Malicious software detection method
A malware and detection method technology, applied in the direction of computer components, instruments, platform integrity maintenance, etc., can solve the problem of lack of effective detection and killing of new malware, achieve efficient and rapid judgment, ensure safety, and improve detection efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] Example 1: Please refer to Figure 1~4 , a malware detection method, comprising the steps of:
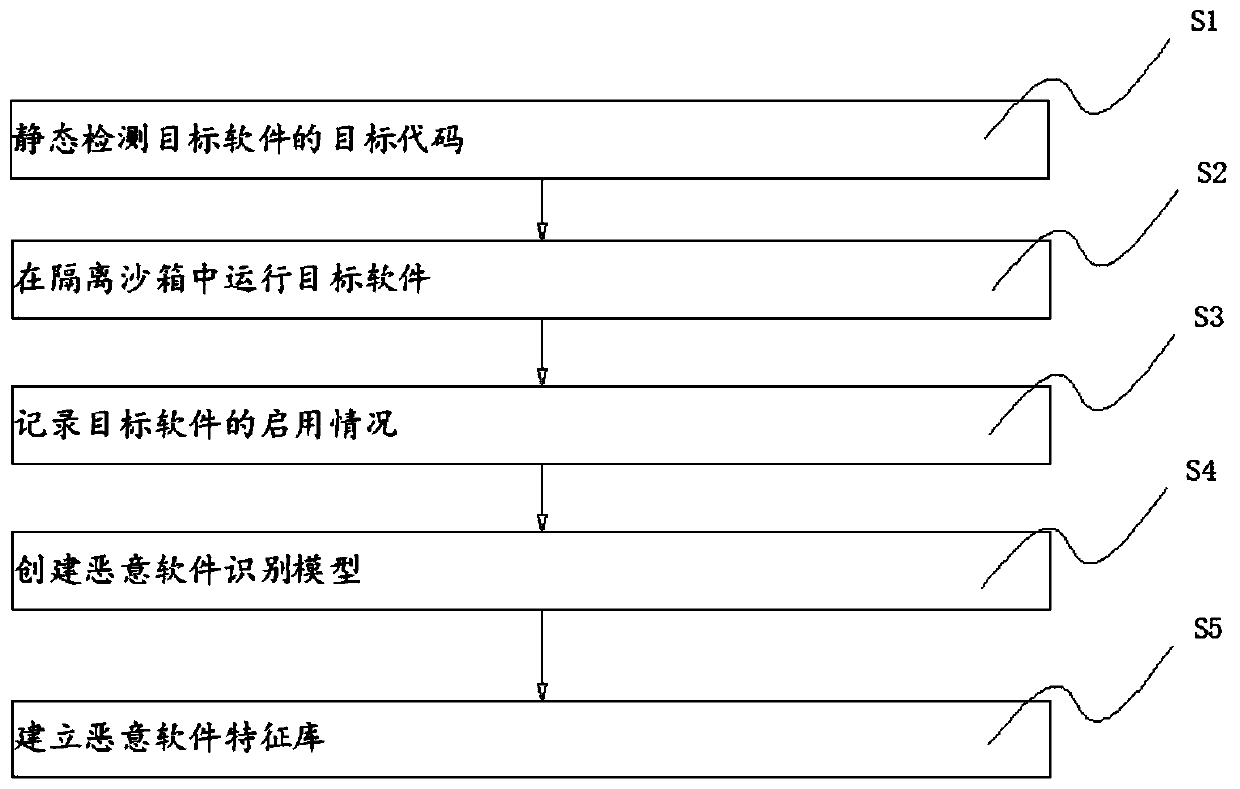
[0035] S1: Statically detect the target code of the target software, decompile the target software in the isolation sandbox to obtain the target code, and then analyze the target code to determine whether there is malicious code;
