Malicious website recognition and interception technology based on communication operator network transmission layer
A technology for carrier networks and malicious URLs, applied in transmission systems, electrical components, etc., can solve problems that endanger users' online security, and achieve the effects of short feedback time, high efficiency and accuracy, and accurate collection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The present invention will be further explained below in conjunction with the accompanying drawings and specific embodiments.
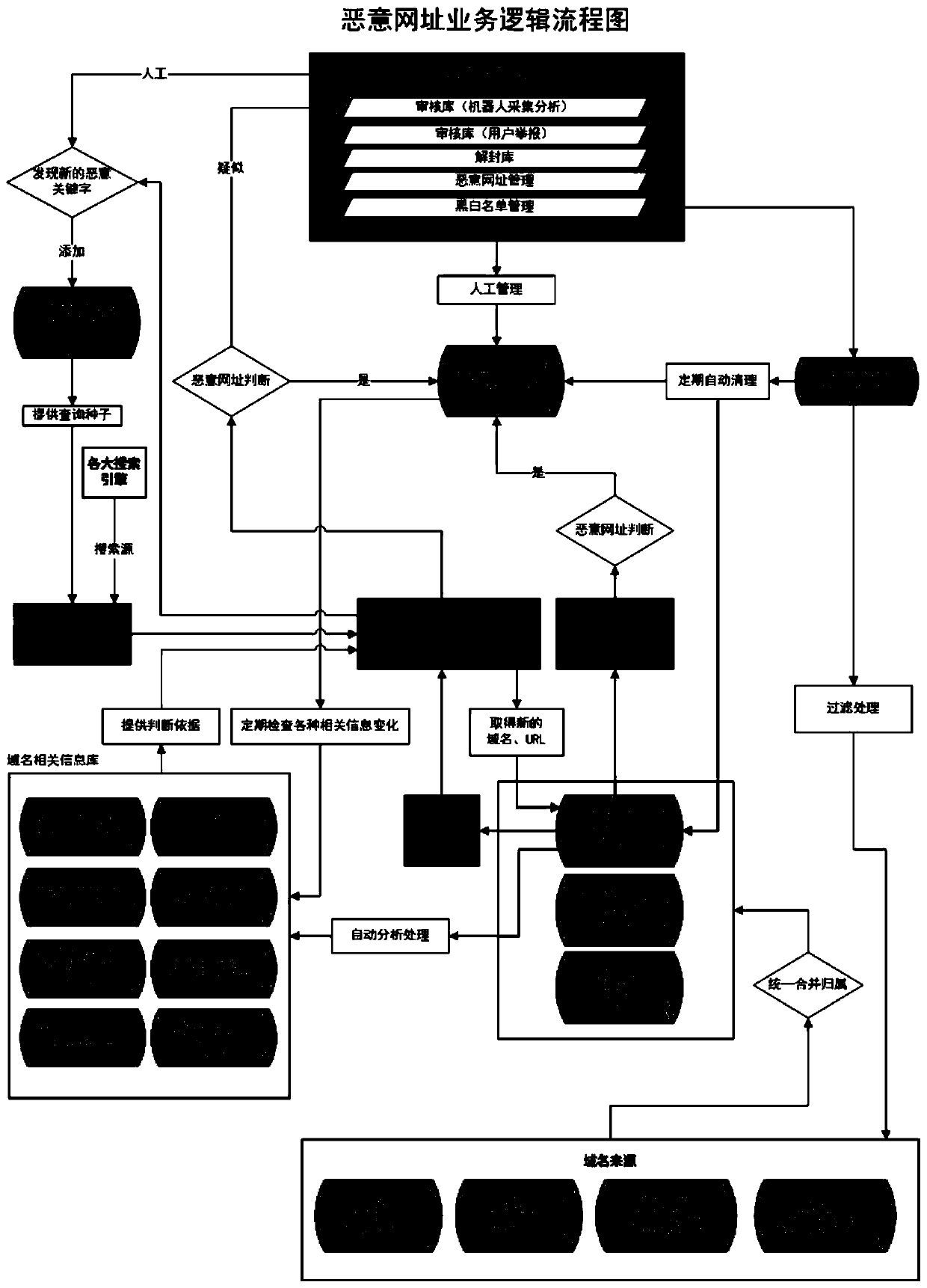
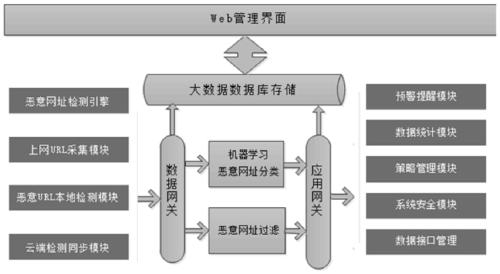
[0042] A malicious website identification and interception technology based on the network transport layer of a communication operator, including a system management center, a malicious website blocking engine, an intelligent detection engine, a website collection module, a cloud detection module, a data management module, a data statistics module, and a strategy It is composed of audit module and security management module; the management center provides interface-based integrated management and control channels for each engine module, configures and distributes a series of instructions so that each module can complete corresponding business operations;
[0043] Include the following steps:
[0044] Step 1. Establish a local malicious website library, support image recognition, keyword detection, and conduct Internet standard collection based on...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com