Encryption key generation and encryption method, decryption key generation and decryption method
An encryption key and decryption key technology, applied to the usage of multiple keys/algorithms and key distribution, can solve problems such as the loss of meaning of data cracking, the complexity of encryption algorithms, and increase data security, so as to ensure performance and improve data security. The effect of cracking difficulty and increasing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
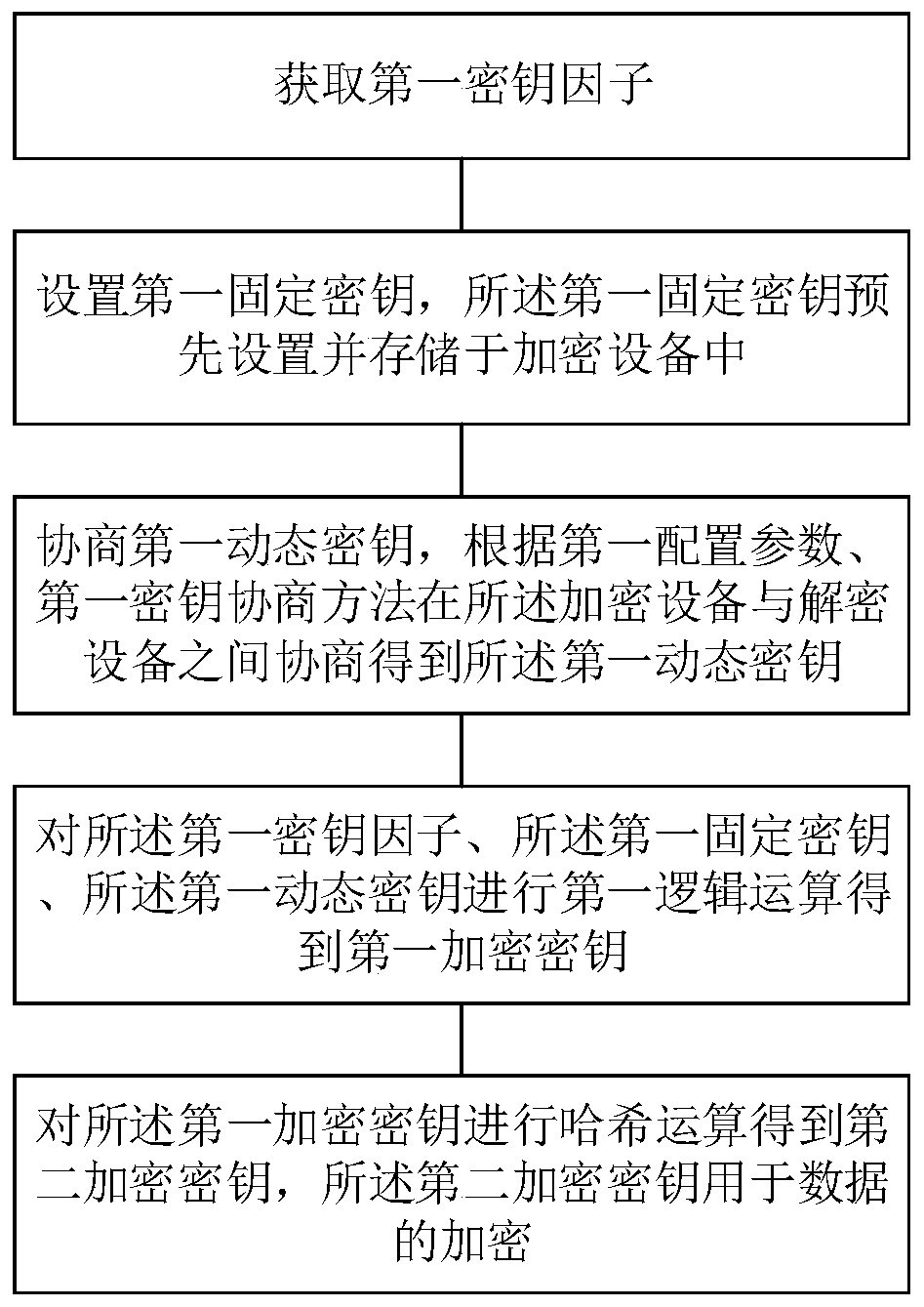
[0050] Data encryption can be seen everywhere. Common symmetric encryption or asymmetric encryption use fixed keys or regularly updated keys. Regardless of whether fixed keys or regularly updated keys are used, there are cases where a large number of data packets use the same key. In order to increase the security of data transmission and reduce the risk of being cracked, in addition to optimizing the encryption algorithm and increasing the difficulty of cracking, it is also necessary to increase the cost of cracking. For example, the cost of cracking a packet of data is 100 yuan, and the average income of cracking a packet of data It is 1 yuan. If you use a fixed key, cracking a packet of data is equivalent to cracking all the data. The cost of cracking is only 100 yuan, and the income is 1*n, where n is the number of data packets. As long as the obtained data packets are greater than 100 is profitable. However, if each packet of data is encrypted with a different key, the co...
