Database auditing method based on blood relationship
A blood relationship and database technology, applied in the field of database auditing based on blood relationship, can solve the problem of low correct rate and achieve the effect of meeting the needs of use, work efficiency and high correct rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
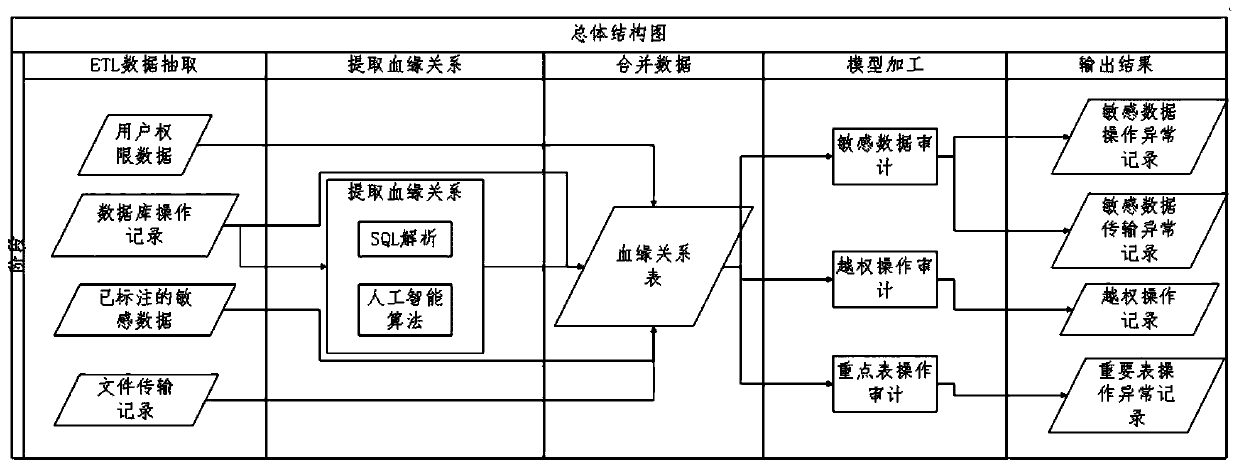
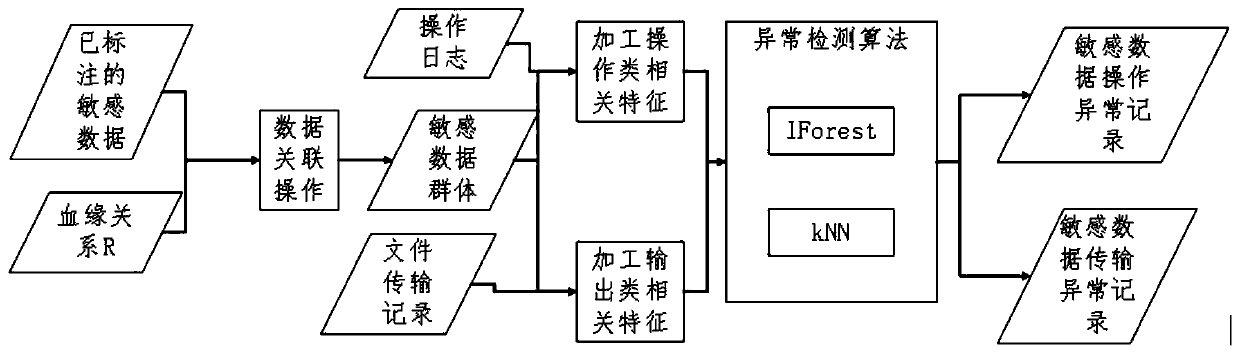
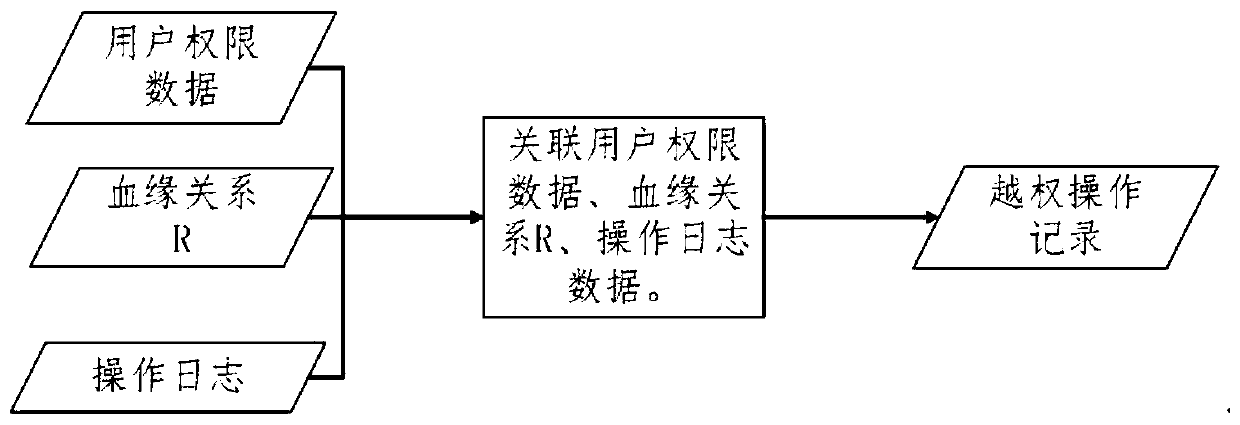
[0024] A database audit method based on consanguinity relationship, the specific steps are as follows:
[0025] Step 1. Find the blood relationship R between the fields in the database. Method 1 is: read the SQL statement in the database operation record, analyze the SQL statement, and find out the blood relationship that reflects the data transmission through the unique rules in the SQL statement , so as to establish a blood relationship table, the second method is: use the kmeans algorithm, the k-means algorithm is a clustering algorithm, the so-called clustering, that is, according to the principle of similarity, divide the data objects with high similarity into the same cluster , to divide data objects with high dissimilarity into different clusters. The biggest difference between clustering and classification is that the clustering process is an unsupervised process, that is, the data objects to be processed do not have any prior knowledge, while the classification process...
Embodiment 2
[0028] A database audit method based on consanguinity relationship, the specific steps are as follows:
[0029] Step 1, extract the create table and insert into two statements with "data transfer" from the SQL statement. Use the sqlparse tool for statement analysis. The sqlparse tool can parse out the part of speech of a word. Parts of speech include: keywords, methods, symbols, etc. The target table name Tt can be located according to the create or insert keyword; the source table name can be located according to the from keyword gather. (Get the table name of a single table or the table name and alias associated with the table); according to the select keyword, you can locate the column name and column alias set (the column name is the original column name, the column alias is the target table column name, and if there is no column alias, the target table The column names are the same as the original column names). Replace the table alias of the column name set with the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com