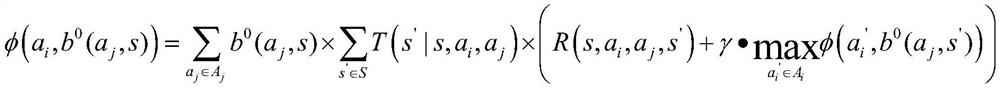An Intrusion Response Method Based on Attack Graph and Theory of Mind
A technology of attack graph and Bayesian attack graph, which is applied in the field of network security and can solve problems such as incompatibility with network attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] specific implementation
[0044] The present invention will be described in detail below according to the accompanying drawings to highlight the purpose and specific effects of the present invention.
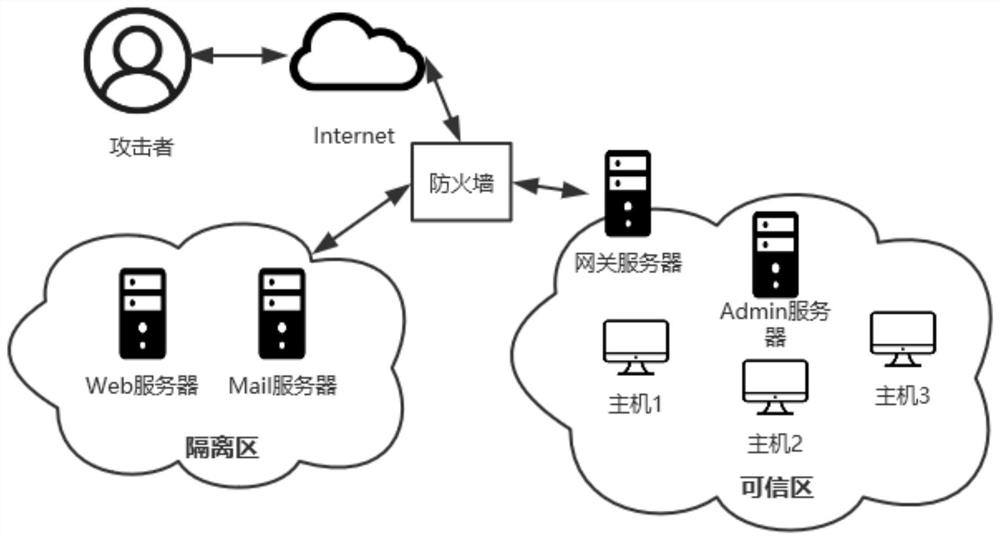
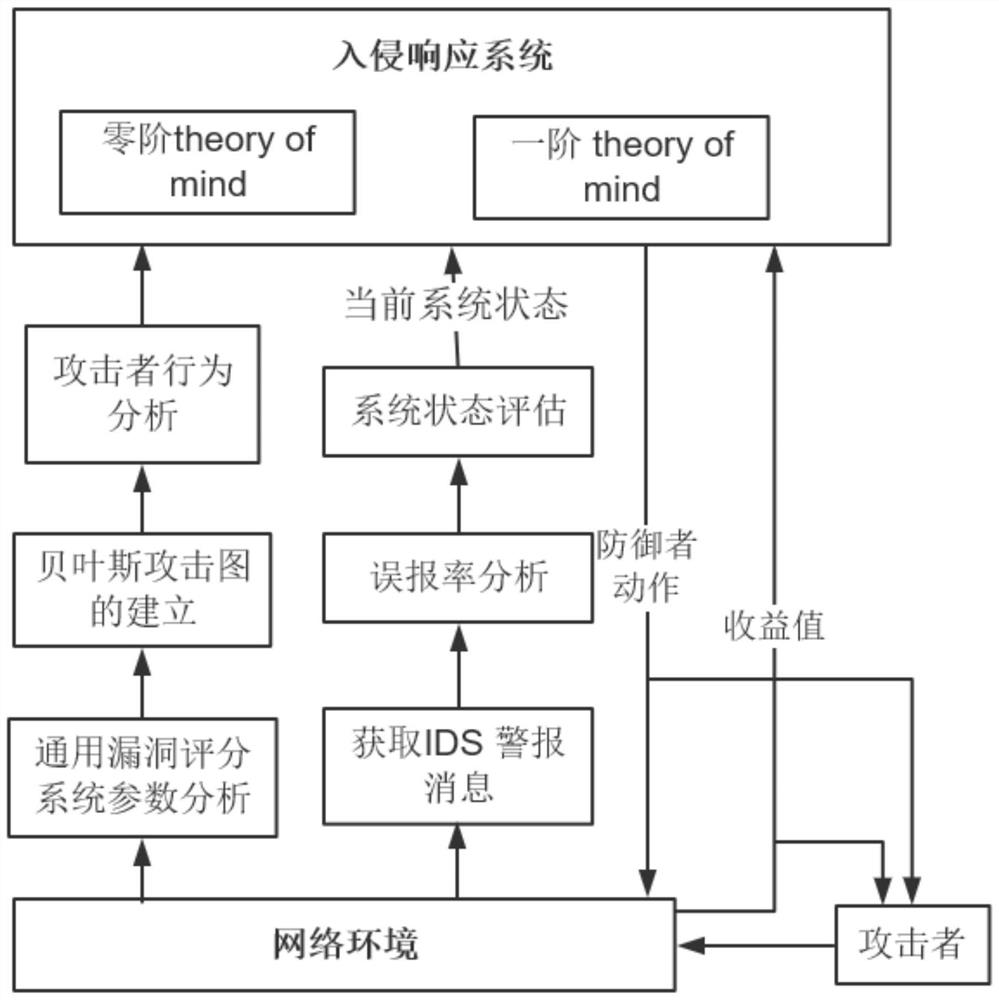
[0045] The present invention is an intrusion response method based on attack graph and psychological theory. Firstly, network attack and defense parties are modeled as a zero-sum two-player random game. Attackers aim to invade the entire network by exploiting a series of loopholes in the system, while defenders deploy monitoring devices to obtain the current network status, analyze the behavior of the attacker, and use the first-order ToM to speculate that the attacker will be most effective at the next moment. Attacks that may be taken, so that real-time and effective response measures can be formulated. The present invention mainly comprises the following steps:
[0046] Step 1: The present invention firstly models both network attack and defense as a two-person zero-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com