A device and method for performing saturated addressing load and store operations
A storage operation and addressing technology, applied in the field of processing methods and devices for saturated storage access operations, can solve the problems of large performance loss, large performance loss, user private data theft, etc., and achieve the effect of eliminating software attacks and small performance losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
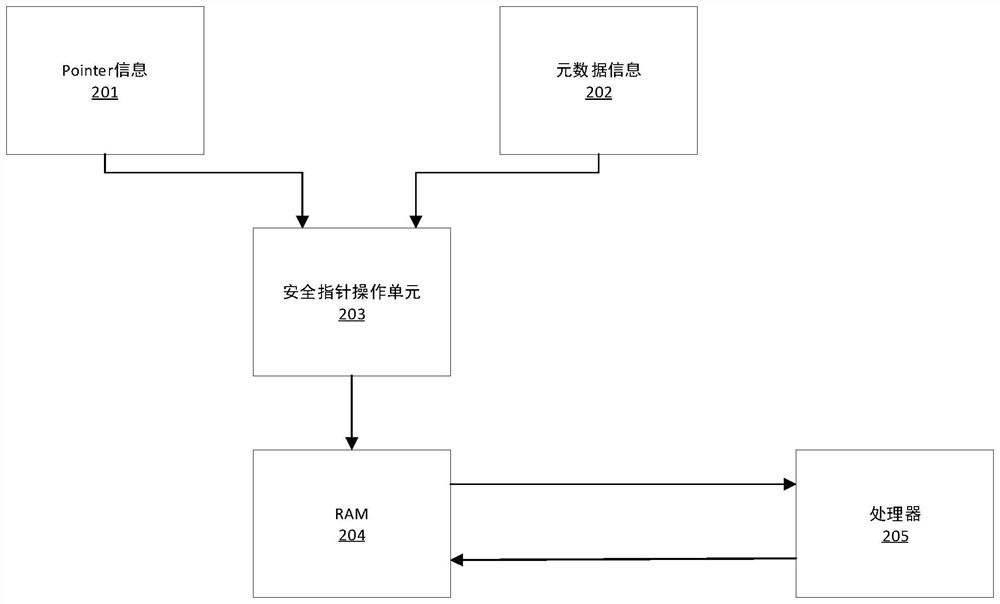
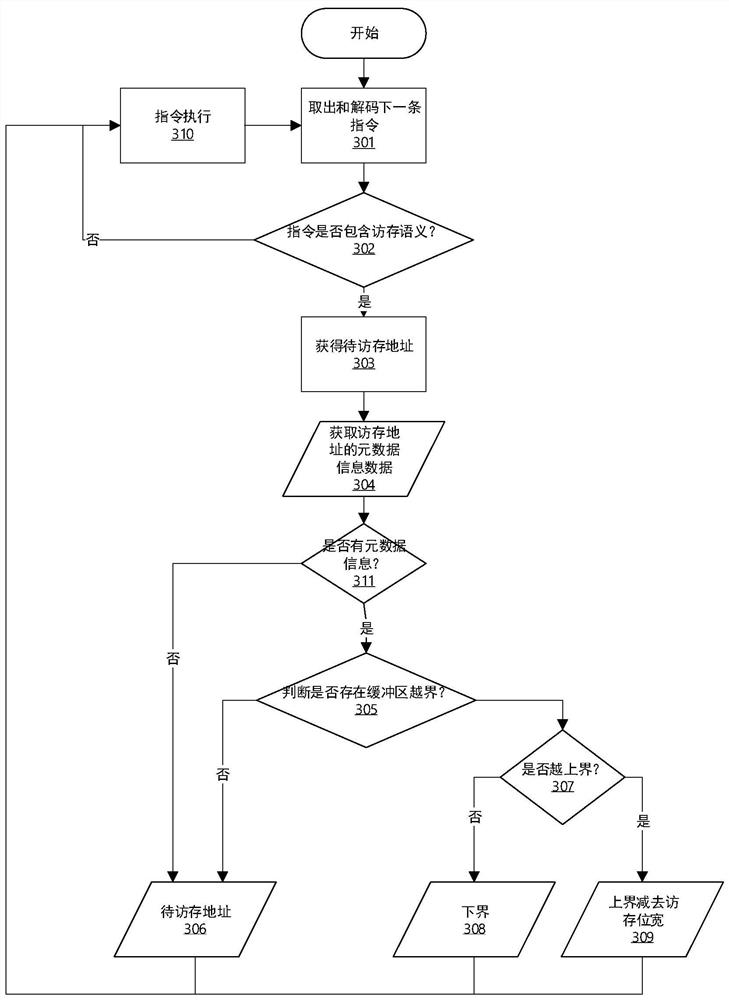
[0044] The present invention will be explained in detail below in conjunction with the accompanying drawings and examples, so as to clearly understand the purpose, technical solutions and advantages of the present invention. It should be noted that the drawings and examples herein are only for explaining the present invention, not for limiting the present invention. The following describes how the present invention works according to buffer limit information through a fat pointer storage format, then provides a hardware operating mode and hardware design prototype, and finally provides a command system based on the present invention.
[0045] At present, the code based on C language is full of buffers, and in C language, whether it is a buffer allocated on the stack, a buffer dynamically allocated on the heap, or a buffer initialized by global variables, the size of all buffers It is defined according to the writer's functional design based on the program, so the buffer size c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com