Single sign-on implementation method based on ukey authentication
An implementation method and single sign-on technology, applied in the network field, to achieve the effect of highlighting substance and ensuring legitimacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
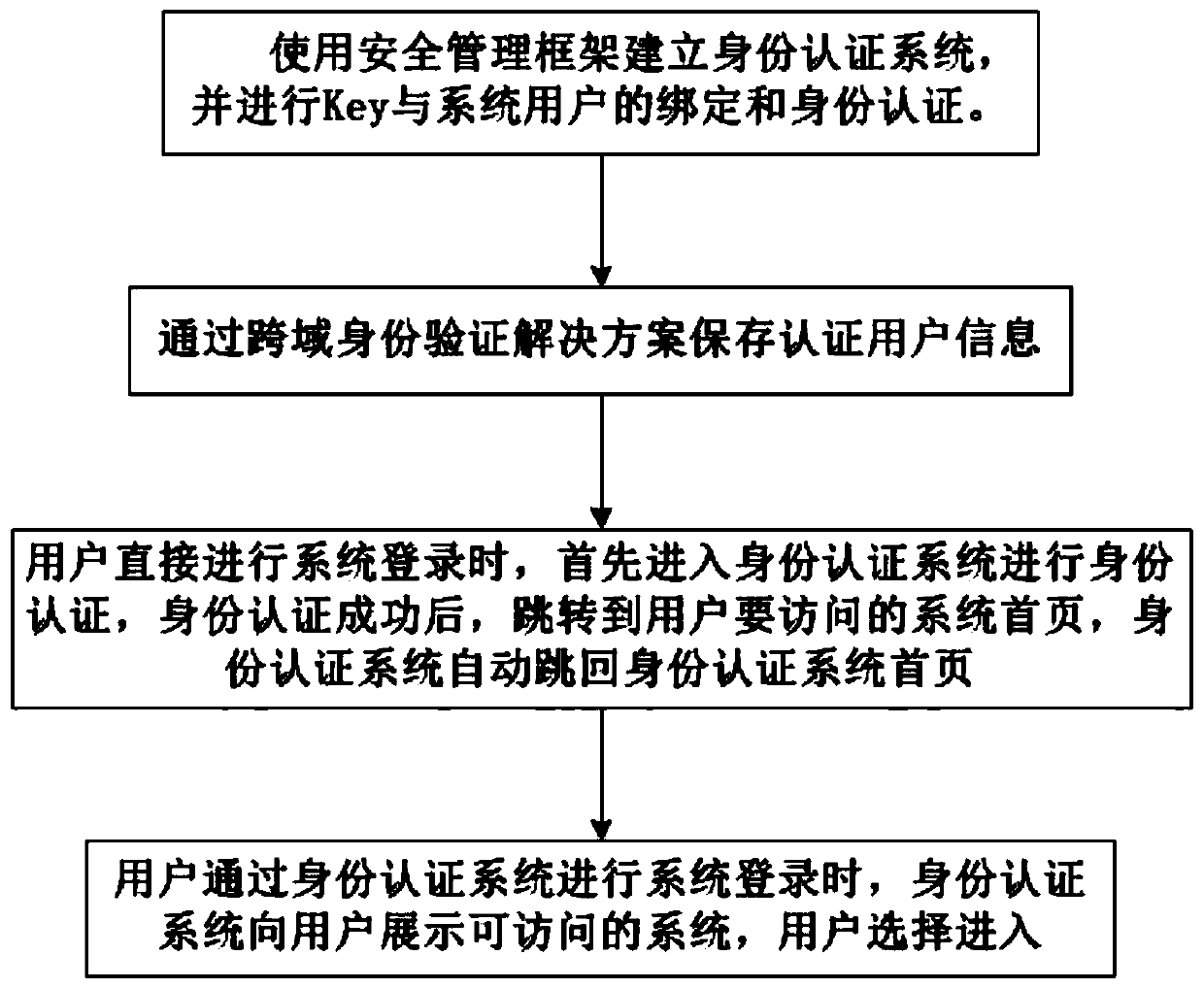
[0033] Such as figure 1 A single sign-on implementation method based on ukey authentication is shown, including:
[0034] Use the security management framework to establish an identity authentication system, and perform key and system user binding and identity authentication.
[0035] Save authenticated user information through cross-domain authentication solutions.
[0036] When the user directly logs in to the system, he first enters the identity authentication system for identity authentication. After the identity authentication is successful, he jumps to the homepage of the system that the user wants to visit, and the identity authentication system automatically jumps back to the homepage of the identity authentication system.
[0037] When the user logs in to the system through the identity authentication system, the identity authentication system shows the user the accessible systems, and the user chooses to enter.
