Method and apparatus for protecting device
A technology for protecting equipment and equipment, applied in the direction of digital data protection, computer security devices, instruments, etc., can solve problems such as programming errors, lack, and inability to fully protect computers, and achieve the effect of reducing security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
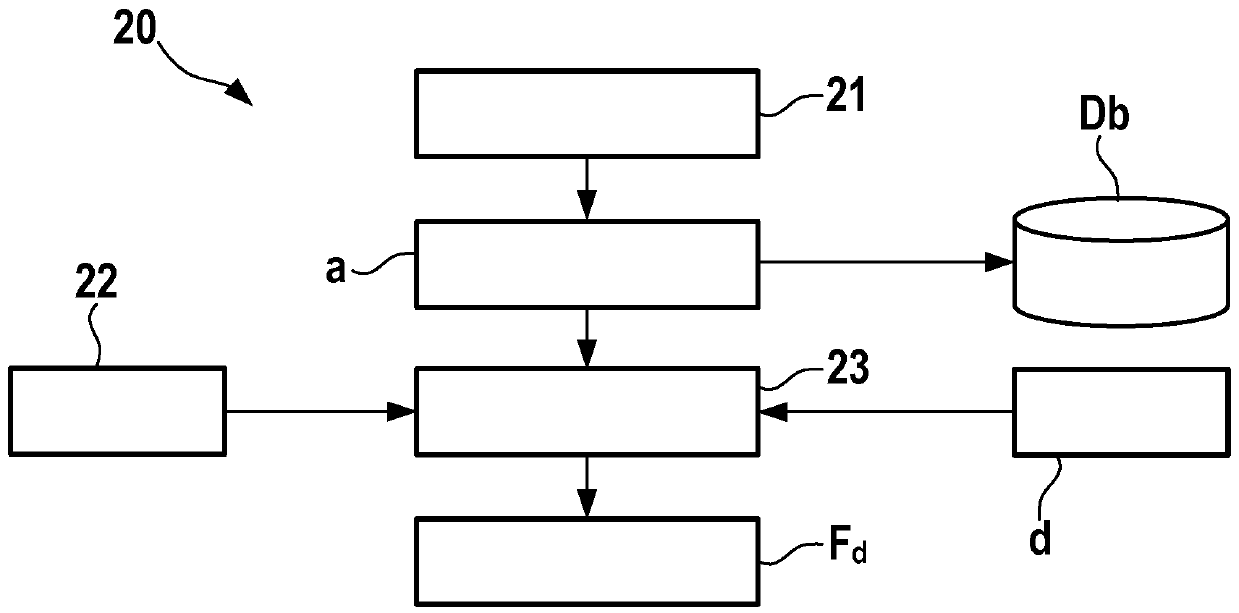
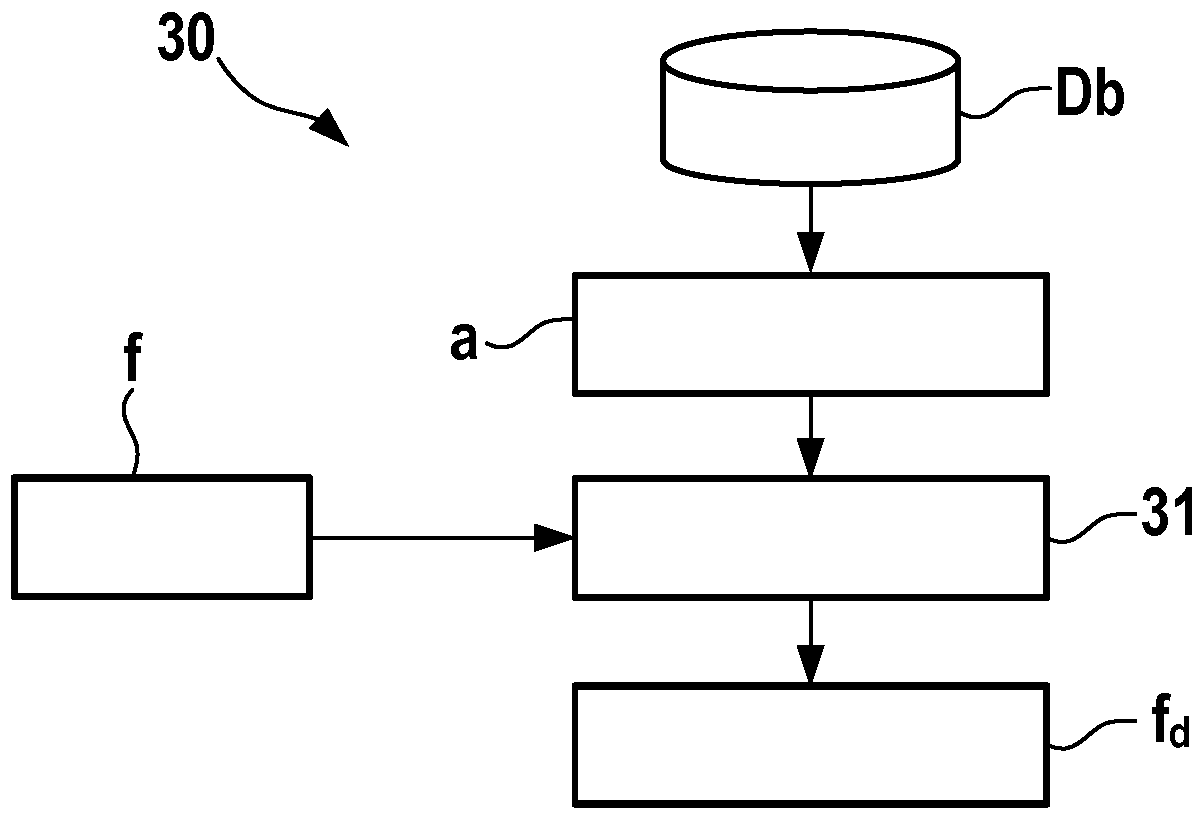
[0017] In the following, the term "file" is used in a broad sense for input data of networked devices. Examples of files are eg software updates, multimedia files or text files which may contain requirements for the device in question. In general, each file consists of header data and useful data. The useful data of the file is related to its actual content, such as images, movies or texts. The file's header contains its so-called metadata, such as the format of the file, the version of the tool used to create it, etc.
[0018] A fundamental aspect of the invention is to bind a given file to a determined device such that said file can only be correctly processed (ie read and interpreted) on that specified device. An overview of the method proposed for this is in figure 1 shown in .
[0019] For simplicity, a prototype implementation of the concept is now illustrated based on a file system executable with user privileges (Filesystem in Userspace, FUSE). This principle can ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com