A security encryption method and decryption method for train CAN bus communication
A CAN bus, communication security technology, applied in bus network, secure communication device, key distribution, can solve problems such as cracking and tampering, easy to be monitored by attackers in train CAN bus communication, and unable to judge the authenticity of data, etc., to achieve the steps Simplicity and safety-enhancing effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0049] This embodiment relates to a secure encryption method for train CAN bus communication.
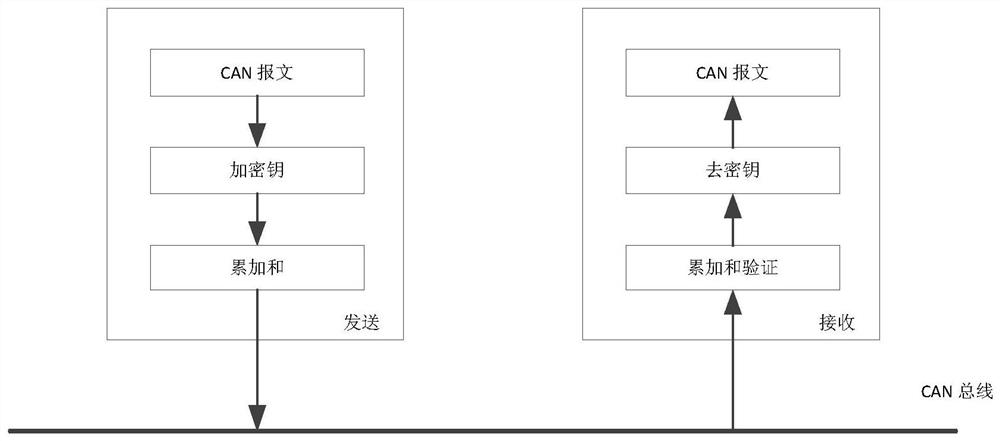
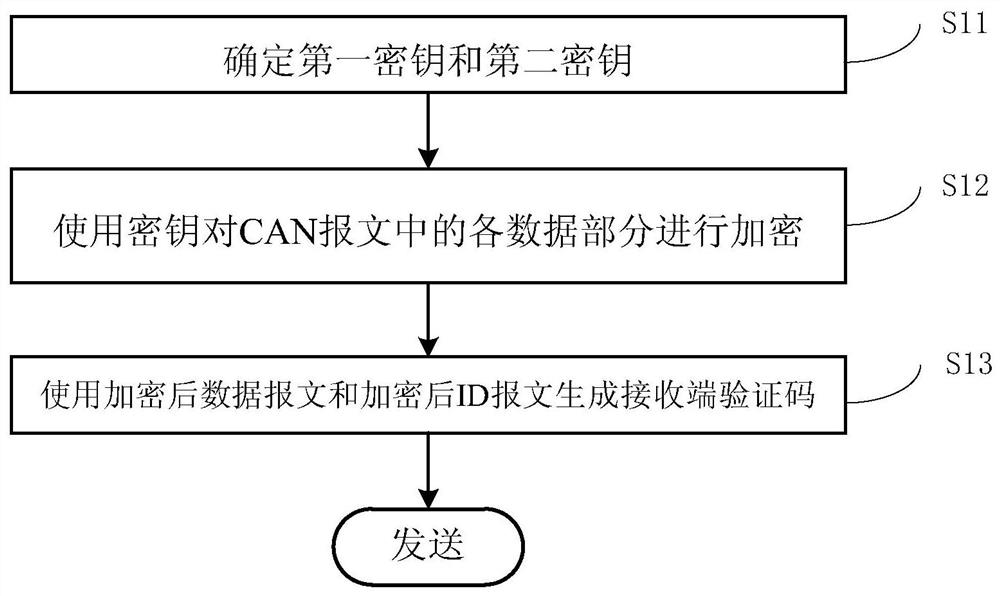
[0050] Combine below figure 1 The flow chart of the train CAN bus communication security encryption process in the middle left half and figure 2 To specifically illustrate the CAN bus communication security encryption method. Such as figure 1 and figure 2 As shown, the train CAN bus communication security encryption method of this embodiment mainly includes the following steps 11 to 13.
[0051] In step 11, a first key and a second key are determined.
[0052] In a preferred embodiment of the present invention, both the first key and the second key use Gold codes, and the generation expression is XOR of two m-sequences. Because the Gold code has the advantages of easy generation, strong regularity, random distribution of 0 and 1 codes, and it is difficult to be guessed without knowing the expression of the generated Gold code, so applying it to the train CAN bus communication...
no. 2 example
[0068] This embodiment relates to a secure decryption method for train CAN bus communication.
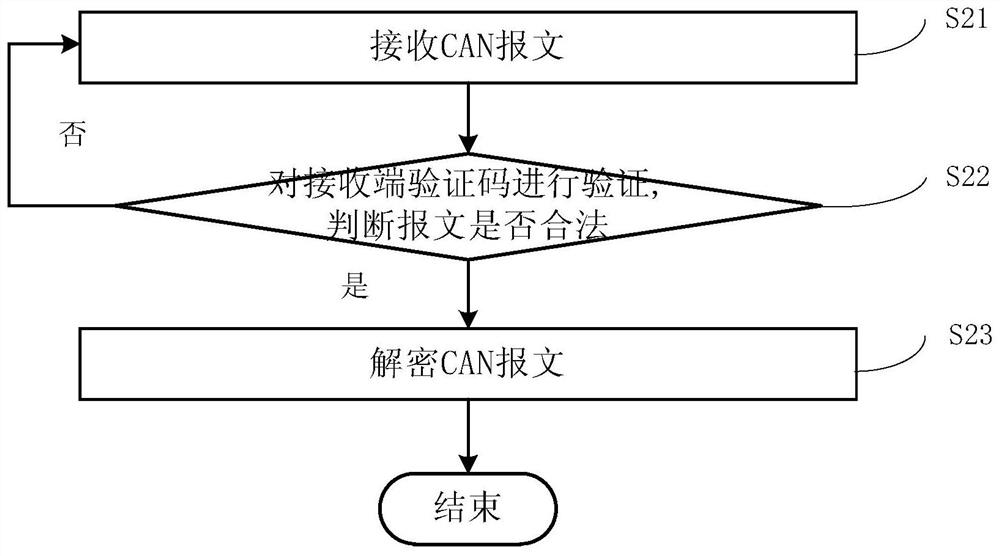
[0069] In addition to the above-mentioned safe encryption method for train CAN bus communication, the present invention also includes a safe decryption method for train CAN bus communication. figure 1 The middle right half is the flow chart of the train CAN bus communication security decryption process. Combine below figure 1 and image 3 To specifically illustrate the train CAN bus communication security decryption method. The secure decryption method for train CAN bus communication in this embodiment mainly includes the following steps 21 to 23.
[0070] In step 21, the receiver first receives the encrypted CAN message. Here, the encrypted CAN message includes the receiving end verification code, the encrypted data message encrypted by the first key, and the encrypted ID message encrypted by the second key.
[0071] In step 22, it is judged whether the encrypted CAN message i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com