Mimicry defense system based on certificate identity authentication and certificate issuing method
A technology of certificate issuance and defense system, which is applied in the field of mime defense system and certificate issuance based on certificate identity authentication, which can solve the problems of incomprehensibility and issuance, and achieve the effect of high security and high security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The scheme will be further described and explained below in conjunction with the accompanying drawings.
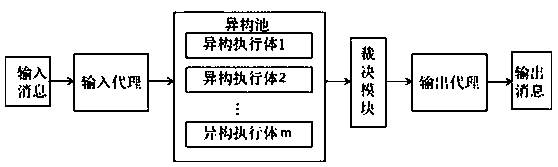
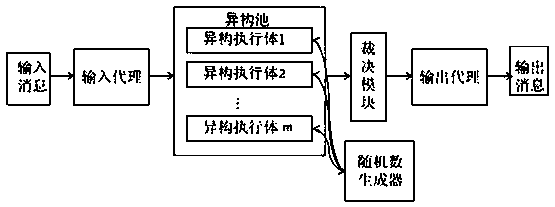
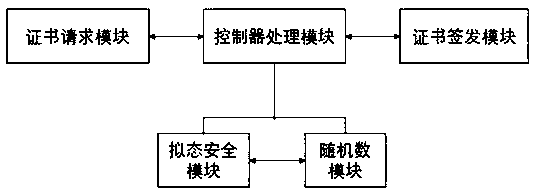
[0041]as attached figure 2 And attached image 3 As shown, a mimetic defense system based on certificate identity authentication includes the underlying device that needs to install a certificate, an intermediate controller, and a certificate issuance center. The intermediate controller and the certificate issuance center each have a unique certificate, and the certificate stores its own public information. key, and the corresponding private key is kept privately by each device and is not disclosed to the public.
[0042] Devices are devices that need to access the network, such as routers, PCs, mobile phones, etc. The devices include a certificate request module, which is used to generate public-private key pairs, encrypt and decrypt, generate certificate request files, and install certificates.
[0043] Among them, the intermediate controller includes a control...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com