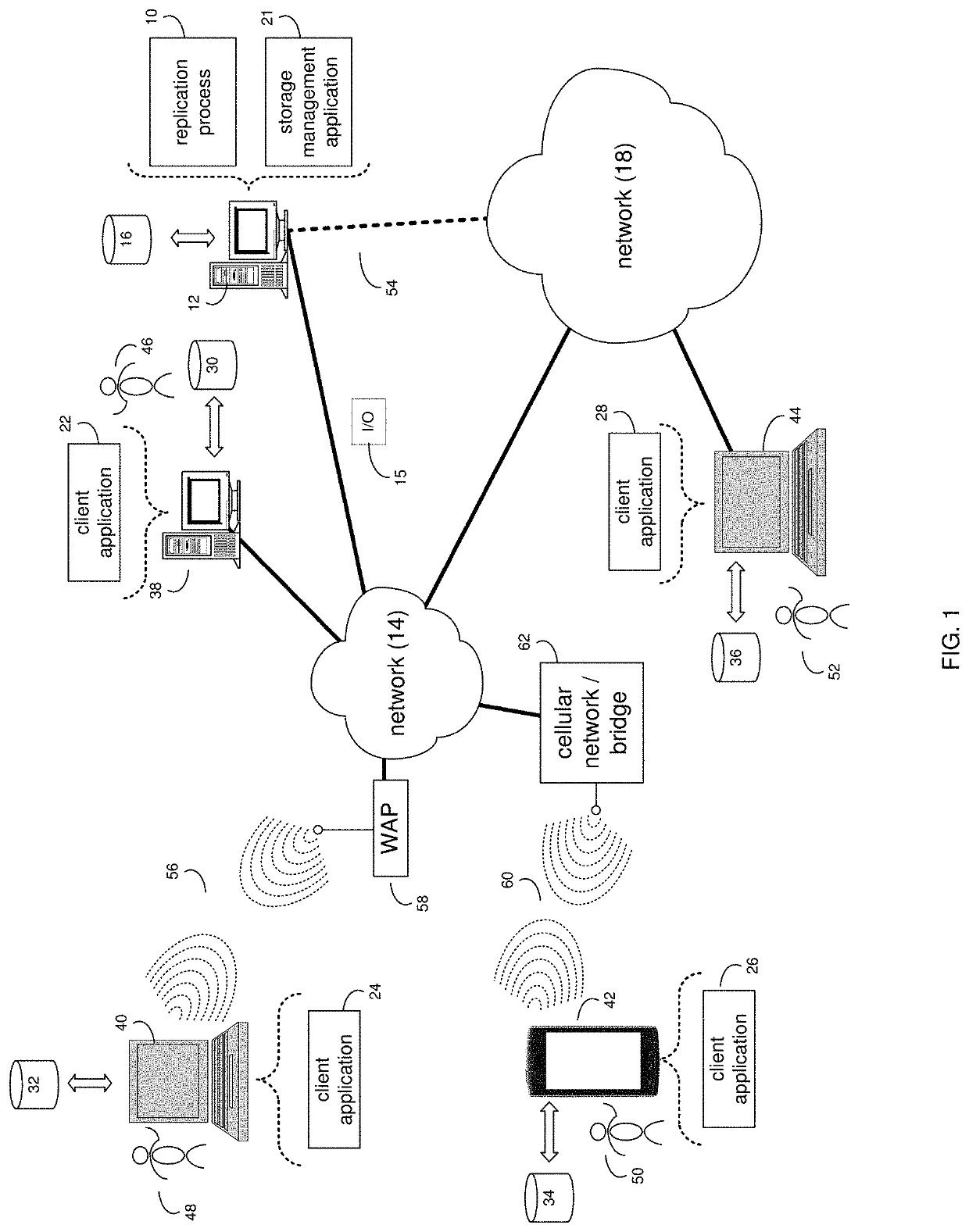
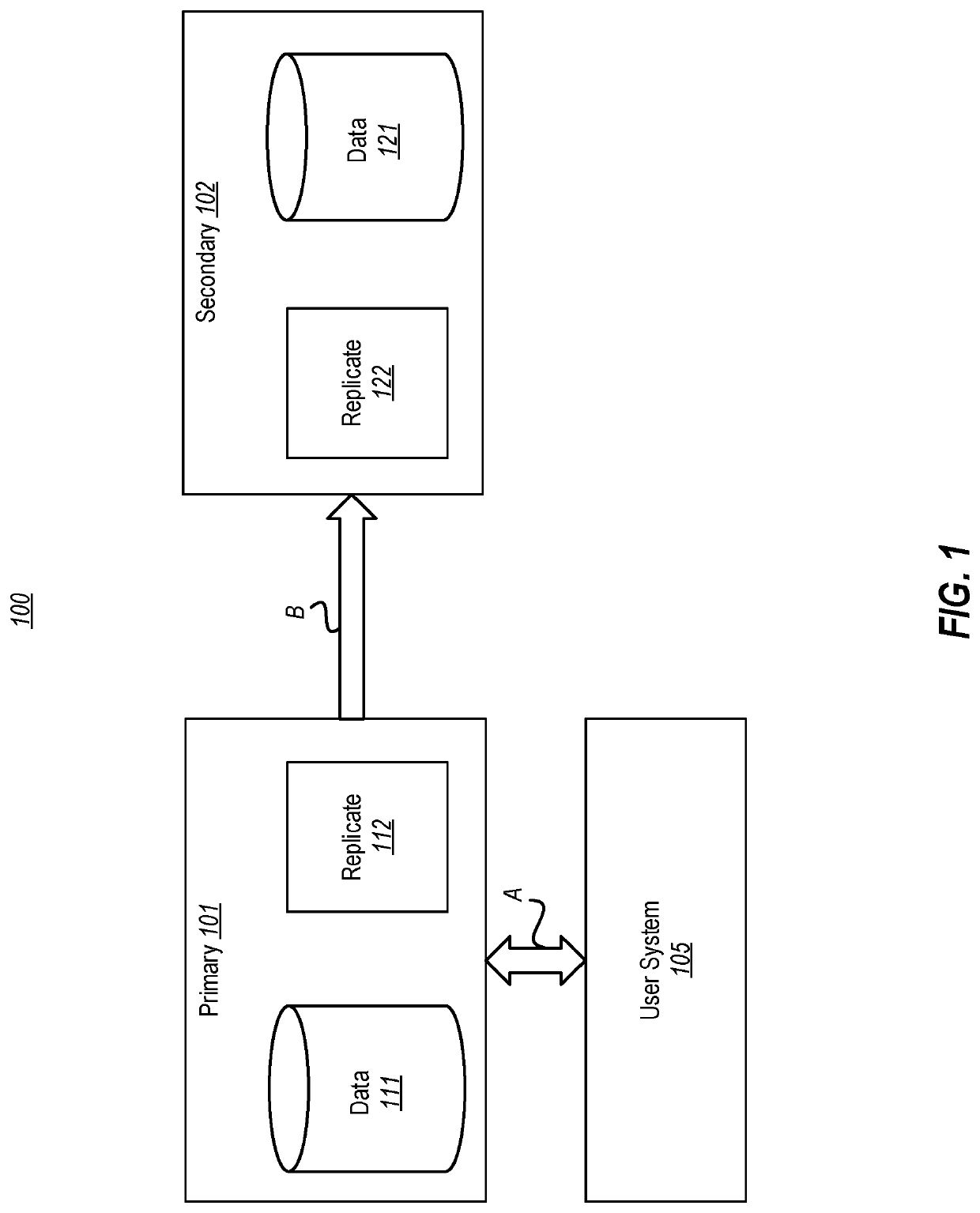
Patents
Literature
54 results about "Replication (computing)" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
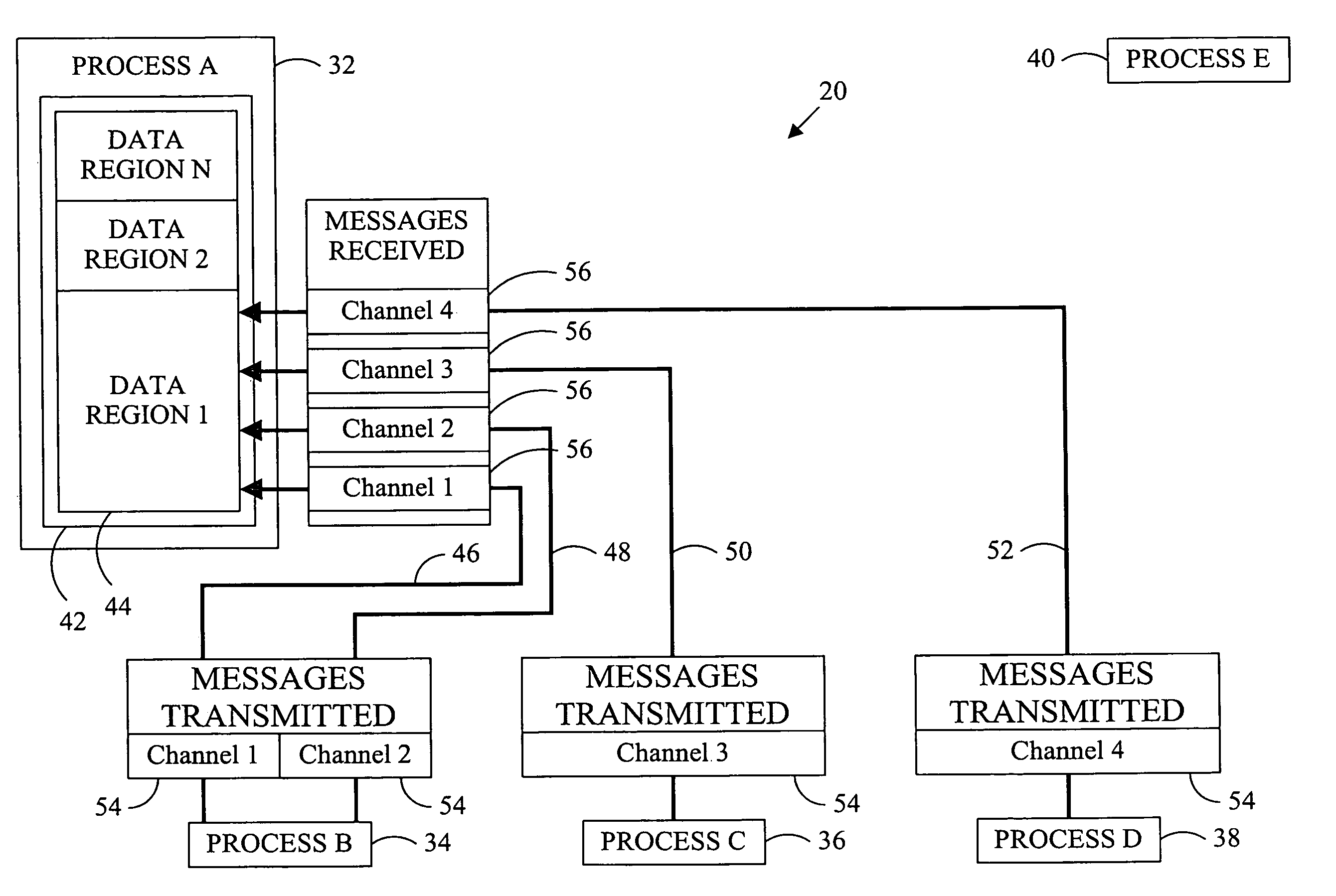
Replication in computing involves sharing information so as to ensure consistency between redundant resources, such as software or hardware components, to improve reliability, fault-tolerance, or accessibility.
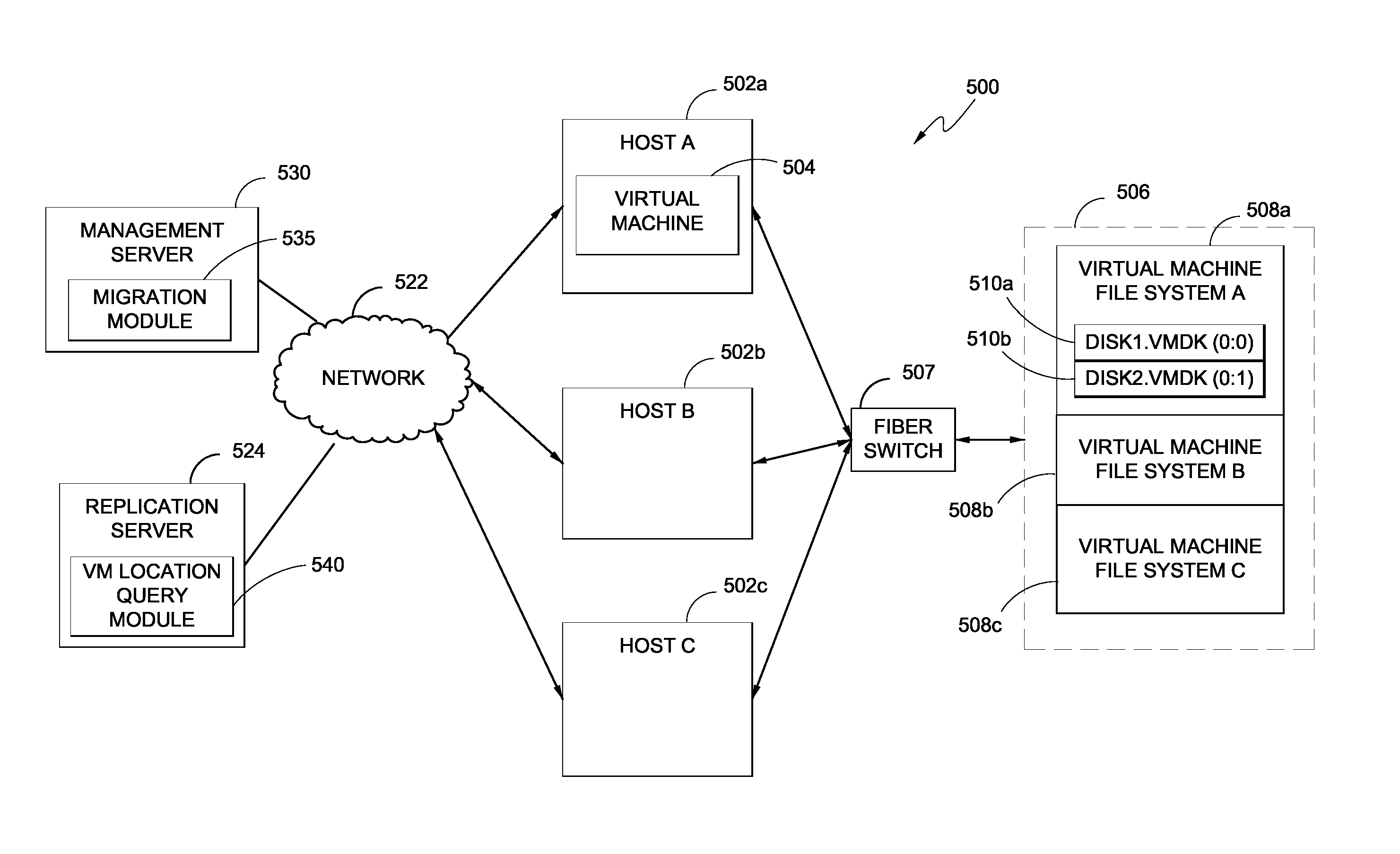
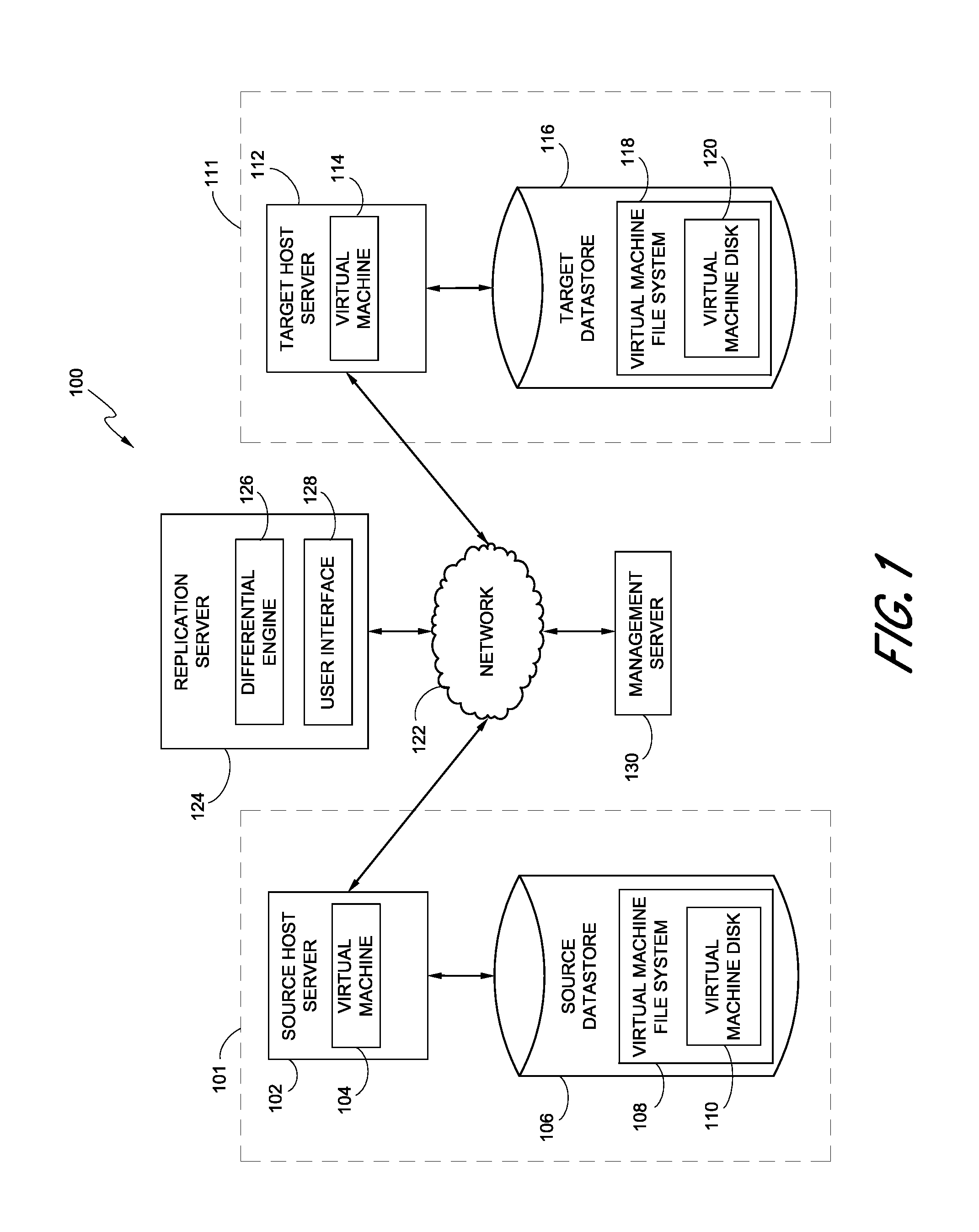
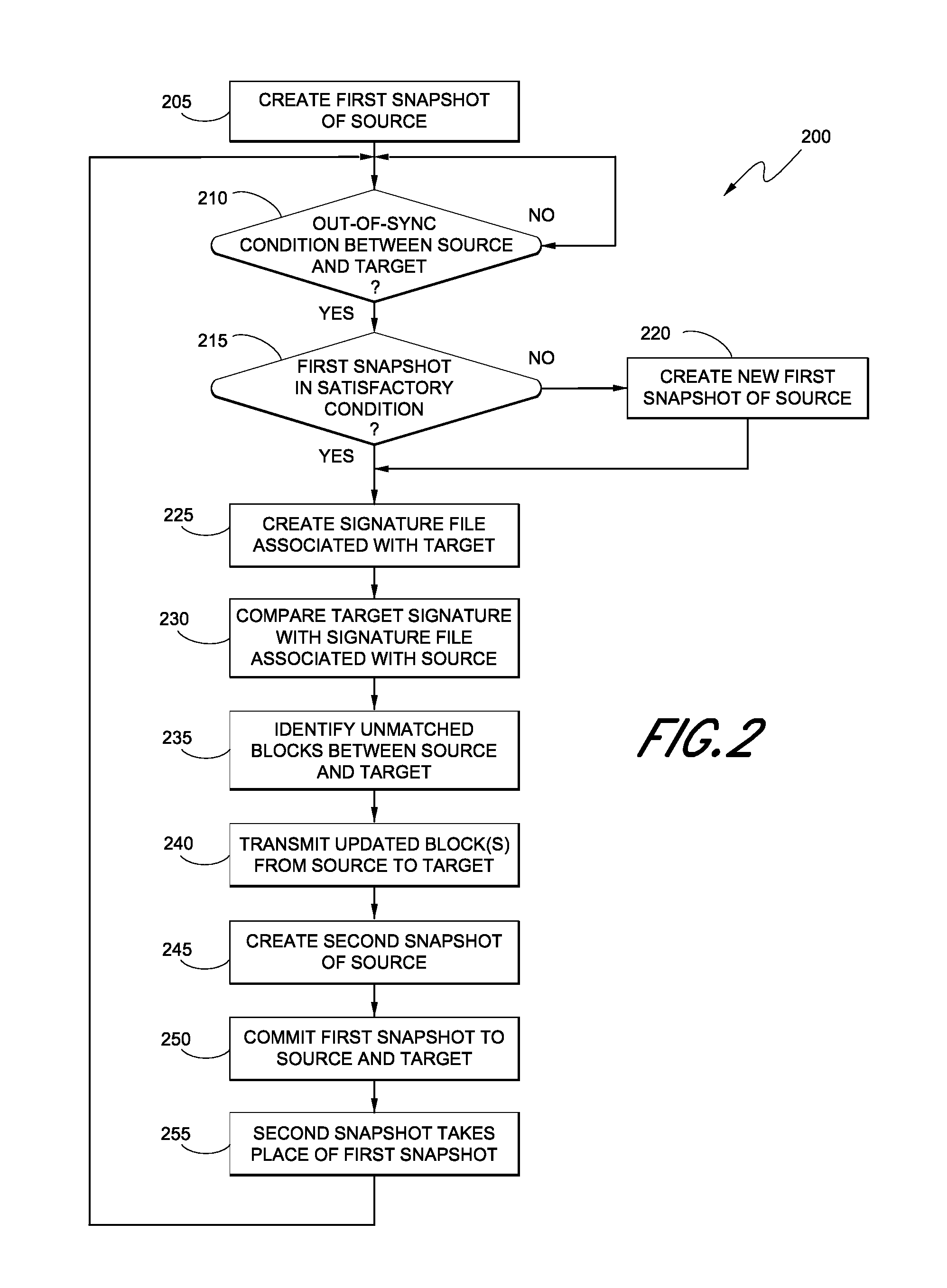
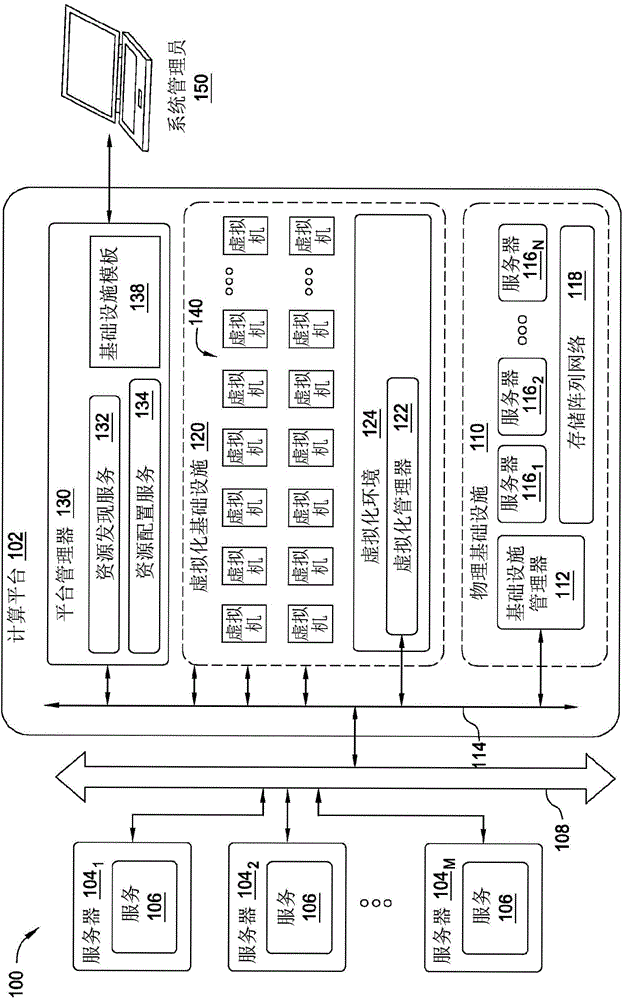
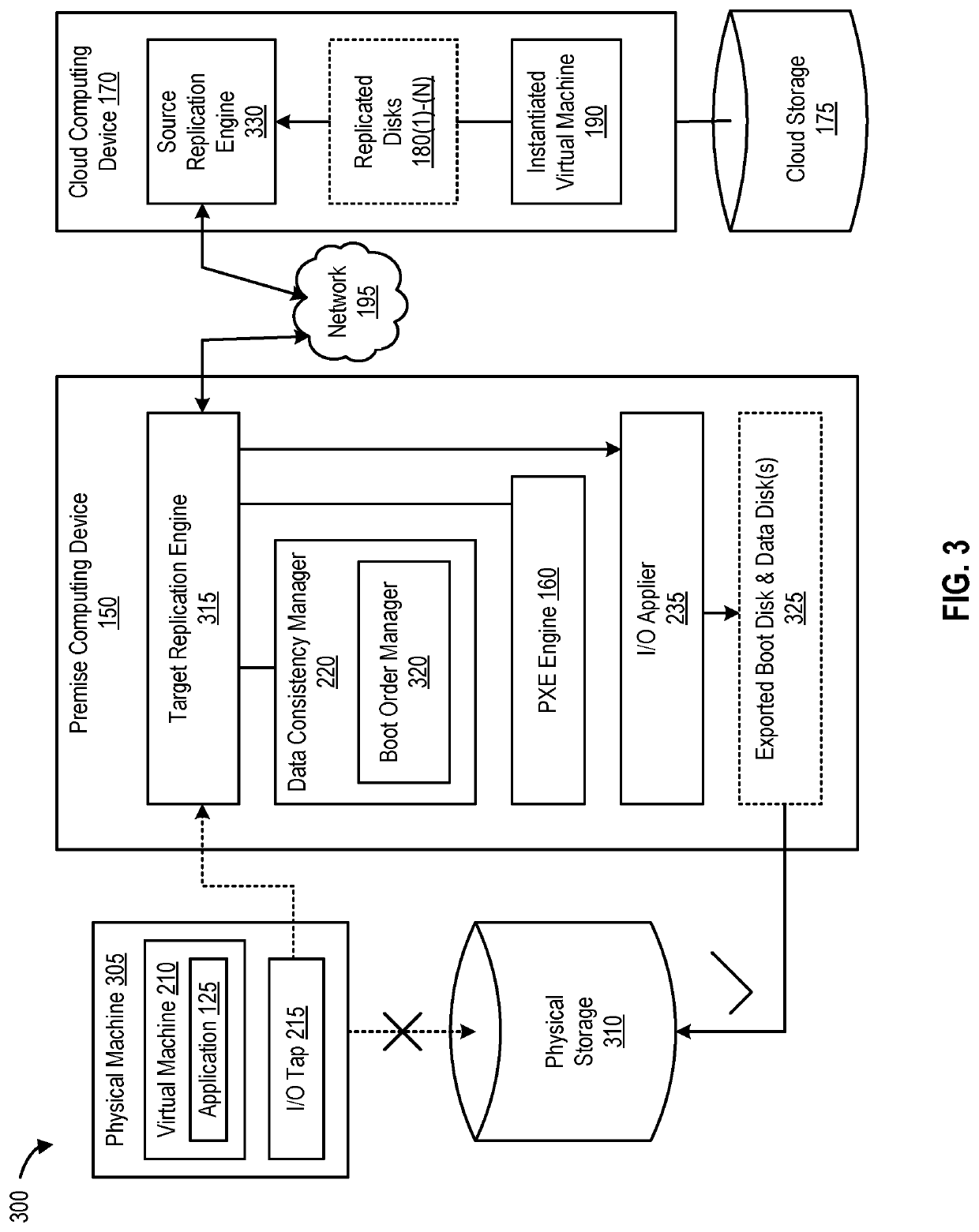
Replication systems and methods for a virtual computing environment
Hybrid replication systems and methods for a virtual computing environment utilize snapshot rotation and differential replication. During snapshot rotation, data modifications intended for a source virtual machine disk (VMDK) are captured by a primary snapshot. Once a particular criterion is satisfied, the data modifications are redirected to a secondary snapshot while the primary snapshot is committed to both source and target VMDKs. The secondary snapshot is then promoted to primary, and a new secondary snapshot is created with writes redirected thereto. If the VMDKs become out-of-sync, disclosed systems can automatically perform a differential scan of the source data and send only the required changes to the target server. Once the two data sets are synchronized, snapshot replication can begin at the previously configured intervals. Certain systems further provide for planned failover copy operations and / or account for migration of a virtual machine during the copying of multiple VMDKs.
