Detection method, system and device for mining byvirtual currency and storage medium
A virtual currency and detection method technology, applied in the field of malicious attack detection, can solve problems such as unsatisfactory use effect, unsolvable, increase of mining pools and mining programs, etc., to achieve better detection effect and easy engineering implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
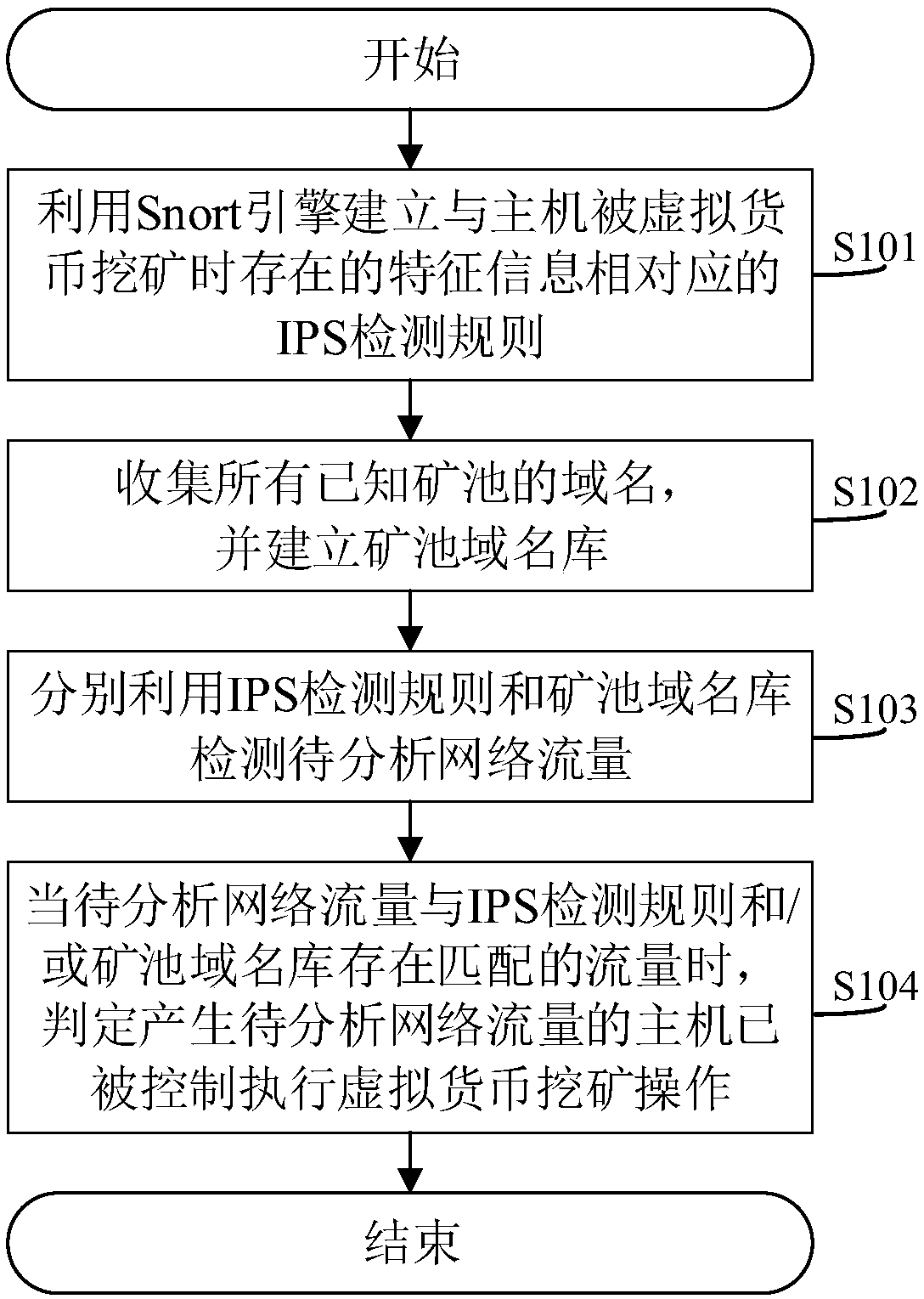
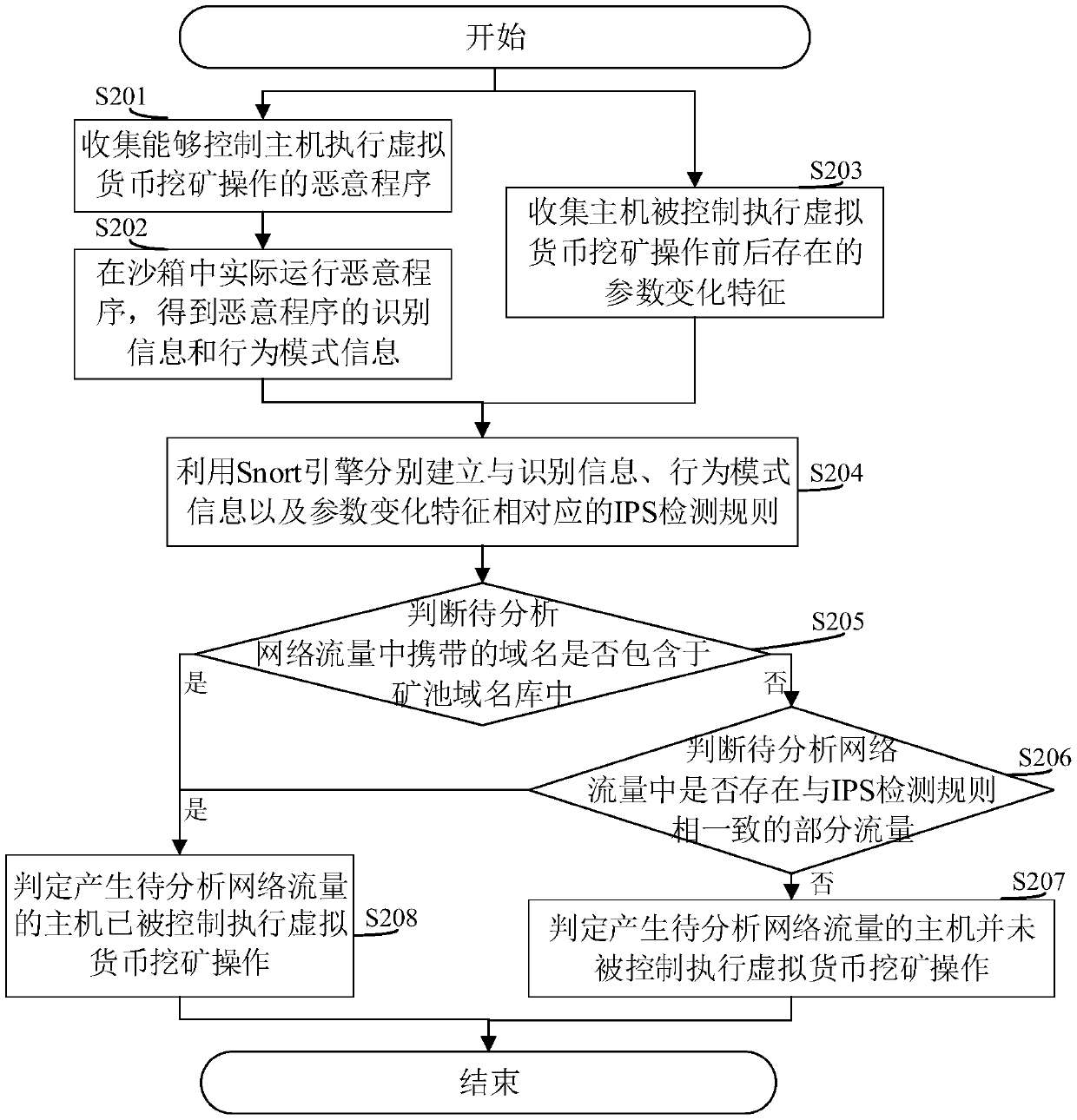
[0052] The core of this application is to provide a detection method, system, device and computer-readable storage medium for being mined by virtual currency. On the basis of using the mining pool domain name database to detect the domain name, it also uses the Snort engine to build and control the host The IPS detection rules corresponding to the feature information that exists when performing virtual currency mining operations, that is, use the IPS detection rules and the mine pool domain name database to detect and analyze network traffic at the same time. The IPS detection rules based on rule matching can detect and analyze various The detection of content effectively makes up for the shortcoming that the content must be known when only using the domain name library of the mining pool. The IPS detection rules constructed by the Snort engine can dig out the common points hidden behind the data from the feature information, making the mined The detection effect of behavior is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com