Quantum key distribution method, device and system
A quantum key distribution system technology, applied in the field of devices and systems, quantum key distribution methods, can solve the problems of high cost of quantum key distribution network, heavy operation and maintenance workload, etc., to reduce network construction and operation and maintenance cost effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
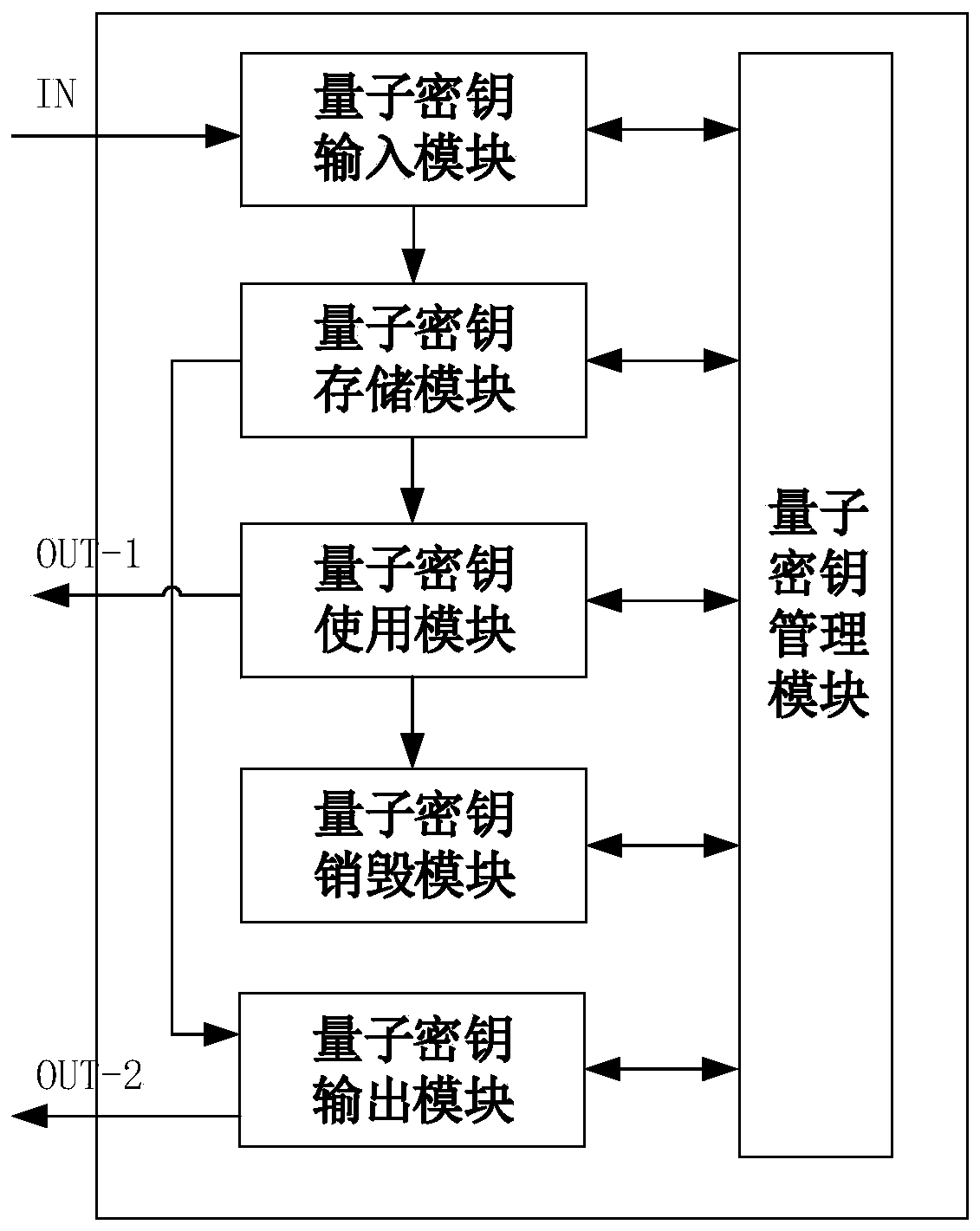
[0062] A quantum key distribution method is provided in an embodiment of the present invention, which specifically includes the following steps:
[0063] (1) Send instructions to each communication-connected first quantum secret key management service terminal, and control each first quantum secret key management service terminal to send the quantum secret key to the corresponding communication-connected second quantum secret key management service terminal, wherein , the first quantum secret key management service terminal and the second quantum secret key management service terminal use the same ID to store the same quantum secret key, so that each first quantum secret key management service terminal or each second quantum secret key management service terminal In the process of communication, obtain the quantum key of the same ID to encrypt and decrypt business data;
[0064] (2) Send a destruction instruction to each communication-connected first quantum key management ser...
