Automatic vulnerability quantitative evaluation method and system
A quantitative assessment and vulnerability technology, applied in the field of information security, can solve problems such as increased risk value, difficulty in updating CVSS scoring in a timely manner, and difficulty in exploiting vulnerabilities, and achieve the effect of simplifying the scoring steps and reducing the impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
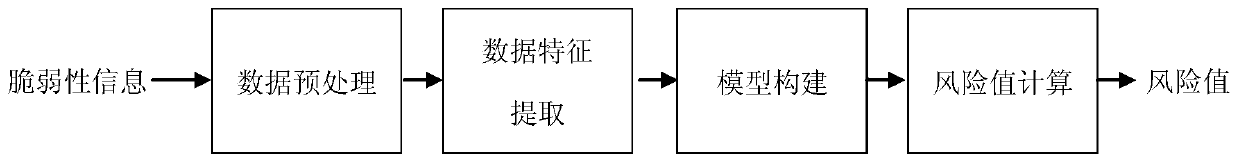
[0026] like figure 1 As shown, this technique is a method for risk quantification of system vulnerability automation. The specific implementation is as follows:
[0027] 1) Data preprocessing
[0028] First conduct an online search for a system vulnerability and collect relevant results. Usually, the results contain many web pages, and similar networks need to be clustered as well. For example, if you search for information on the vulnerability CVE-2019-9601, the returned results include 120 webpage information, and some of them are simply forwarded. Therefore, you need to delete the repeated results to get the number of different webpages.
[0029] In order to delete duplicate web pages, it is necessary to compare their similarities. Use the N-Gram similarity comparison method. For each web page, use n words to decompose the content. Then calculate the hash value of n words. Therefore, for each web page, a series of hash values can be obtained. Therefore, by calcula...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com