Asset transaction monitoring method
An asset and asset information technology, applied in the field of communication and network, can solve serious security and problems, and achieve the effect of efficient asset management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
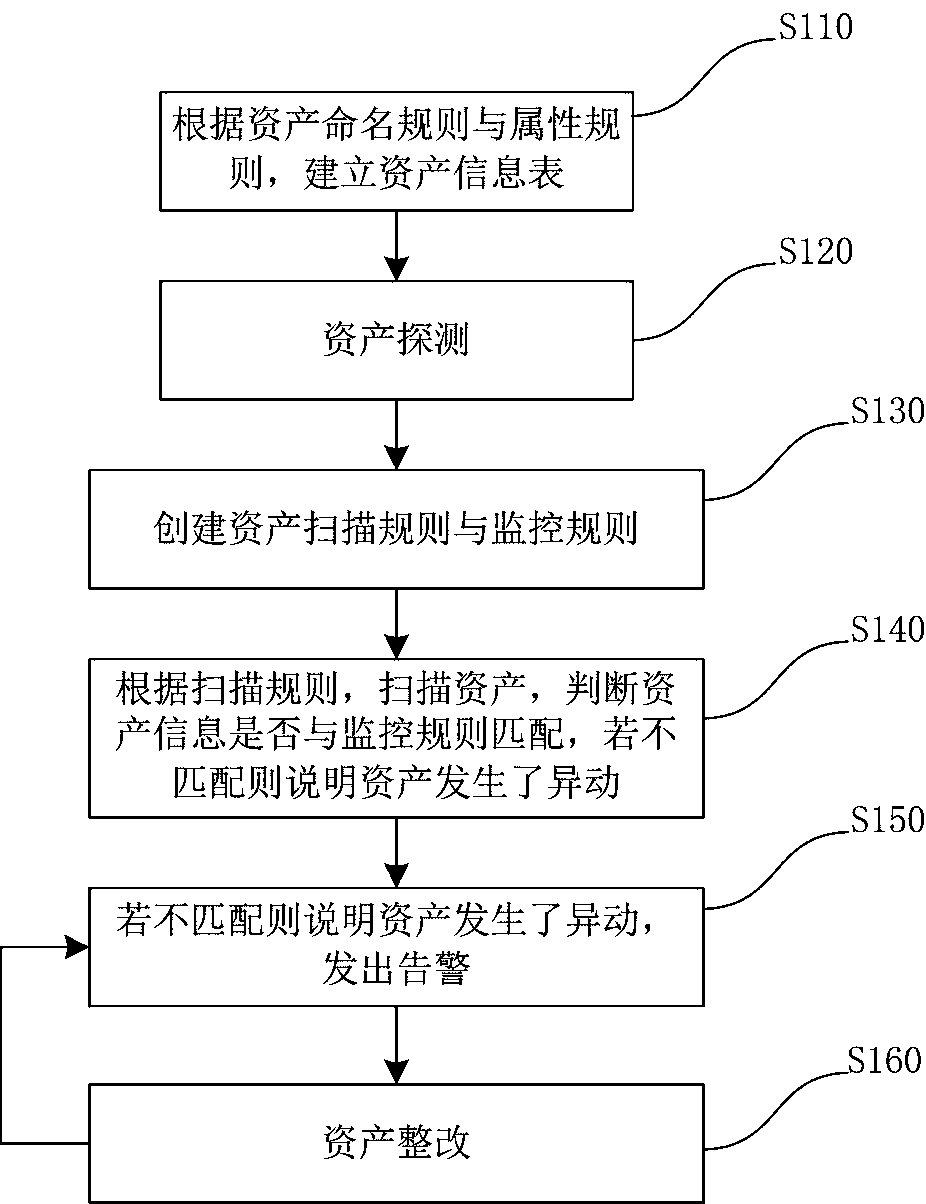
[0043] The asset naming rule is stipulated as "An_Bn_Cn_X", where An represents the unit, Bn represents the department, Cn represents the group, and X represents the Arabic numeral number; divide different network segments for different levels, that is, when the network segment is located at a1, the asset belongs to the A1 unit, and further When the network segment is still in the b1 segment, it still belongs to the B1 department. When the network segment is also in the c1, the asset still belongs to the C1 group; and the rule is encrypted and stored.
[0044] The structure of the specified asset attribute rule is "hostname_IP_MAC_hardware brand / model".
[0045] Establish an asset information list according to the above-mentioned asset naming rules and attribute rules.
[0046] Start asset detection, obtain all information that can describe assets through ping (packet exploration), snmp (simple network management protocol), ssh protocol, wmi (Windows Management Instrumentation...
Embodiment 2
[0056] The asset naming rule is stipulated as "An_Bn_Cn_X", where An, Bn, and Cn represent different authority levels from high to low, and X is an Arabic numeral number. For example, if asset 1 only has the third-level permission 1, its asset name can be "A0_B0_C1_01"; asset 2 has the second-level permission 1, then its asset name can be "A0_B1_C0_01"; asset 3 has the first-level permission If the authority is 1, its asset name can be "A1_B0_C0_01"; assets without any authority can be named "A0_B0_C0_01"; assets with the same authority can be distinguished by the last Arabic numeral.
[0057] It is stipulated that the structure of the asset attribute rule is "hostname_IP_MAC_permission_vulnerability library version".
[0058] Establish an asset information list according to the above-mentioned asset naming rules and attribute rules.
[0059] Start asset detection, obtain all information that can describe assets through ping (packet exploration), snmp (simple network manageme...
Embodiment 3
[0069] The asset naming rule is stipulated as "An_Bn_Cn_X", where An, Bn, and Cn represent the application software categories that assets can be installed and used, and X is an Arabic numeral number. For example, if asset 1 can only install and use A1 software, its asset name can be "A1_B0_C0_01"; asset 2 can install and use A1 and B1 software, then its asset name can be "A1_B1_C0_01"; asset 3 can install and use A1 If software of the same category, software of category B1, and software of category C1, the asset name can be "A1_B1_C1_01"; assets that can be installed with the same category of software can be distinguished sequentially by the last digit of the Arabic numeral.
[0070] It is stipulated that the structure of the asset attribute rule is "host name_IP_MAC_installable software category_system version".
[0071] Establish an asset information list according to the above-mentioned asset naming rules and attribute rules.
[0072] Start asset detection, obtain all inf...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap