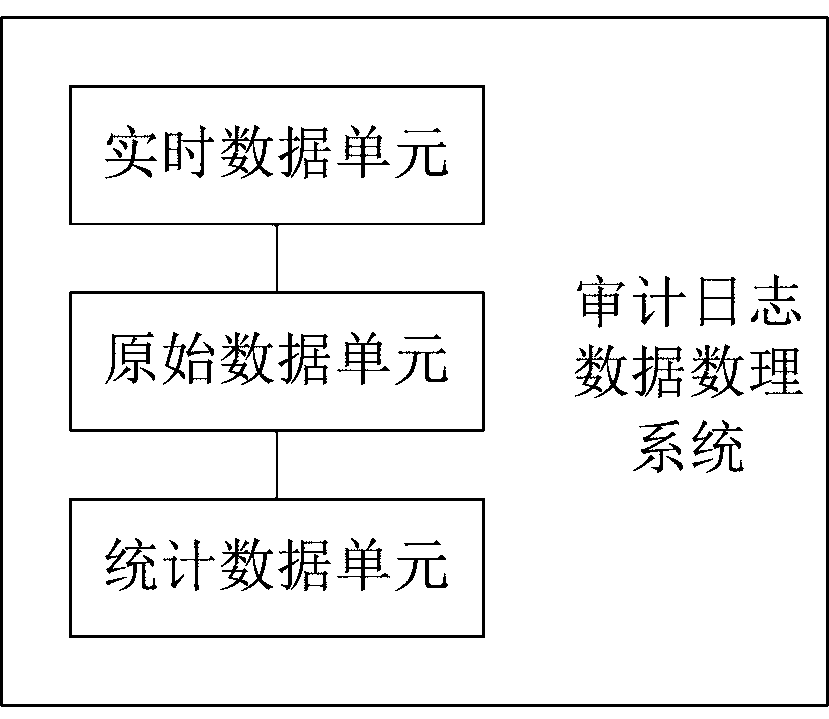
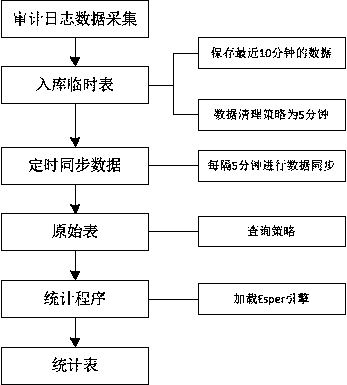
Audit log data processing method and system
A technology of data processing and processing methods, which is applied in the field of network security, can solve problems such as low database query efficiency, achieve the effects of improving data processing efficiency, improving query efficiency, and saving system resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] In order to facilitate understanding of the technical solutions of the embodiments of the present invention, two existing solutions that are often used to improve database query efficiency are listed.
[0043] Option 1, Mongodb replaces temporary tables
[0044] Using Mongodb as a substitute for temporary tables can improve the speed of data insertion and query retrieval, reduce the pressure on the Mysql database, and transfer statistical queries to Mongodb data. After several experiments, the test data shown in the following table are obtained:
[0045]
[0046] It can be seen that after using Mongodb, the writing speed is very fast, and the total number of queries and pagination retrieval speeds are also very fast, basically in line with expectations. However, by observing the disk usage and memory usage, we will find that with the increase of the amount of data stored in the database, the amount of disk space and memory space occupied will increase linearly, whic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com