IoT security verification framework based on 5G network slice and service method thereof
A network slicing and security verification technology, applied in the Internet of Things architecture and its services, can solve the problems of neglecting to establish secure communication, unable to meet QoS and security, and achieve the effect of ensuring anonymity and authenticity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
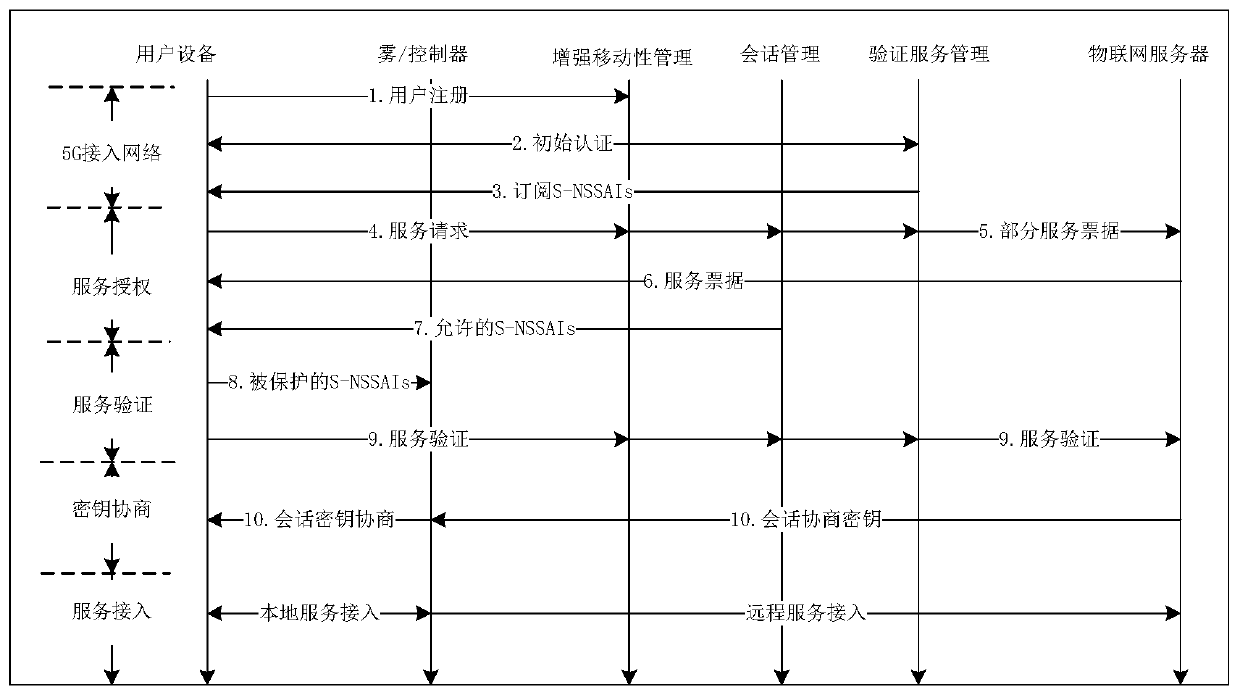
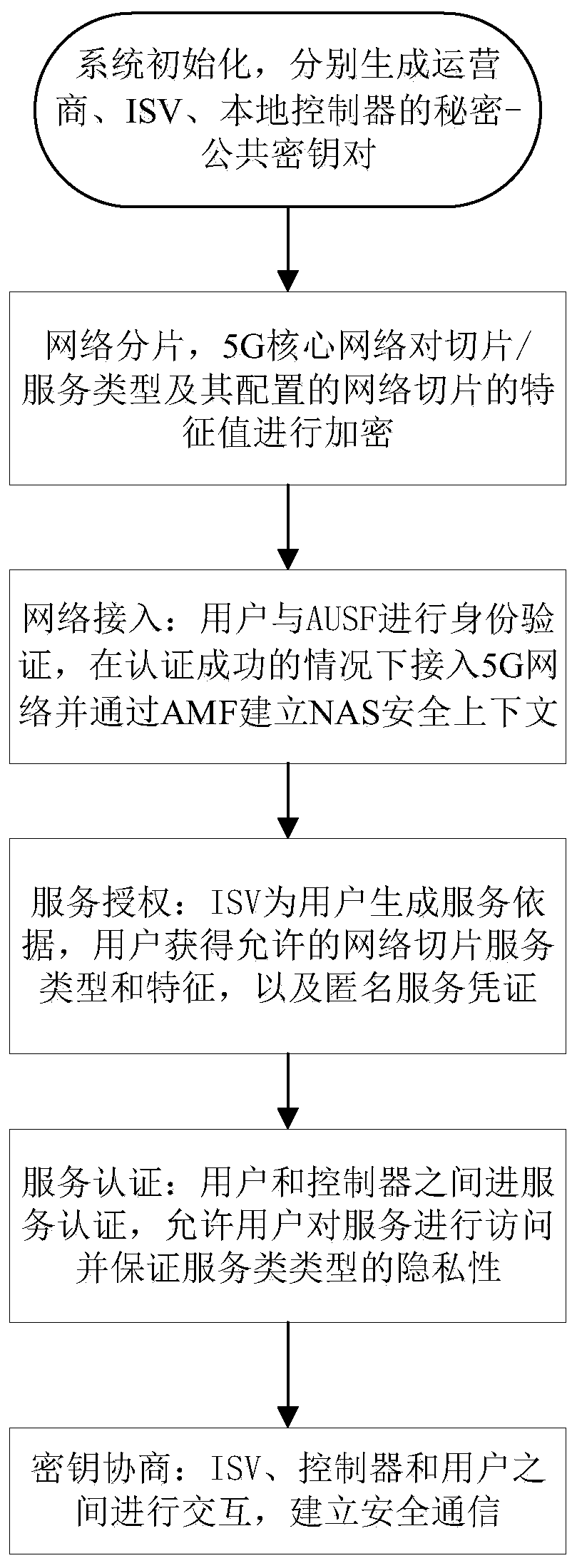
[0017] The technical solution of the present invention will be further described below in conjunction with the accompanying drawings. It should be understood that the embodiments provided below are only intended to disclose the present invention in detail and completely, and fully convey the technical concept of the present invention to those skilled in the art. The present invention can also be implemented in many different forms, and does not Limited to the embodiments described herein. The terms used in the exemplary embodiments shown in the drawings do not limit the present invention.
