Cloud computing security data sharing method based on double-chain structure
A technology of secure data and chain structure, applied in the field of blockchain, can solve problems such as unreliability, privacy disclosure, and tediousness, and achieve the effect of real and more reliable data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] Blockchain is a new application model of computer technologies such as distributed data storage, point-to-point transmission, consensus mechanism, and encryption algorithm. Blockchain is essentially a decentralized database, which is a series of data blocks associated with each other using cryptographic methods. Each data block contains a batch of network transaction information to verify the validity of its information. .
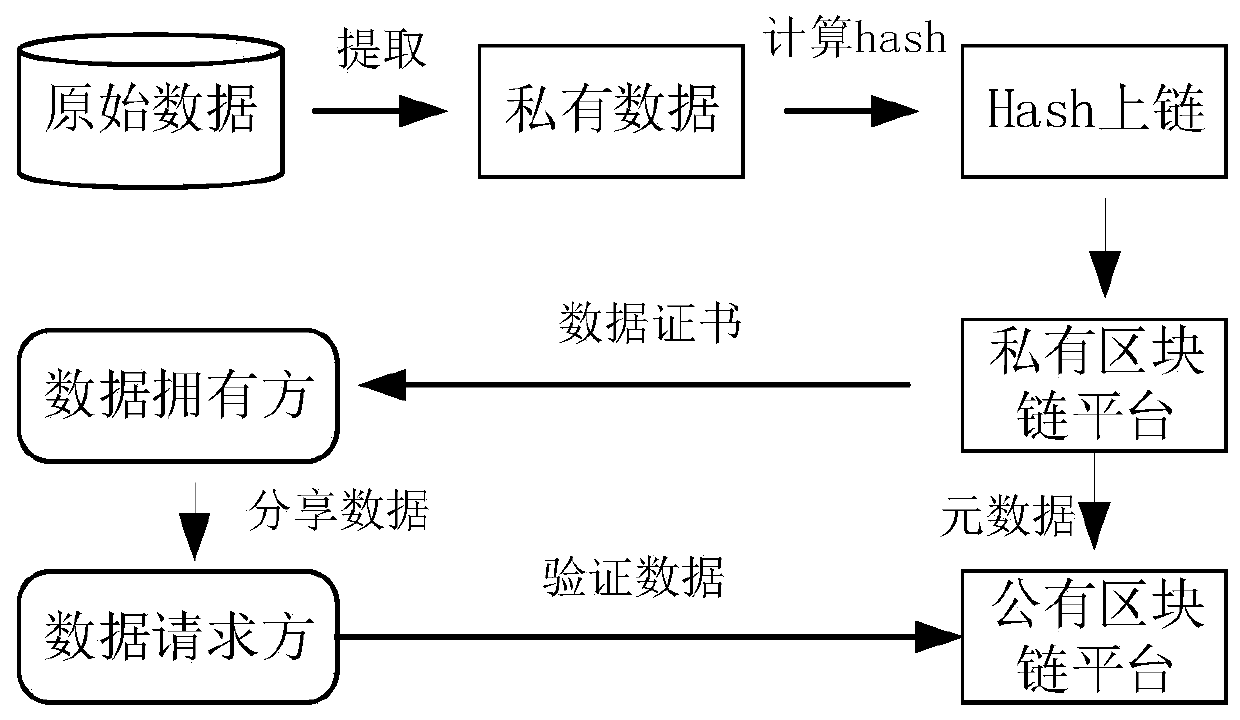
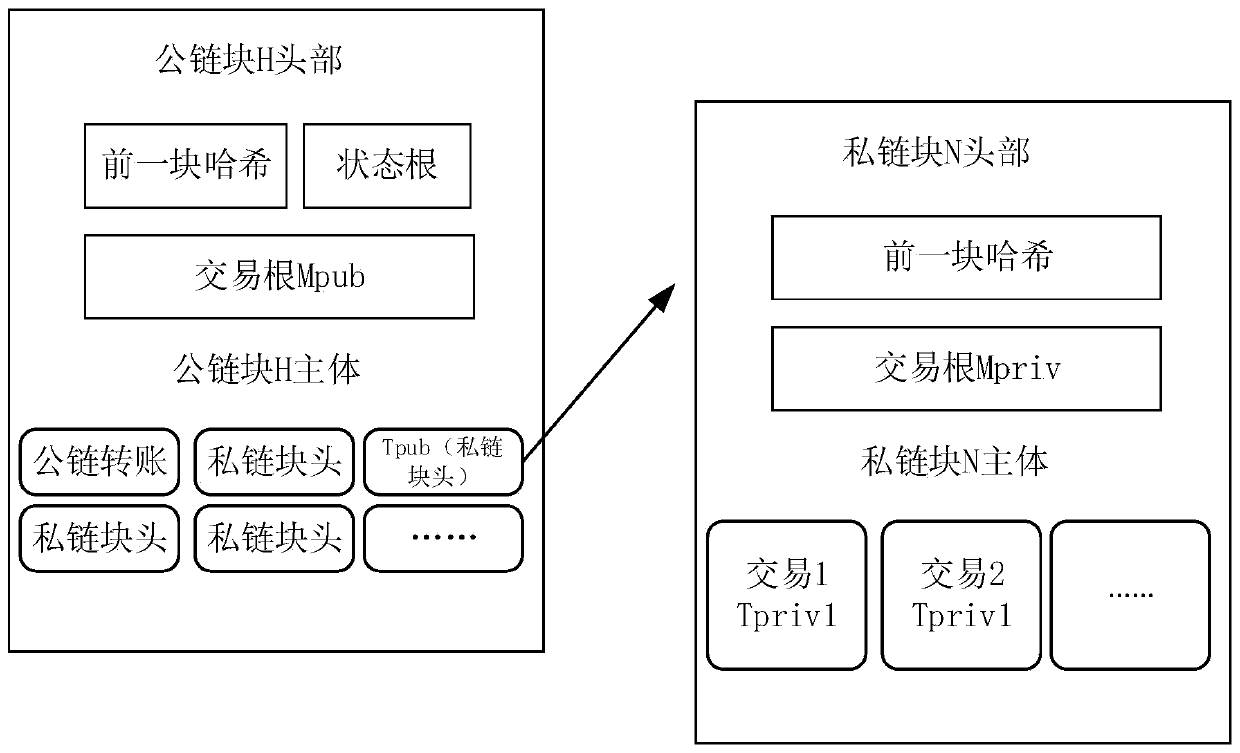
[0021] like figure 1 As shown, a cloud computing security data sharing method based on a double-chain structure adopts a "public chain + private chain" double-chain structure, and applies blockchain and data encryption technology to protect cloud platform data. The encryption system ensures that the ownership of the data is controlled in the hands of the data owner, and there will be no security risks such as tampering, illegal use, and large-scale leaks, and through the blockchain smart contract, the privacy of platform data during business proces...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com