Embodiment 2
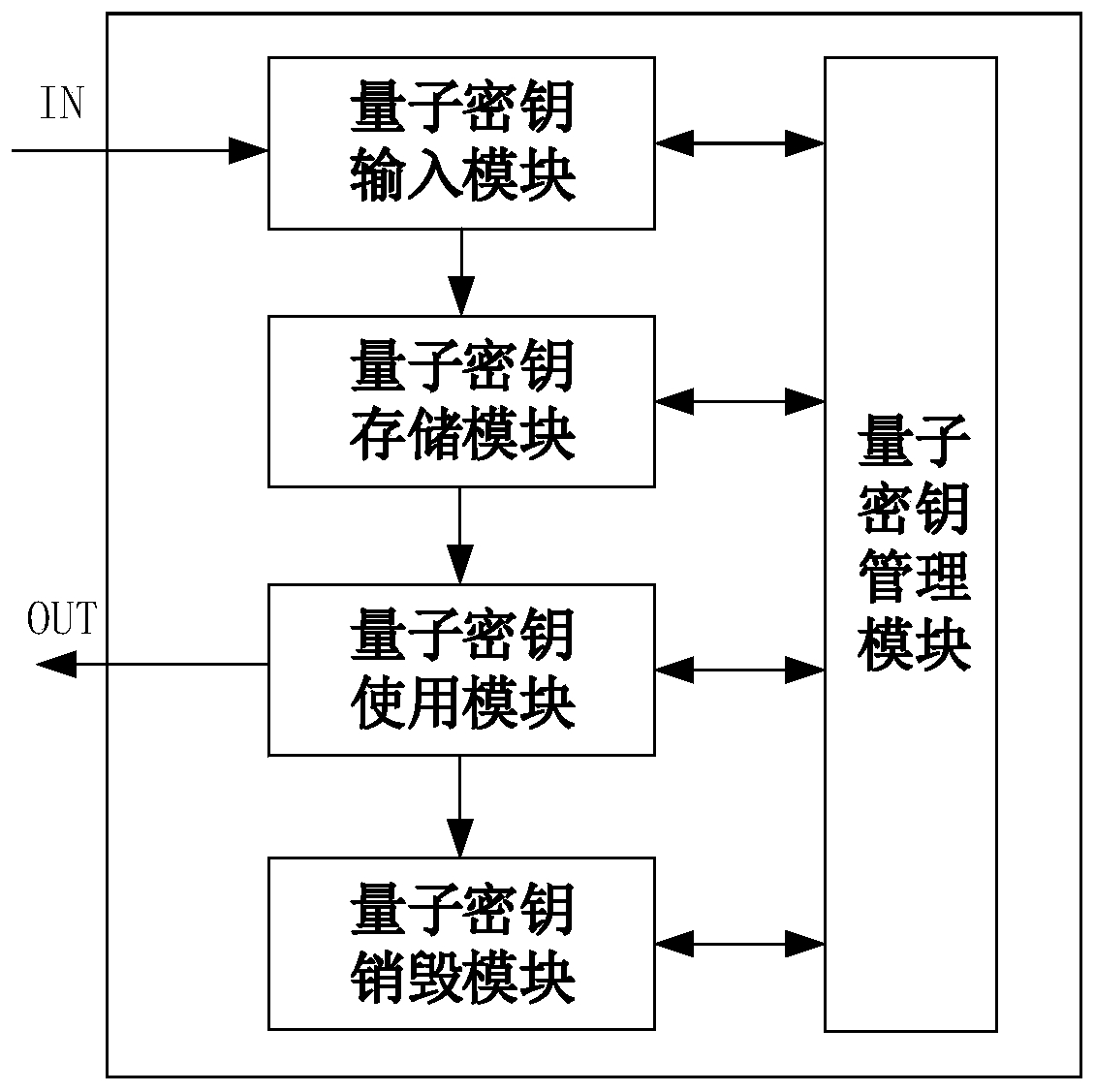
[0071] The difference between the embodiment of the present invention and embodiment 1 is that the method further includes:
[0072] After detecting that a second quantum key management service terminal uses a certain quantum key to encrypt and decrypt business data, it sends a destroy command to the corresponding second quantum key management service terminal to destroy the used quantum key, ensuring One time password.