[0036] S2: Run the target software in the isolation sandbox, copy and create a local system in the isolation sandbox, and then use the system in the sandbox to run the target software;
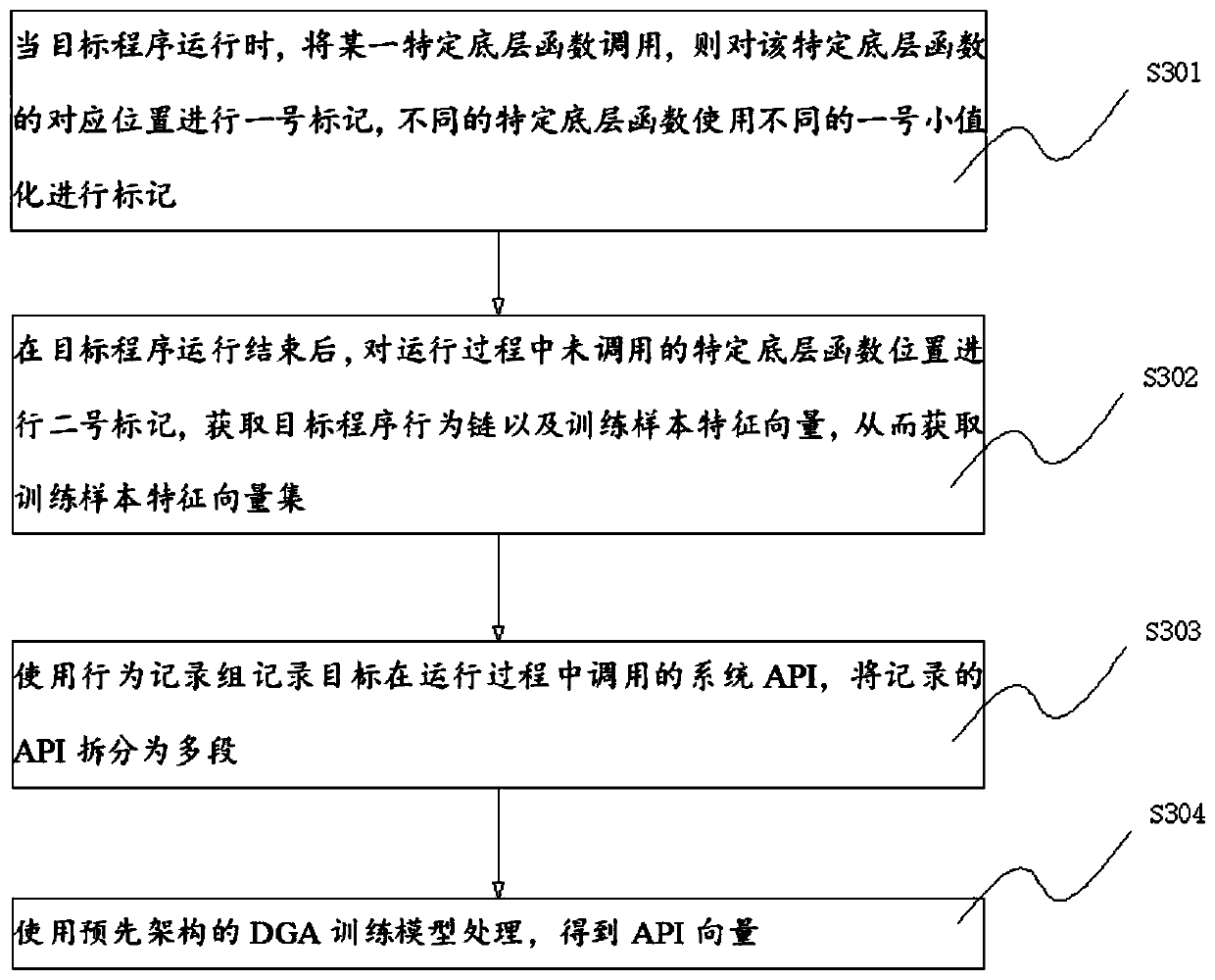
[0037] S3: Record the enablement of the target software, record the enablement of the corresponding pre-selected multiple specific underlying functions during the running process of the target software, and the system API called by the target software, and generate a sample vector to be identified;
[0038] S4: Create a malware recognition model, use the pre-created malware recognition model, use a machine learning algorithm to classify the sample vectors to be re...