Owner:QUEST SOFTWARE INC
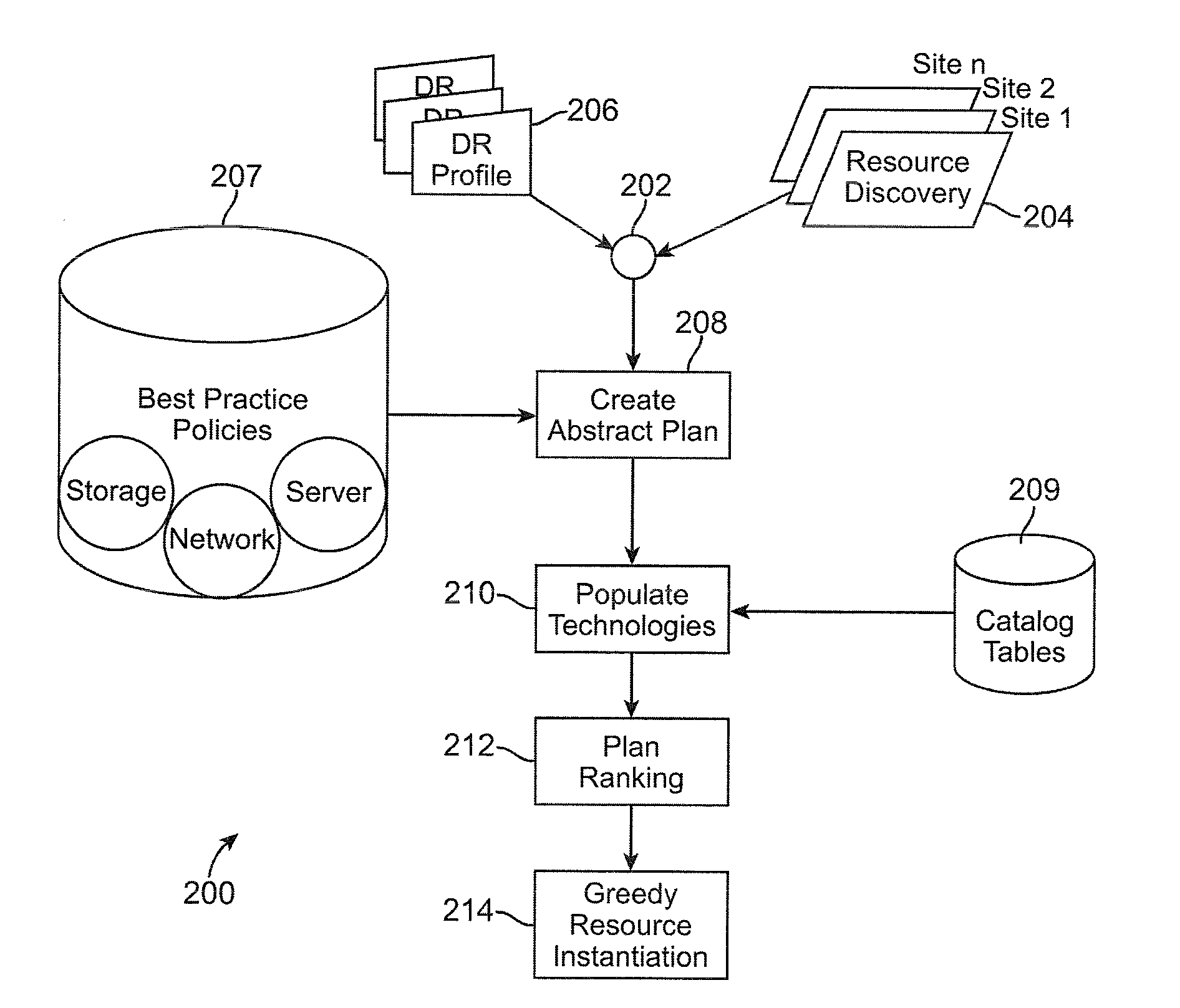
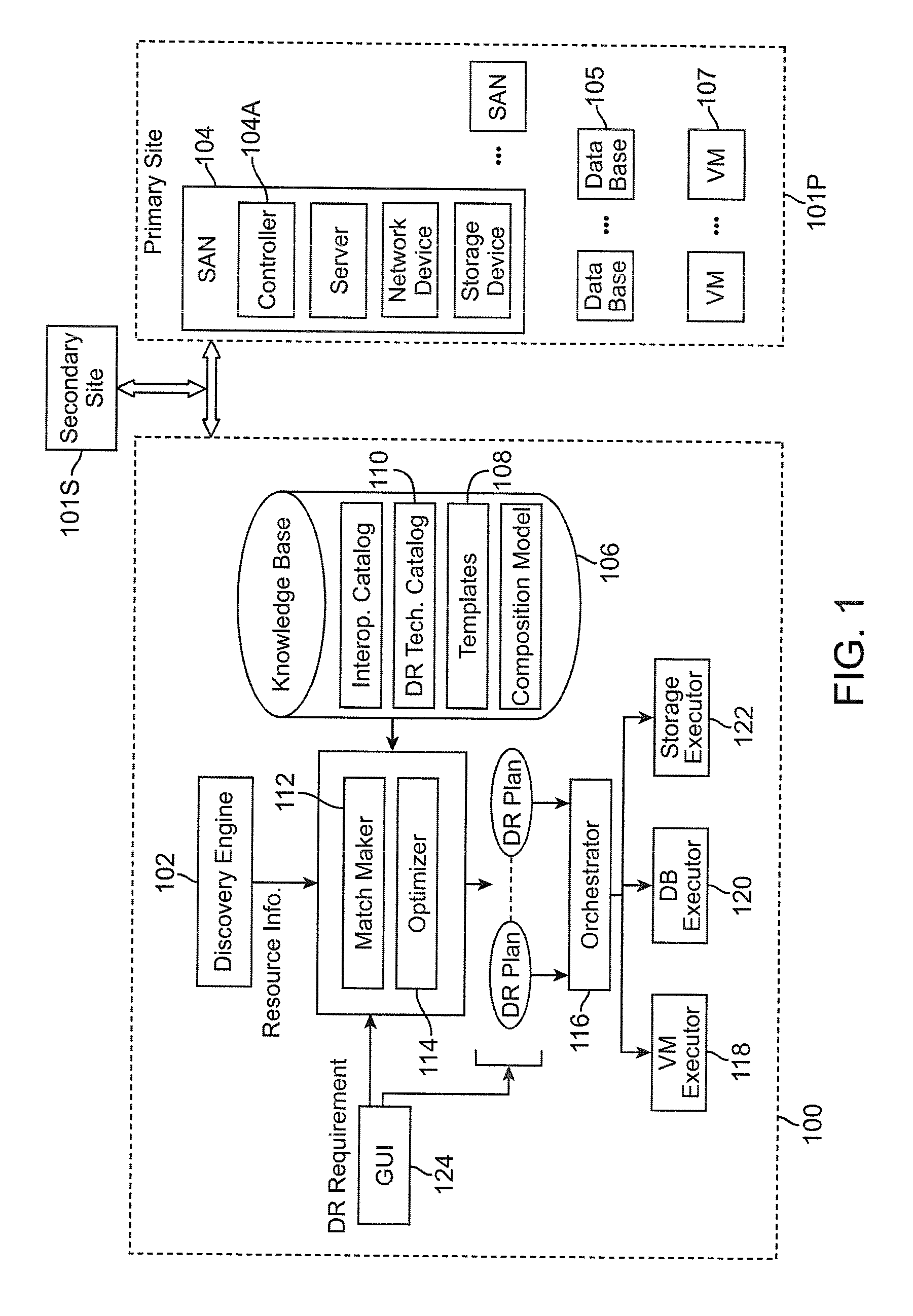
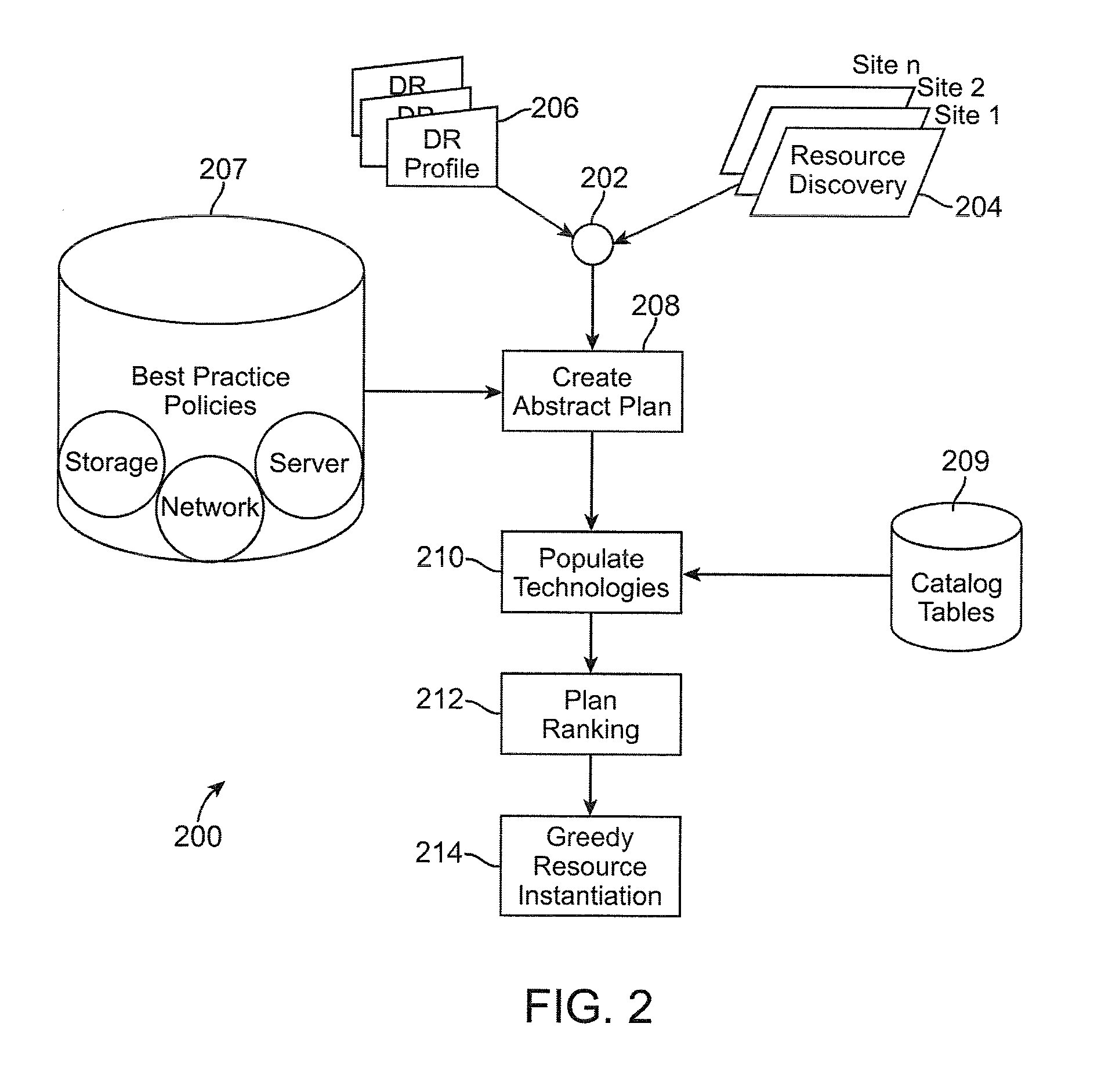
Method and system for automated integrated server-network-storage disaster recovery planning
ActiveUS20090307166A1Knowledge representationInference methodsReplication (computing)Disaster recovery plan
An automated disaster recovery (DR) planning system for a computing environment is provided. A discovery module discovers servers, networks, and storage devices in a computing environment. An expert knowledge base module captures best practices in planning, and capabilities, interoperability, limitation and boundary values for different DR technologies. A match-making module determines multiple DR plans as combinations of one or more replication technologies that can be used to satisfy DR requirements. And, an optimizer configured for assessing a feasible DR plan from said multiple DR plans, to deploy for DR planning of a primary computing environment.
Owner:DAEDALUS BLUE LLC
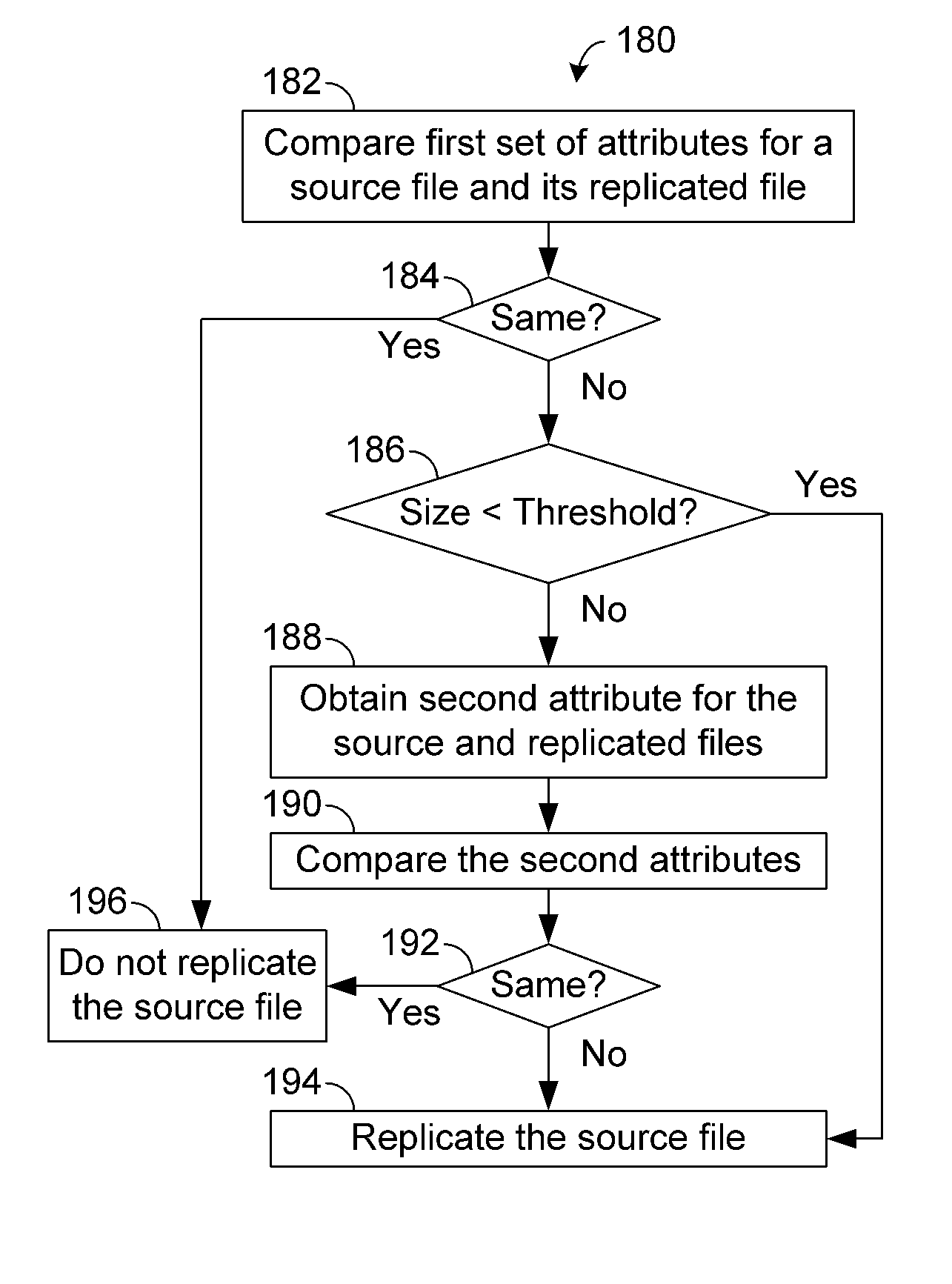
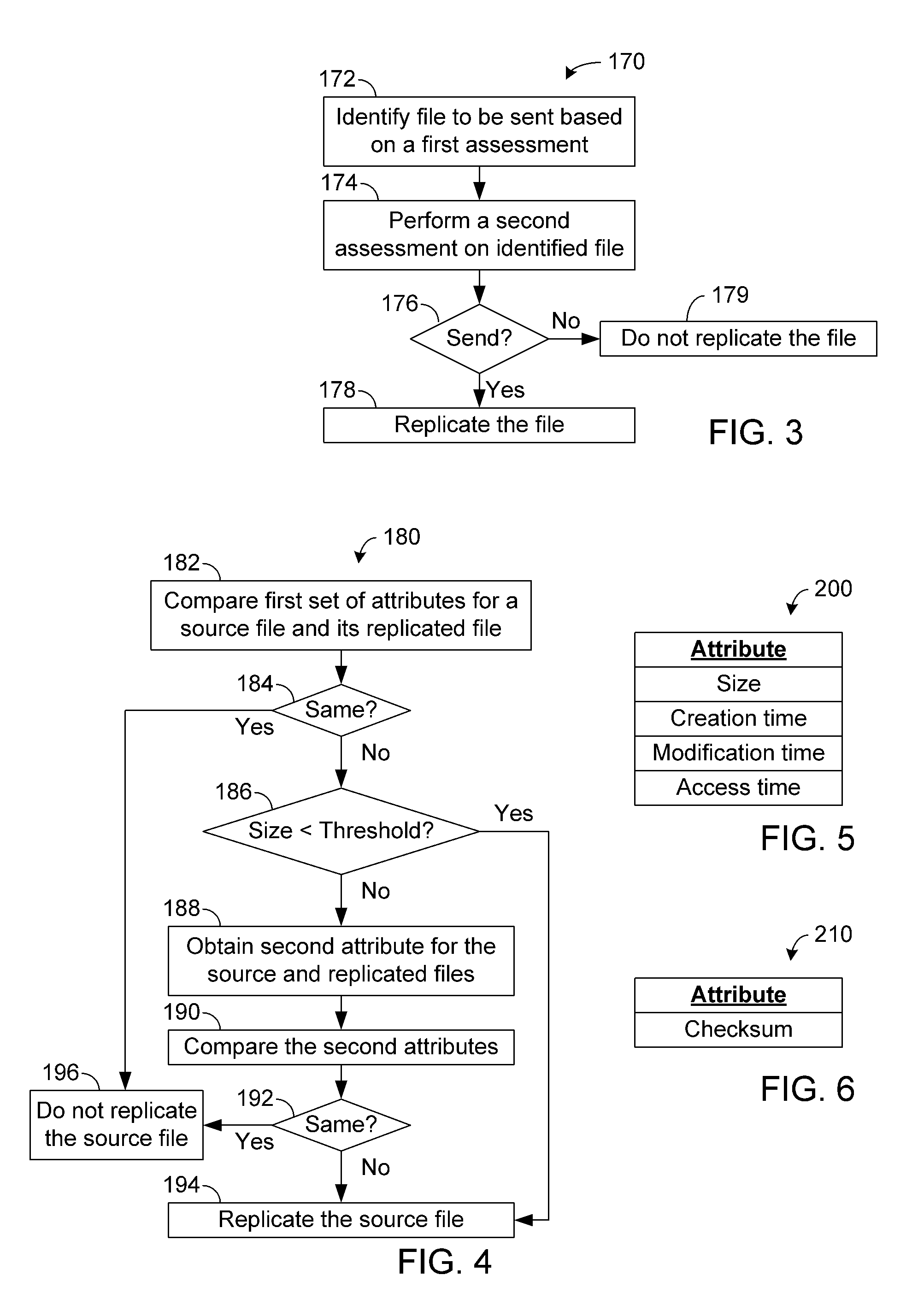
Systems and methods for selective data replication
ActiveUS20110238621A1Digital data information retrievalDigital data processing detailsMetadataChecksum
Systems and methods for performing data replication are disclosed. Determining whether to update replicated data typically involves comparison of readily obtainable attributes of a given source file and its corresponding replicated file. Such attributes can be obtained from, for example, metadata. In certain situations, an additional assessment of the source and replicated files can be beneficial. For example, if integrity of an existing replicated file's content is maintained, one may not want to re-replicate the corresponding source file. For large source files, such a decision can provide substantial reductions in expenditures of available computing and network resources. In certain embodiments, a threshold for identifying such large files can be based on one or more operating parameters such as network type and available bandwidth. In certain embodiments, replication file's integrity can be checked by calculating and comparing checksums for the replication file and its corresponding source file.
Owner:COMMVAULT SYST INC
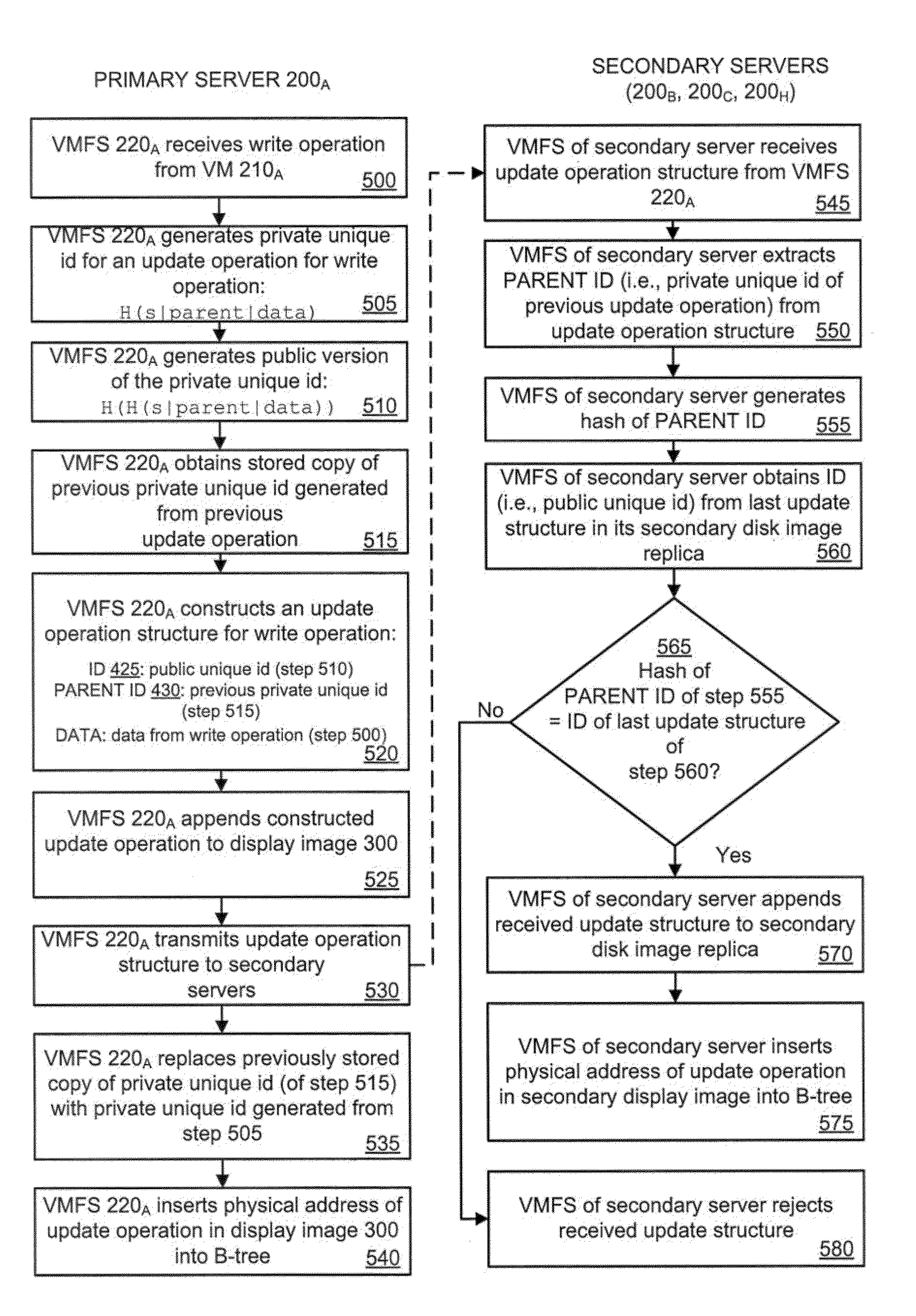
System and method for replicating disk images in a cloud computing based virtual machine file system
ActiveUS8352482B2Eliminate pointLess reliableDatabase updatingKey distribution for secure communicationFailoverVirtual file system
A replicated decentralized storage system comprises a plurality of servers that locally store disk images for locally running virtual machines as well as disk images, for failover purposes, for remotely running virtual machines. To ensure that disk images stored for failover purposes are properly replicated upon an update of the disk image on the server running the virtual machine, a hash of a unique value known only to the server running the virtual machine is used to verify the origin of update operations that have been transmitted by the server to the other servers storing replications of the disk image for failover purposes. If verified, the update operations are added to such failover disk images.
Owner:VMWARE INC
Method, system and program products for recovering from failures within a shared nothing distributed computing environment
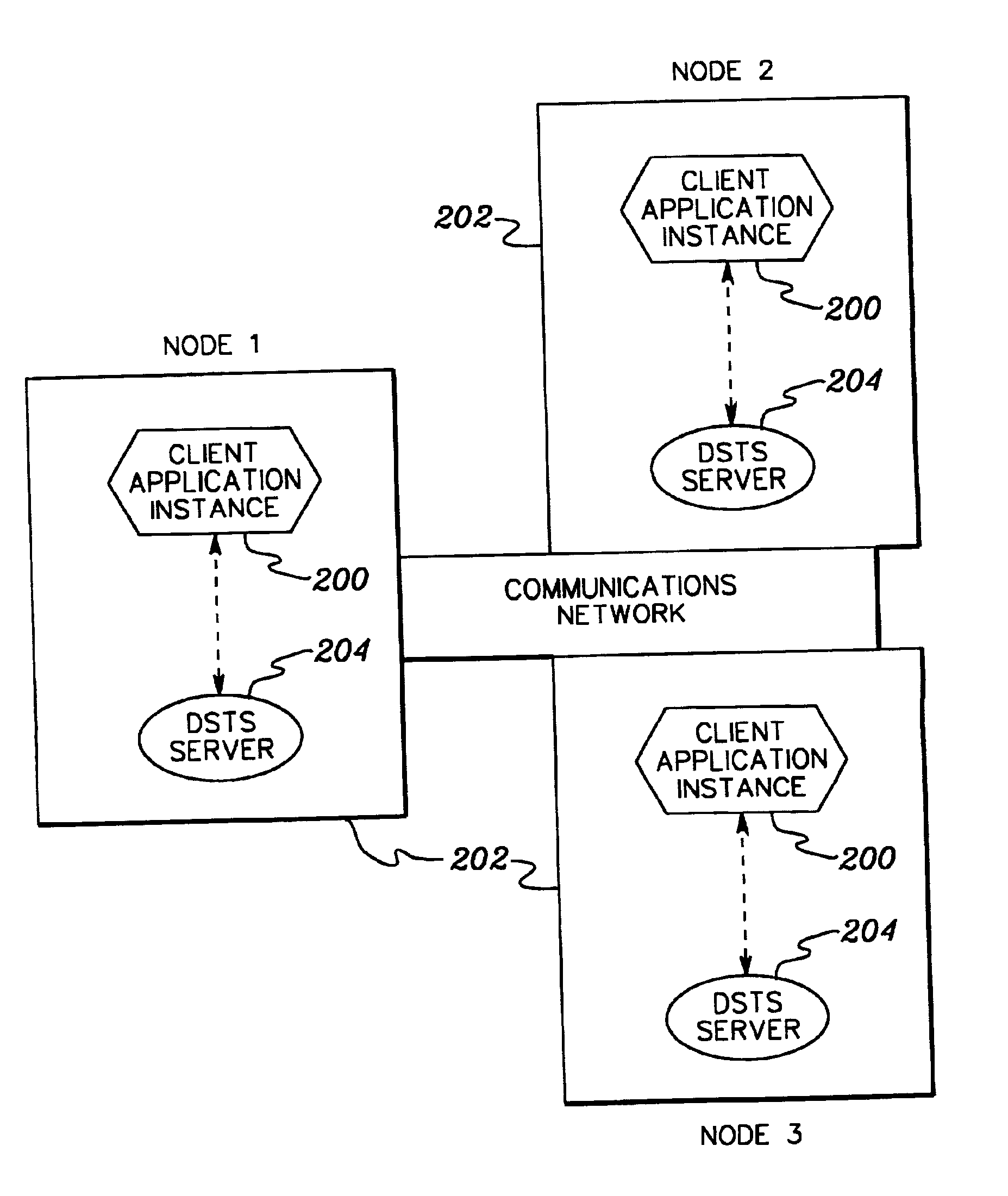
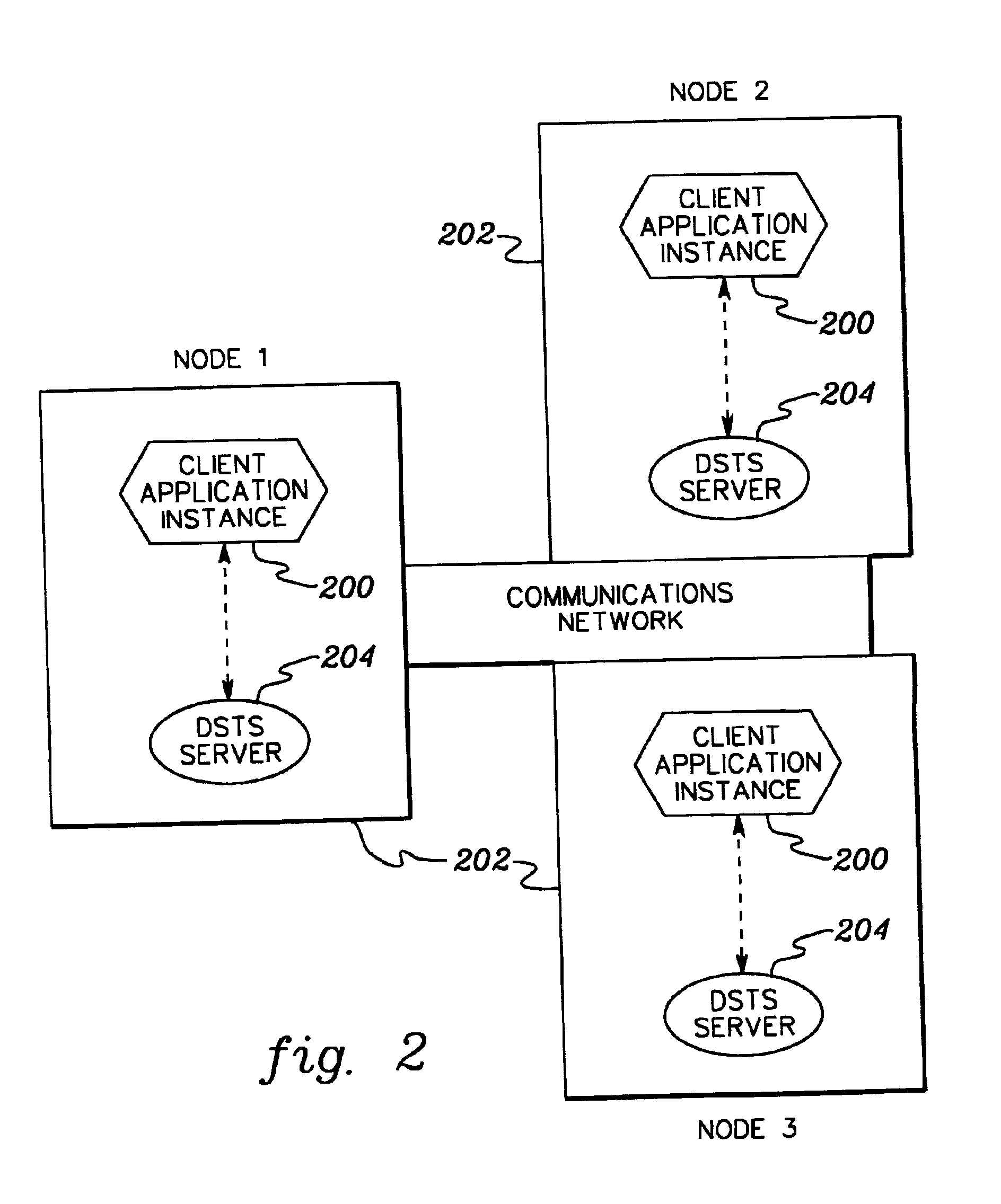
InactiveUS6873987B1Overcomes shortcomingData processing applicationsError detection/correctionDistributed Computing EnvironmentSystems management
The management and use of replicated distributed transactions is facilitated. A distributed synchronous transaction system protocol is provided to manage the replication of distributed transactions for client application instances. The distributed synchronous transaction system allows transactions to be replicated without having the client application instances be aware of other instances to receive the transaction. Further, if a failure occurs during processing of a distributed replicated transaction, the distributed synchronous transaction system manages the recovery of the failure.
