Mobile application program behavior identification method based on spectral clustering and random forest algorithm
A random forest algorithm and mobile application technology, applied in the field of information security, can solve the problems of affecting the accuracy of the classifier, overfitting, and large algorithm time overhead, so as to reduce the clustering time complexity, reduce misjudgment, and reduce the time complexity. small effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings.
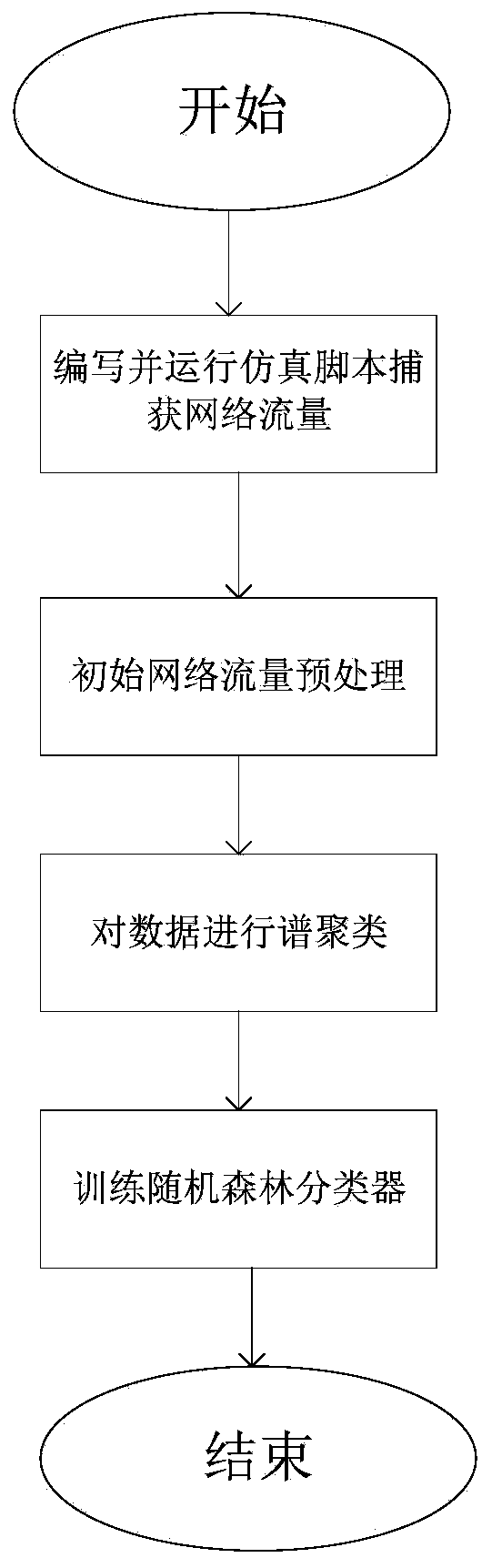
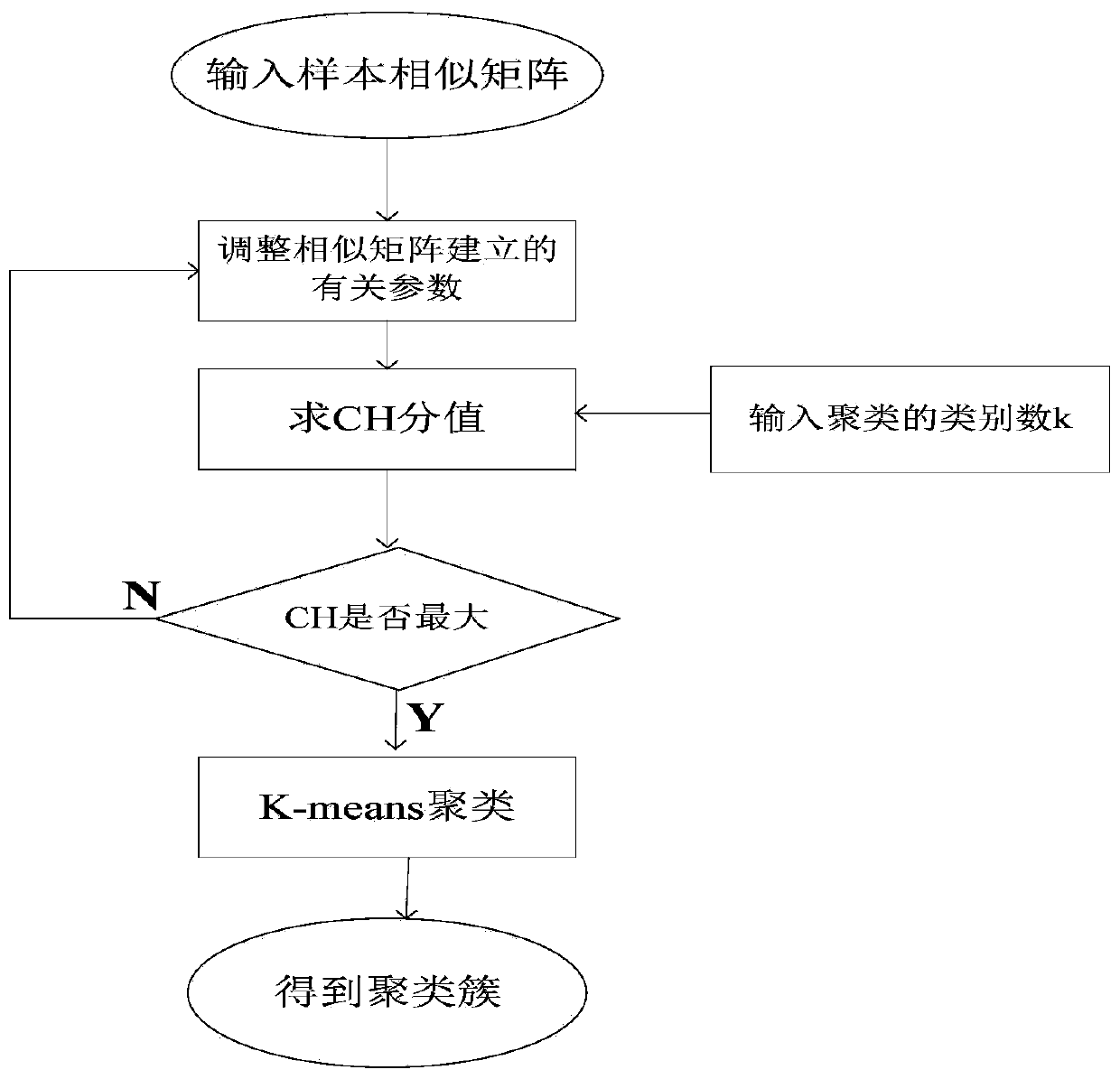
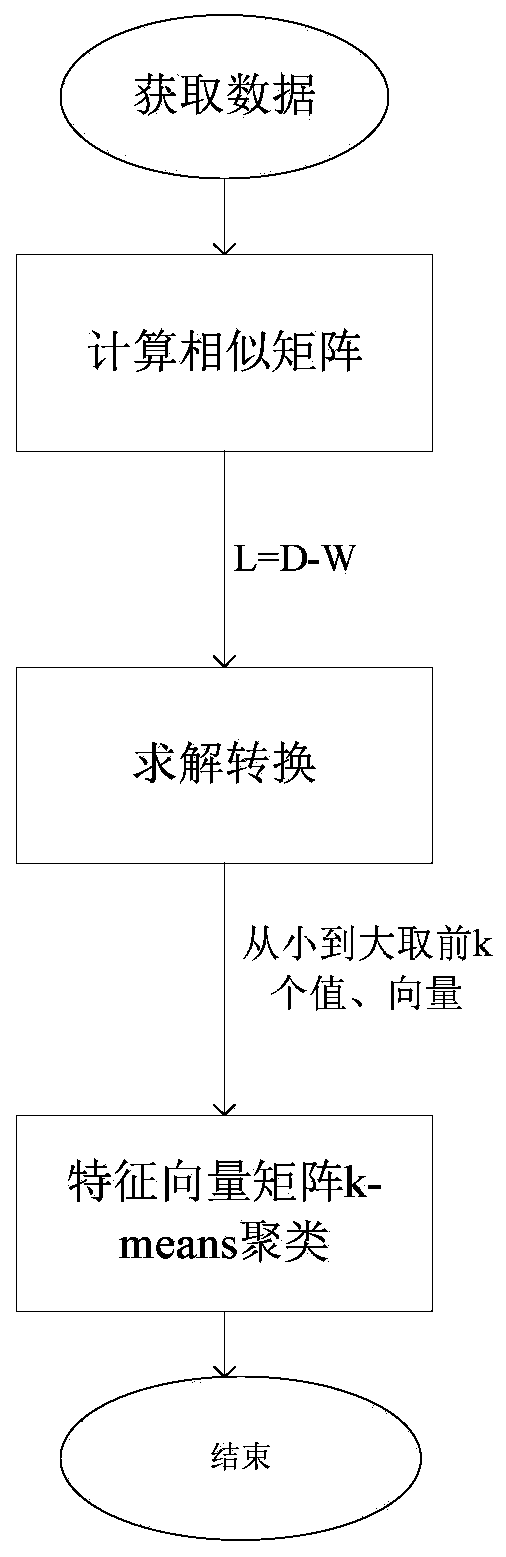
[0047] according to figure 1 Given the overall process flow chart, the specific implementation of this embodiment is as follows:
[0048] Step 1: Write and run a simulation script to capture network traffic.
[0049] Simulation script writing and implementation, the specific steps are as follows:
[0050] 1.1 Use the ADB command to write a script that submits the operation sequence to the mobile phone to generate the application startup, touch and button. The full name of ADB command is Android Debug Bridge. It provides a general debugging tool. With this tool, we can debug the developed program well;
[0051] 1.2 Insert the written simulation script from the Wi-Fi access point, capture the data flow from the network flow script of the eavesdropping device from the network side, and record the execution time of each operation;
[0052] 1.3 By ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com