Embodiment 3
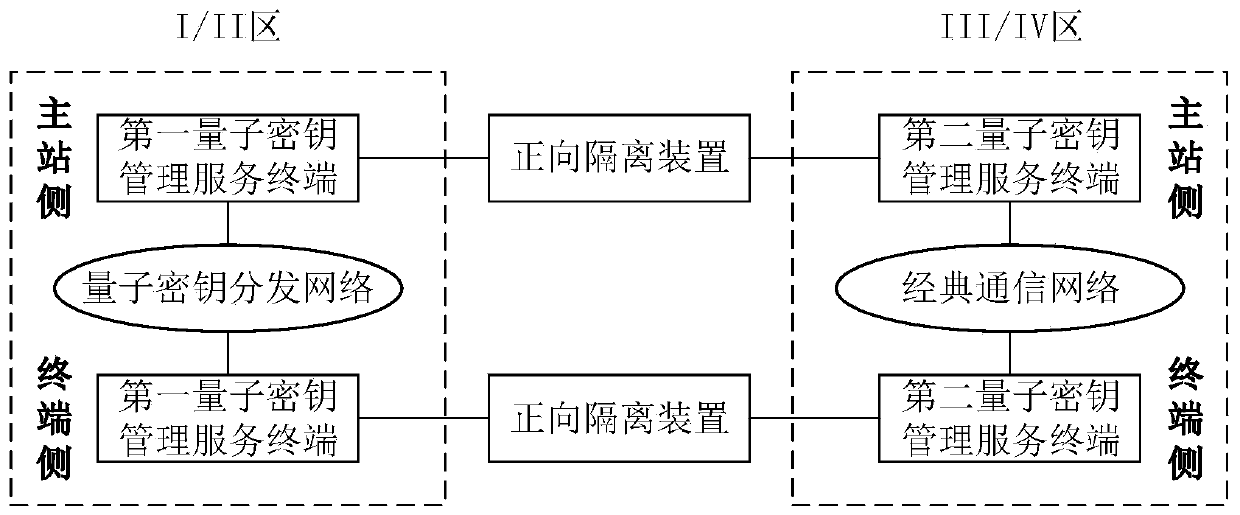
[0074] An embodiment of the present invention provides a method for distributing quantum keys, which is suitable for quantum key distribution suitable for cross-safety areas of power systems, and specifically includes the following steps:
[0075] (1) Obtain the quantum secret key;
[0076] (2) Distribute the obtained quantum secret key to the first quantum secret key management service terminal connected by communication, and the same quantum secret key is stored with the same ID in each first quantum secret key management service terminal, so that each first quantum secret key During the communication process, the secret key management service terminal obtains the quantum secret key of the same ID to encrypt and decrypt the business data, so as to realize the business data encryption inside each area; preferably, each first quantum secret key management service terminal passes through The quantum secret key distribution network is connected in communication, and the quantum ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com