Owner:IBM CORP
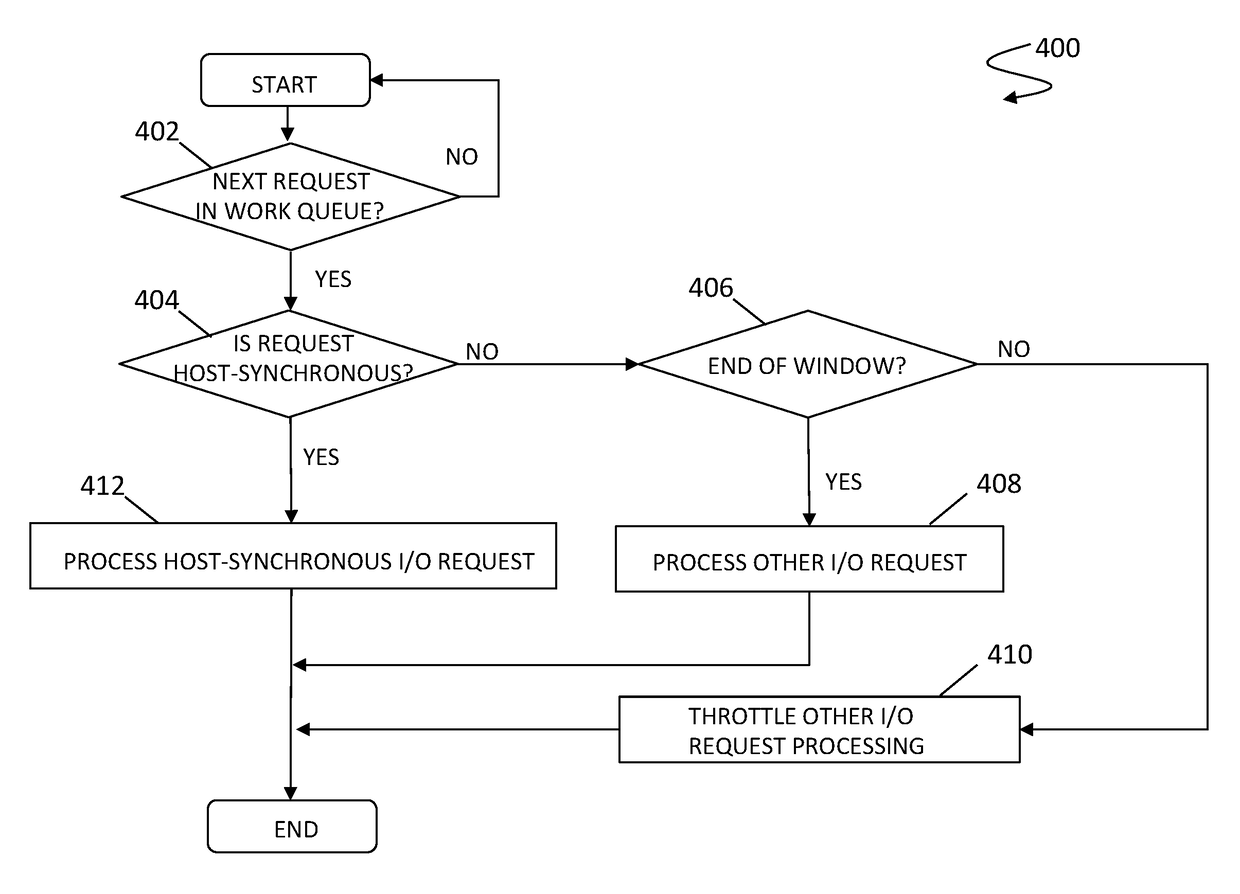
Balancing response times for synchronous I/O requests having different priorities
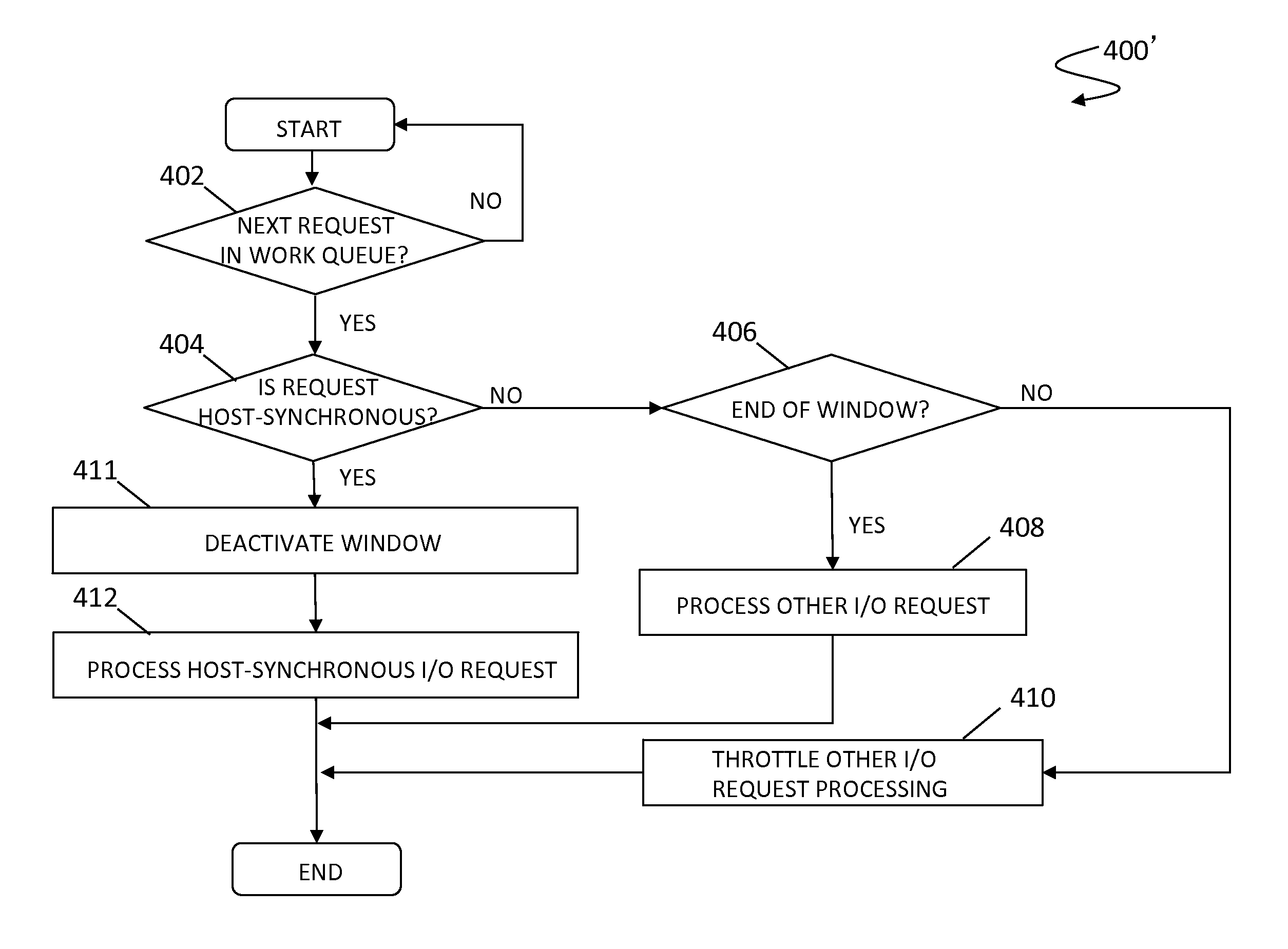
ActiveUS9330048B1Multiple digital computer combinationsFault locationEngineeringReplication (computing)
A computing environment, such as an data mirroring or replication storage system, may need to process synchronous I / O requests having different priorities in addition to handling I / O requests on the basis of synchronous or asynchronous groupings. The system described herein provides a data storage system that addresses issues involving efficient balancing of response times for servicing synchronous I / O requests having different priorities. Accordingly, the system described herein provides for maintaining an optimal response time for the host-synchronous I / O requests and the optimal throughput of non-host-synchronous I / O requests using a host-synchronous request time window within which processing of non-host-synchronous I / O requests is throttled. The host-synchronous request time window may be selected to enable the optimal response time for the host-synchronous I / O and also to minimize the impact on the overall throughput of the I / O processor of the storage device.
Owner:EMC IP HLDG CO LLC
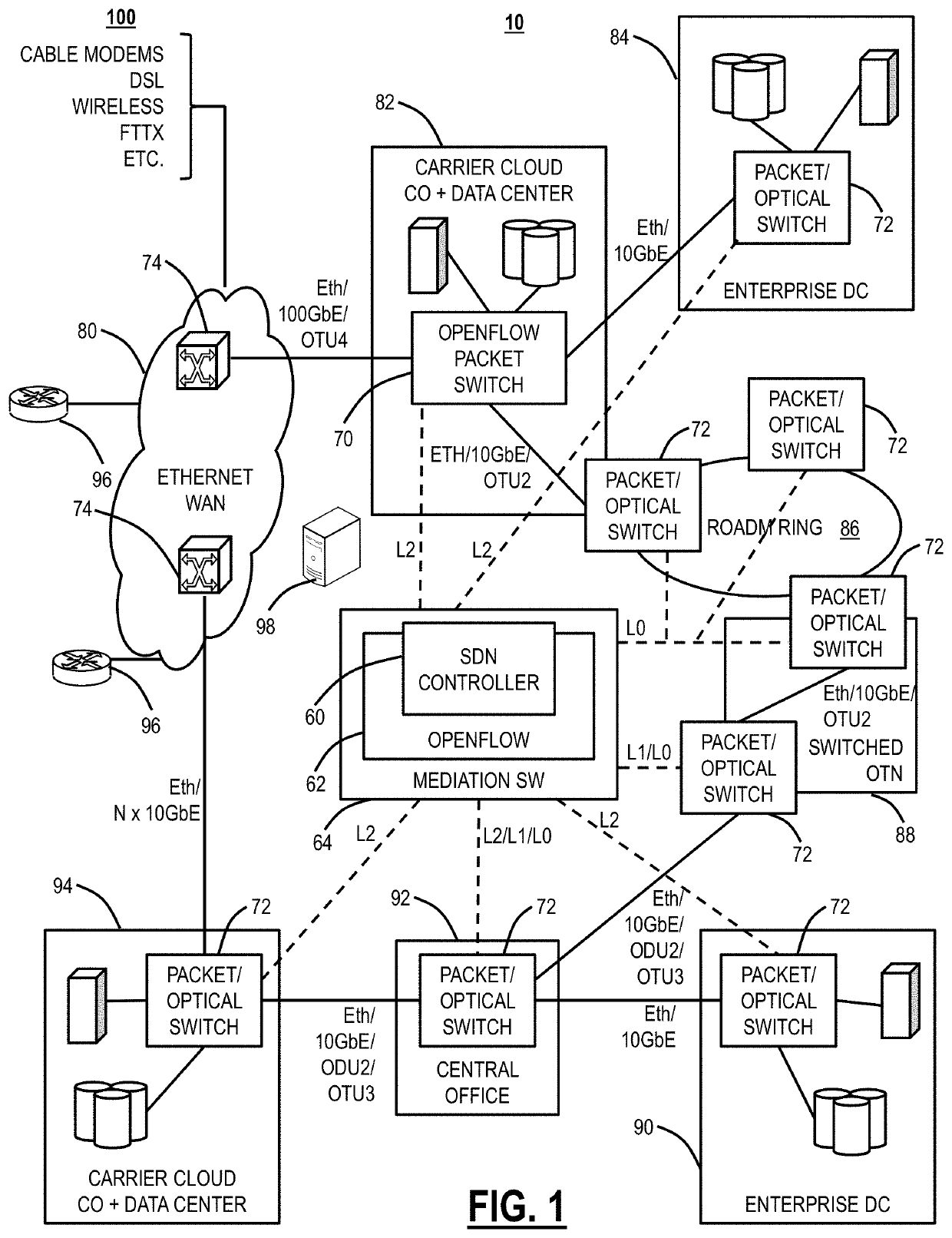
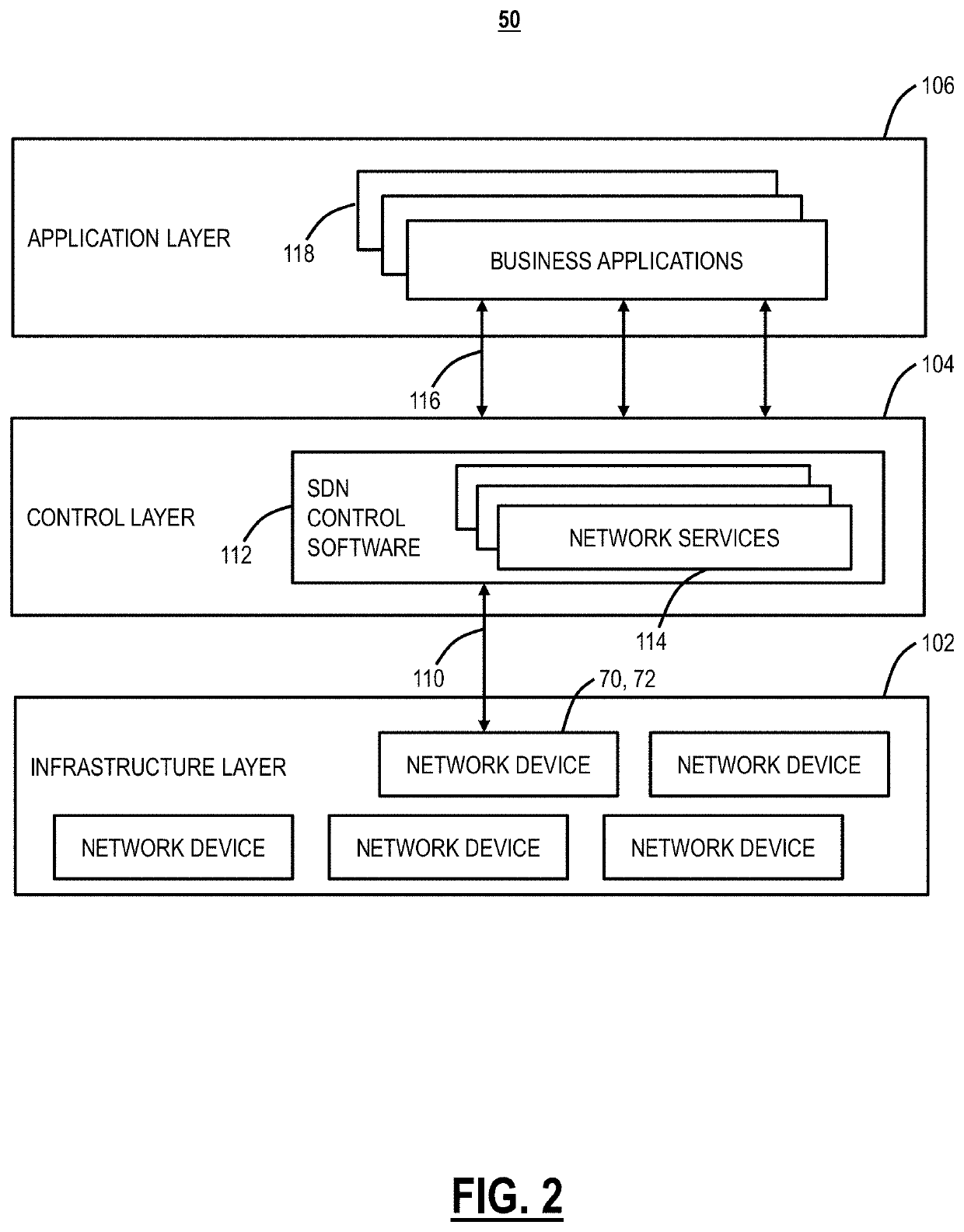
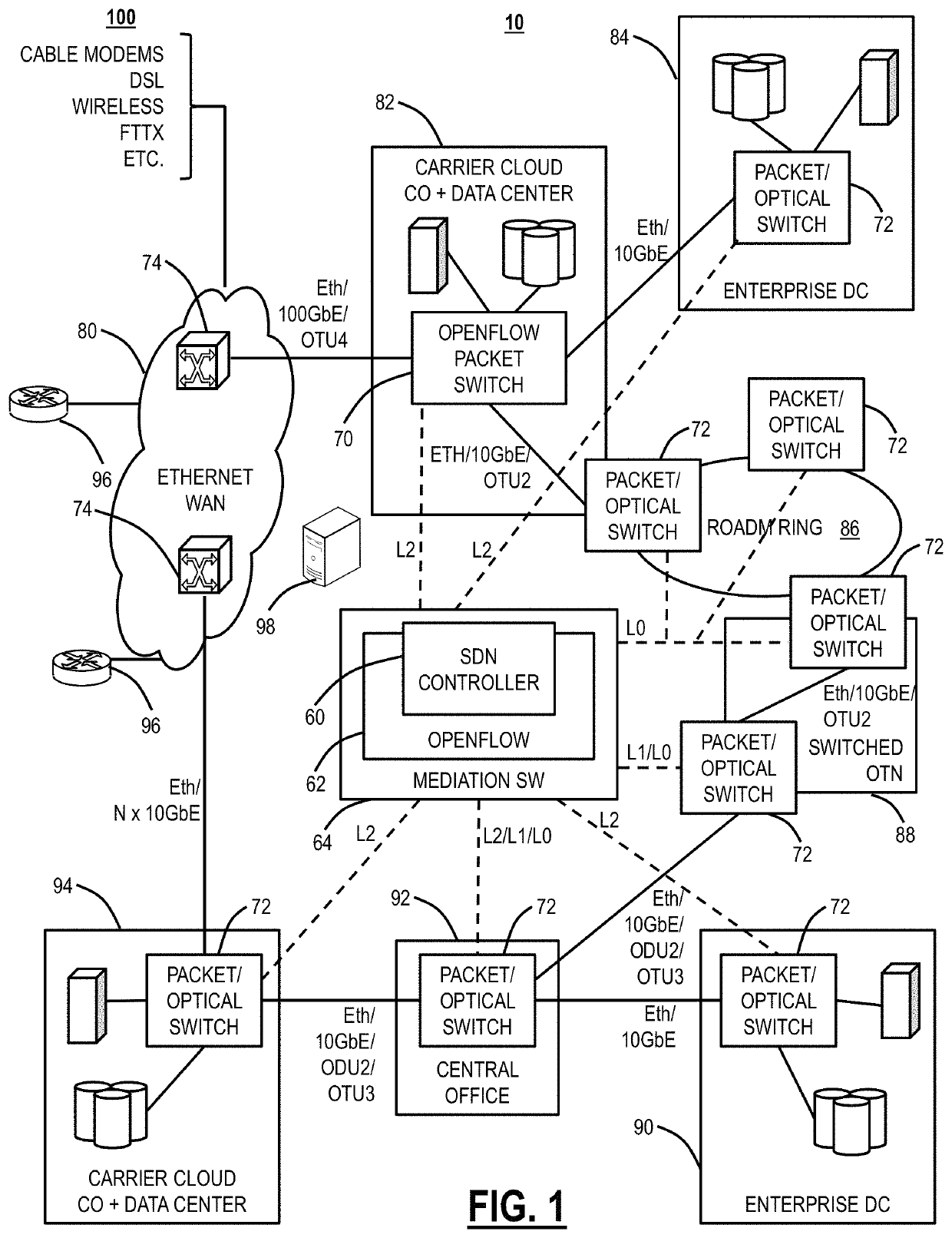
Data network and execution environment replication for network automation and network applications
Network replica systems and methods include, via a server, a group of servers, or in a cloud computing environment, communicating with one or more management systems and one or more networks associated with the one or more management systems via one or more Application Programming Interfaces (APIs); obtaining data from the one or more management systems and / or the one or more networks; storing the data in a database of record which defines a detailed model of a current state of the networks; and applying one or more assertions to data of interest in the database of record to emulate behavior in the one or more networks, wherein the assertions map actual device, process, business, architecture, and technology behaviors onto the data of interest from the database of record to emulate the behavior, wherein the database of record and the applied one or more assertions include a network replica of the networks.
