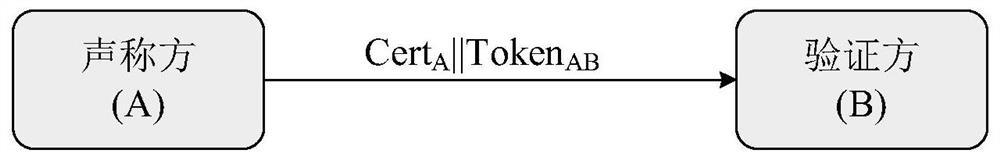A method and system for secure interconnection and intercommunication of pdf signed documents
A technology of interconnection and documentation, applied in the computer field, can solve problems such as data leakage, high implementation cost, and poor data consistency, and achieve the effects of reducing difficulty and cost, improving security, and achieving standardization and normativeness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
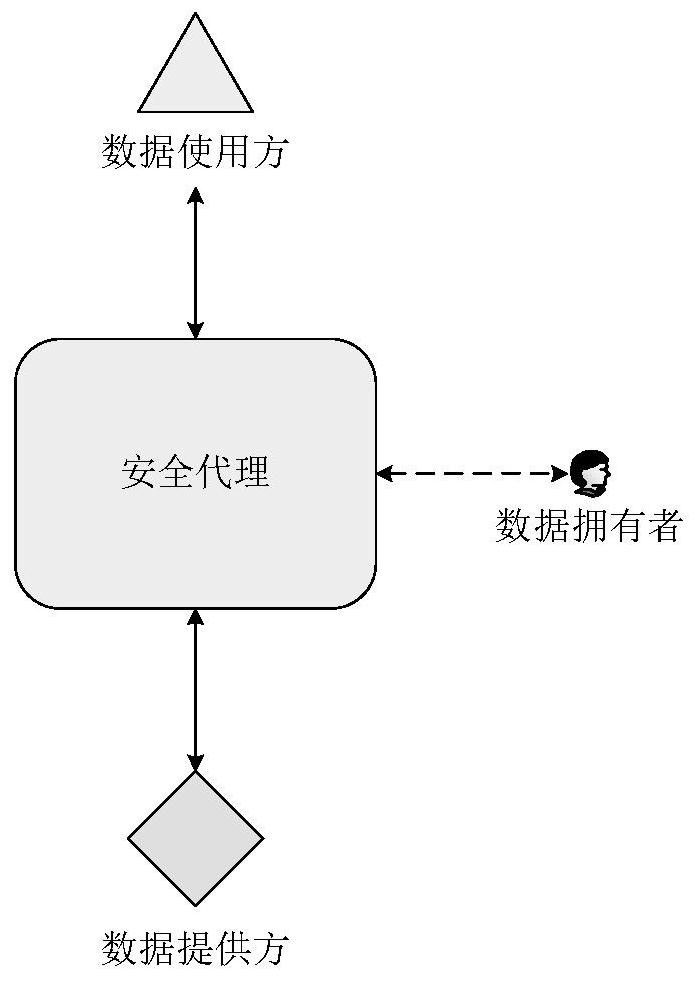
[0045] This embodiment is a PDF signature document interconnection system, including four components: a document provider, a document user, a document owner, and a security agent. See figure 1 , the functions of each part are:
[0046] The document user is the party who has the need to use the document;
[0047] The document provider generates and saves the document object, and is responsible for the access control of the document, that is, to decide whether to allow the response to the request of the document user. In real life, the generation, preservation and ownership of documents are not uniform. In other words, documents are not generated and kept by their owners;
[0048] The document owner is the actual owner of the document and has the right to decide the disposal of the document and its contents. The document provider or user can transmit or use the document only with the owner's consent and authorization.
[0049] The security agent is the security middleware in t...
Embodiment 2
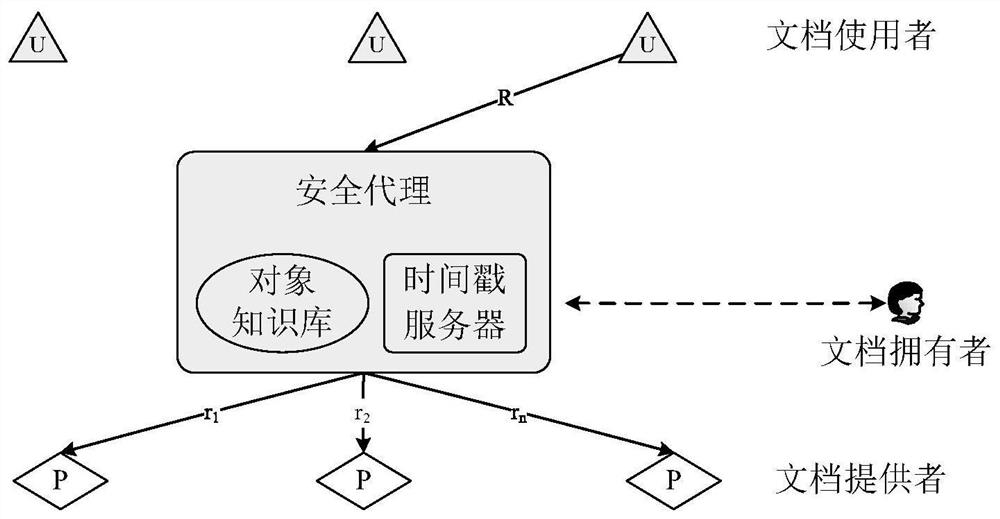
[0057] This embodiment is a method for interconnecting and interoperating PDF signature documents using the system of Embodiment 1, such as image 3 The specific process is as follows:
[0058] S1. When the document user needs to use the PDF document belonging to the owner but stored in the document provider (for example, the pharmacy needs to view the electronic prescription issued by the patient in the hospital), first generate a PDF document request R, and send the time to the security agent Stamp server request timestamp T R , then use the private key to pair R and T R Sign and get the signature value S U (R||T R ).
[0059] Among them, the content of R includes the request scope (such as "municipal hospital"), the object type (such as "electronic prescription") and the owner (such as "Li Jian"), and the form of R is a key / value pair (such as "hospital") = Municipal Second Hospital & Name = Li Jian & Data Type = Prescription Form") or a combination of keywords (such a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com