Embodiment 2
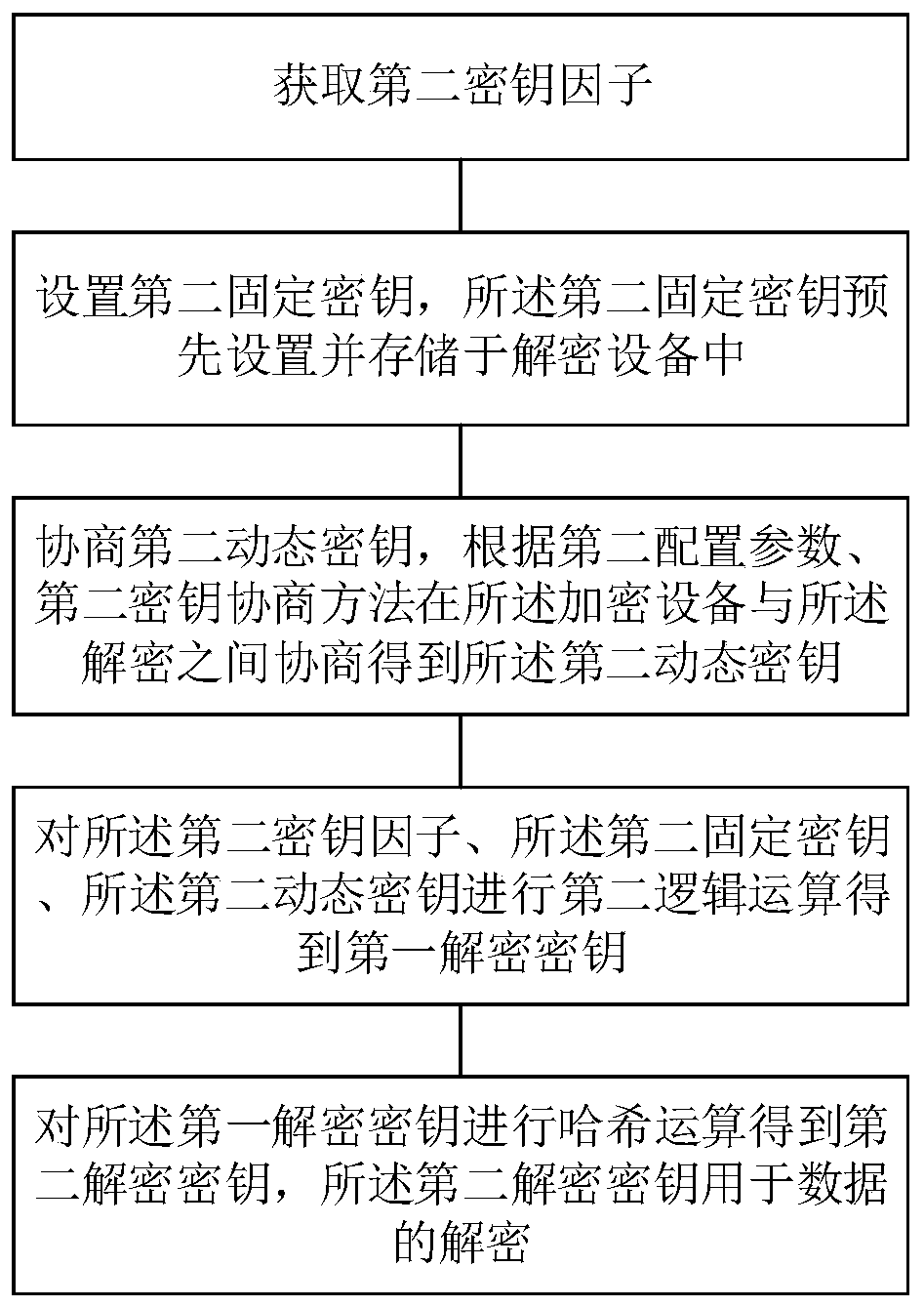
[0095] On the basis of the first embodiment above, please refer to figure 2 , figure 2 It is a schematic flowchart of a method for generating a decryption key provided by an embodiment of the present invention. This embodiment provides a decryption key generation method including:
[0096] Step 1, obtaining the second key factor;
[0097] Step 2, setting a second fixed key, which is preset and stored in the decryption device;
[0098] Step 3, negotiating the second dynamic key, and obtaining the second dynamic key through negotiation between the encryption device and the decryption method according to the second configuration parameter and the second key negotiation method;
[0099] Step 4, performing a second logical operation on the second key factor, the second fixed key, and the second dynamic key to obtain the first decryption key;
[0100] Step 5: Perform a hash operation on the first decryption key to obtain a second decryption key, and the second decryption key i...