Owner:CIENA
Network intrusion detection method, device and system and storage medium
PendingCN111049849AImprove securityOvercome technical issues that reduce detection efficiencyTransmissionData streamConcurrent computation
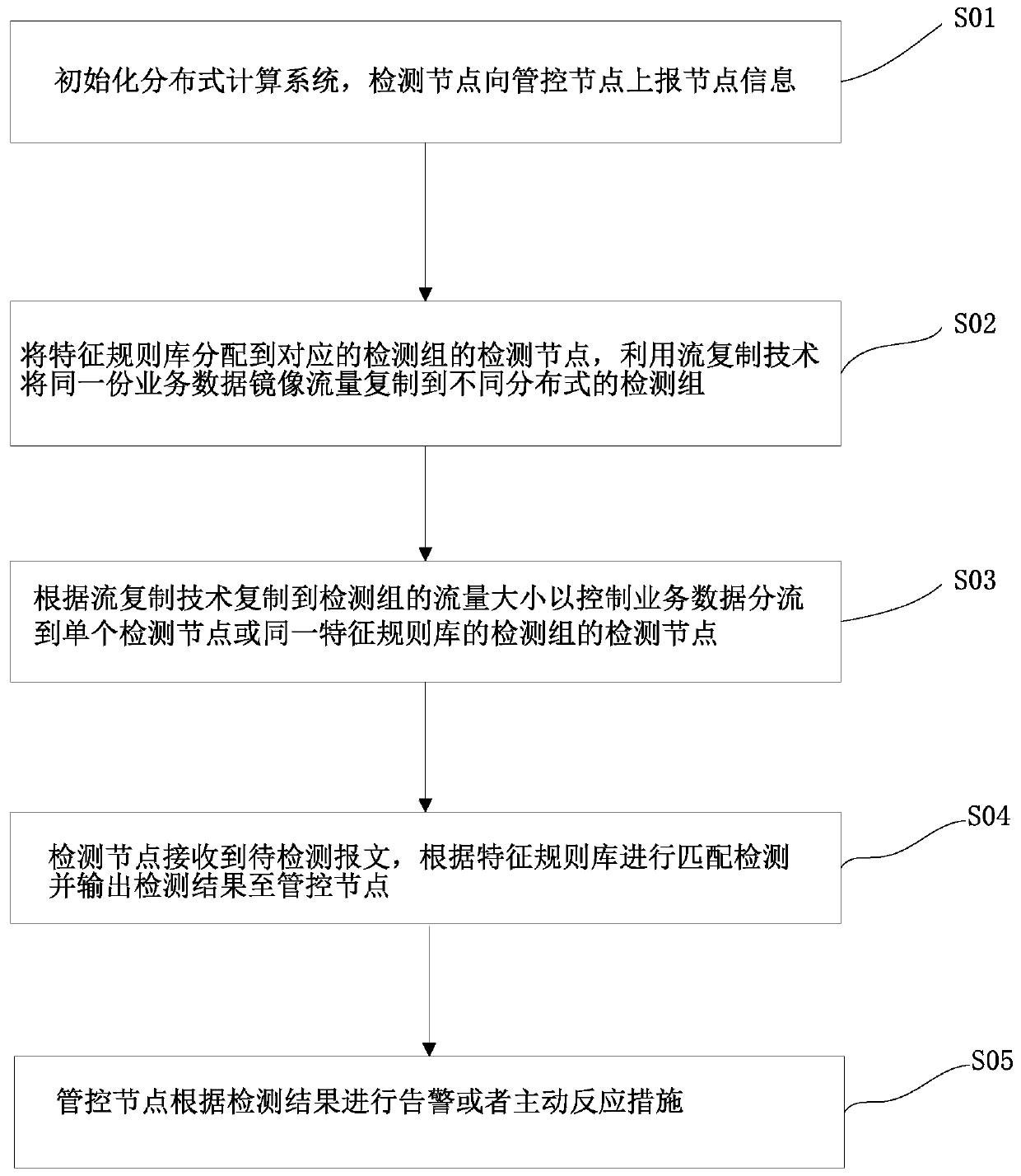
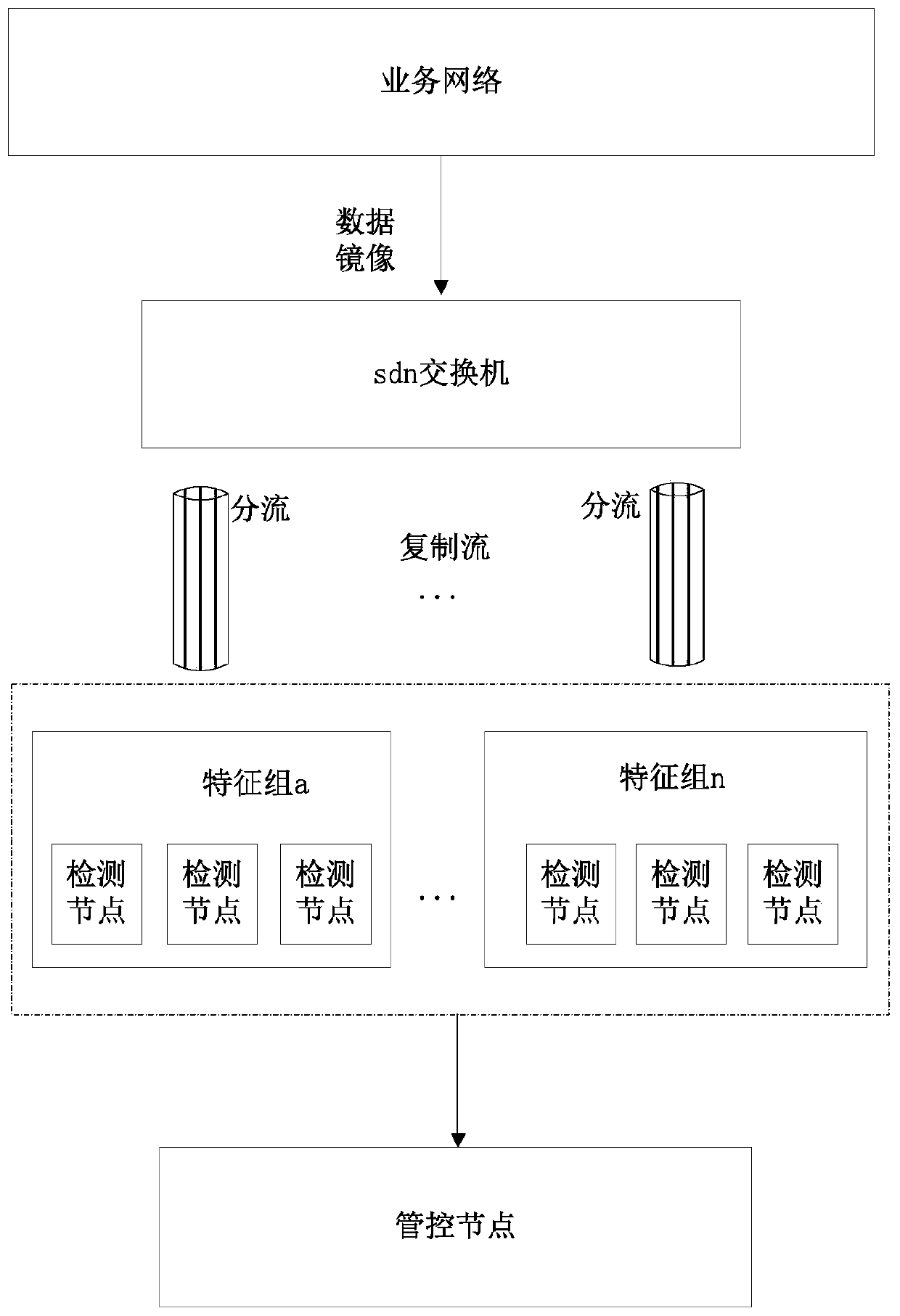
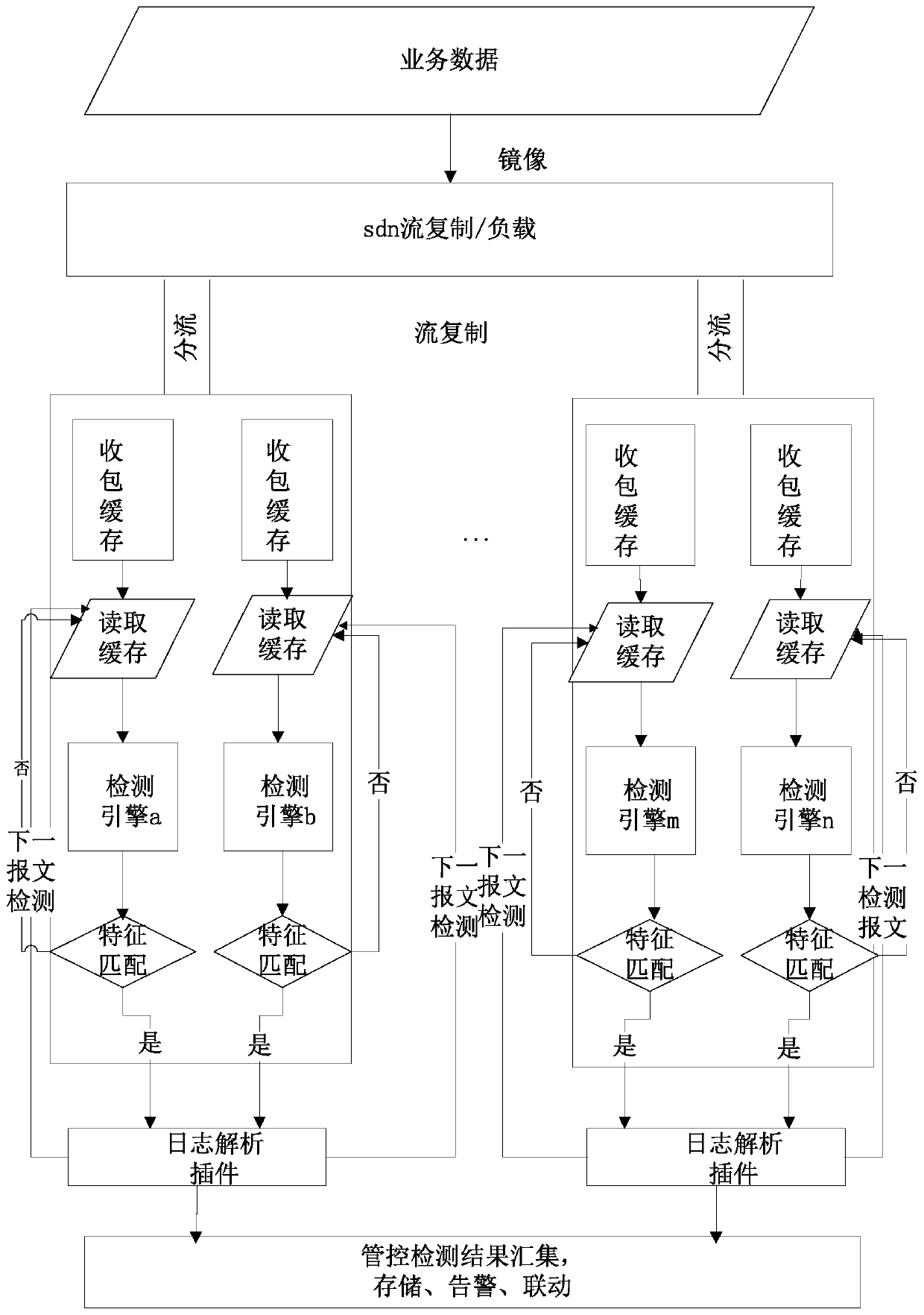
The invention discloses a network intrusion detection method, device and system and a storage medium, and the method comprises the steps: initializing a distributed computing system, and enabling a detection node to report node information to a management and control node; distributing a feature rule base to detection nodes of corresponding detection groups, and copying the same service data mirror image traffic to different distributed detection groups by using a stream copying technology; according to the flow copied to the detection group by the flow copying technology, controlling the service data to be shunted to a single detection node or a detection node of the detection group of the same feature rule base; and enabling the detection node to receive the to-be-detected message, perform matching detection according to the feature rule base and output a detection result to the management and control node. Through a technical means of adopting a distributed and parallel computing architecture and shunting a network data stream to a plurality of detection nodes by utilizing distributed and sdn switch stream replication, the technical problem of low detection efficiency during large-flow data in the prior art is solved, and the effect of improving the system detection efficiency is achieved.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
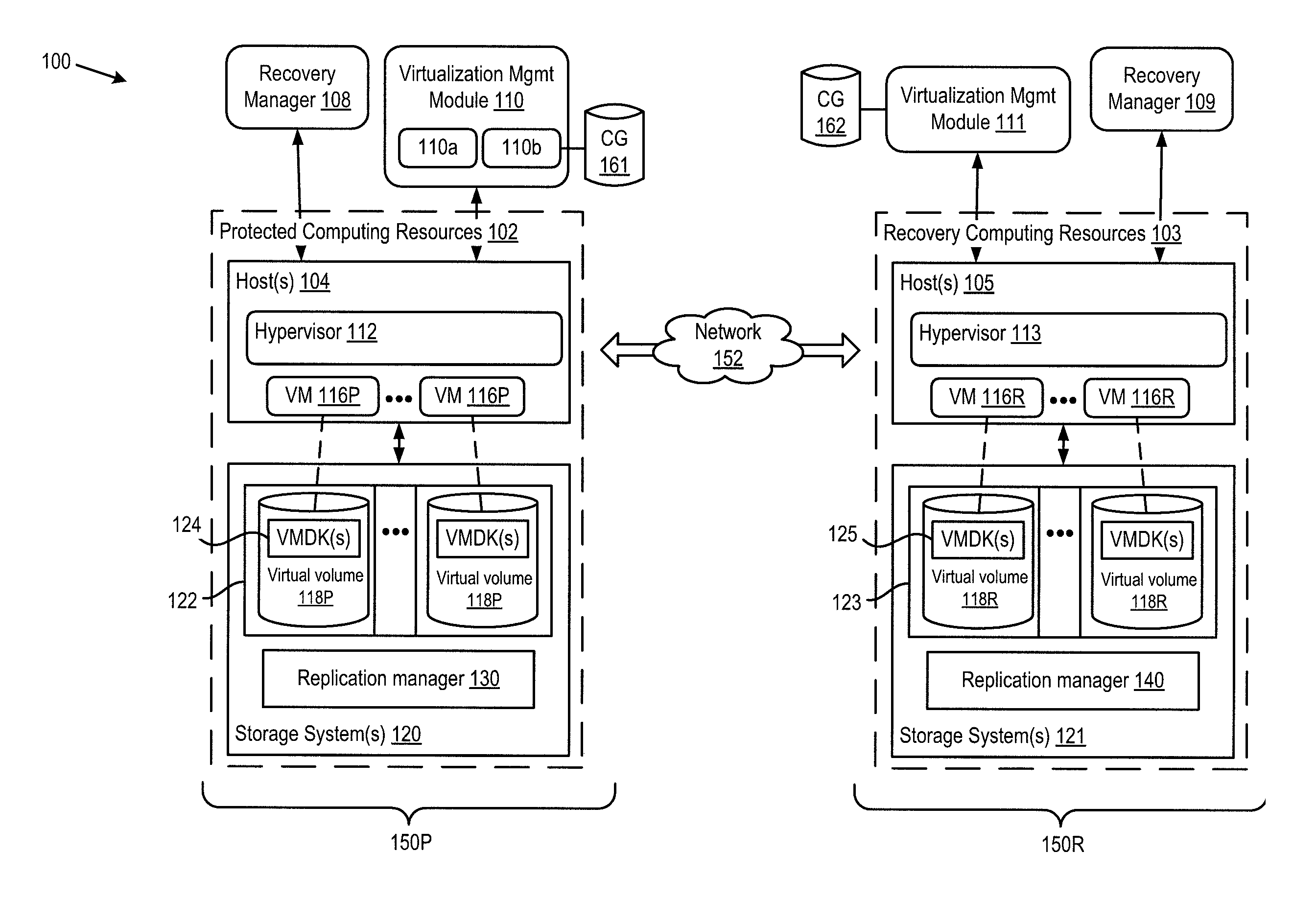
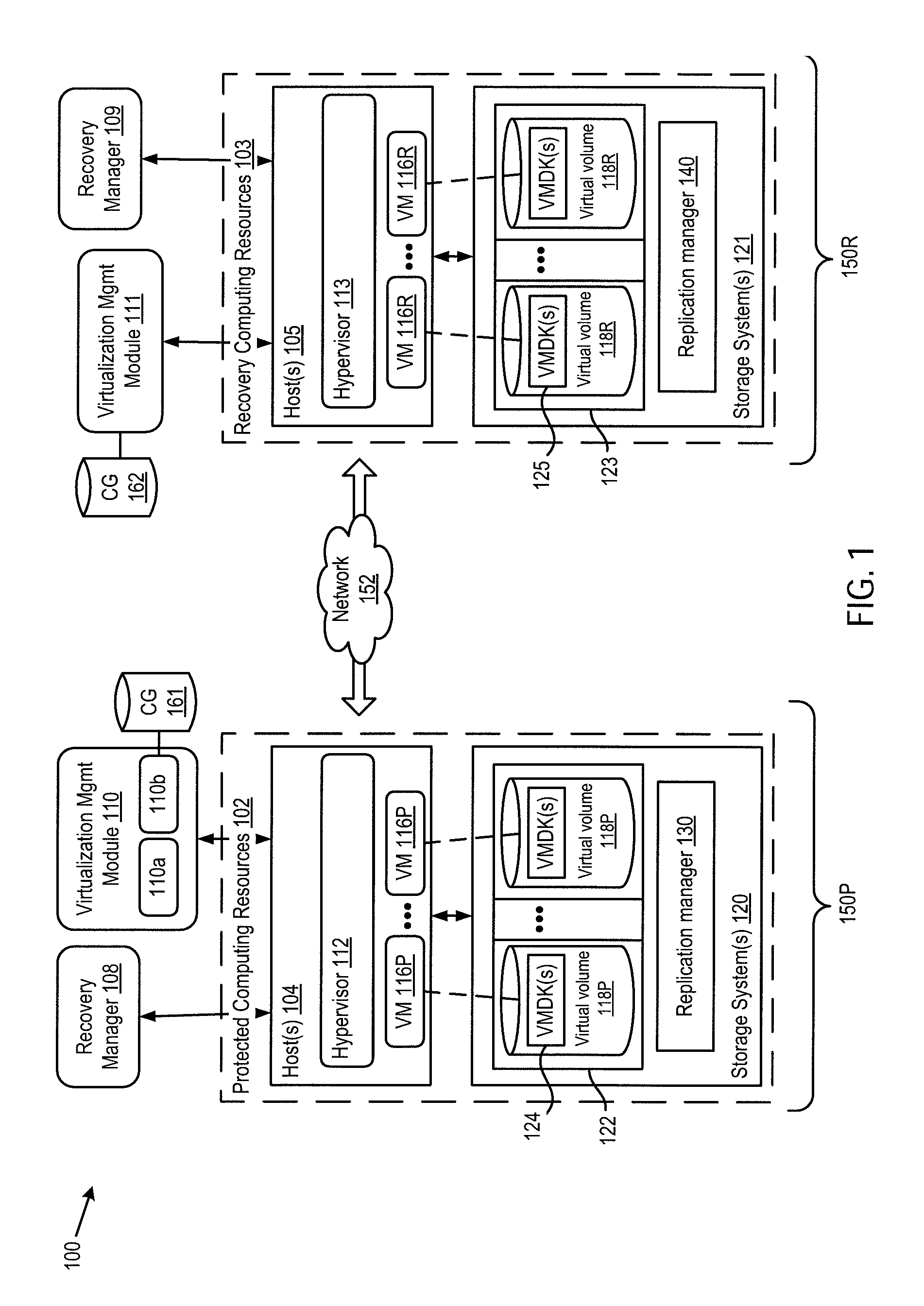
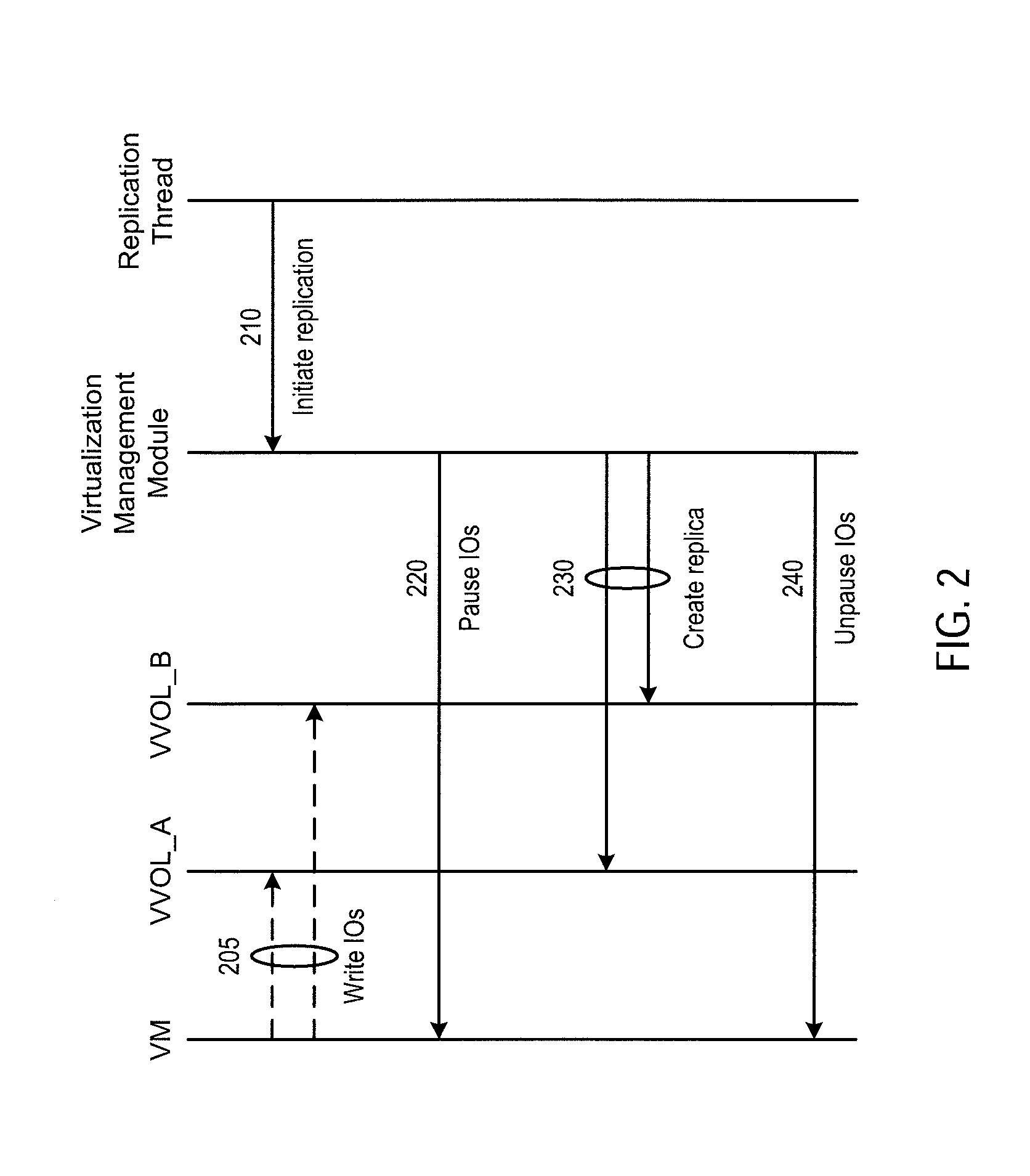
Consistent replication of virtual computing instance data
ActiveUS20160179437A1Input/output to record carriersDigital data processing detailsVirtual computingOperating system
Virtual computing instance data that are stored across multiple storage volumes are replicated in a manner such that the write order is maintained. The frequency of the replication is set so that the recovery point objective defined for the VM data can be satisfied. The replication includes the steps of determining a set of logical storage volumes across which the virtual computing instance issues dependent write IOs, issuing a first command to the virtual computing instance to block new IOs and to block receipt of IO acknowledgements, issuing a command to create replicas of all the logical storage volumes in the set, and then issuing a second command to the virtual computing instance to unblock new IOs and unblock receipt of IO acknowledgements.
Owner:VMWARE INC
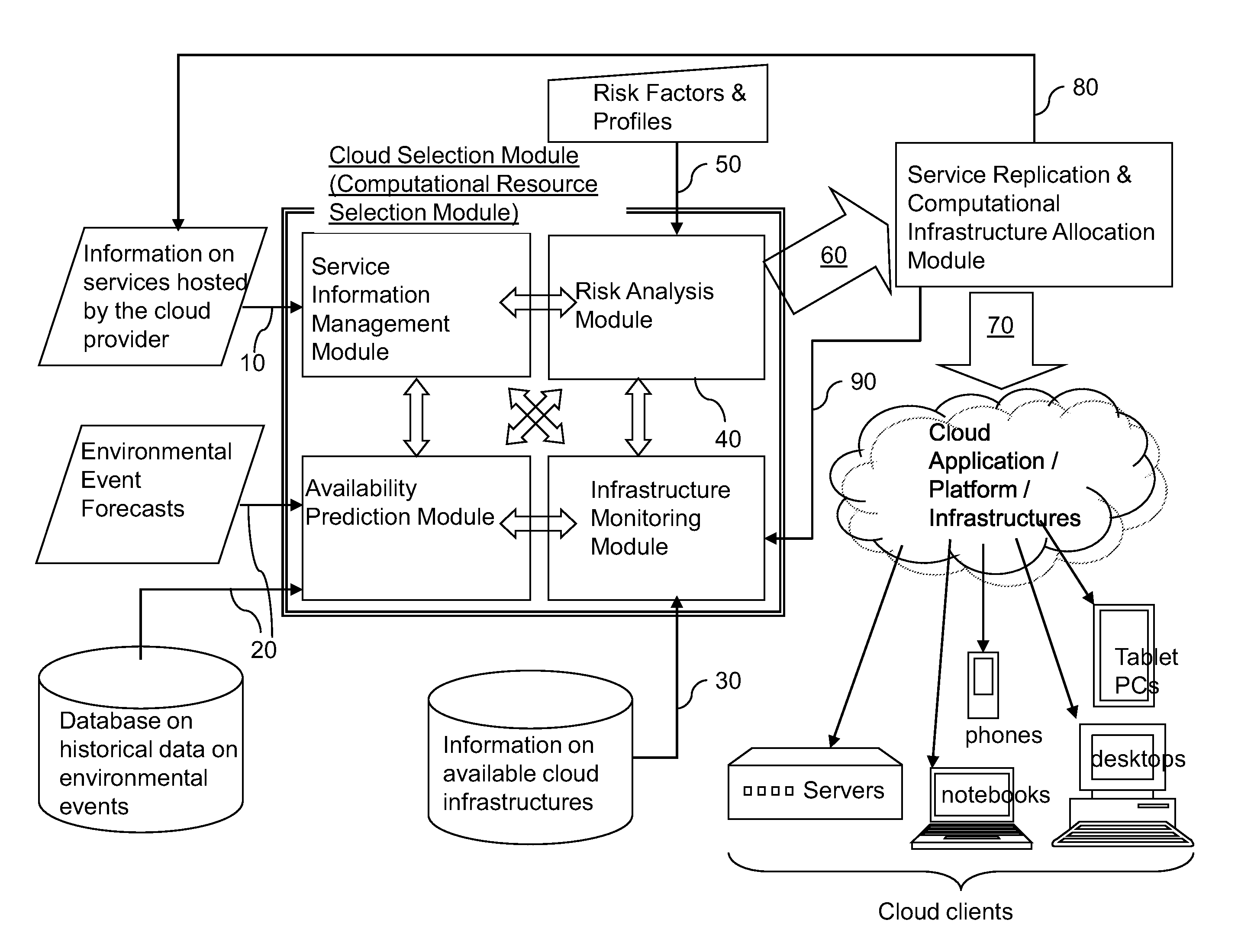
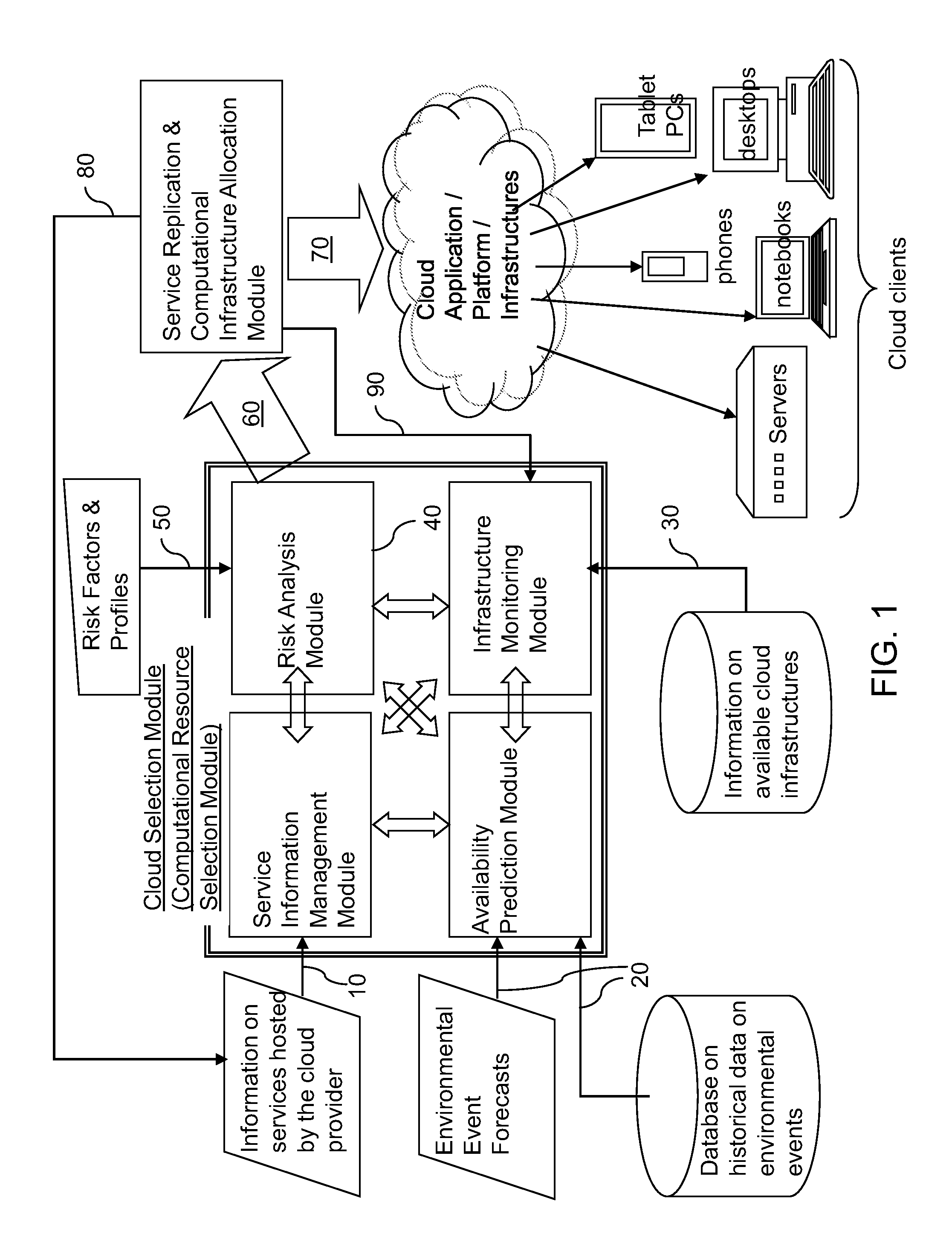
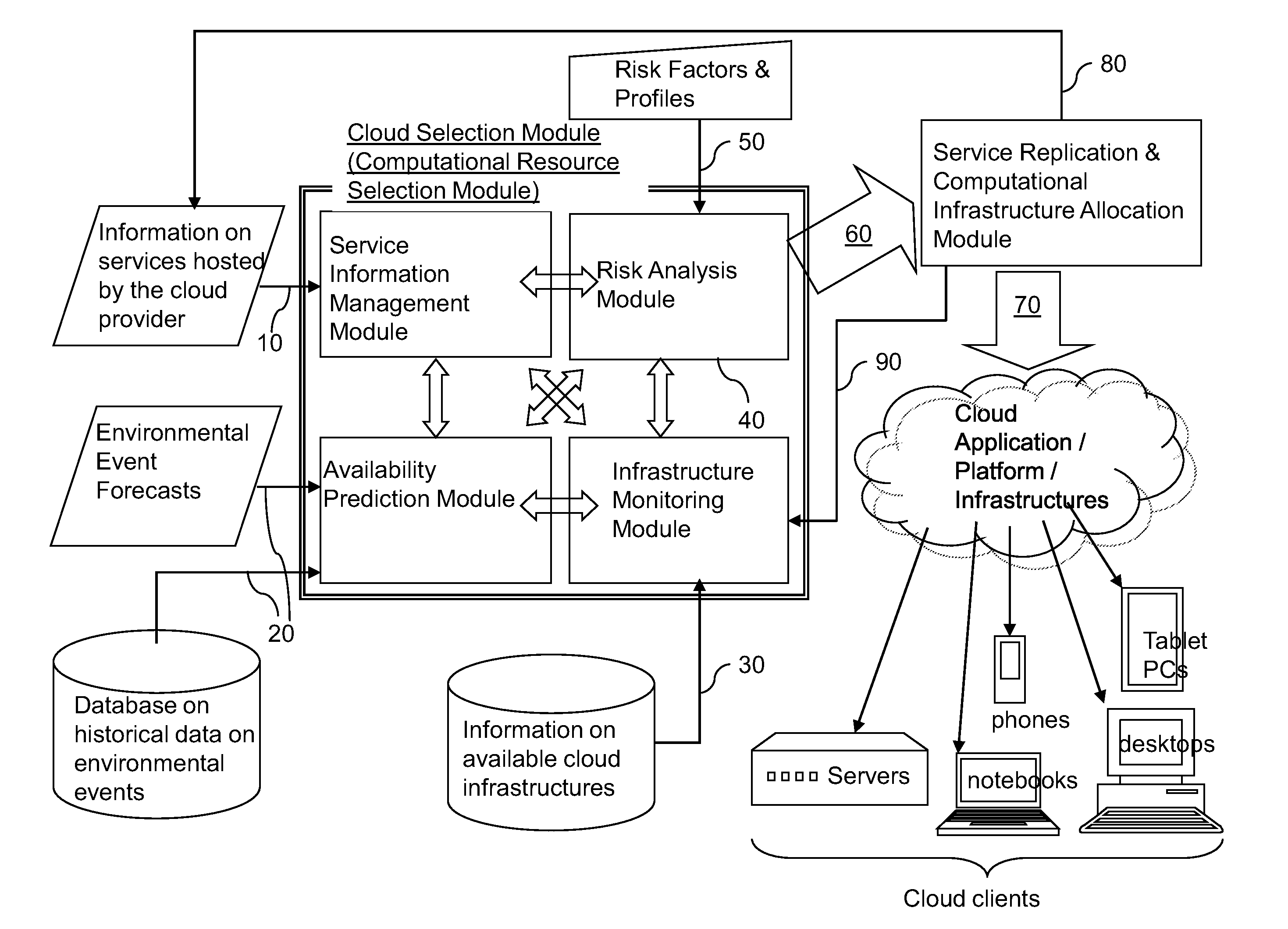
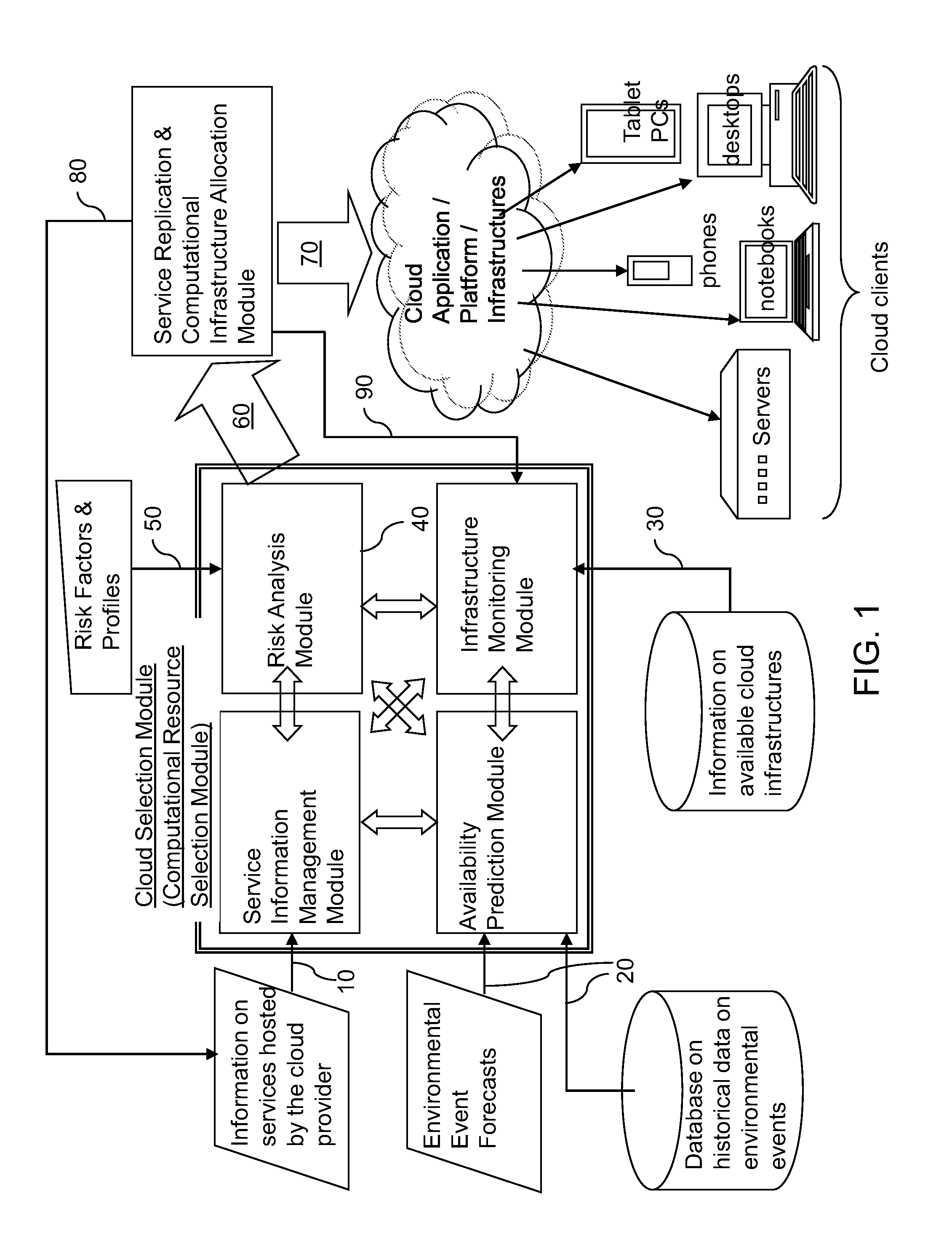
Risk-based dynamic geo-location based replication of services in cloud computing
InactiveUS20130339204A1Improve service resiliencyCost of disruptionFinanceDigital computer detailsCloud computingRisk profile
Dynamic provisioning of resources is employed to replicate capabilities and / or services in a distributed computing infrastructure to overcome potential disruptions in the capabilities and / or services. Predictive tools for weather forecasts, risk profile analysis based on geographical location of data / service centers, and historical data are employed to improve service resiliency. Further, for each local computing service that is considered for replication, the cost of disruption is compared with the total cost of replication to ensure that a computing infrastructure service provider is selected in a cost-efficient manner.
