Differential privacy-based data exception detection method
A technology of differential privacy and detection methods, which is applied in other database retrieval, digital data protection, electronic digital data processing, etc., can solve the problems of privacy information leakage, achieve high robustness, strong adaptability, and improve the recall rate Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
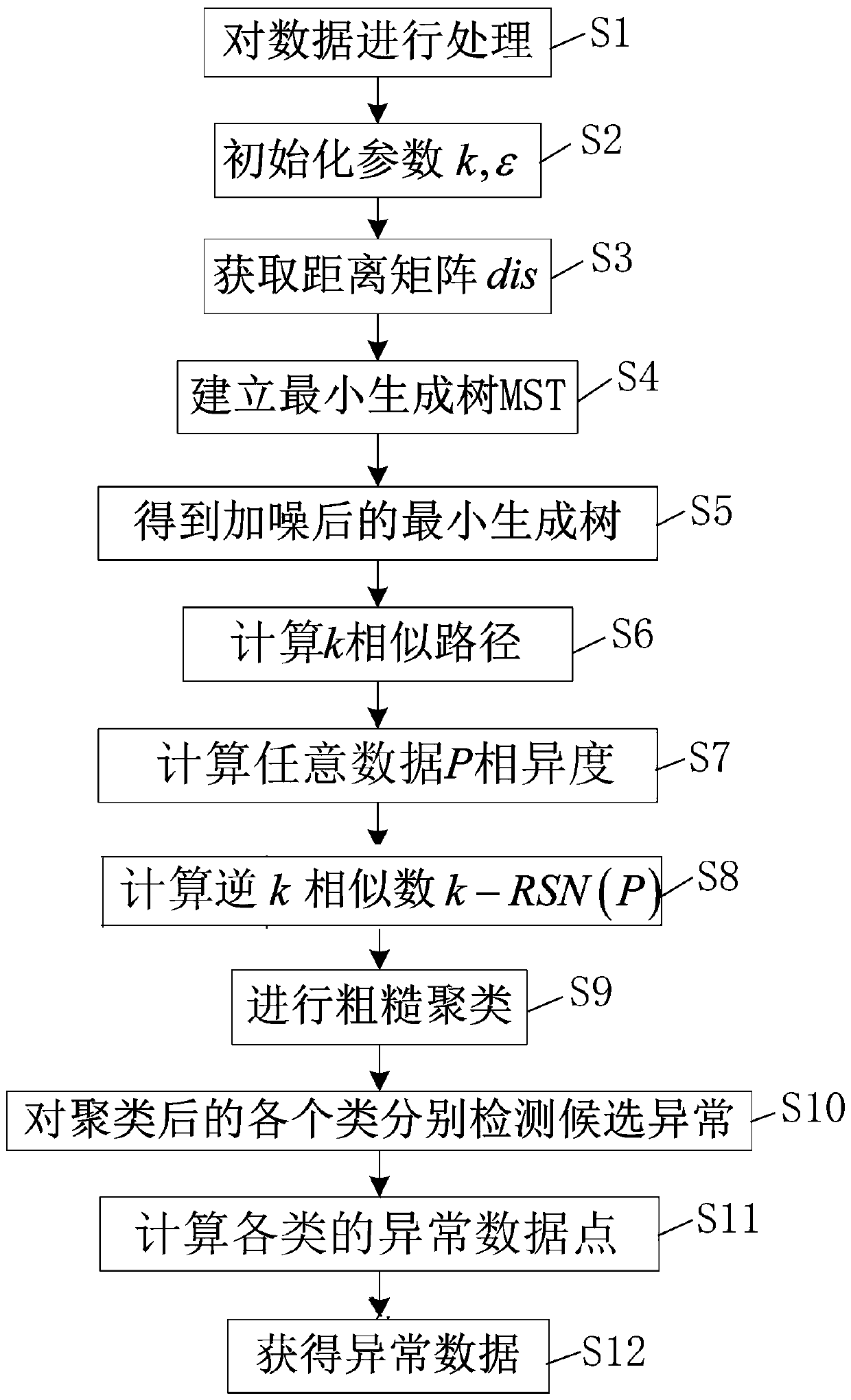
[0055] The content of the present invention will be further elaborated below in conjunction with the accompanying drawings and embodiments, but the present invention is not limited thereto.
[0056] refer to figure 1 , a data anomaly detection method based on differential privacy, comprising the following steps:
[0057] S1 processes the data: the real data set in the UCI machine learning database is processed, the real data has been marked with a category label and some attributes are missing, and the category label of the data is removed in order to verify that the method of the present invention can Abnormal data is effectively detected, and at the same time, data objects with missing attributes are removed.
[0058] S2 Initialization parameters k, ε: Set initialization parameters, where k represents the k nearest similar neighbors of the data object, and ε is the privacy protection coefficient of differential privacy.
[0059] S3 gets the distance matrix: if X i , X j ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com