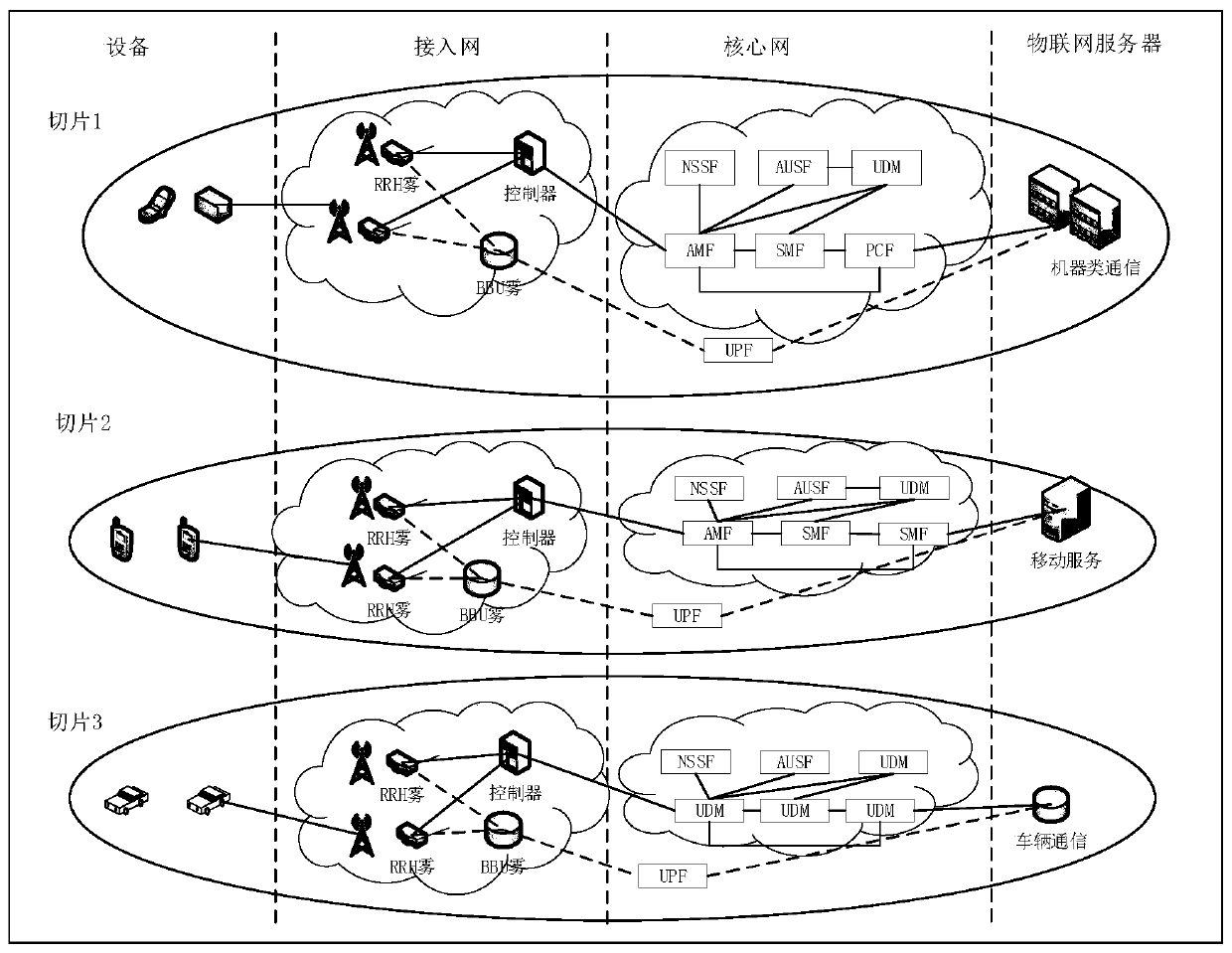
[0018] In order to support different IoT services in the 5G network, the present invention introduces a network slicing architecture, which realizes the separation and prioritization of resources on public infrastructure, including network functions, computing resources, virtual network functions and wireless access technology settings. 5G communication devices are divided into different n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com