A dual-image active authentication method in fractional tchebichef transform domain
An active authentication and fractional-order technology, which is applied in the fields of information hiding and image security, can solve the problem that it is difficult to further improve the robustness of the algorithm by embedding information, and achieve the effects of ensuring imperceptibility, enhancing embedding strength, and strong robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
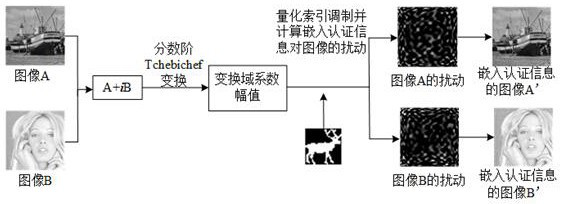
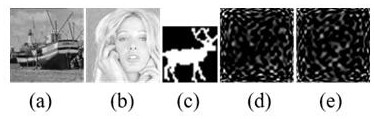
[0091] Take the image of the boat and the image of the woman as the original image, and the image of the deer as the authentication information.
[0092] Such as image 3 As shown, where (a) the boat image after embedding information, (b) the woman image after embedding authentication information, (c) the extracted deer information, (d) the difference between the boat image after hiding information and the original image, (e ) is the difference between the hidden image of the woman and the original image.
[0093] Images of boats and women to be authenticated (attached image 3 (a), 3(b) shown), is through the appended figure 1 The image with the authentication information hidden in the authentication information embedding process obtained, the added authentication information is a binary image deer (as attached image 3 (c)).
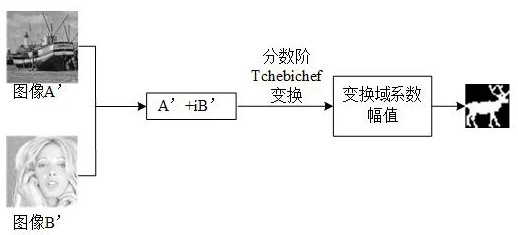
[0094] According to the extraction process of authentication information (as attached figure 2 ), the original embedded authentication informati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com