Network intrusion detection method, device and system and storage medium
A technology of network intrusion detection and detection nodes, which is applied in the field of network security, can solve the problems of detection engine missing reports, intrusion detection efficiency reduction, and inability to meet security detection, etc., to achieve the effect of improving detection efficiency and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
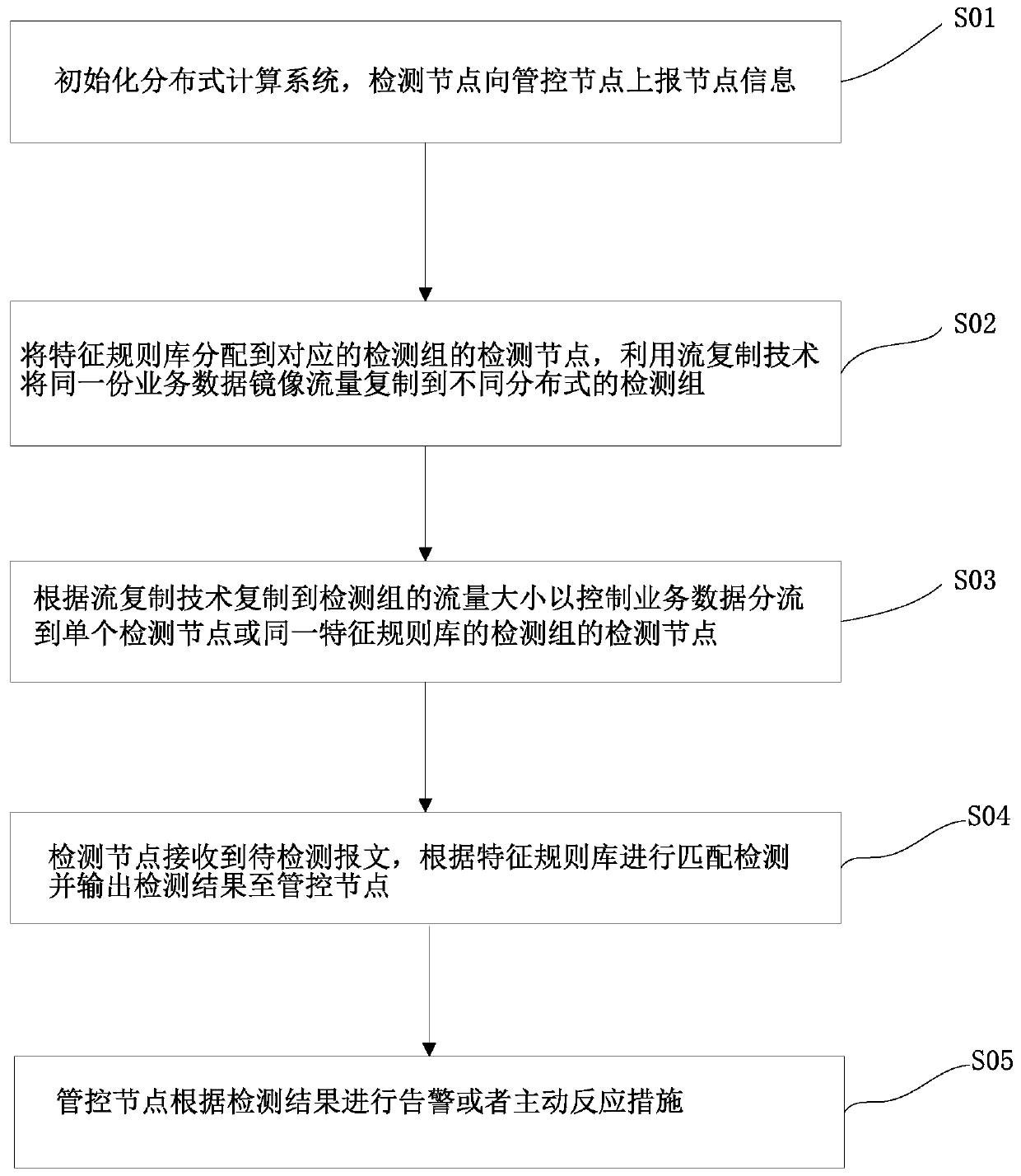
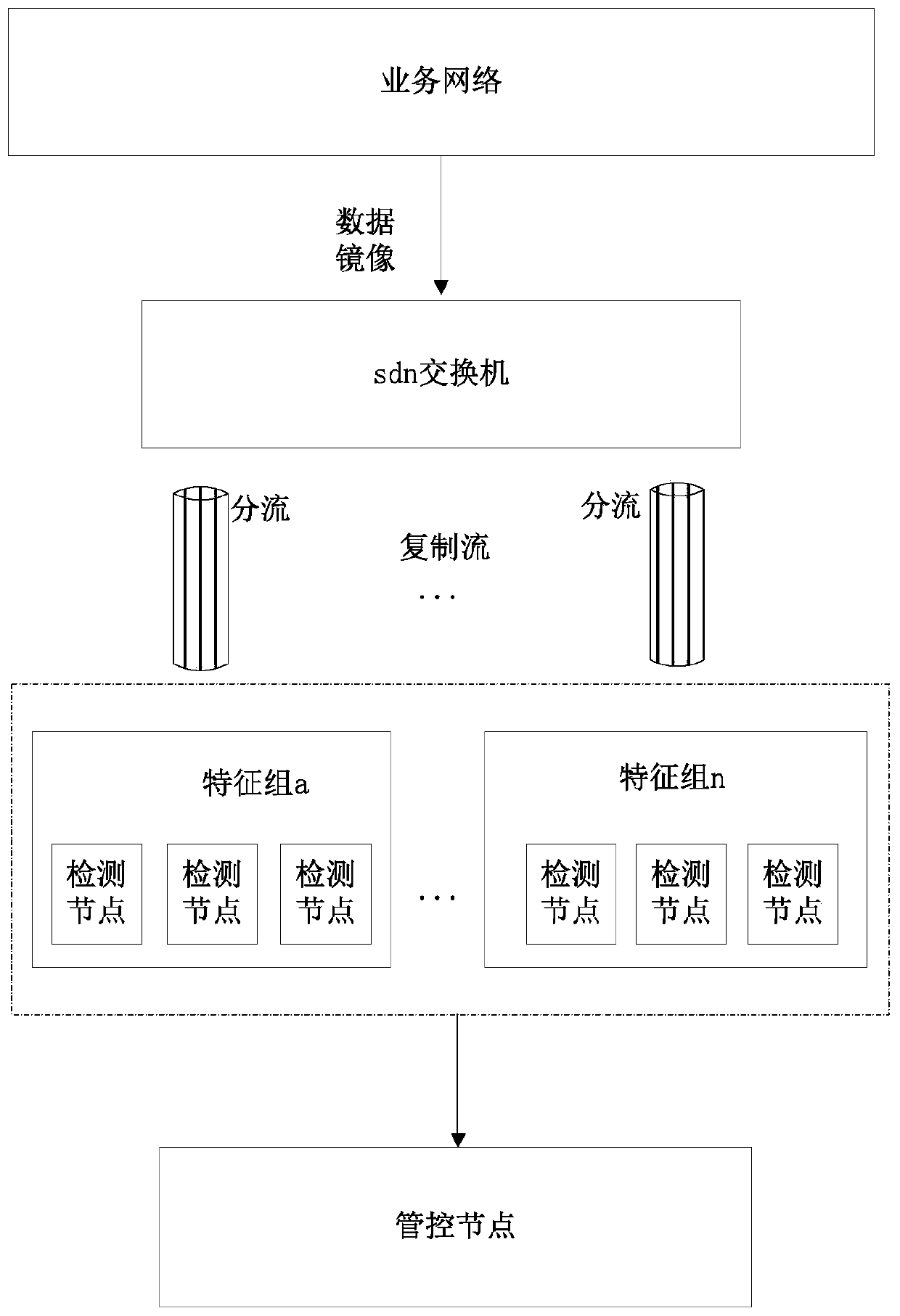
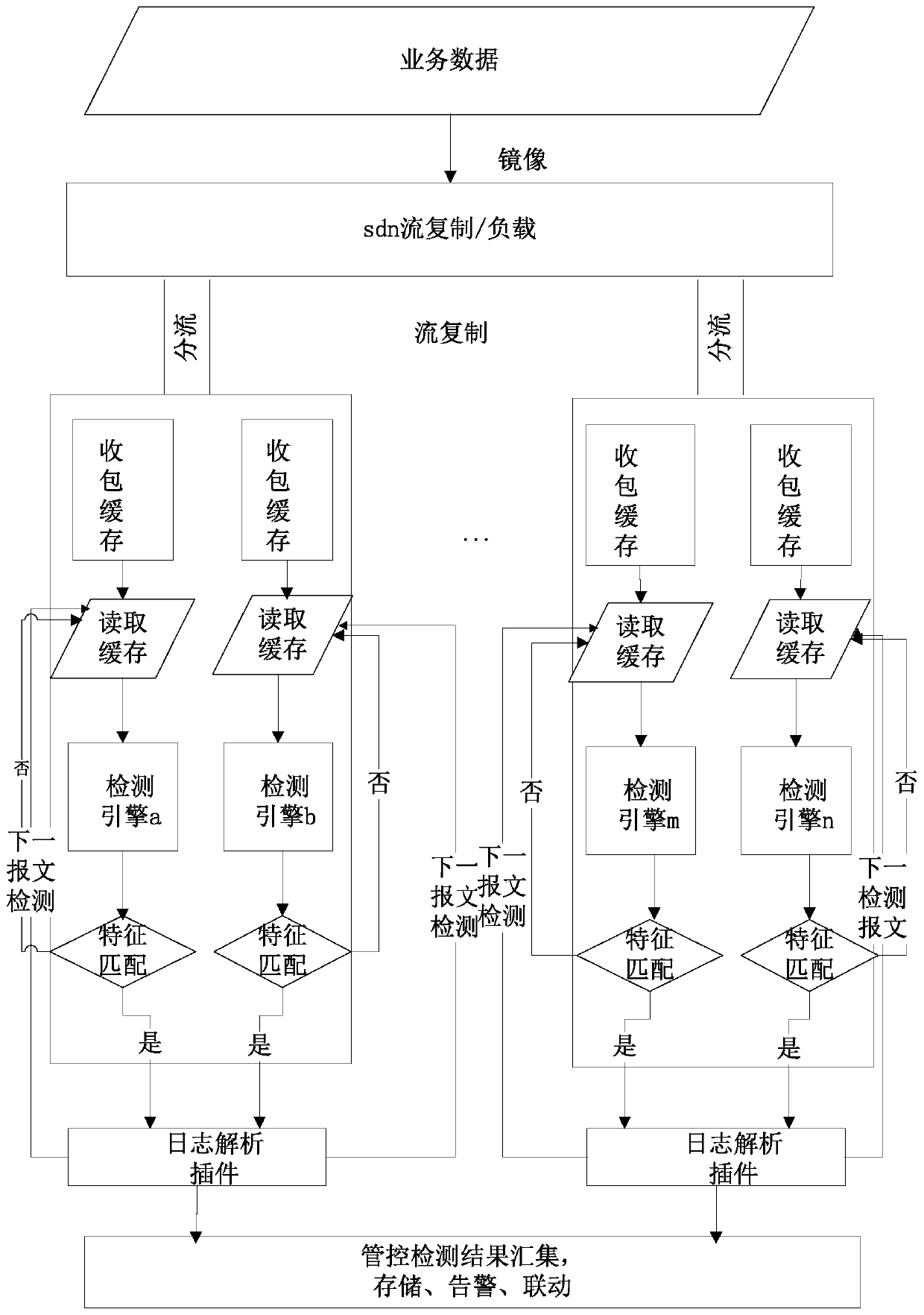
[0072] Embodiment two: refer to Figure 4 , the embodiment of the present invention discloses a network intrusion detection device, the network intrusion detection device includes: an initialization module 10, a distribution module 20, a replication module 30, a calculation module 40, a distribution module 50, a detection module 60 and an addition module 70, the initialization Module 10 is used to initialize the distributed computing system, distribution module 20 is used to assign the feature rule library to