Embodiment 2
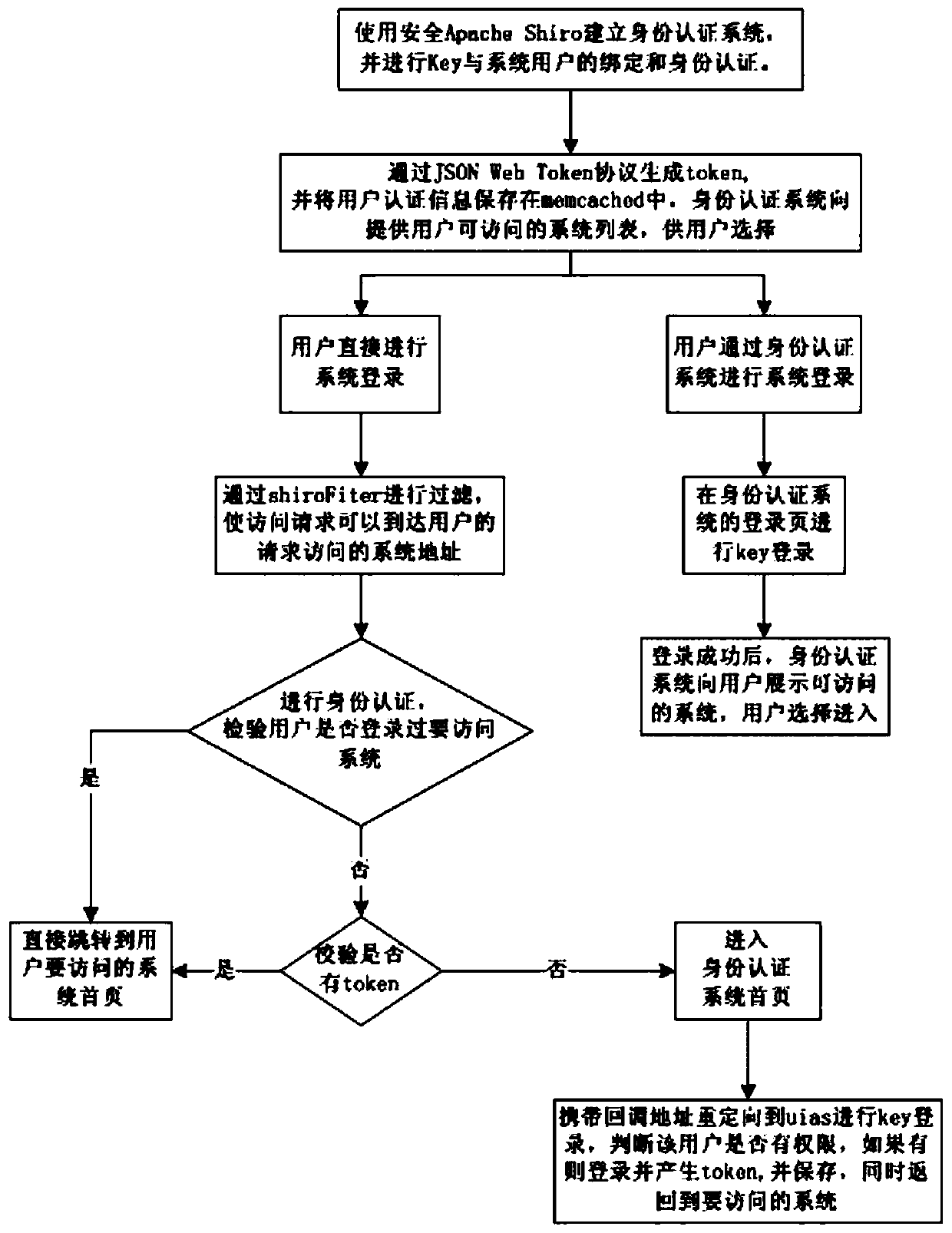
[0039] Based on the first embodiment, the security management framework adopts Apache Shiro; the cross-domain authentication solution adopts JSON Web Token. Apache Shiro is a powerful and easy-to-use Java security framework that performs authentication, authorization, password and session management. With the help of the existing excellent security management framework shiro to realize the authority management of the system, and at the same time refer to the cas mode to realize the authentication system, the authentication of the system is completed based on the ukey authentication at the PKI level. After the authentication is completed, the token generated by jwt is saved in memcached, and the user can log in to other systems without further authentication. After the user logs out of a certain system, he needs to re-authenticate. SON Web Token (JWT) is currently the most popular cross-domain authentication solution.
[0040] Such as figure 2 A single sign-on implementation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com