Method and computing device for isolating power information and relying on it for power checking
A technology of power and inspection results, applied in the information field, can solve problems such as lack of effective mechanisms, and achieve the effect of avoiding unauthorized operations, single function, and simple processing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
[0058] An implementation method for "no interaction with the outside world during the calculation and processing of any power information" is:
[0059] Before shutting down, the general shutdown program of the kernel triggers a special program for power information synchronization to synchronize all the power information to the peripherals to ensure that the power information stored on the peripherals is consistent with the power information in the memory. The logic of this special program includes synchronizing power information on peripherals, and there is no other content, so as to ensure its single function and simple logic. The correctness of this special program can be confirmed through formal testing and exhaustive testing , it will not generate attacks by itself during synchronization and affect the reliability of power information.
Embodiment 3
[0061] An implementation method for "no interaction with the outside world during the calculation and processing of any power information" is:
[0062] Take creating a file as an example:
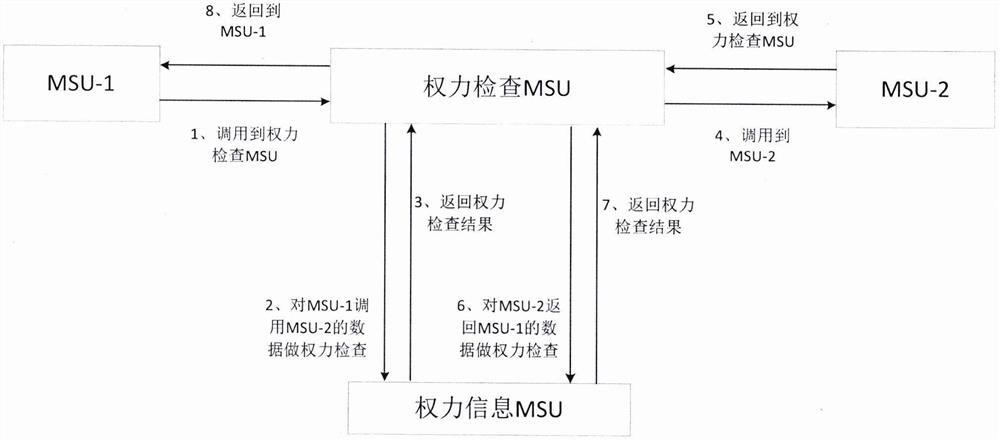
[0063] Through the system call soft interrupt, after entering the corresponding function MSU of the system call, the function MSU will receive parameters including the path of the file to be created, read and write attributes, and create file tags, etc., and will first call the power check MSU to perform permission checks, power checks The MSU will pass the passed parameters to the power information MSU. The specific inspection work is performed in the power information MSU by a special program for file power information processing, that is, by analyzing the path name, it is determined whether the current user has the right to access directory files at all levels. If the check is passed, finally create and add a file management structure for the target file (wherein the file authority attri...
Embodiment 4
[0069]An implementation method for "no interaction with the outside world during the calculation and processing of any power information" is:
[0070] Take writing to a file as an example:
[0071] Through the system call soft interrupt, after entering the function MSU corresponding to the system call, it will receive parameters including the file handle to write the target file, the address of the data to be written in the process space, and the number of bytes to be written. Call the power check MSU to perform permission check. The power check MSU will pass the passed parameters to the power information MSU. The specific checking work is carried out in the power information MSU by a special program for data block processing, and the file file management is obtained through the file handle. structure, check whether the file management structure is within the scope of the current user-operable file, if the check is passed, further obtain the data block index information, and d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com