A multi-party controlled two-way quantum secure direct communication method and system based on cluster state
A secure direct communication, multi-party technology, applied in the field of multi-party controlled two-way quantum secure direct communication, to achieve the effect of high transmission efficiency, guaranteed security, efficient and secure quantum secure direct communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
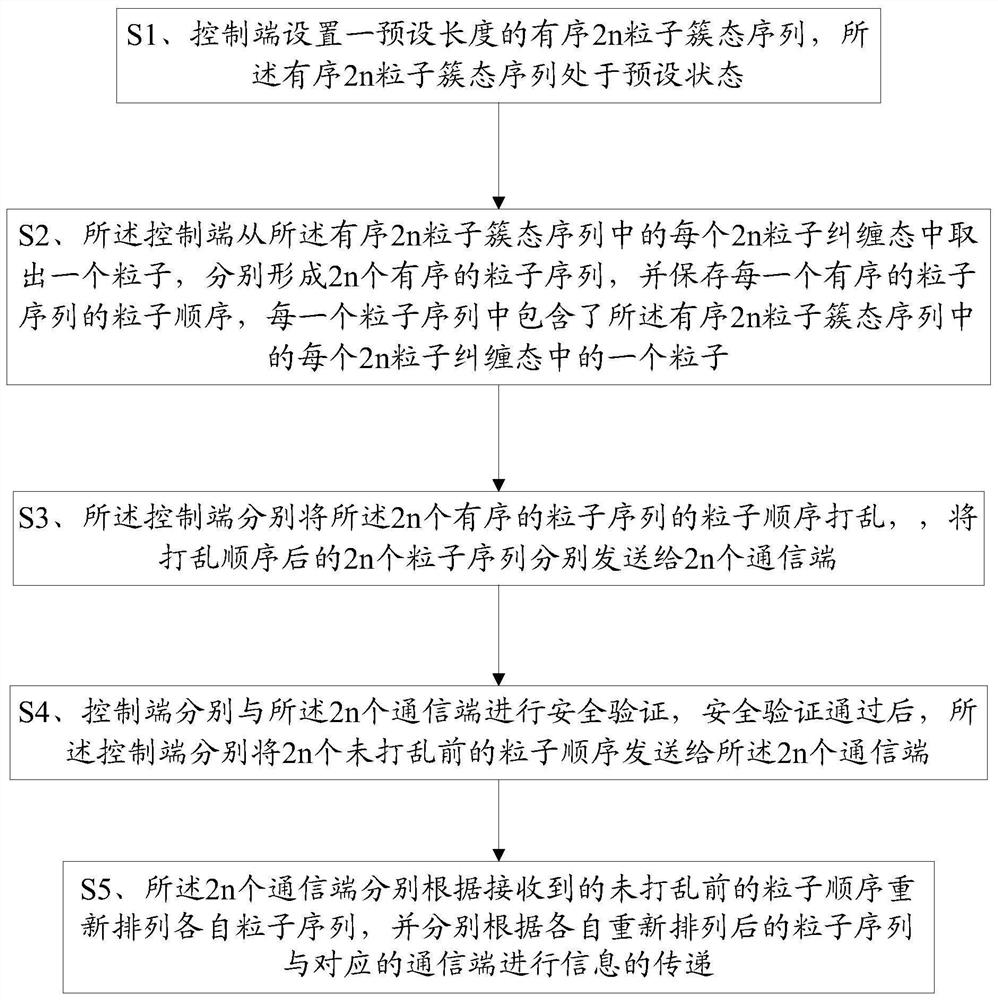
[0087] Please refer to figure 1 , a multi-party controlled two-way quantum secure direct communication method based on the cluster state, comprising steps:
[0088] S1. The control terminal sets an ordered 2n particle cluster state sequence of a preset length, and the ordered 2n particle cluster state sequence is in a preset state Among them, σ z =|0>
[0089] S2. The control terminal takes out a particle from each 2n particle entangled state in the ordered 2n particle cluster state sequence to form 2n ordered particle sequences respectively, and saves the particles of each ordered particle sequence order, each particle sequence contains a particle in each 2n particle entangled state in the ordered 2n particle cluster state sequence;
[0090] S3. The control terminal respectively scrambles the particle sequences of the 2n ordered particle sequences, and sends the scrambled 2n particle sequences to 2n communication terminals respectively, that is, after the tth scrambled se...