Owner:IBM CORP
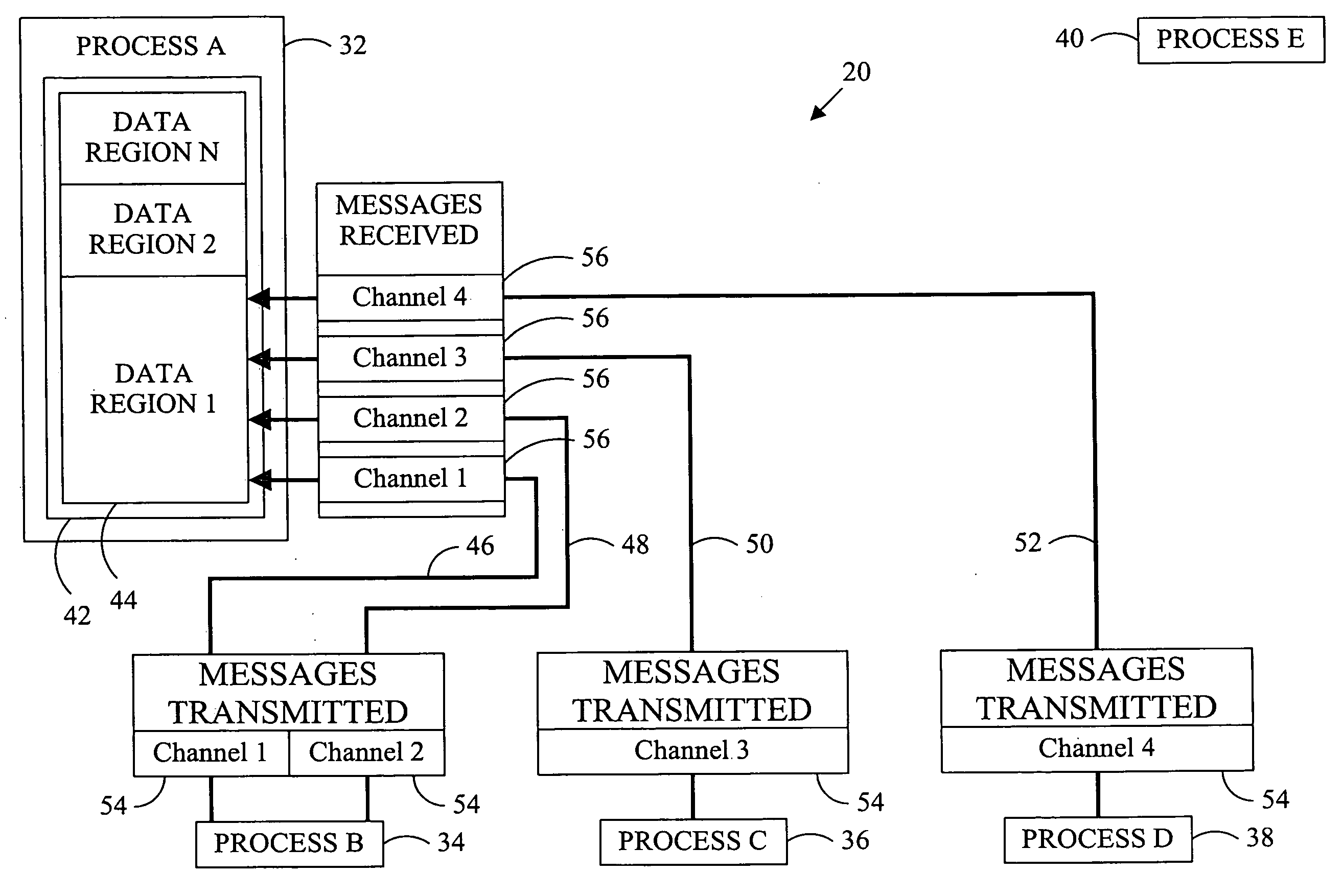
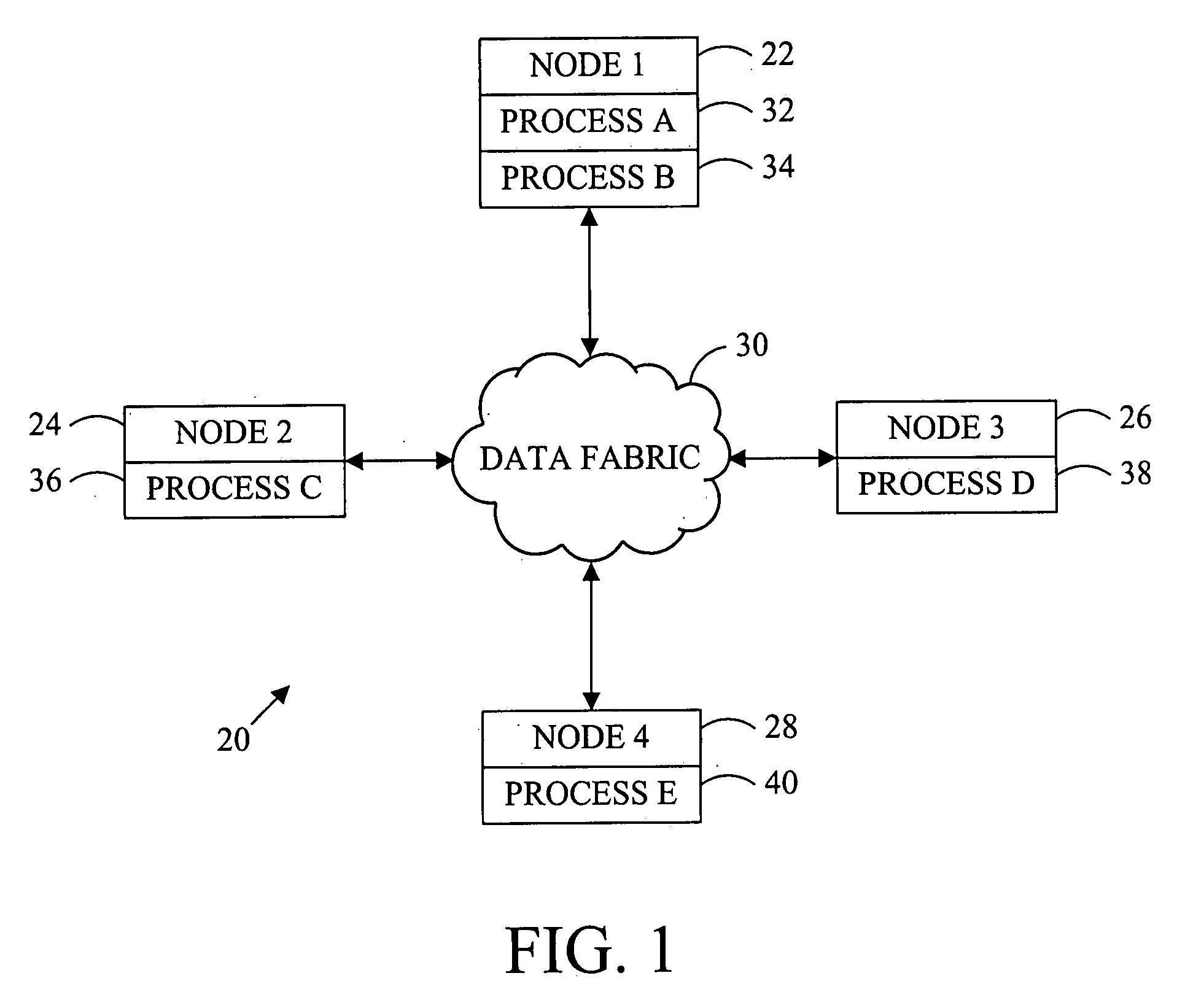
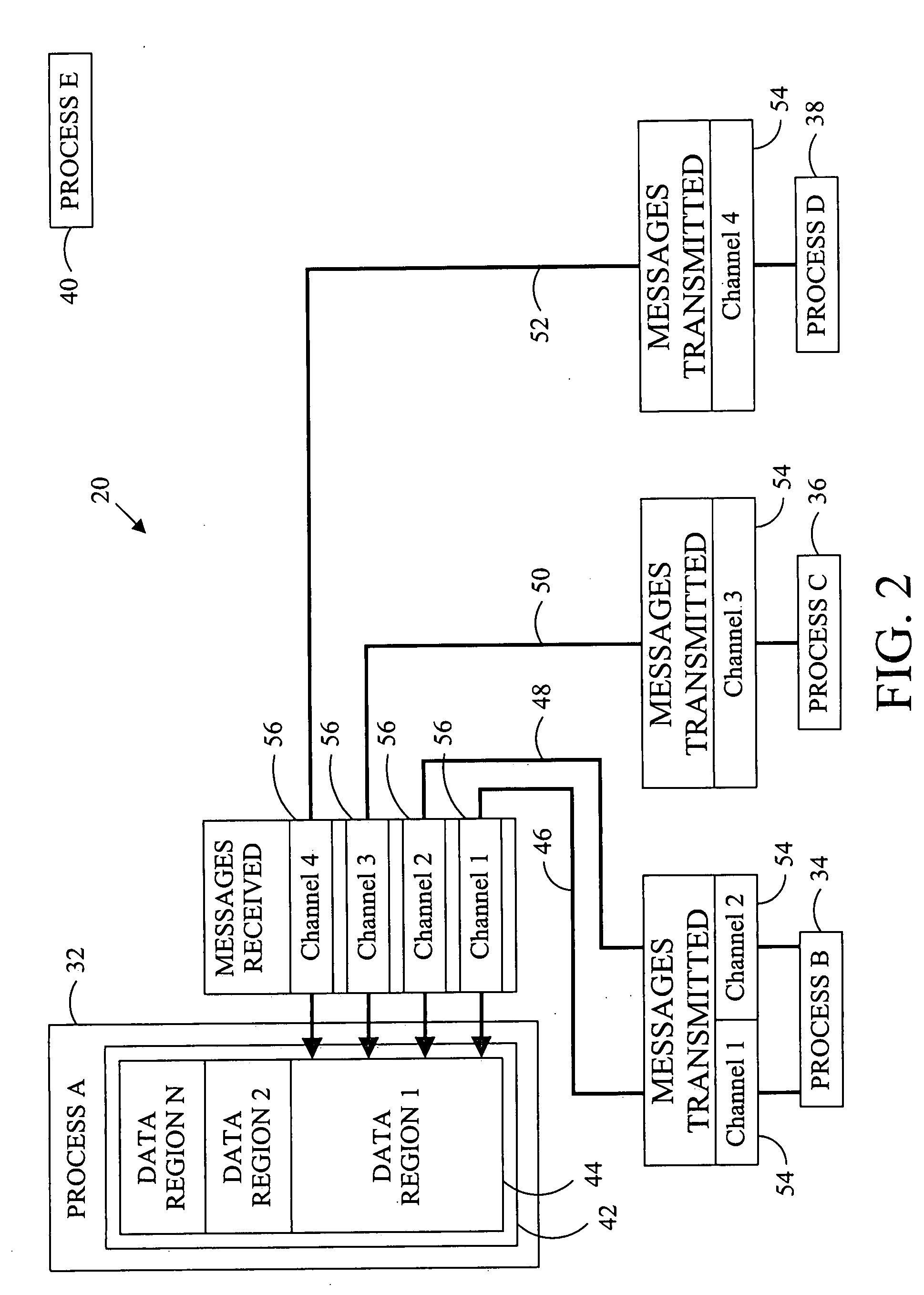
Data replication method
ActiveUS20090119347A1Digital data information retrievalDigital data processing detailsReceiptReplication method
To ensure data consistency for a new data replica created for a computing system, the transmission and receipt of messages altering the data are monitored and replication of the data is permitted when all changes to the data that have been transmitted to the data have been received.
Owner:GOPIVOTAL
Data replication method
ActiveUS8005787B2Digital data information retrievalDigital data processing detailsEngineeringReplication (computing)
To ensure data consistency for a new data replica created for a computing system, the transmission and receipt of messages altering the data are monitored and replication of the data is permitted when all changes to the data that have been transmitted to the data have been received.
Owner:GOPIVOTAL
Risk-based dynamic geo-location based replication of services in cloud computing
InactiveUS20130339203A1FinanceDigital computer detailsRisk profilingDistributed computing infrastructure
Dynamic provisioning of resources is employed to replicate capabilities and / or services in a distributed computing infrastructure to overcome potential disruptions in the capabilities and / or services. Predictive tools for weather forecasts, risk profile analysis based on geographical location of data / service centers, and historical data are employed to improve service resiliency. Further, for each local computing service that is considered for replication, the cost of disruption is compared with the total cost of replication to ensure that a computing infrastructure service provider is selected in a cost-efficient manner.
Owner:IBM CORP
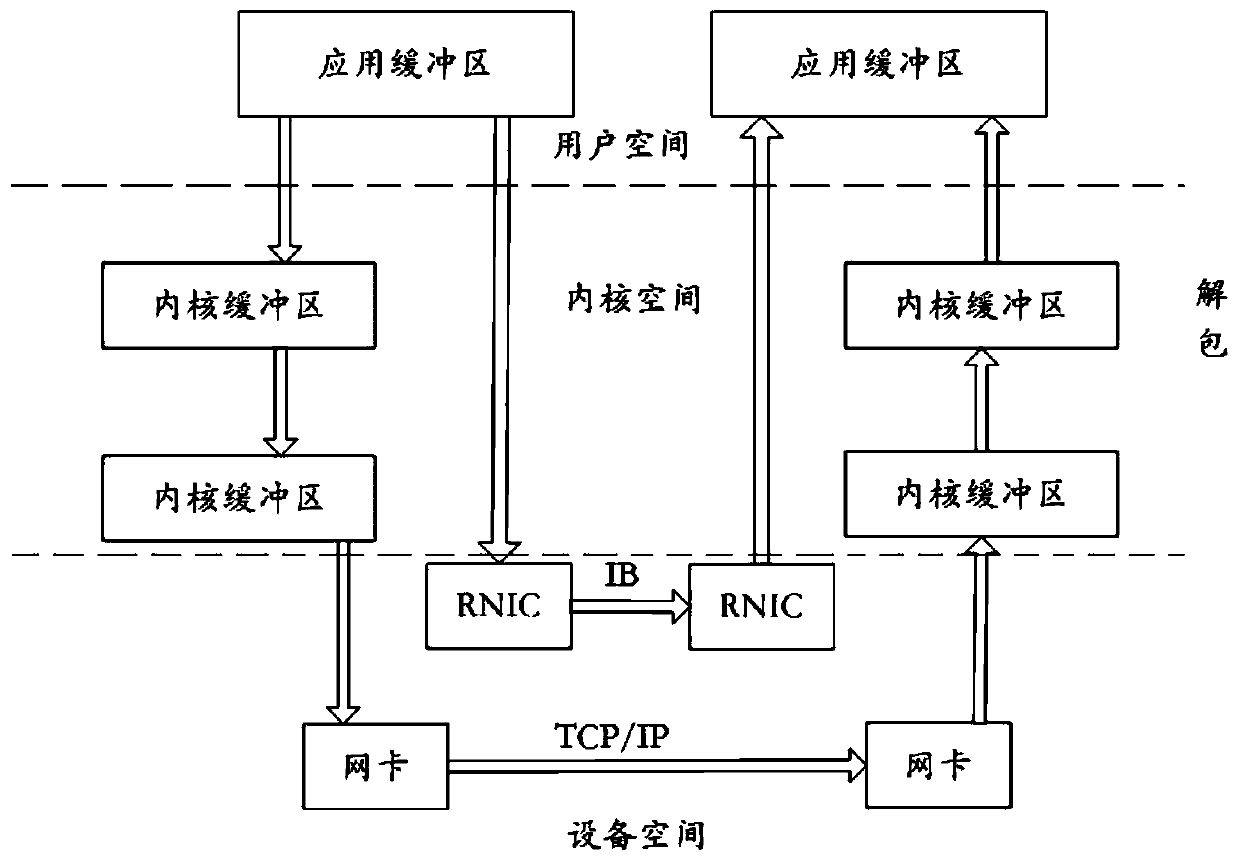
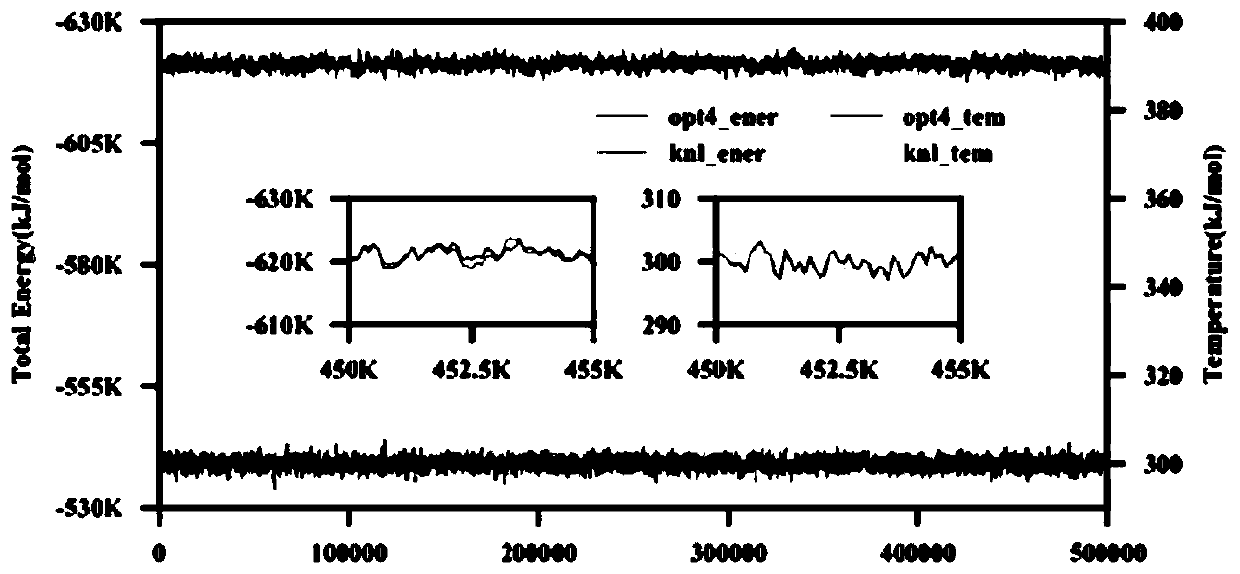
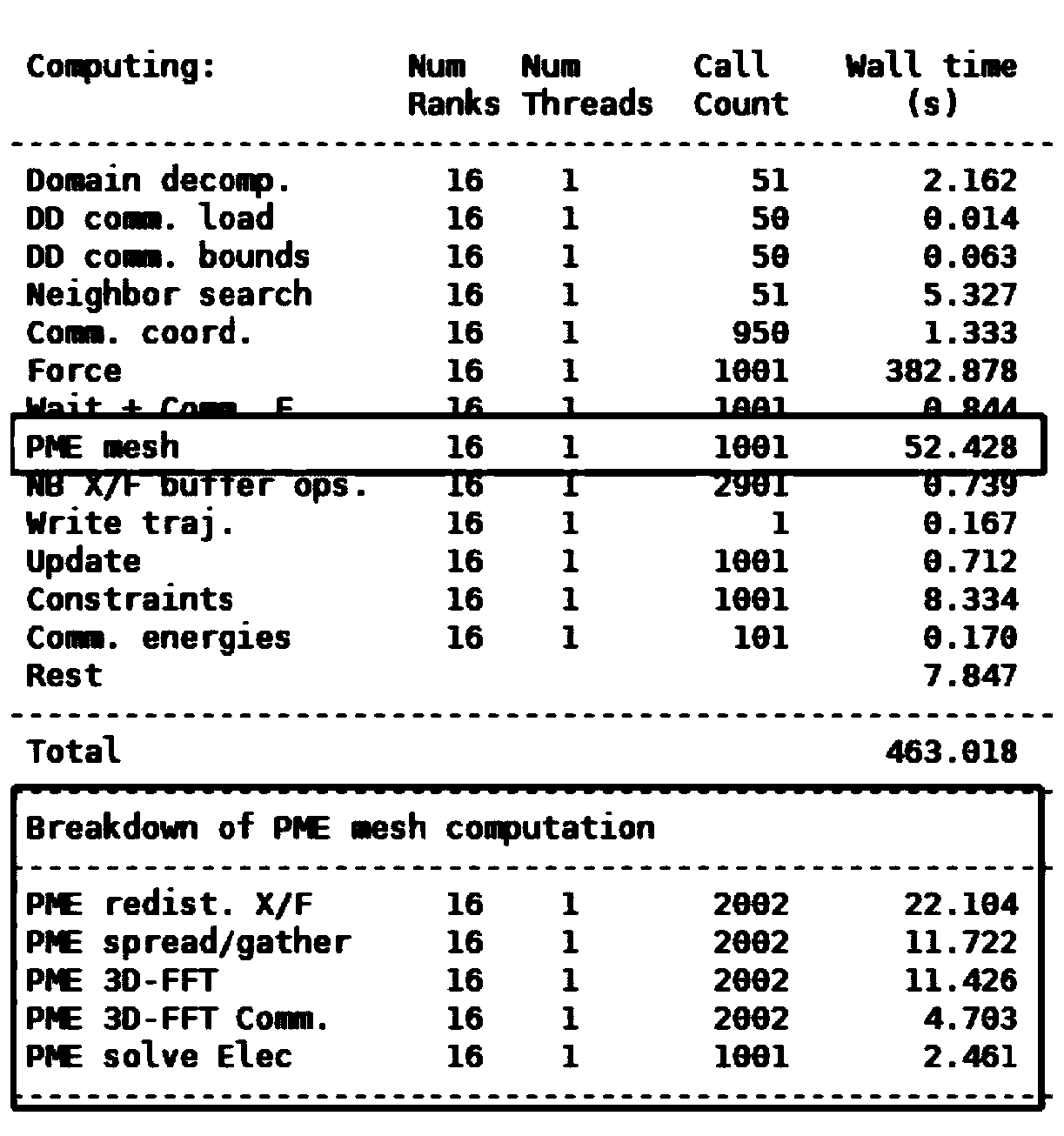
Acceleration optimization method and system for parallel PME of molecular dynamics simulation software
PendingCN111444134AImprove performanceOptimize execution timeSingle instruction multiple data multiprocessorsComputational theoretical chemistryComputational scienceFast Fourier transform
The invention provides an acceleration optimization method and system for parallel PME of molecular dynamics simulation software, and the method comprises the steps: a calculation task is divided intoa plurality of parts, the calculation task is distributed to all slave cores of a super calculation platform, and the calculation is carried out through the slave cores; in the fast Fourier transformin the calculation process, data replication of matrix transposition is completed by utilizing data partitioning and a slave core; and the master core obtains the calculation results of the slave cores in a DMA mode, merges and vectorizes the calculation results, and the master core uses an RDMA technology to replace a traditional MPI technology to obtain data of other master cores. According tothe method, the molecular dynamics simulation software can be smoothly loaded on the super computing platform, and meanwhile, the computing performance can be improved.
