Agent-based vulnerability scanning method
A vulnerability scanning and vulnerability technology, applied in the field of network security, can solve the problems such as the inability to obtain login status information, the inability to discover security vulnerabilities, and the inability to scan IOT devices, and achieve the effect of high scalability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0007] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
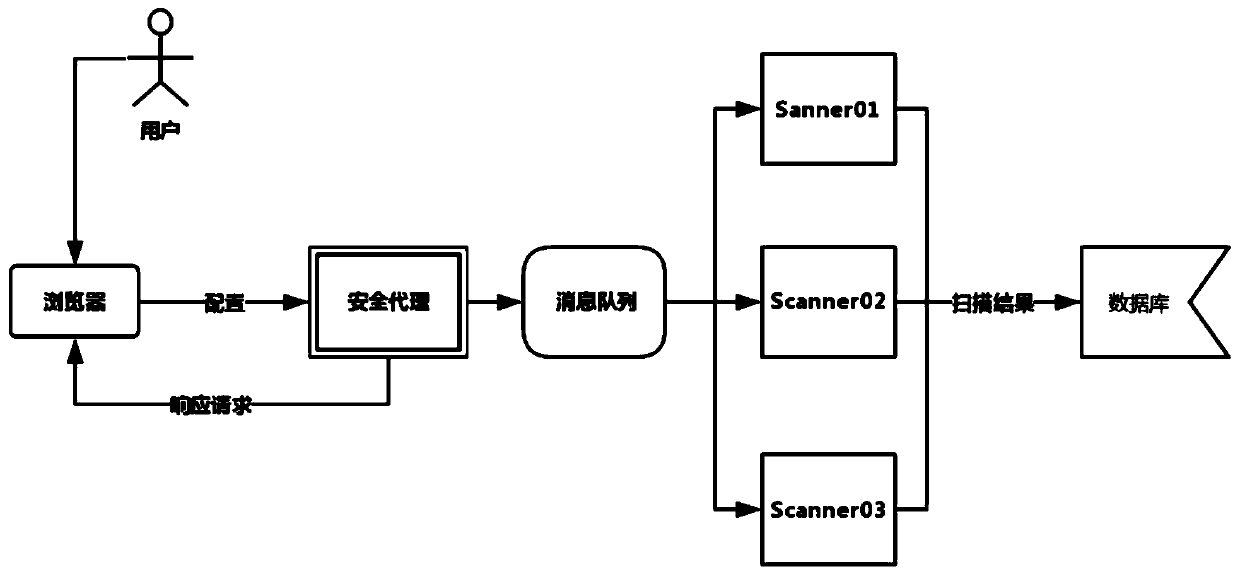
[0008] figure 1 It is a schematic diagram of the architecture of the agent-based vulnerability scanning system of the present invention.
[0009] See figure 1 , the agent-based vulnerability scanning method provided by the present invention mainly includes two core modules, an agent module and a vulnerability scanning module,
[0010] The proxy module provides an http(s) proxy to format the target traffic accessed by users, and extracts the information needed for scanning nodes, including url, cookies, headers, request parameters, etc.
[0011] The vulnerability scanning module performs vulnerability scanning on the information provided by the agent node, and stores the vulnerability information in the database.
[0012] Concrete operation process of the present invention is as follows:
[0013] Step 1: User configures proxy authorization and CA cer...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com