Embodiment 2
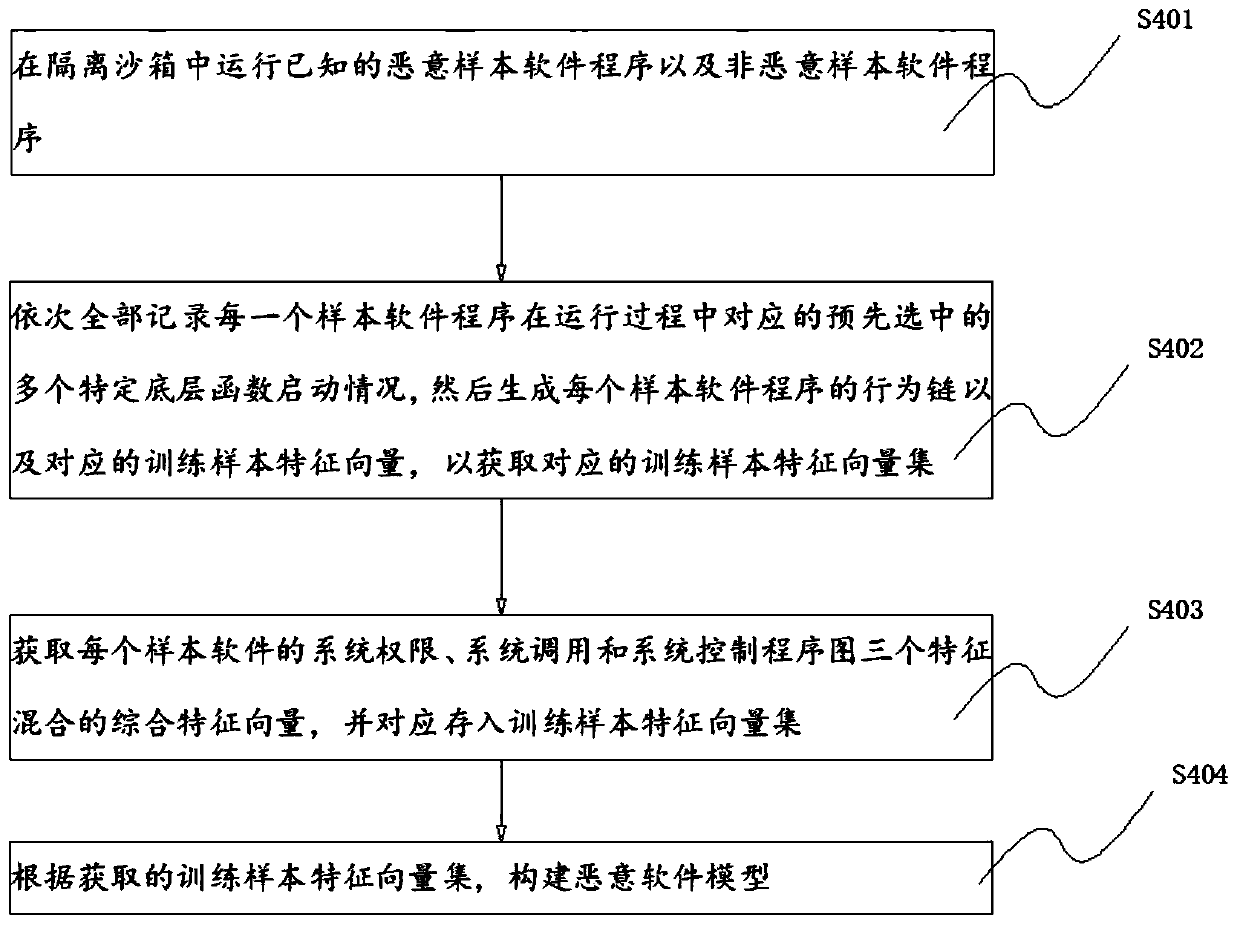
[0049] Embodiment 2: This embodiment adds the following technical features on the basis of Embodiment 1:
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com