Owner:SHANDONG UNIV
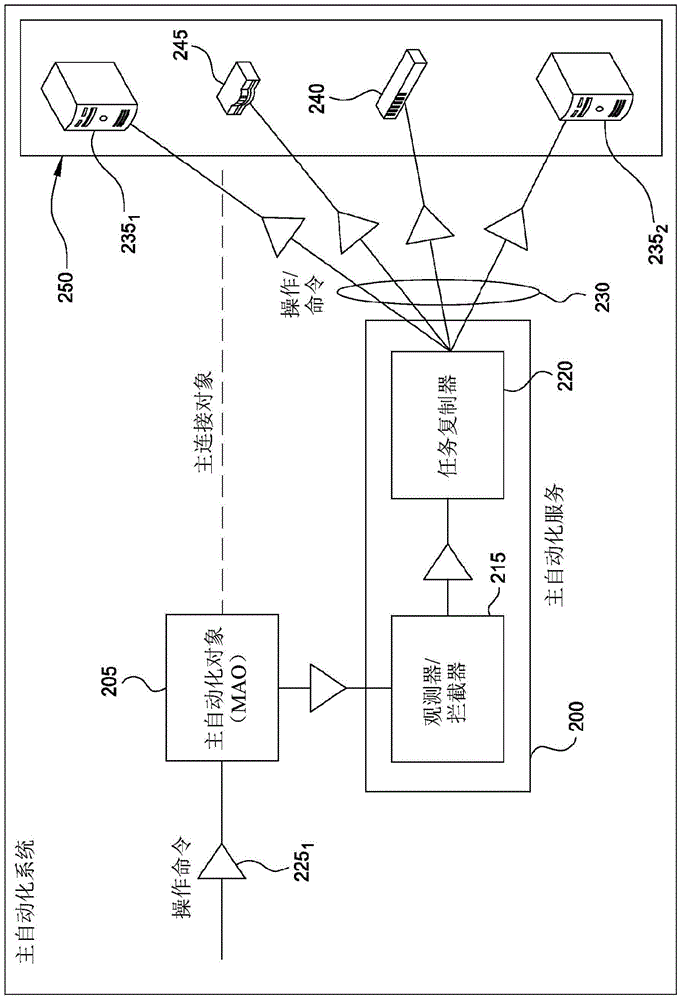
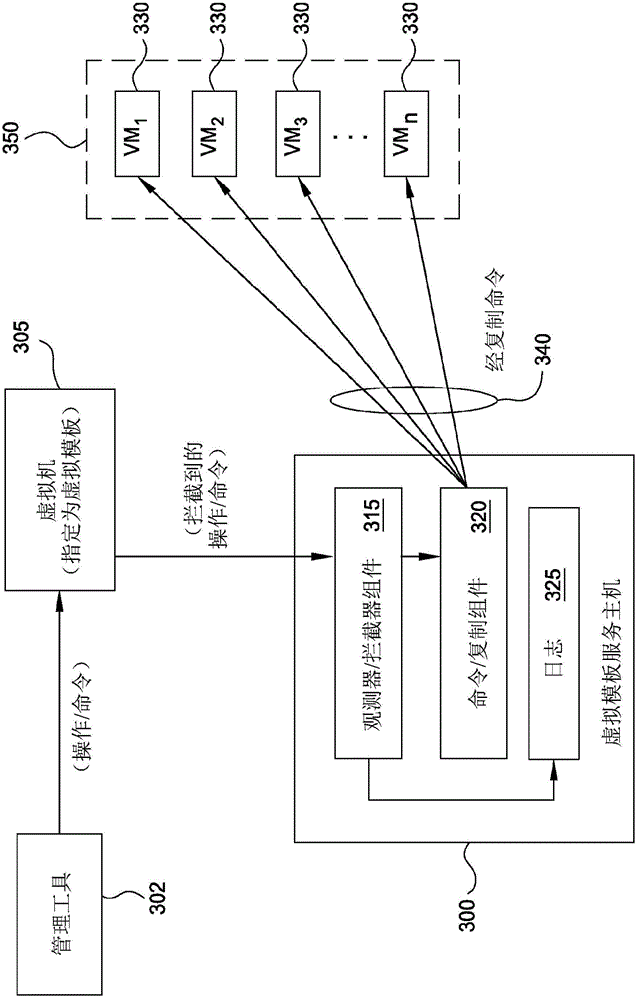
Master automation service
ActiveCN104956332AResource allocationSoftware simulation/interpretation/emulationData centerSoftware engineering
Owner:VCE
Data network and execution environment replication for network automation and network applications
Owner:CIENA
Distributed virtual block storage network
ActiveUS10275179B2Input/output to record carriersTransmissionApplication programming interfaceData access
A virtual storage network may be implemented and exposed as a single virtual namespace, using physical disk storage distributed across multiple computing devices. In various embodiments, each computing device contributing physical disk storage to the virtual storage network may include one or more virtual block devices configured to provide a local interface to the virtual storage network, an application programming interface (API) or other software components to translate the local data access requests into tuple-space operations compatible with the tuple-space data model, and / or a tuple-space storage engine configured to provide access to the data tuple-space of the distributed virtual storage network. The tuple-space storage engine executing on each of the computing devices of the virtual storage network may coordinate via low-level communication to satisfy data access requests from client devices, and to perform data replication and migration tasks so that devices may be seamlessly added or removed from the virtual storage network.
Owner:ORACLE INT CORP
Balancing response times for synchronous I/O requests having different priorities
ActiveUS9652414B1Multiple digital computer combinationsFault locationEngineeringReplication (computing)
A computing environment, such as an data mirroring or replication storage system, may need to process synchronous I / O requests having different priorities in addition to handling I / O requests on the basis of synchronous or asynchronous groupings. The system described herein provides a data storage system that addresses issues involving efficient balancing of response times for servicing synchronous I / O requests having different priorities. Accordingly, the system described herein provides for maintaining an optimal response time for the host-synchronous I / O requests and the optimal throughput of non-host-synchronous I / O requests using a host-synchronous request time window within which processing of non-host-synchronous I / O requests is throttled. The host-synchronous request time window may be selected to enable the optimal response time for the host-synchronous I / O and also to minimize the impact on the overall throughput of the I / O processor of the storage device.
Owner:EMC IP HLDG CO LLC
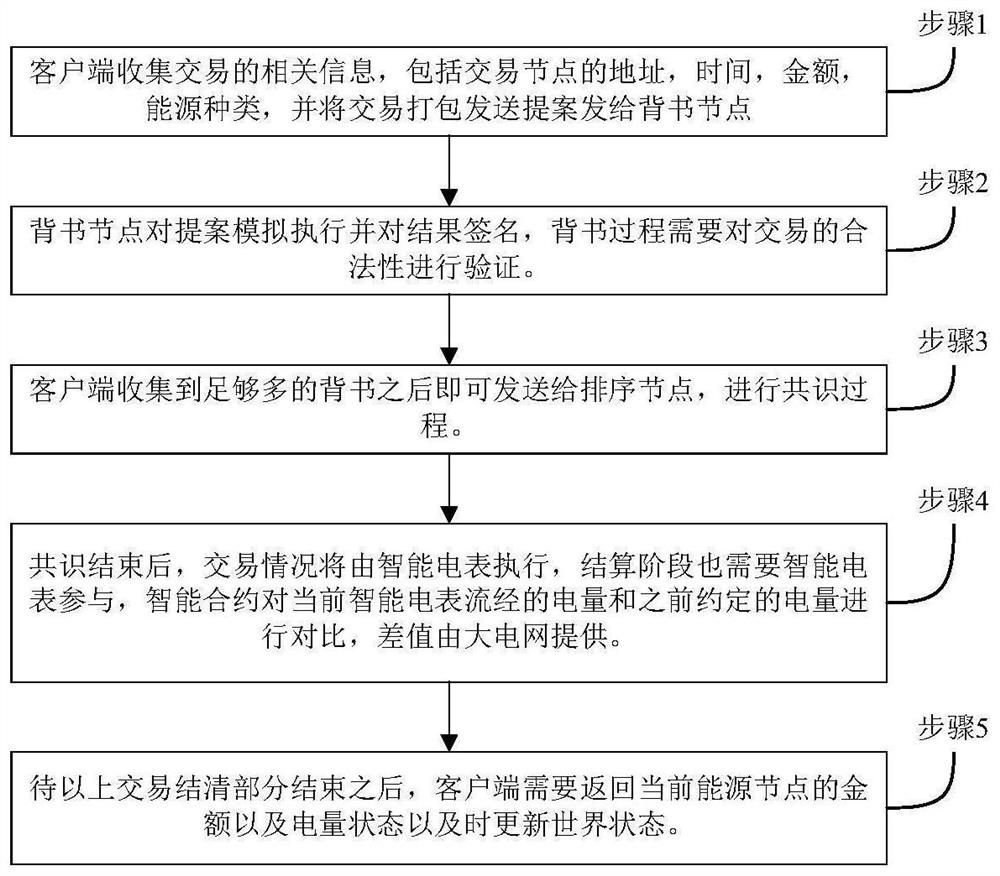
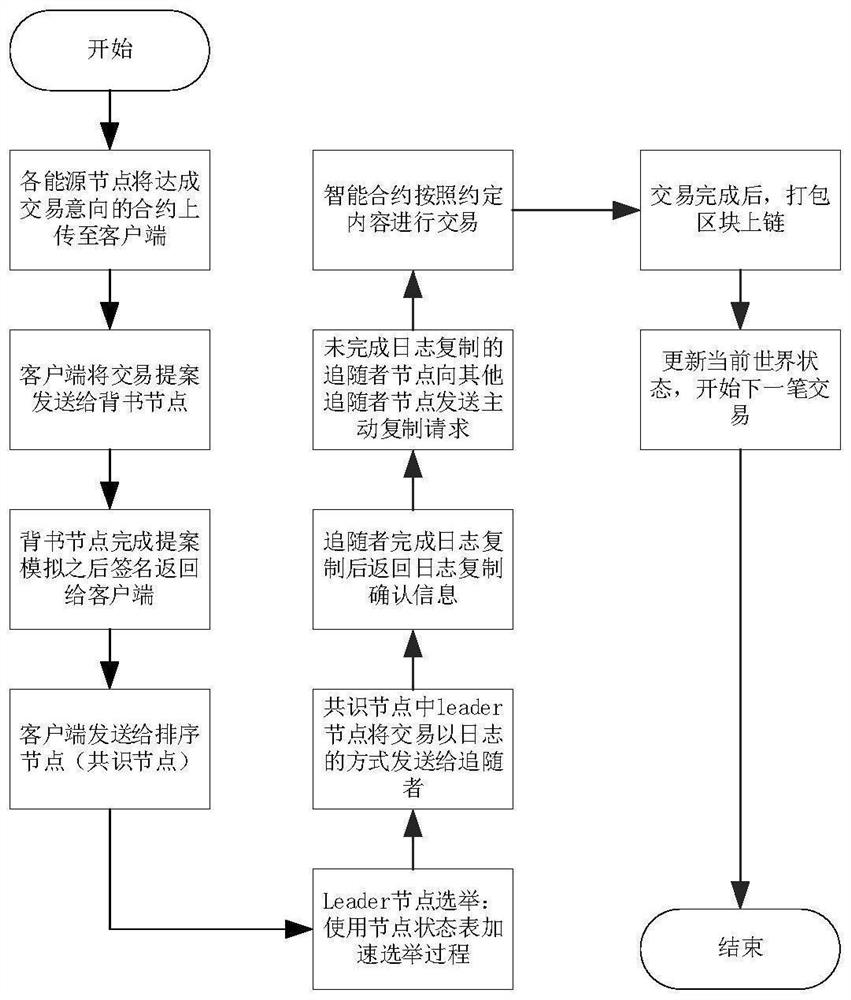
Block chain system for energy transaction based on V-raft consensus algorithm
PendingCN114745135AShorten the timeImprove consensus efficiencyFinanceUser identity/authority verificationFault toleranceAlgorithm
The invention provides a block chain system for energy transaction based on a V-raft consensus algorithm, and belongs to the field of computer software assembly programs and data security. A V-raft consensus algorithm is used in a consensus layer of the system, and according to the improved consensus algorithm, a node state table is added on the basis of an original Raft consensus algorithm to optimize collapse fault tolerance, and the improved consensus algorithm acts on a leader node election stage and a log copying stage respectively; the condition that the state rotation of the following node becomes a candidate due to unstable network to disturb the node log replication process is reduced, and the time of waiting for the following node to reply a day-ahead replication result by the leading node is shortened. Compared with an existing energy block chain network, the method abandons POW and other consensus algorithms which consume computing power and PBFT and other consensus algorithms which cannot dynamically add and delete nodes, and the improved V-raft consensus algorithm is used on the basis of network access auditing of the alliance block chain to accelerate the consensus efficiency of energy transaction and the concurrent processing speed of the transaction.
Owner:SOUTHWEST PETROLEUM UNIV
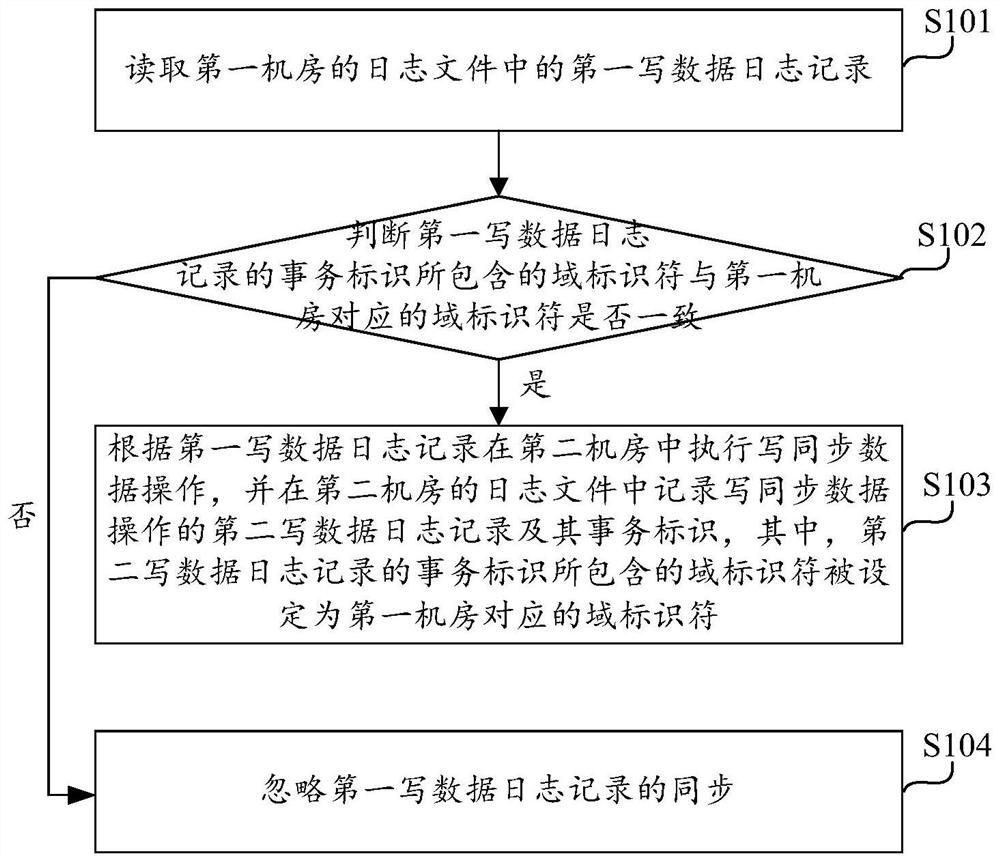
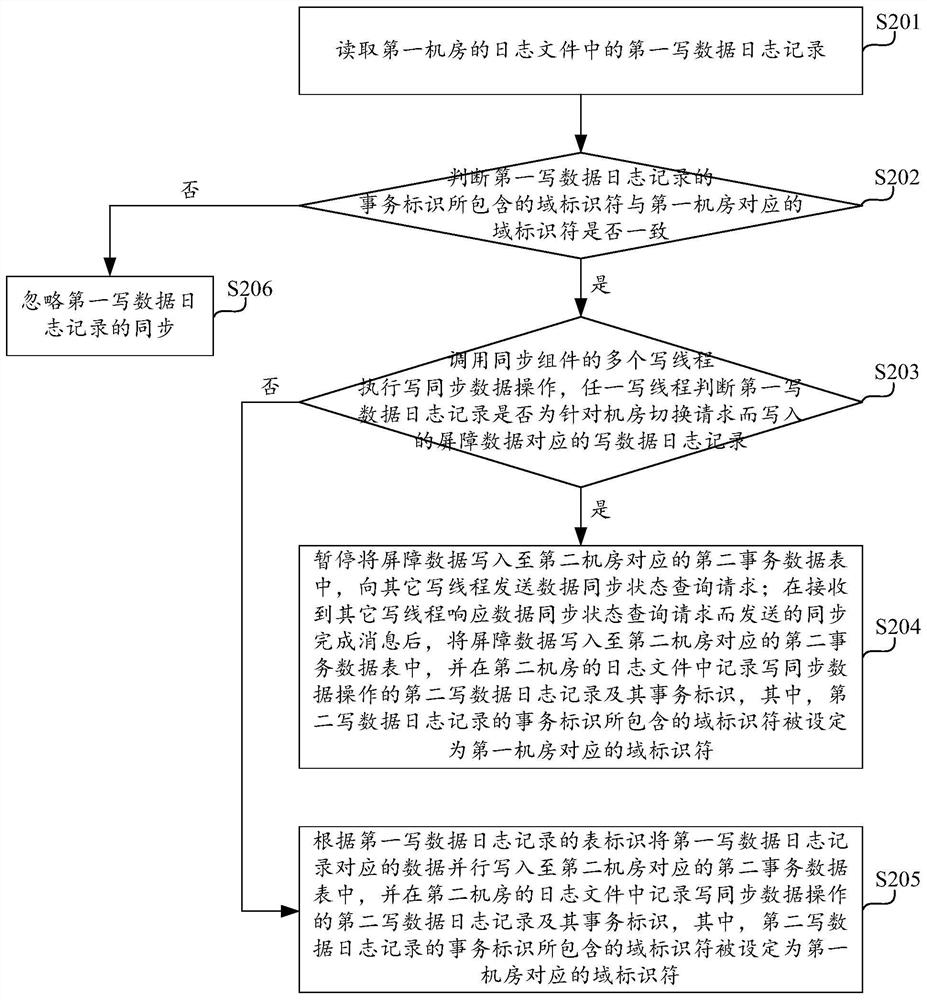
Transaction identifier-based multi-computer-room synchronization method, computing equipment and storage medium
ActiveCN112905696AImprove synchronization efficiencySolve the problem of replication loopbackDatabase distribution/replicationSpecial data processing applicationsData synchronizationEngineering
The invention discloses a transaction identifier-based multi-computer-room synchronization method, computing equipment and a storage medium. The method comprises the following steps: reading a first write data log record in a log file of a first machine room, and judging whether a domain identifier contained in a transaction identifier of the first write data log record is consistent with a domain identifier corresponding to the first machine room or not; if yes, performing synchronous data writing operation in a second machine room according to the first data writing log record, and recording a second data writing log record of the synchronous data writing operation and a transaction identifier of the second data writing log record in a log file of the second machine room, wherein the domain identifier contained in the transaction identifier of the second write data log record is set as the domain identifier corresponding to the first computer room; if not, neglecting the synchronization of the first write data log record, so that loop replication is broken, the problem of replication loopback in multi-machine-room bidirectional synchronization is solved, and the data synchronization efficiency is further improved due to the fact that the judgment process is simple.
Owner:ZHANGYUE TECH CO LTD
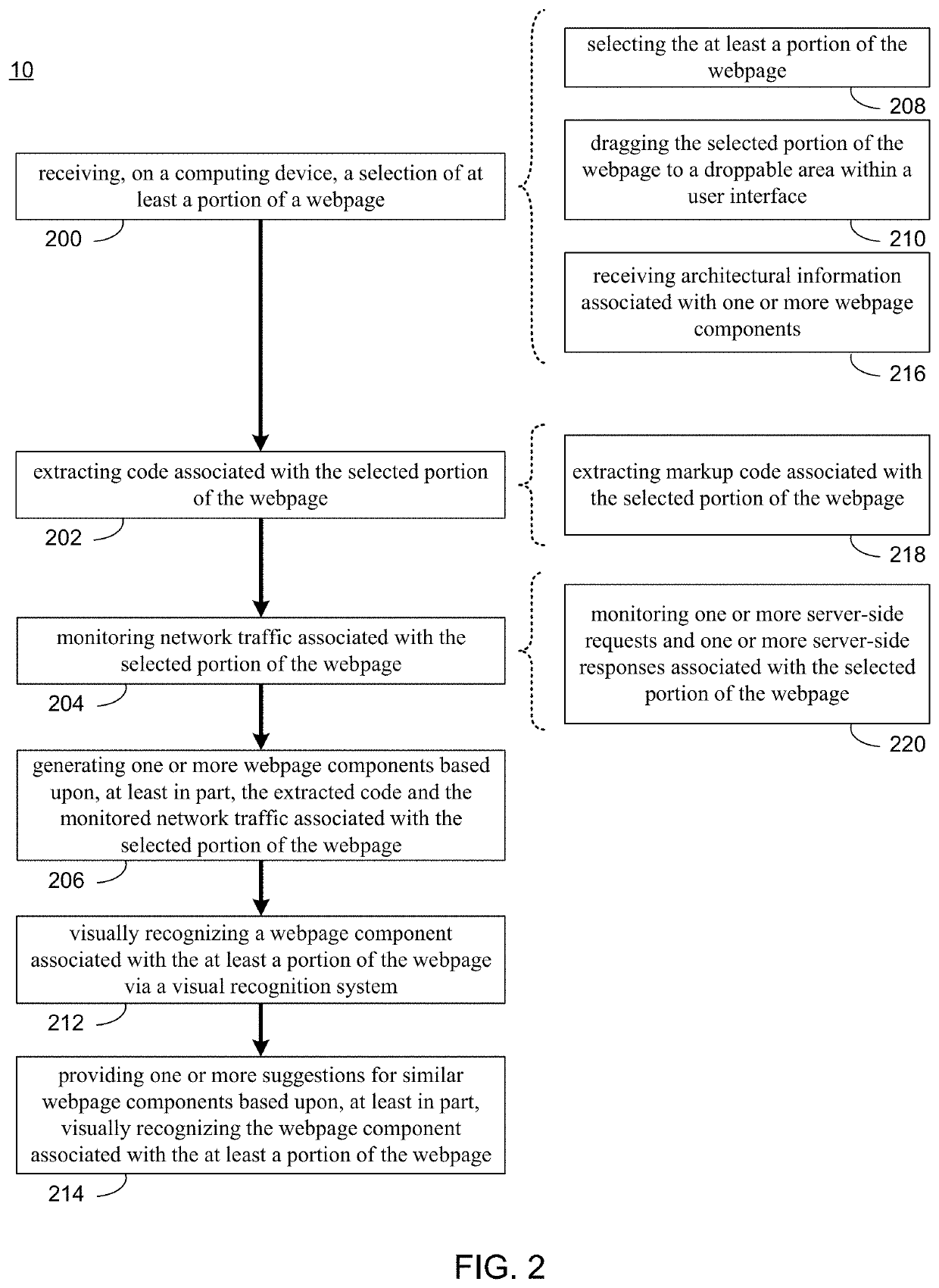
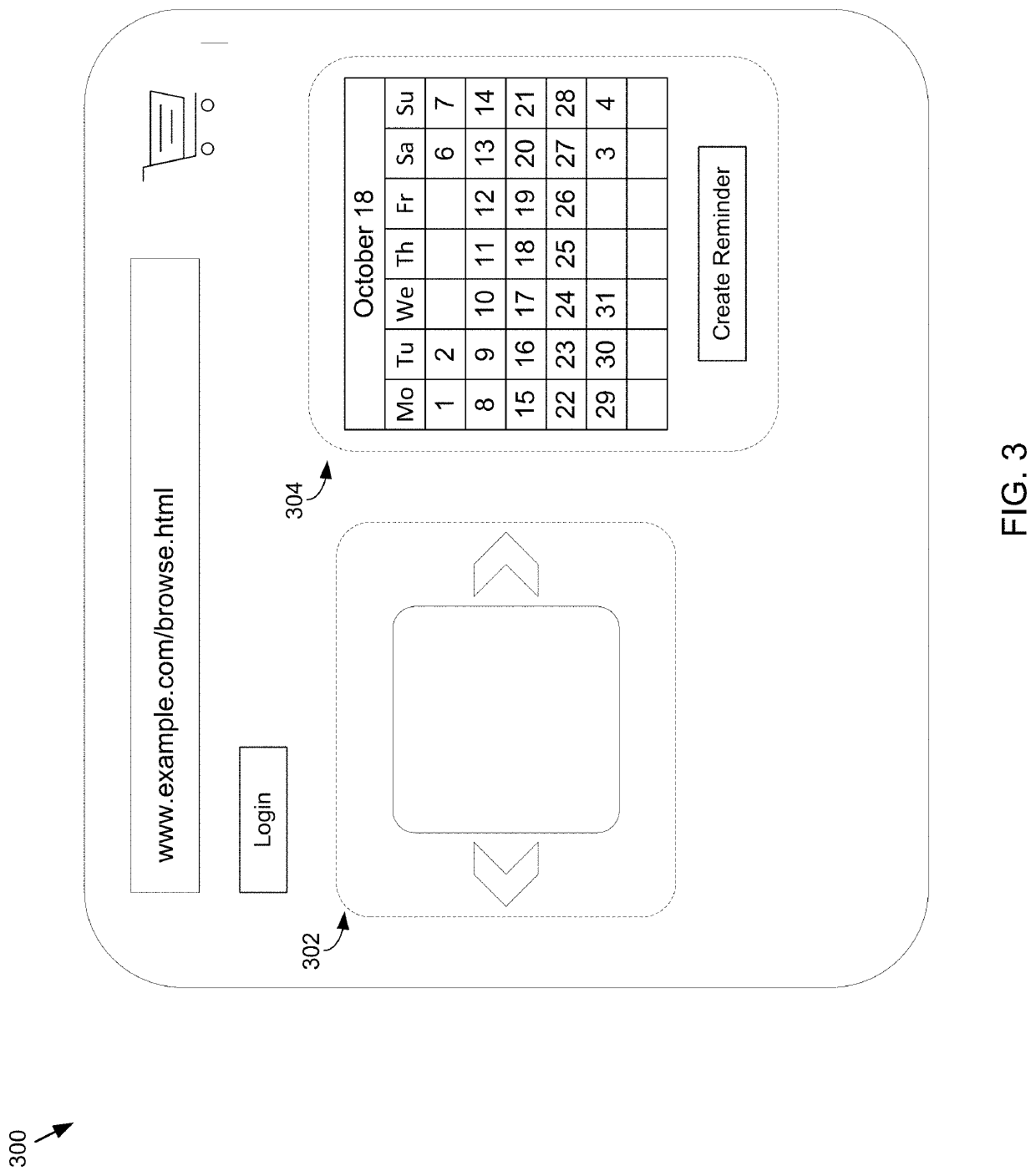
Webpage component replication system and method
InactiveUS20200151241A1Text processingWebsite content managementInternet trafficSoftware engineering
A method, computer program product, and computing system device for receiving a selection of at least a portion of a webpage. Code associated with the selected portion of the webpage may be extracted. Network traffic associated with the selected portion of the webpage may be monitored. One or more webpage components may be generated based upon, at least in part, the extracted code and the monitored network traffic associated with the selected portion of the webpage.
Owner:IBM CORP
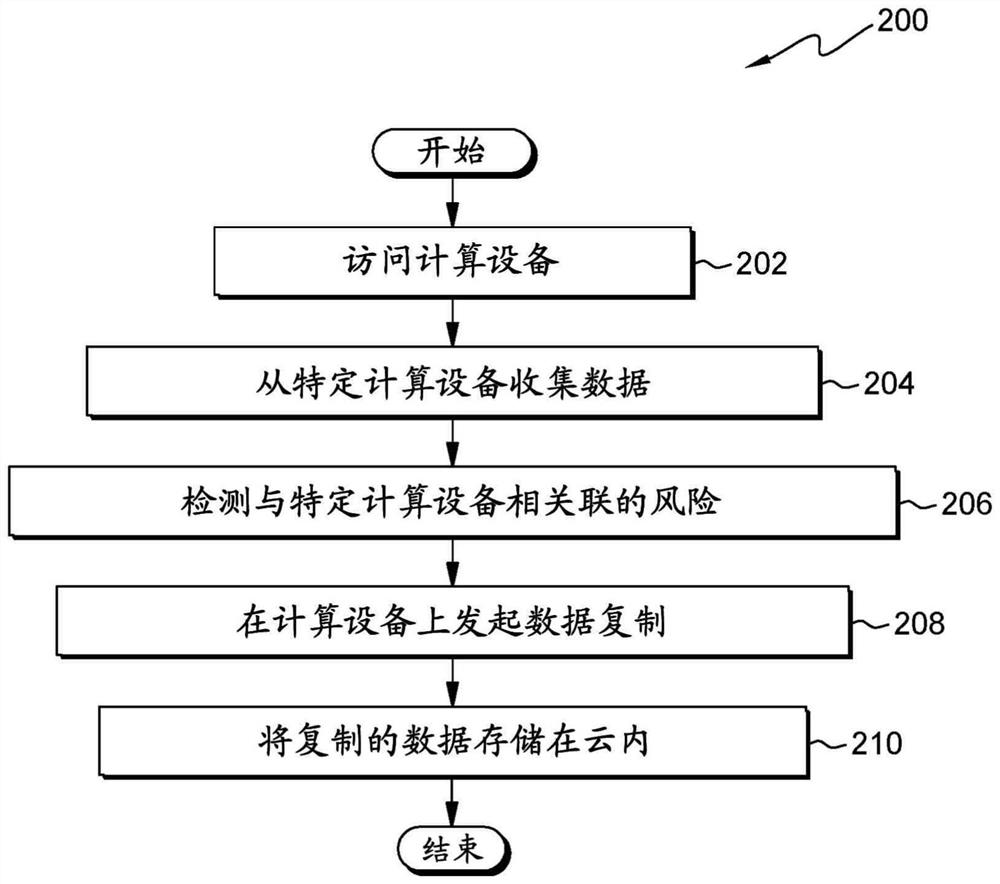
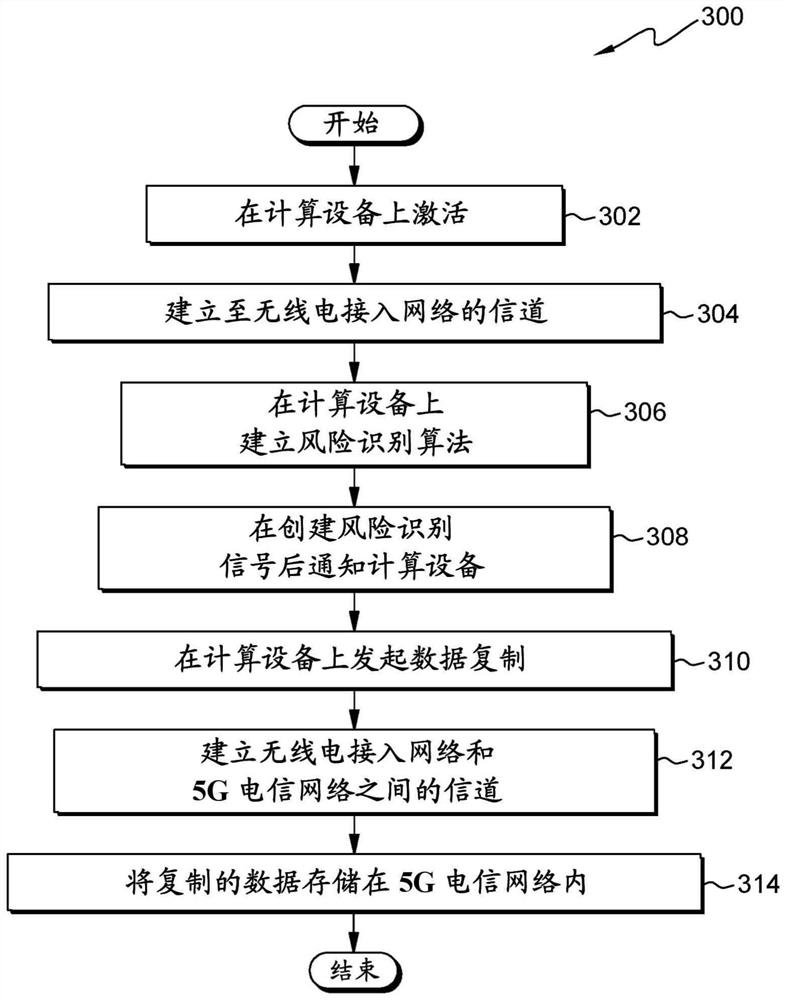
Risk detection of data loss for 5G-enabled devices
PendingCN114787803AError detection/correctionPlatform integrity maintainanceCloud storage systemReplication (computing)
A computer system, computer program product, and method are provided that include: collecting data replicable from a computing device; detecting a risk of the computing device, wherein detecting the risk includes detecting a surrounding environment, a location, a speed, and a condition of the computing device; upon determining that the risk reaches a predetermined threshold, initiating data replication on the computing device; and storing the copied data in a cloud storage system using a 5G network.