Embodiment 2
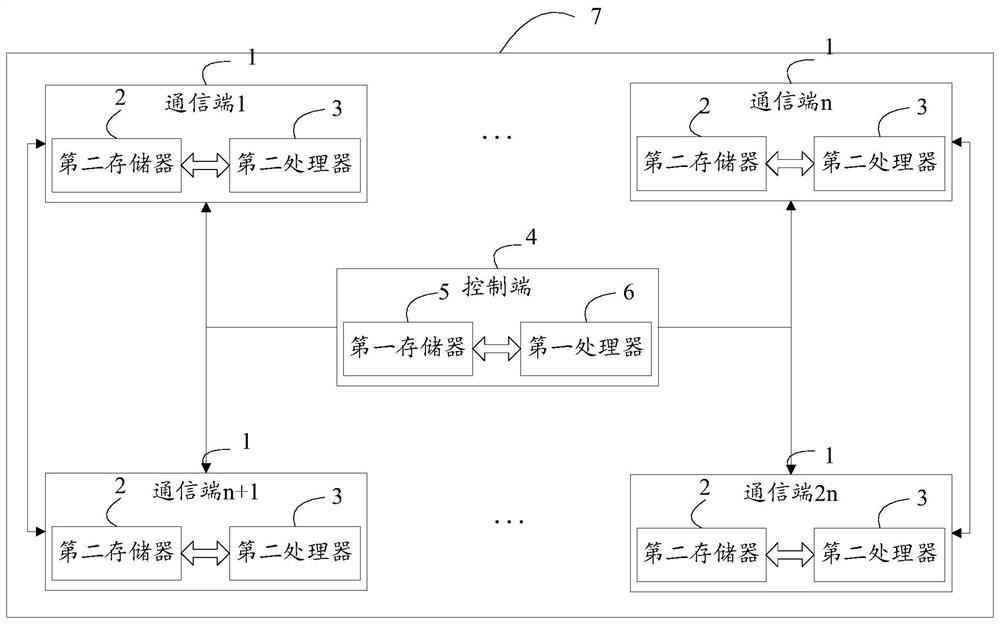
[0120] Please refer to figure 2 , a controlled two-way quantum-safe direct communication system 7 based on a cluster state, including a control terminal 4 and 2n communication terminals 1;
[0121] The control terminal 4 includes a first memory 5, a first processor 6 and a first computer program stored on the first memory 6 and operable on the first processor 6, and the communication terminal 1 includes a second memory 2 , the second processor 3 and the second computer program stored on the second memory 2 and operable on the second processor 3, the first processor 6 implements the first computer program when executing the first computer program The steps executed by the control terminal 4;
[0122] When the second processor 2 executes the second computer program, the steps performed by the communication terminal 1 in the first embodiment are realized.
Embodiment 3
[0124] Apply the above cluster state-based four-way controlled two-way quantum secure direct communication method to practical application scenarios:
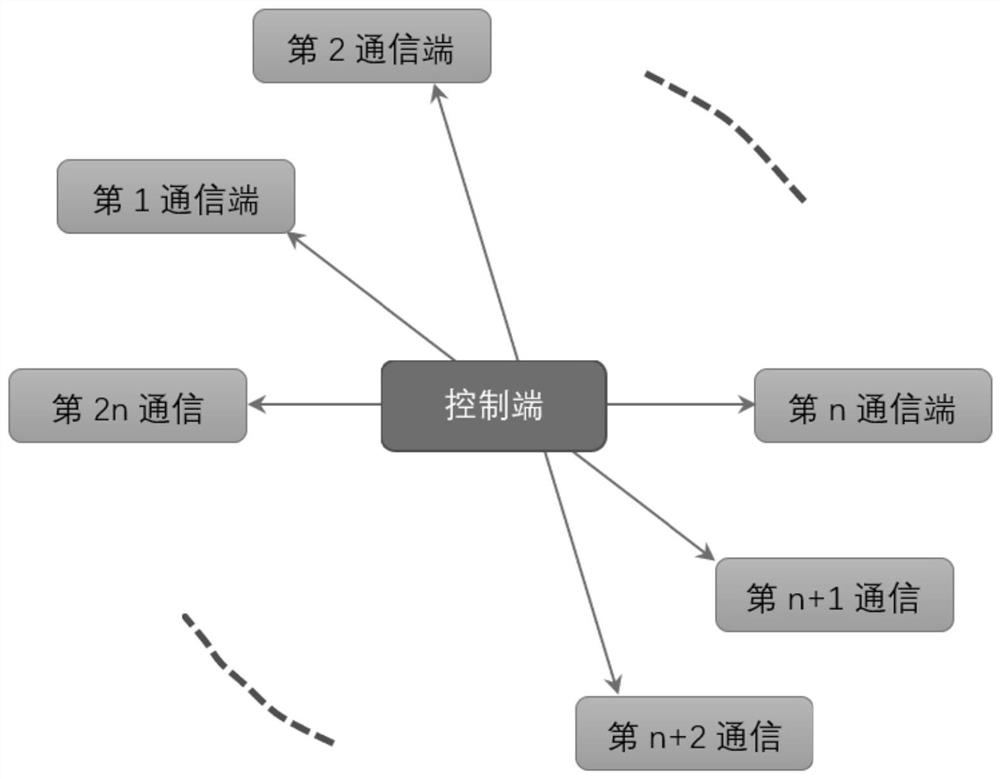
[0125] Step S1: if Figure 4 As shown, there are four communication terminals: Alice, Bob, Charlie and David, that is, users, and a semi-trusted control terminal, Trent, that is, the administrator. Alice and Charlie, Bob and David carry out two-way information transmission through Trent ; Alice put the secret message sent to Charlie, and at the same time, Charlie sends the secret message Send to Alice; Bob sends the secret message Send to David, at the same time, David sends the secret message send to Bob;
[0126] Step S2: Administrator Trent prepares an ordered four-particle cluster state sequence with length l=2N+4δ, each sequence is in state. Trent takes out one particle from each four-particle entangled state to form four ordered particle sequences: A={a 1 ,a 2 ,...,a l}, B={b 1 ,b 2 ,...,b l}, C={c 1 ,c ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com