Method and system for preventing sensitive data leakage
A sensitive data and sensitive technology, applied in the fields of digital data protection, data processing applications, electrical digital data processing, etc., can solve the problem of not forming anti-leakage methods and processes, achieve intuitive circulation and use process, improve accuracy, reduce The effect of the risk of leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
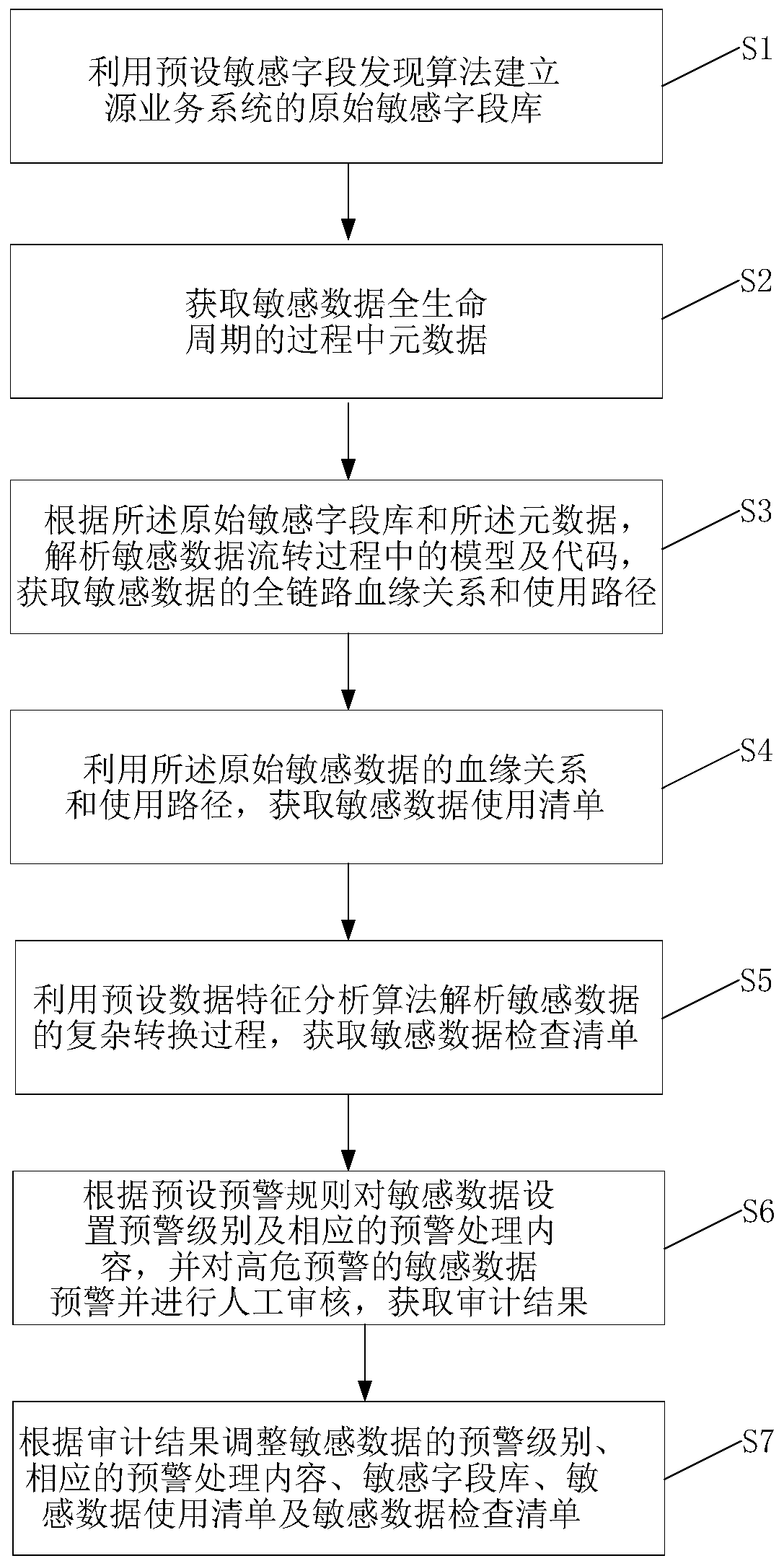
[0031] The embodiment of the present invention provides a method for preventing leakage of sensitive data, which can be applied to the field of big data security governance, such as figure 1 As shown, the method for preventing leakage of sensitive data includes the following steps:
[0032] Step S1: Establish the original sensitive field library of the source business system by using a preset sensitive field discovery algorithm.