Owner:IBM CORP
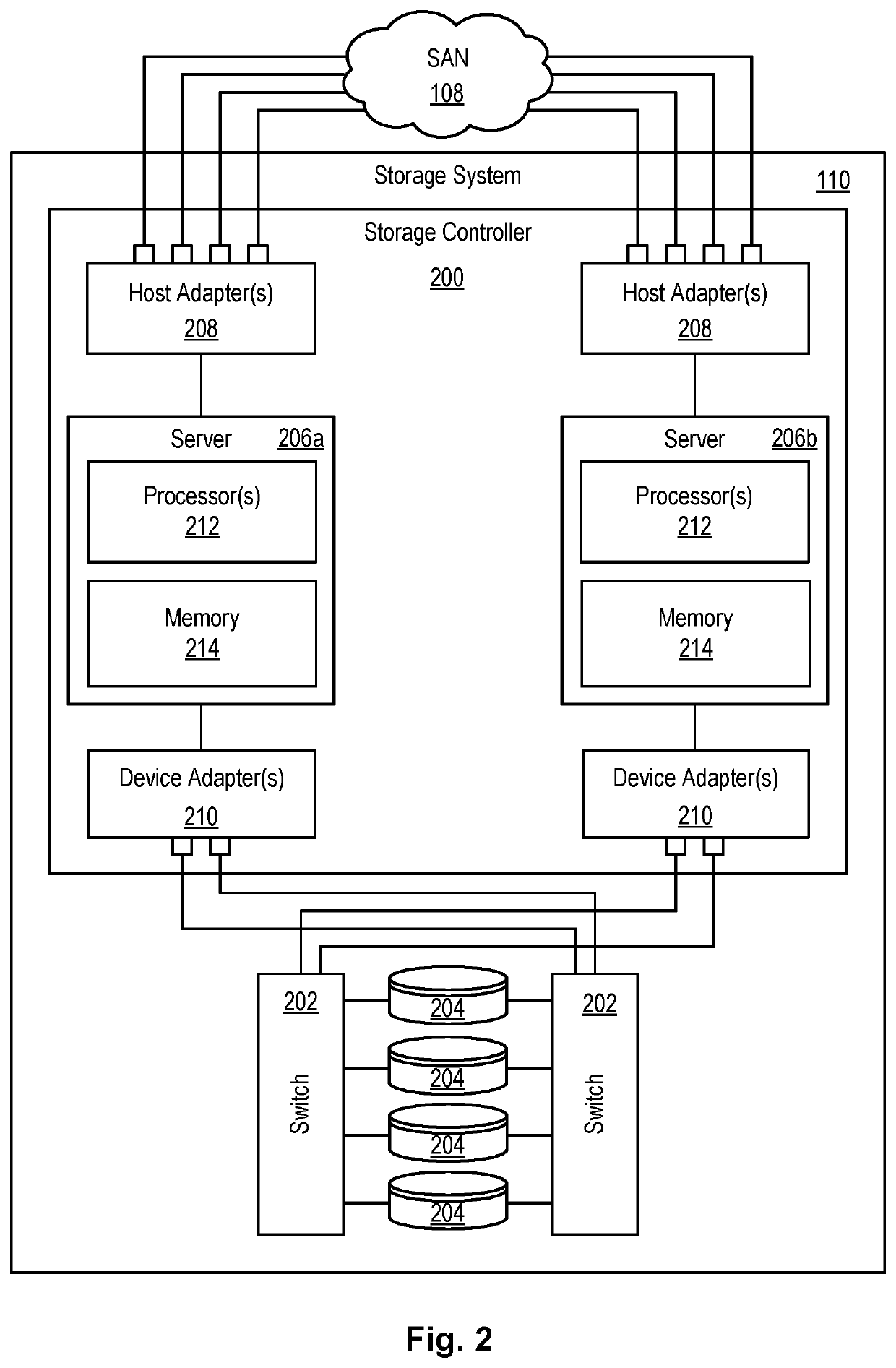
Remote health monitoring in data replication environments
PendingUS20210011821A1Input/output to record carriersRedundant hardware error correctionEngineeringReplication (computing)
A method for more effectively utilizing computing resources in a data replication environment is disclosed. In one embodiment, such a method detects, at a primary system, activity occurring on the primary system. This activity is recorded in systems logs located at the primary system. The method automatically mirrors the system logs from the primary system to a secondary system that is in a mirroring relationship with the primary system. The system logs are analyzed at the secondary system. In the event abnormal activity is detected in the system logs at the secondary system, the method automatically sends, from the secondary system to the primary system, one or more commands that are designed to address the abnormal activity. A corresponding system and computer program product are also disclosed.
Owner:IBM CORP
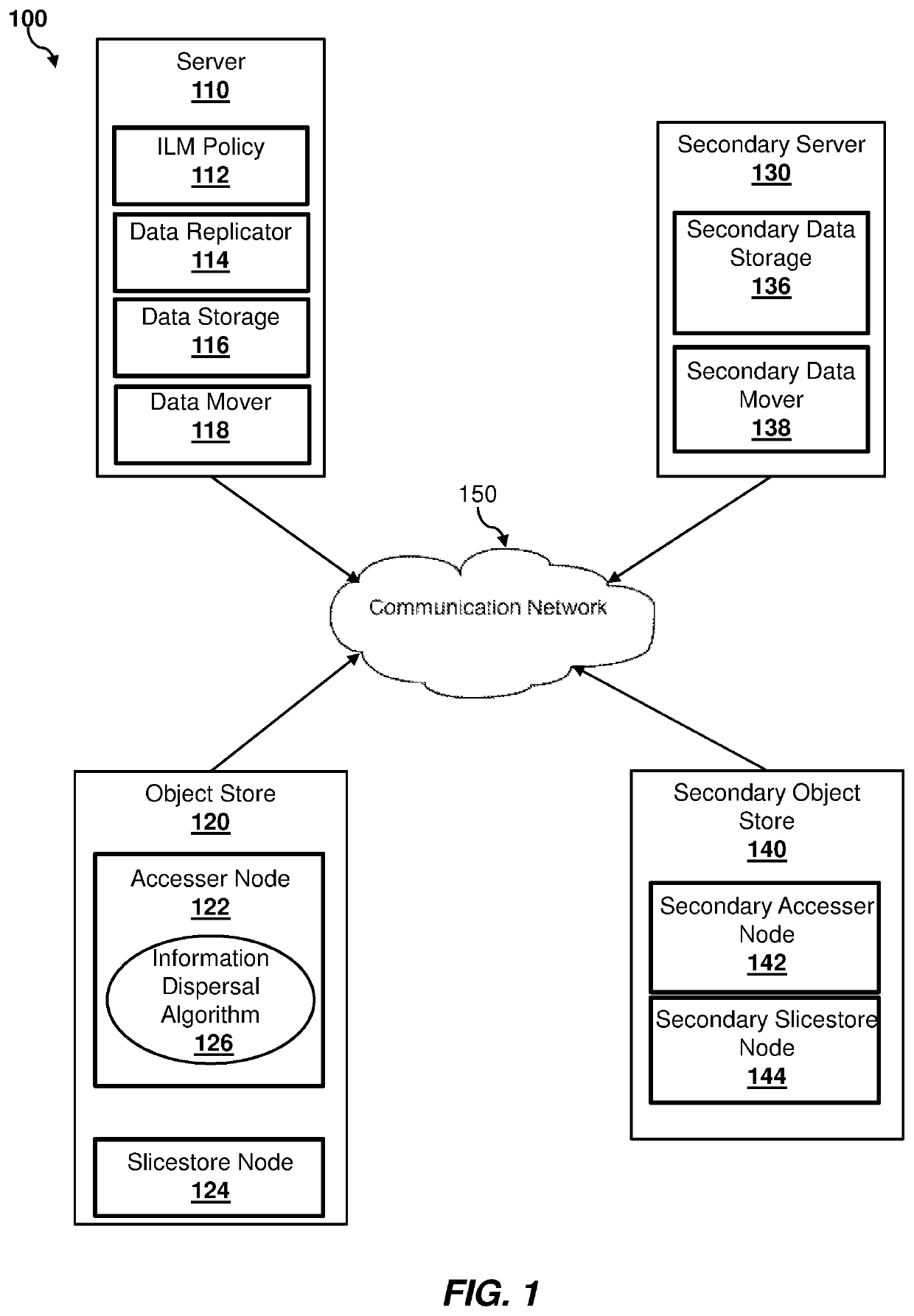
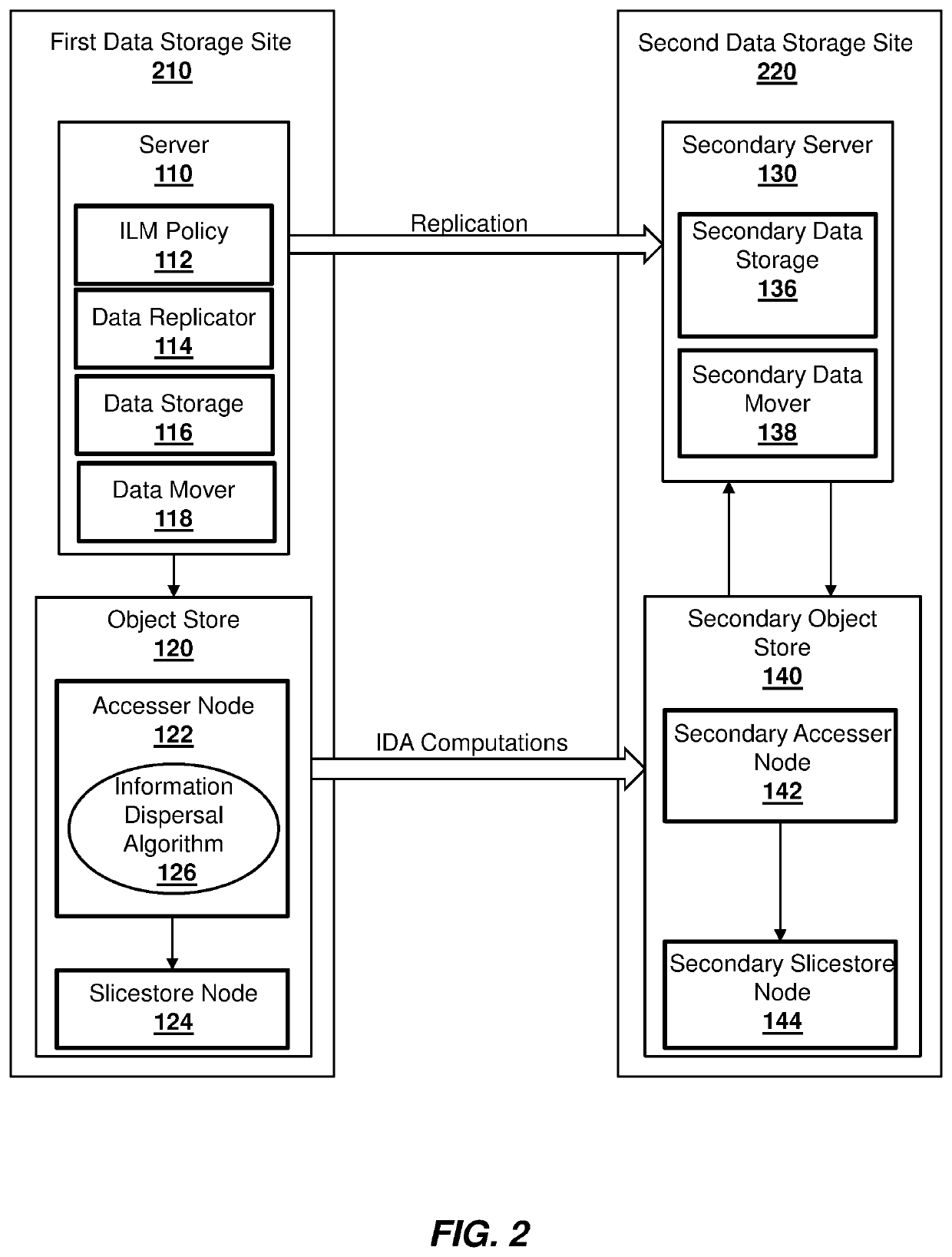
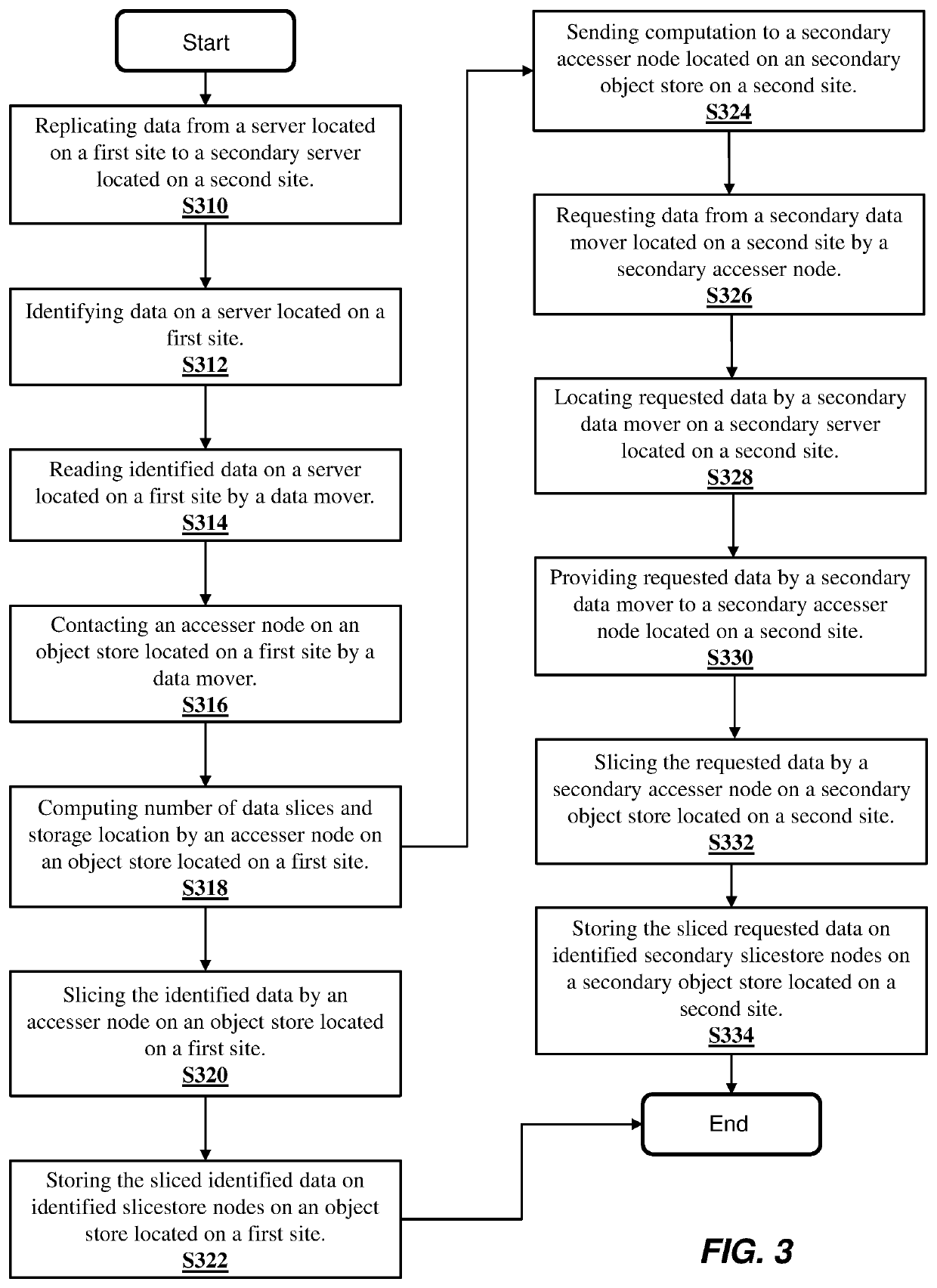
Optimized data replication in multi-tier storage environment
ActiveUS10552082B2Efficient and cost-effectiveInput/output to record carriersTransmissionInformation dispersalSituated computing
The method, computer program product and computer system of the present invention may include a computing device that replicates data from a first data storage site, which may have a plurality of data storage tiers, to one or more second data storage sites. The computing device may identify a portion of the data on a first tier of the first data storage site to be inactive and move the inactive data to a second tier of the first data storage site. The computing device may compute a number of slices to slice the inactive data into and a location to store the slices of inactive data using an information dispersal algorithm. The computing device may send the computed number of slices and storage location for the inactive data to the one or more second data storage sites to apply to the data replicated from the first data storage site.
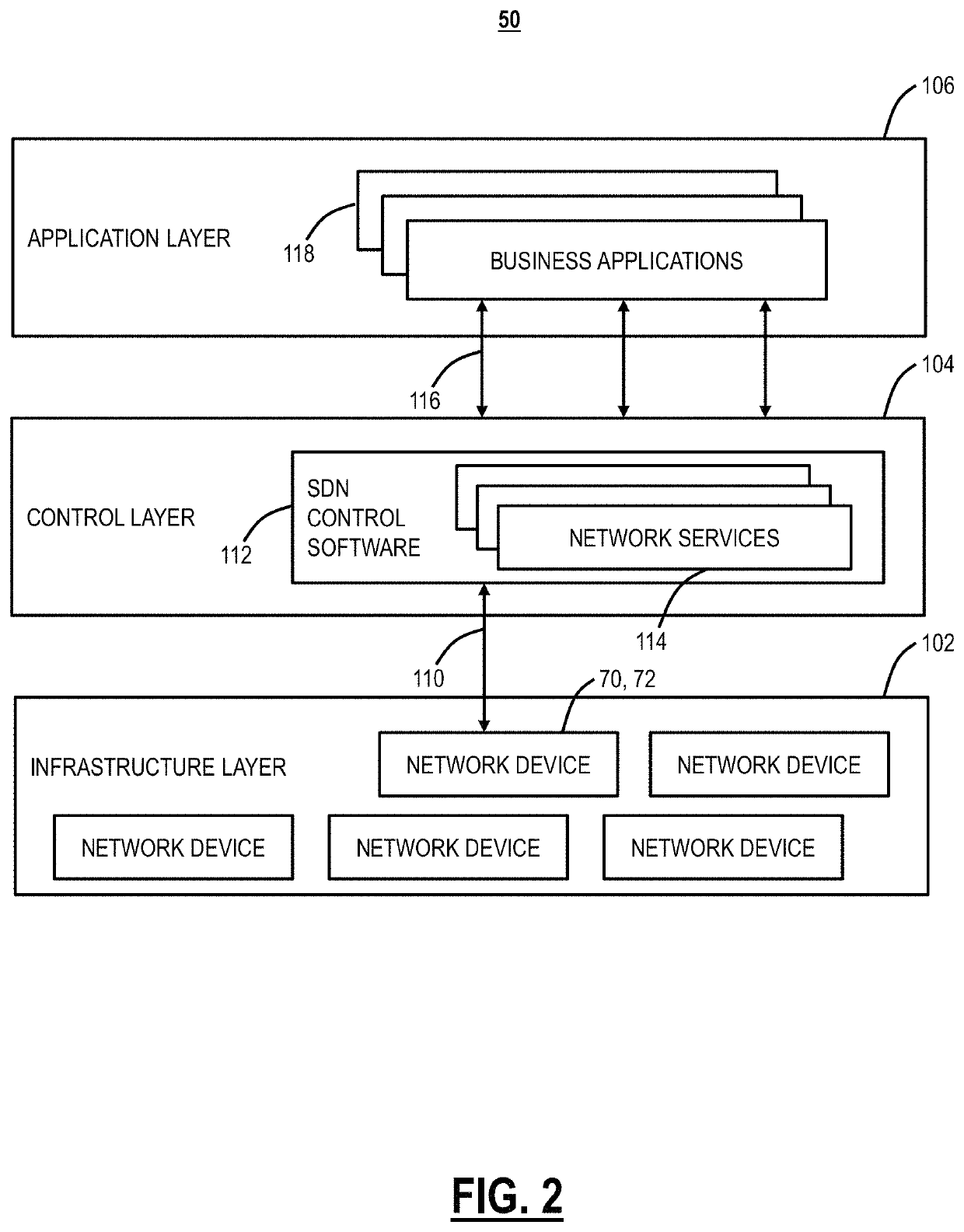
Owner:INT BUSINESS MASCH CORP
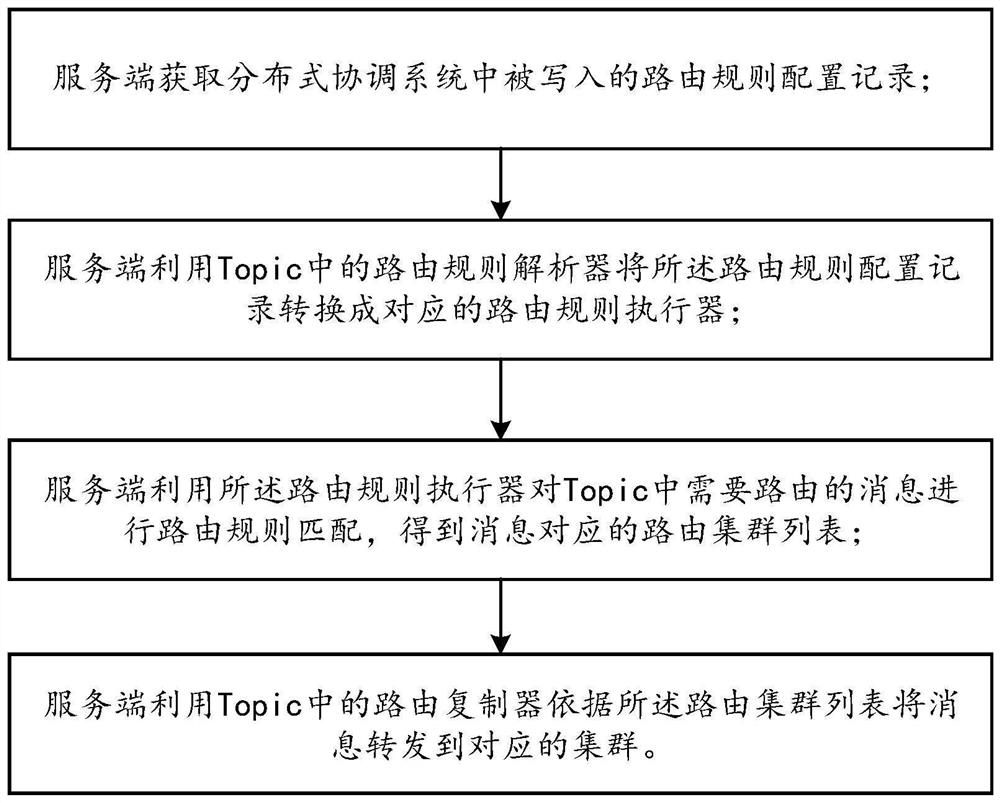
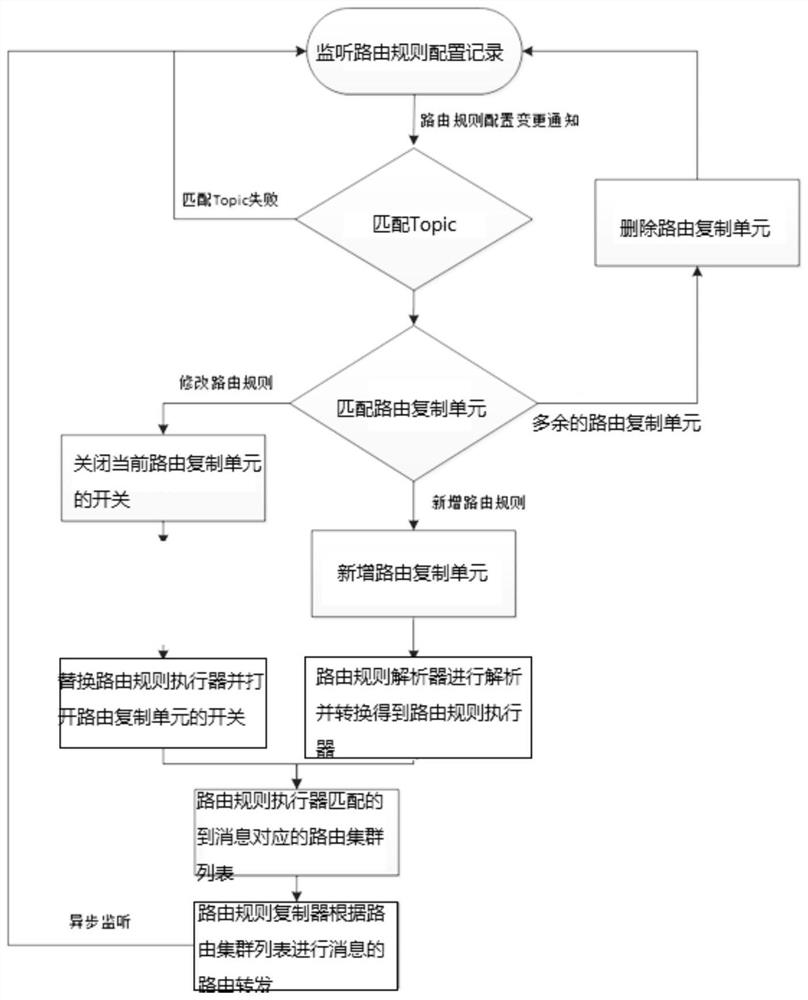
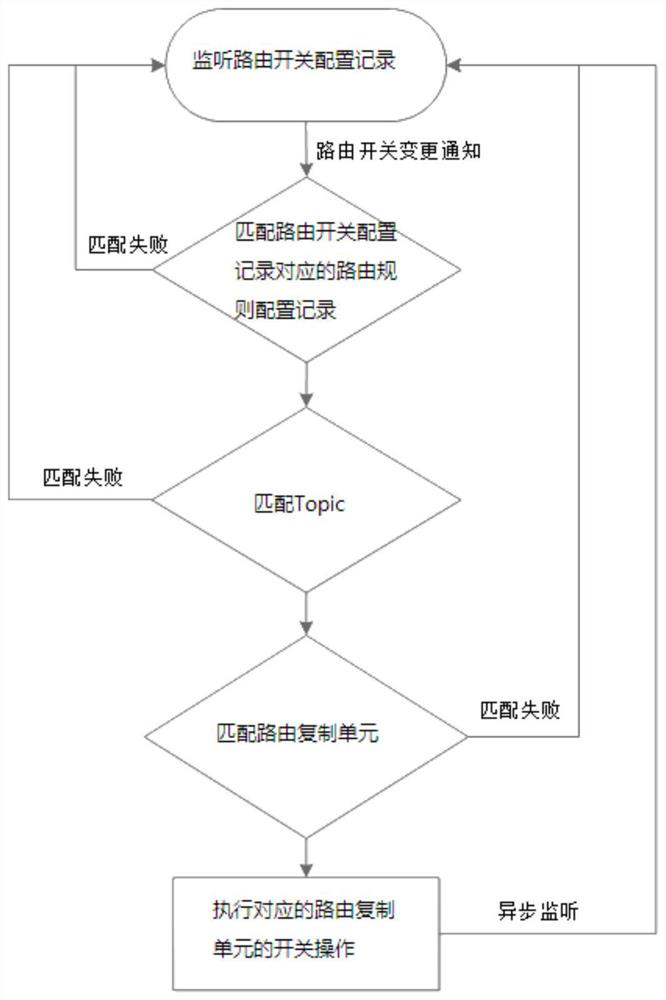
Message cross-cluster routing forwarding method and system
ActiveCN112511408AReduce maintenance costsSave computing resourcesData switching networksEngineeringReplication (computing)
The invention discloses a message cross-cluster routing forwarding method and system, and the method comprises the steps that a server obtains a routing rule configuration record written in a distributed coordination system; the server converts the routing rule configuration record into a corresponding routing rule executor by using a routing rule analyzer in the Topic; the server performs routingrule matching on messages needing to be routed in the Topic by utilizing the routing rule executor to obtain a routing cluster list corresponding to the messages; and the server forwards the messageto the corresponding cluster according to the routing cluster list by using a routing duplicator in the Topic. According to the message cross-cluster routing forwarding system provided by the invention, the message cross-cluster routing forwarding method is adopted, and the cross-cluster routing replication forwarding of the message is realized by relying on the distributed coordination system atthe server to perform routing rule configuration, so that the consumption of additional computing resources is avoided, and the maintenance cost is reduced.
