Dynamic and static combination detection method for Android mobile network terminal malicious codes based on SVM
A malicious code, dynamic and static combination technology, applied in the field of information security, can solve the problems of low malware detection accuracy, malicious family classification accuracy, inability to handle dynamic loading, runtime encryption and decryption, etc. The effect of accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
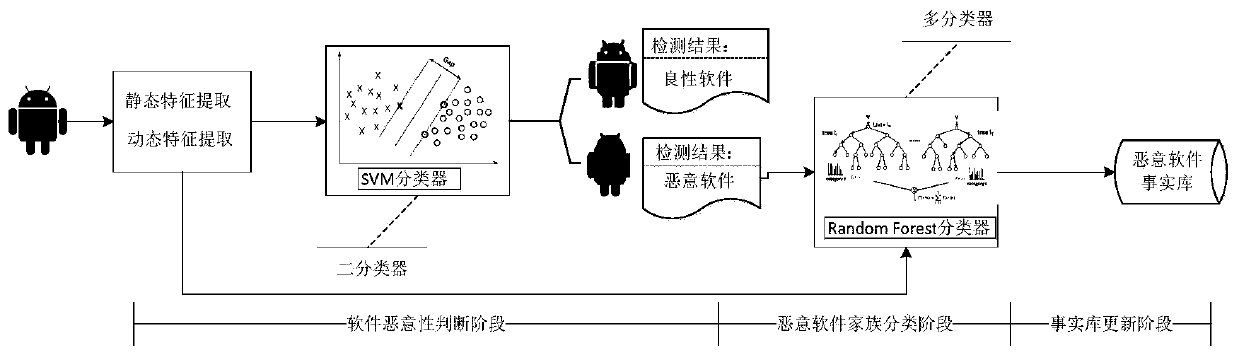
[0060] In order to verify the effectiveness of the scheme of the present invention, Drebin data set and non-malware samples obtained from Google Play are used to form a data set, and malicious code detection and family classification simulation are carried out.
[0061] Step 1. Divide the samples in Drebin according to the malicious families they belong to, use the web crawler method to obtain non-malware software on Google Play, and use the VirusTotal online detection service to verify, so as to build a sample data set and select 70 % of samples as training data;
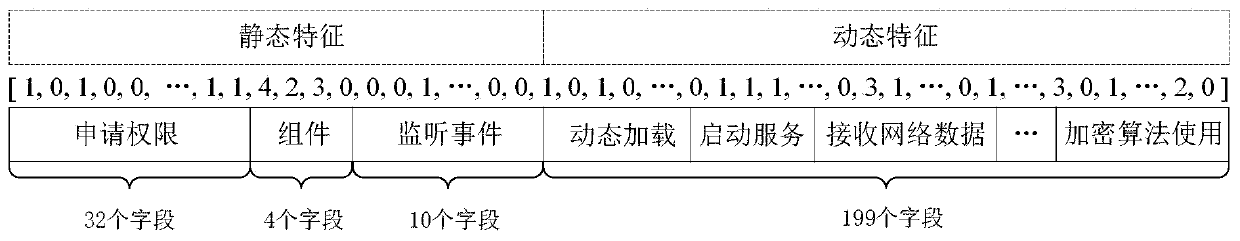
[0062] Step 2. Use APKParser to process the Android software sample, parse the AndroidManifest.xml file, extract the permission list of the software application, the declared components and the system events of the software monitoring according to the tag field in the xml, and construct the static feature F of the software static ,Expressed as:
[0063] f static =
[0064] Among them, Per is a list set of all pe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com