the corresponding detection group; copy module 30 is used to copy the same business data mirroring flow to different distributed Detection group; Calculation module 40 is used to calculate the traffic size of the business data copied by sdn exchange flow replication technology mirroring traffic; Distribution module 50 distributes business data to a single detection node or detection group according to the traffic size; Detection module 60 is used for according to character...
Embodiment 3
[0075] Embodiment 3: This embodiment discloses a network intrusion detection system, which includes a storage device and a processor. Wherein, the storage device stores program codes for implementing corresponding steps in the network detection method according to the embodiment of the present invention. The processor is used to run the program code stored in the storage device to execute the corresponding steps of the network detection method according to the embodiment of the present invention, and to realize the corresponding modules in the network detection device according to the embodiment of the present invention.
Embodiment 4
[0076] Embodiment 4: According to a network intrusion detection device, in this embodiment, a storage medium is also provided, on which program instructions are stored, and when the program instructions are run by a computer or a processor, they are used to execute the implementation of the present invention. The corresponding steps of the network detection method of the example are used to realize the corresponding modules in the code review device according to the embodiment of the present invention. The storage medium may include, for example, a memory card, a hard disk, a read-only memory (ROM), an erasable programmable read-only memory (EPROM), a portable compact disc read-only memory (CD-ROM), a USB memory, or any combination of the above-mentioned storage media . The computer readable storage medium can be any combination of one or more computer readable storage medium.
[0077] According to an embodiment of the present invention, a computer program is also provided, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com