[0033]In the embodiment of the present invention, since the sensitive fields are all generated from the source business system, it is necessary to sort out the sensitive data in the source business, and at the same time use the preset sensitive field discovery algorithm to establish the original sensitive field library of the source business system to facilitate unified management For all sensitive field information, the preset sensitive field discovery algorithm in the embodiment of the present invention is a relatively mature algorithm in the prior...
Embodiment 2
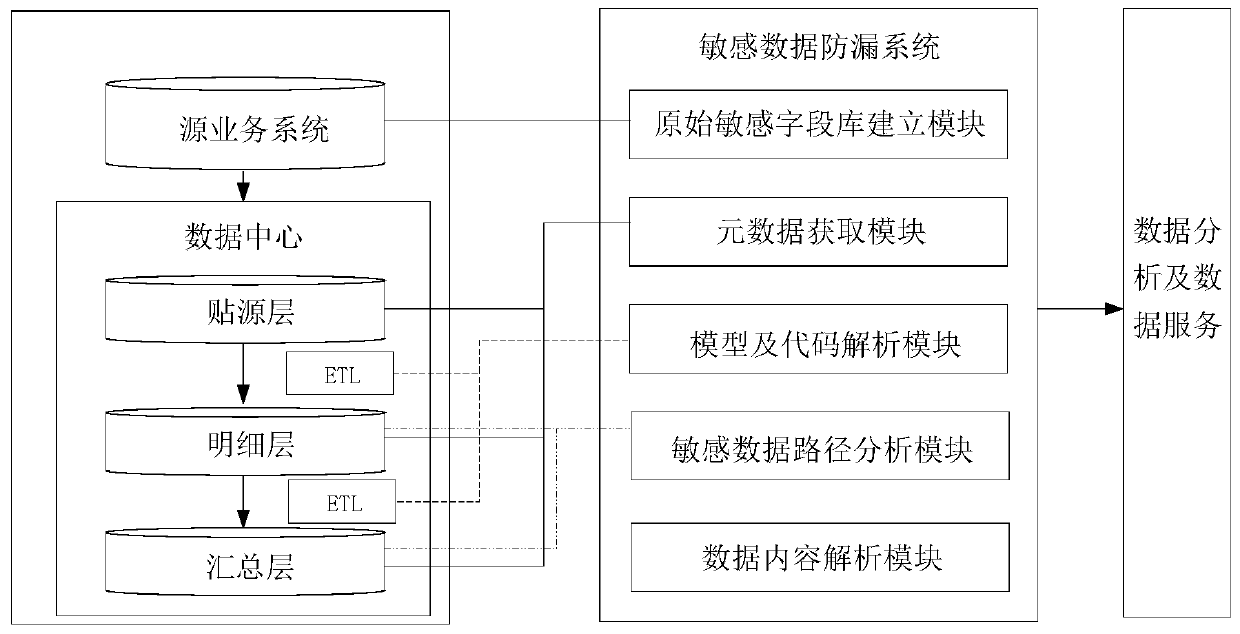
[0083] This embodiment provides a system for preventing leakage of sensitive data, such as Figure 8 shown, including:
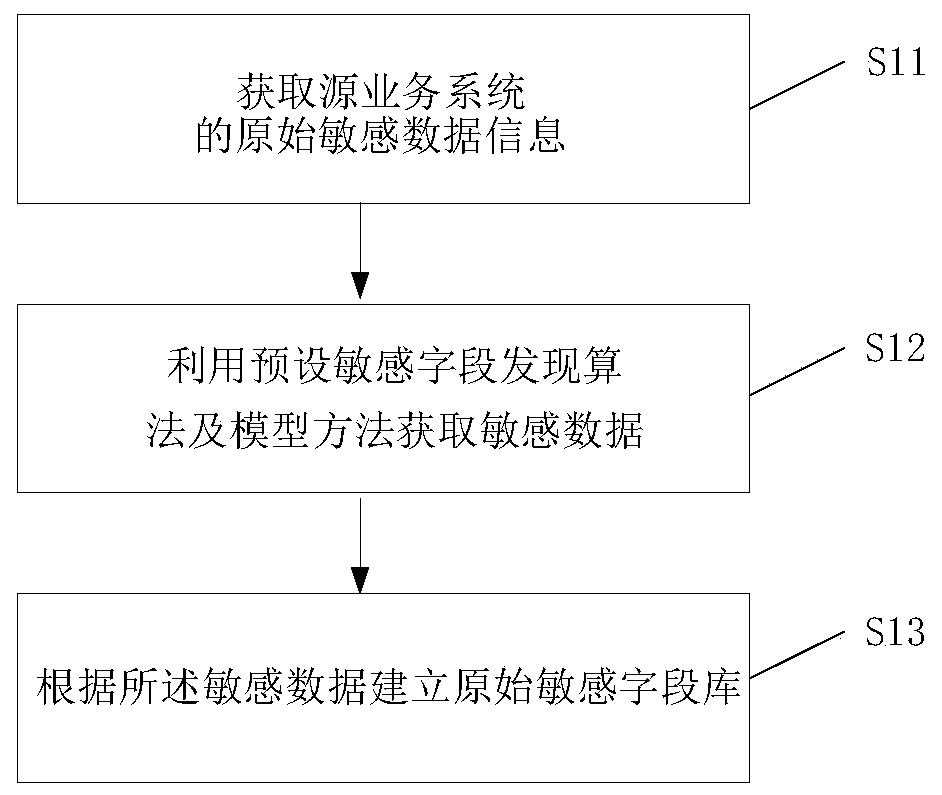
[0084] The original sensitive field library building module 1 is used to create the original sensitive field library of the source business system by using the preset sensitive field discovery algorithm; this module executes the method described in step S1 in Embodiment 1, which will not be repeated here.
[0085] The metadata acquisition module 2 is used to acquire metadata during the whole life cycle of sensitive data; this module executes the method described in step S2 in Embodiment 1, and details are not repeated here.
[0086] The model and code analysis module 3 is used to analyze the model and code in the sensitive data transfer process, and obtain the blood relationship and usage path of the sensitive data in the whole link; this module executes the method described in step S3 in Embodiment 1, and in This will not be repeated here.
[0087] The se...
Embodiment 3
[0093] An embodiment of the present invention provides a computer device, such as Figure 9 As shown, it includes: at least one processor 401 , such as a CPU (Central Processing Unit, central processing unit), at least one communication interface 403 , memory 404 , and at least one communication bus 402 . Wherein, the communication bus 402 is used to realize connection and communication between these components. Wherein, the communication interface 403 may include a display screen (Display) and a keyboard (Keyboard), and the optional communication interface 403 may also include a standard wired interface and a wireless interface. The memory 404 may be a high-speed RAM memory (Ramdom Access Memory, volatile random access memory), or a non-volatile memory (non-volatile memory), such as at least one disk memory. Optionally, the memory 404 may also be at least one storage device located away from the aforementioned processor 401 . The processor 401 may execute the method for pre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com