Embodiment 3
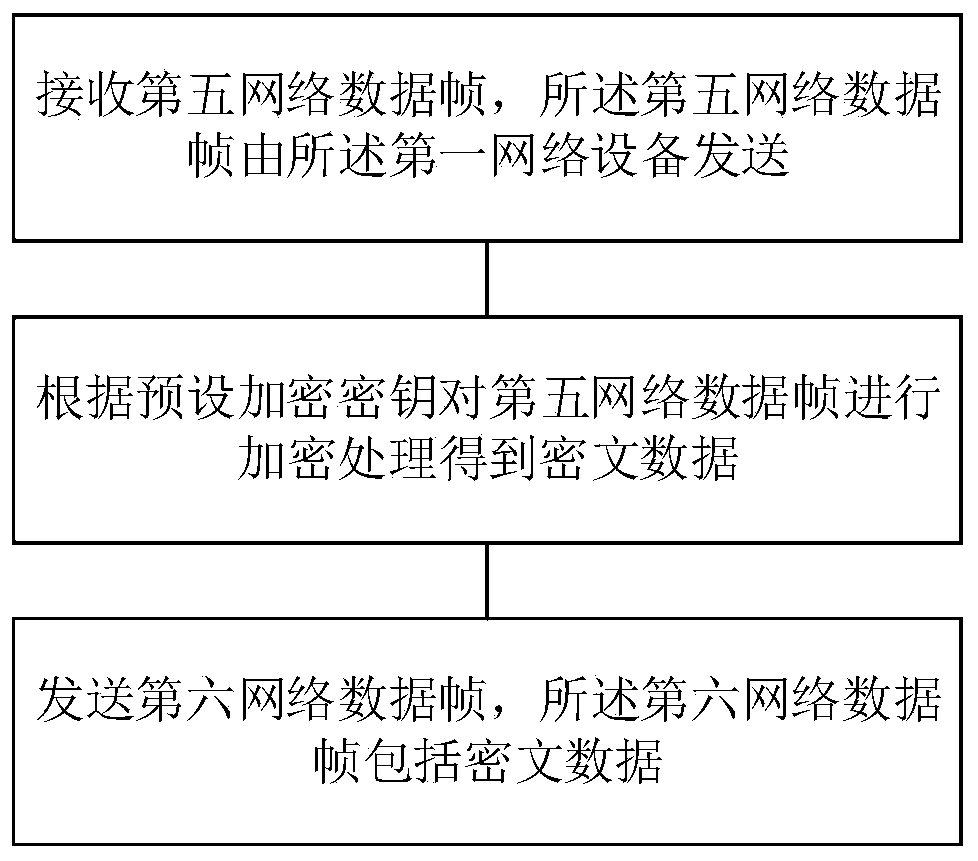
[0114] On the basis of the first embodiment above, please refer to image 3 , Figure 4 , image 3 is a schematic flowchart of a data encryption method provided by an embodiment of the present invention, Figure 4 It is a schematic diagram of the connection relationship between devices in a data encryption method and a data decryption method provided by an embodiment of the present invention. This embodiment provides a data encryption method, including a connected first network device and an encryption device, and the execution of the data encryption method on the encryption device includes:
[0115] Step 1, receiving the fifth network data frame, the fifth network data frame is sent by the first network device;
[0116] Step 2. Encrypt the fifth network data frame according to the preset encryption key to obtain ciphertext data;
[0117] Step 3. Send a sixth network data frame, where the sixth network data frame includes ciphertext data.
[0118] Specifically, see also ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com