Method for verifying integrity of data in hybrid cloud storage
A technology for integrity verification and data storage, applied in the field of data integrity verification in hybrid cloud storage, can solve the problem of wasting private cloud computing power and storage space, achieve efficient dynamic update operations, improve user experience, and improve user experience Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0042] In this embodiment, the respective working processes of the private cloud and the public cloud are described, as follows:
[0043] Assign secret keys to files and generate tags through private cloud as follows:
[0044] The private cloud distributes keys and offline tags in advance, and the offline tags include file block alias information, offline chameleon hash auxiliary variables, and dynamic update general variables in the keys.
[0045] At this time, due to strong privacy, from the perspective of security, the private cloud is used for key distribution, which has high security.
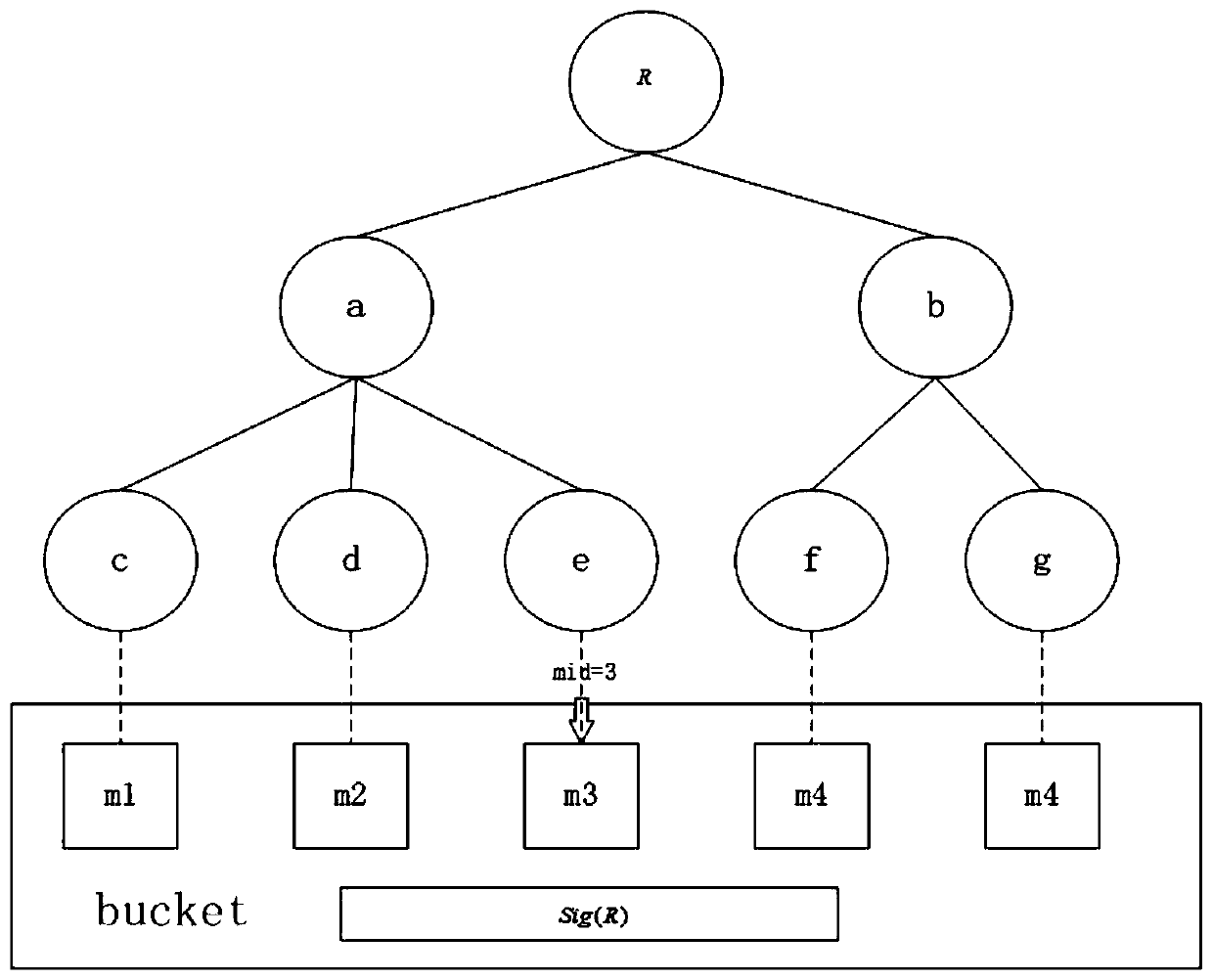
[0046] Further, before the selected file is verified, file segmentation is also included. The file segmentation is specifically that the user divides the file to be uploaded into blocks to obtain a set of file blocks, and performs partition processing for each individual file block , divide a single file block into several sectors, calculate the online chameleon hash auxiliary variable co...
Embodiment 2
[0066] Below in conjunction with embodiment, the present invention is described in detail:
[0067] S1: The key generation stage, which is specifically implemented through the following detailed steps:
[0068] Generate user public and private keys: Initialize G 1 , G 2 , GT is the multiplicative cyclic group of prime order, and defines the bilinear mapping operation e:G 1 ×G 2 →GT; initialize the integer group Zq of prime number order, randomly select any large integer α in the Zq group, as the user's private key, denoted as sk=α, randomly select G 2 The generator of the group is denoted as g; calculate the user public key v=g α ;
[0069] Among them, define the G in the bilinear mapping operation 1 and G 2 It is automatically generated from open source code.
[0070] In this embodiment, any large integer mentioned, that is, a very large integer, may be an integer with a length of several tens of digits.
[0071] Generate the chameleon hash function public key and tr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com