the Google Play application store, including the content of the review and the time of submission of the review. The content of each commen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com