Owner:SUNING CLOUD COMPUTING CO LTD
System and method for synchronous replication write handling
ActiveUS11372573B2Input/output to record carriersError detection/correctionCallbackSoftware engineering
A method, computer program product, and computer system for receiving, at a computing device, a write request from a host, wherein a first portion of a process may receive the write request. A callback and context may be set in the write request by the first portion of the process. The write request may be passed to a second portion of the process. The first process may be provided with the context. The first process may use the context to replicate the write request data to a destination.
Owner:EMC IP HLDG CO LLC
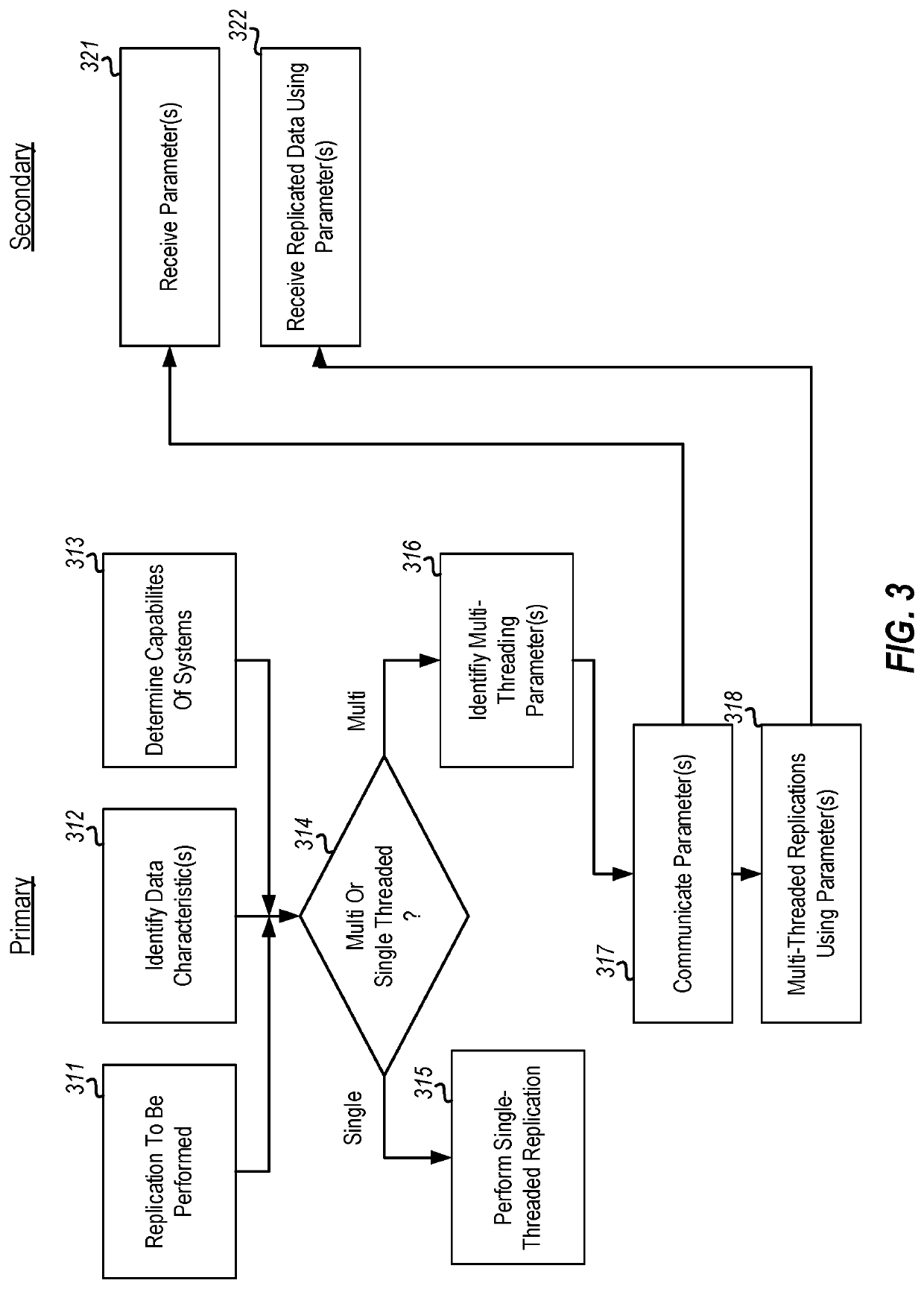
Threading of replication based on data type
ActiveUS20220253217A1Rapid and efficient replicationLess timeInput/output to record carriersConcurrent instruction executionData classTheoretical computer science
Replication of data from a primary computing system to a secondary computing system. The replication is single-threaded or multi-threaded depending on one or more characteristics of the data to be replicated. As an example, the characteristics could include the type of data being replicated and / or the variability on that data. Also, the multi-threading capabilities of the primary and secondary computing systems are determined. Then, based on the identified one or more characteristics of the data, the primary computing system decides whether to perform multi-threaded replication and the multi-threading parameters of the replication based on the one or more characteristics of that data, as well as on the multi-threading capabilities of the primary and secondary computing system.
Owner:MICROSOFT TECH LICENSING LLC
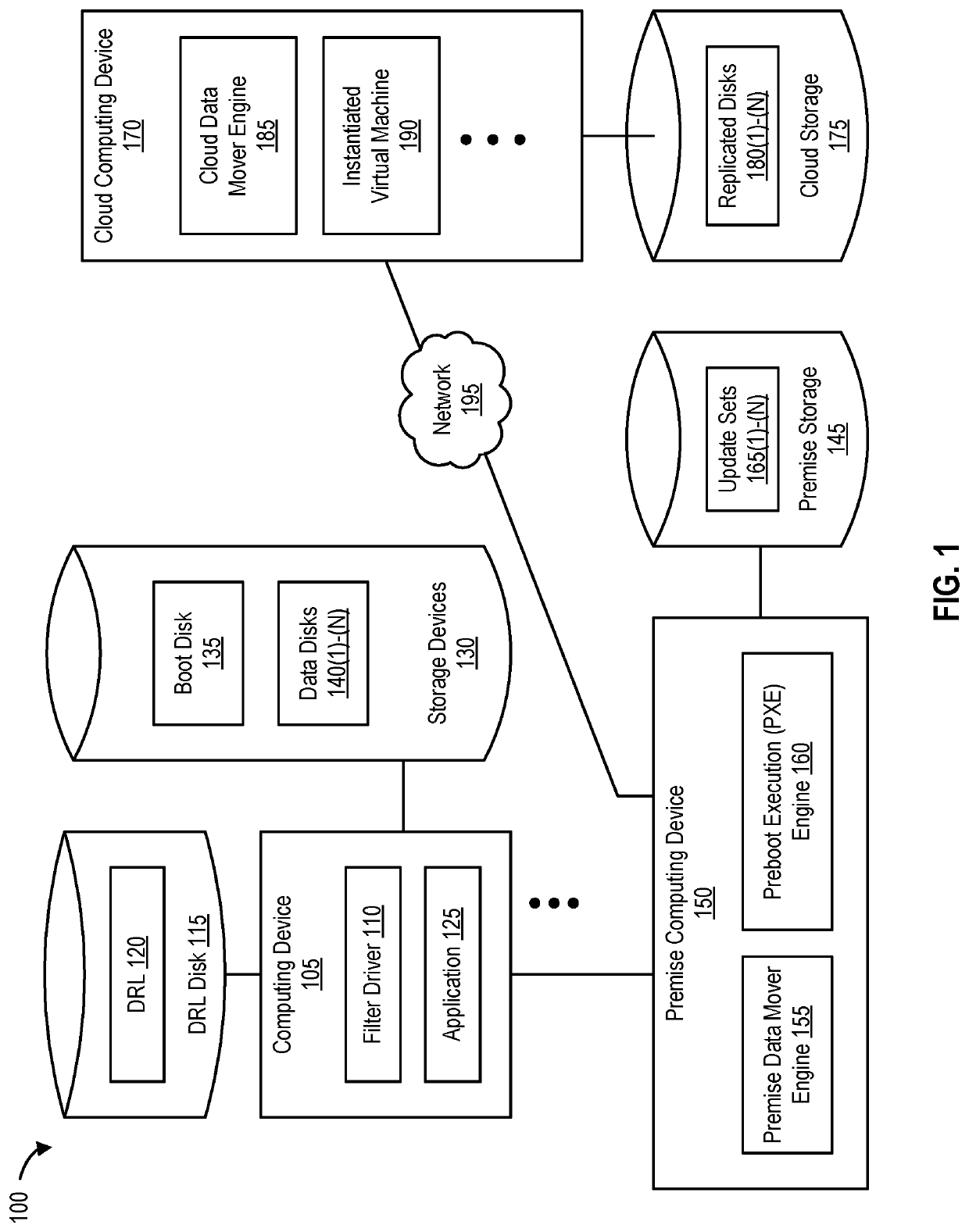
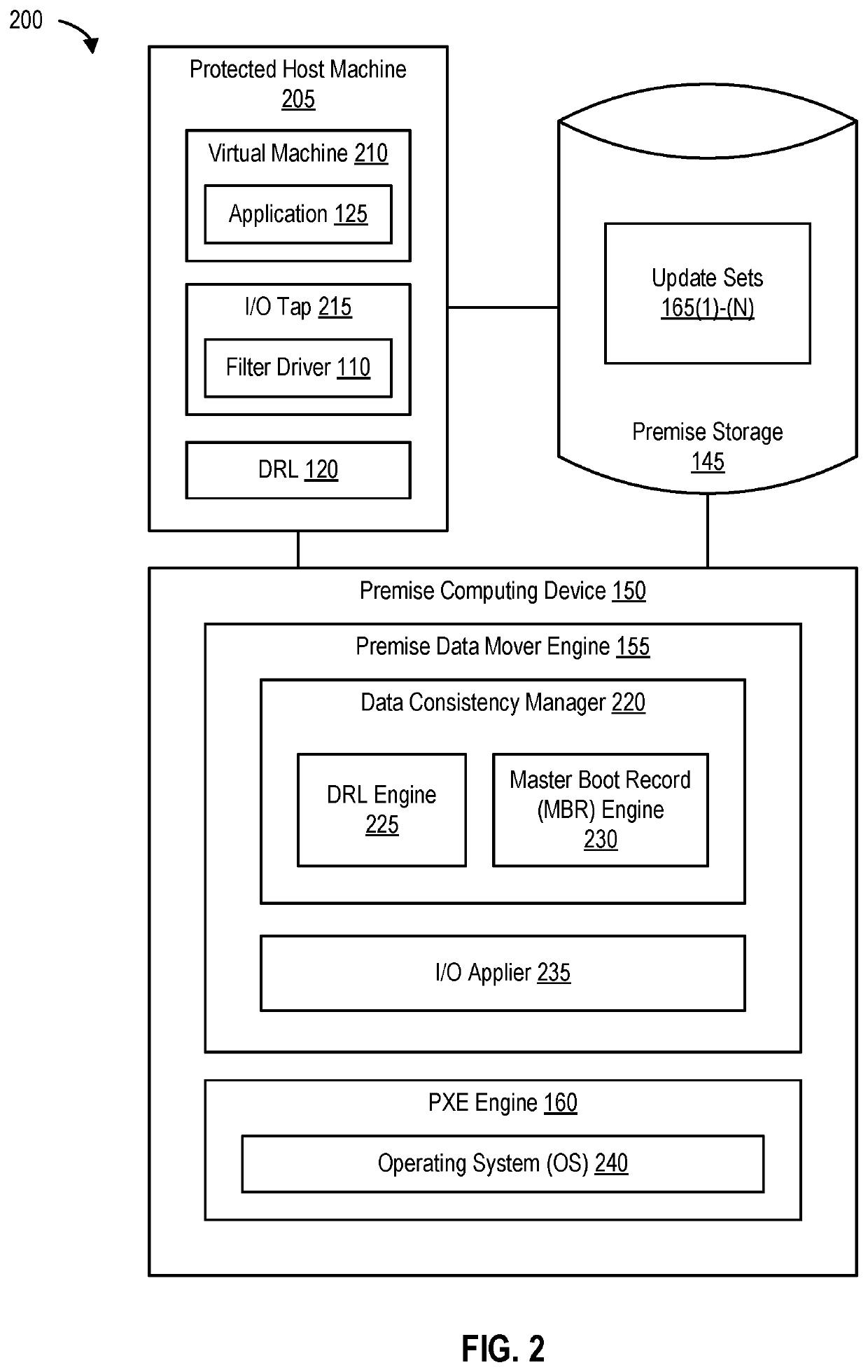
Data consistency during reverse replication
ActiveUS10684788B1Input/output to record carriersRedundant operation error correctionReplication (computing)Record
Disclosed herein are methods, systems, and processes to provide and maintain data consistency during reverse replication. It is determined that a migrate operation or a reverse replication operation has been requested. Upon determining that the migrate operation or the reverse replication operation has been requested, a resynchronization identifier is set in a dirty region log (DRL) associated with a computing device that is subject to the migrate operation or the reverse replication operation. In response to the operation being the reverse replication operation, a master boot record (MBR) sector of a boot disk associated with the computing device is overwritten.
Owner:VERITAS TECH
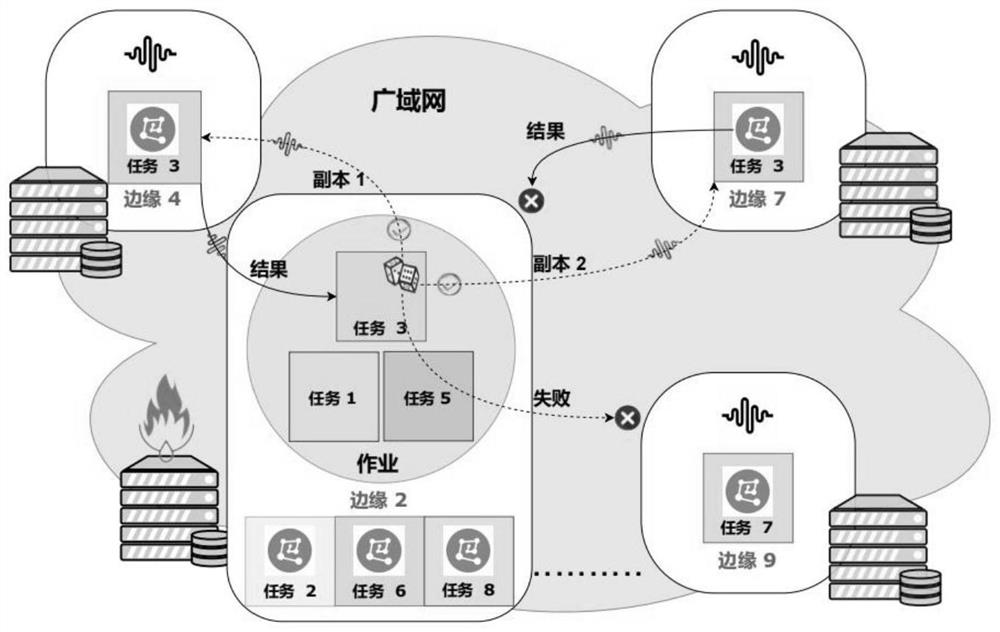
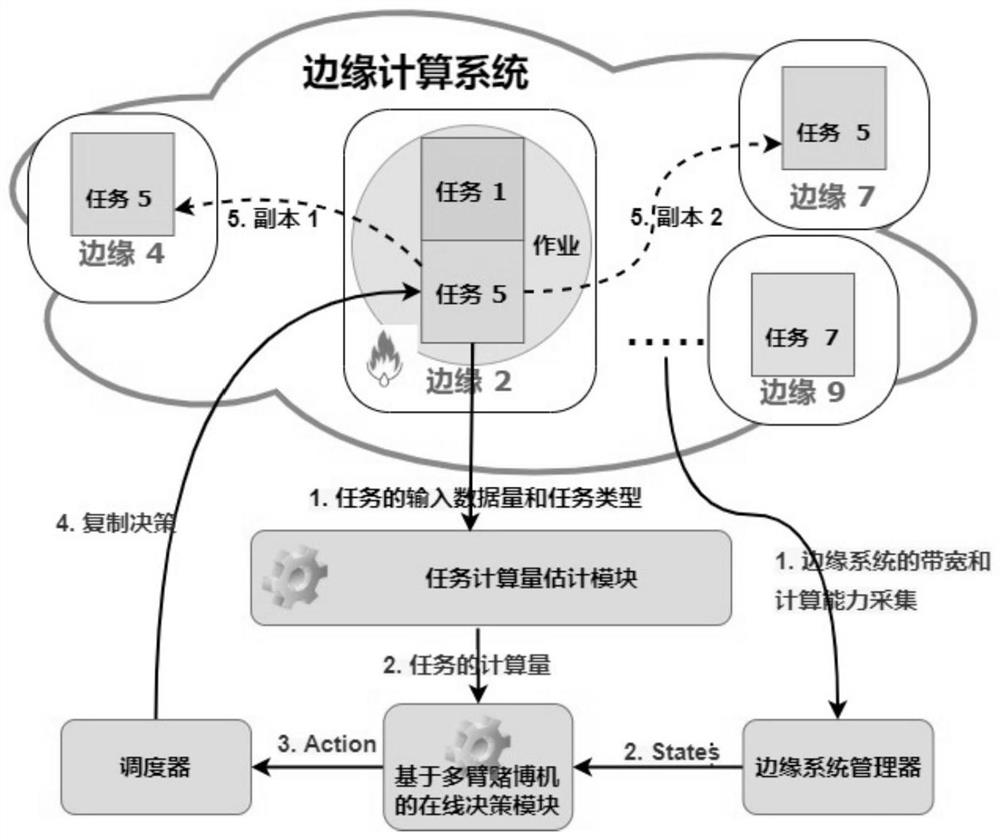
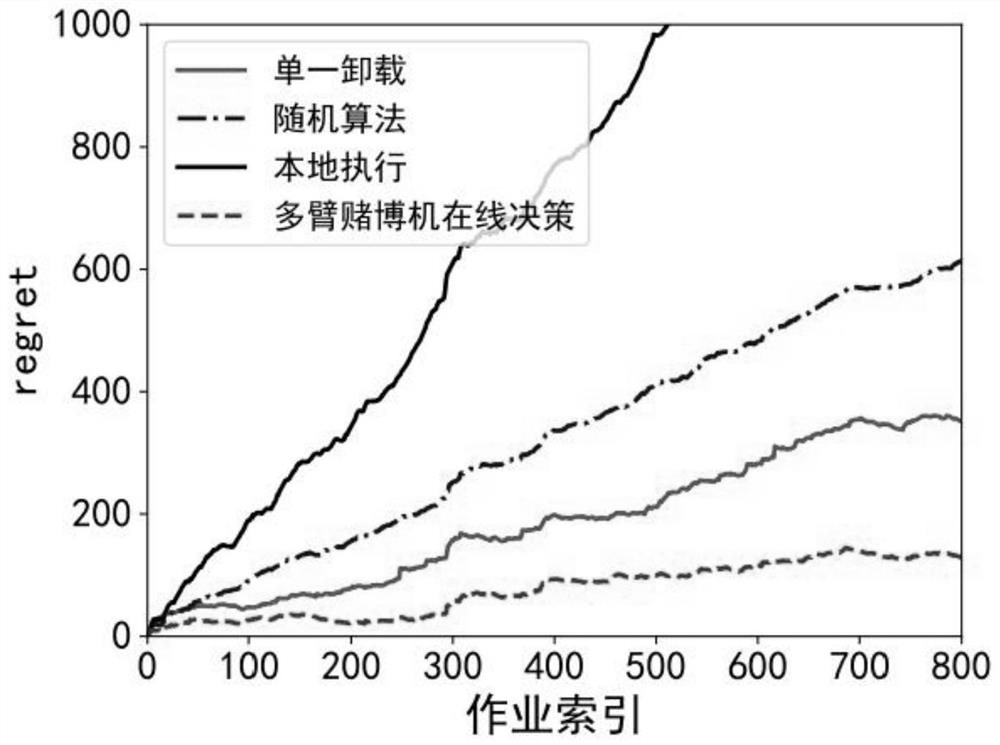
Dynamic task replication method, device and system in edge computing environment
PendingCN114090218AImprove performanceReduce queuingProgram initiation/switchingResource allocationTime delaysParallel computing
The invention discloses a dynamic task replication method, device and system in an edge computing environment. The method comprises the following steps: establishing an optimization problem by taking the minimum difference regret between the total completion time of a job in an edge environment and the total time delay of job completion under an ideal optimal replication decision as a target; solving an optimization problem by using a task replication decision algorithm based on a multi-armed bandit, comprising the following steps of: estimating a task calculation amount wt according to a task type of a task and the size of input data at the beginning of a first time slot; for each task t, calculating the lower confidence limit of the time delay of copying the task t from the edge cluster i to the edge cluster j, determining all available edge clusters, selecting rt smaller available edge clusters as target edge clusters, and copying the task to all the target edge clusters for execution. According to the method, the algorithm based on the multi-armed bandit is applied to the task replication problem of the edge computing system for the first time, and the method has excellent time delay performance and service reliability.
Owner:JIANGSU ELECTRIC POWER CO +2
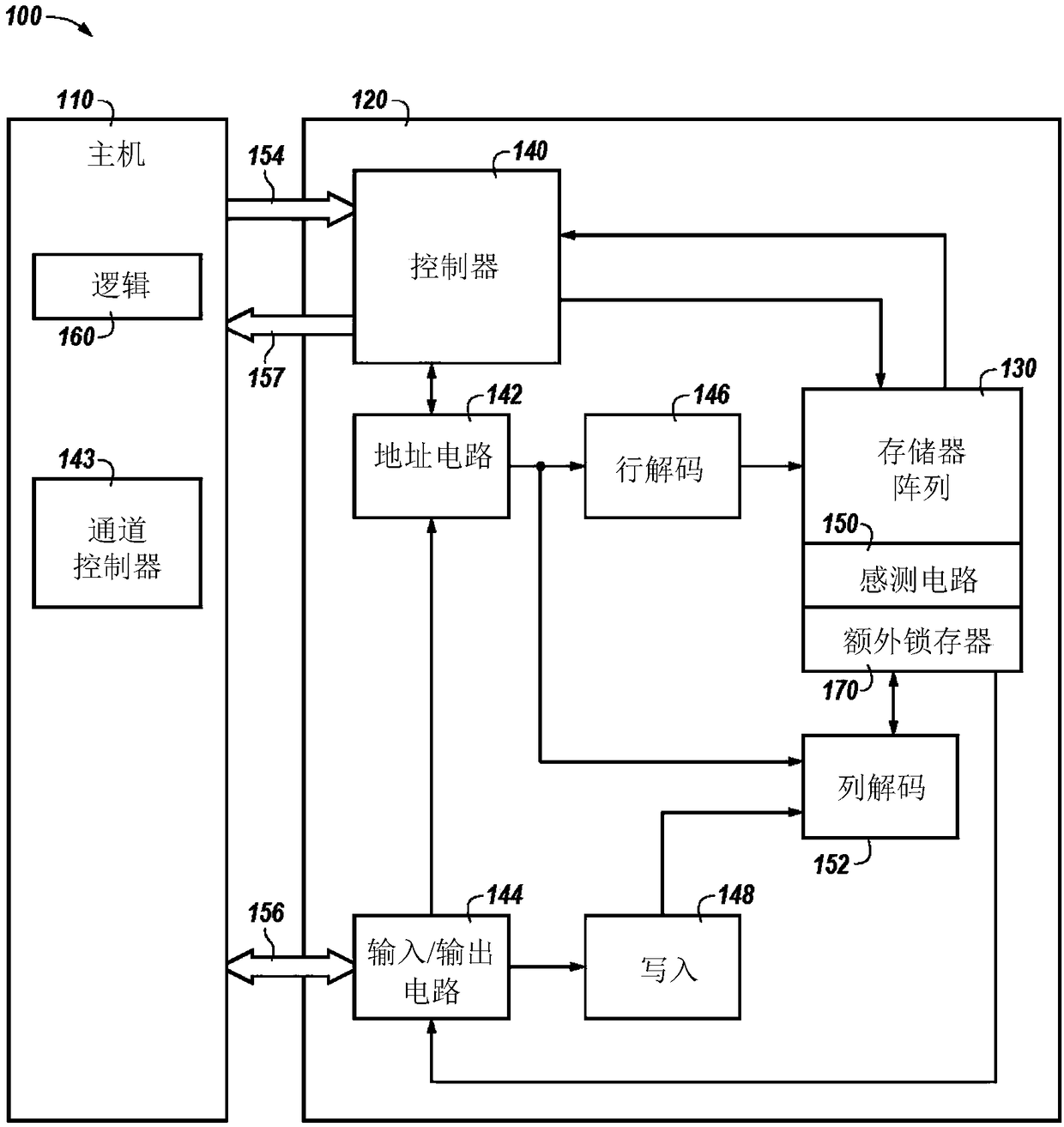
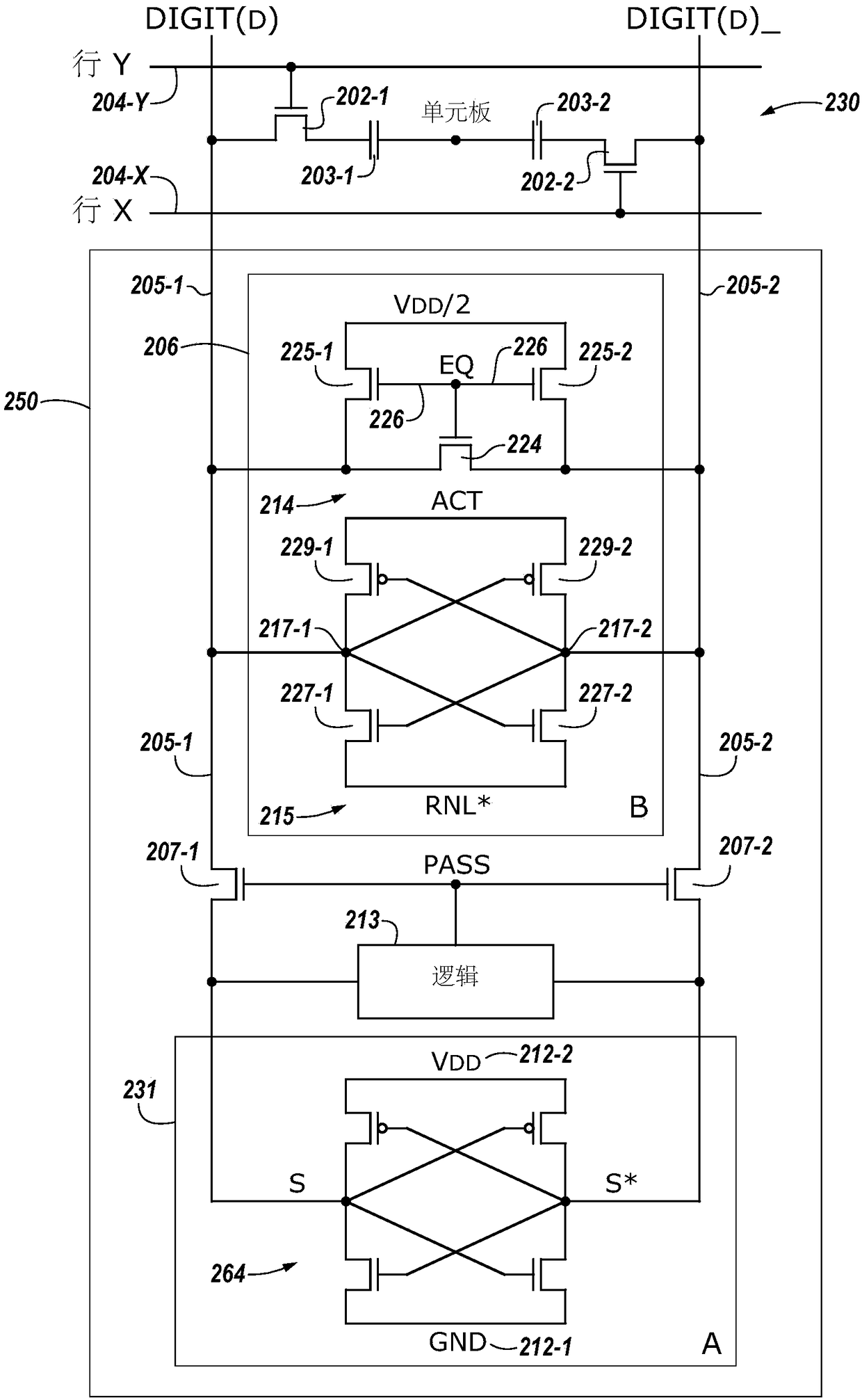
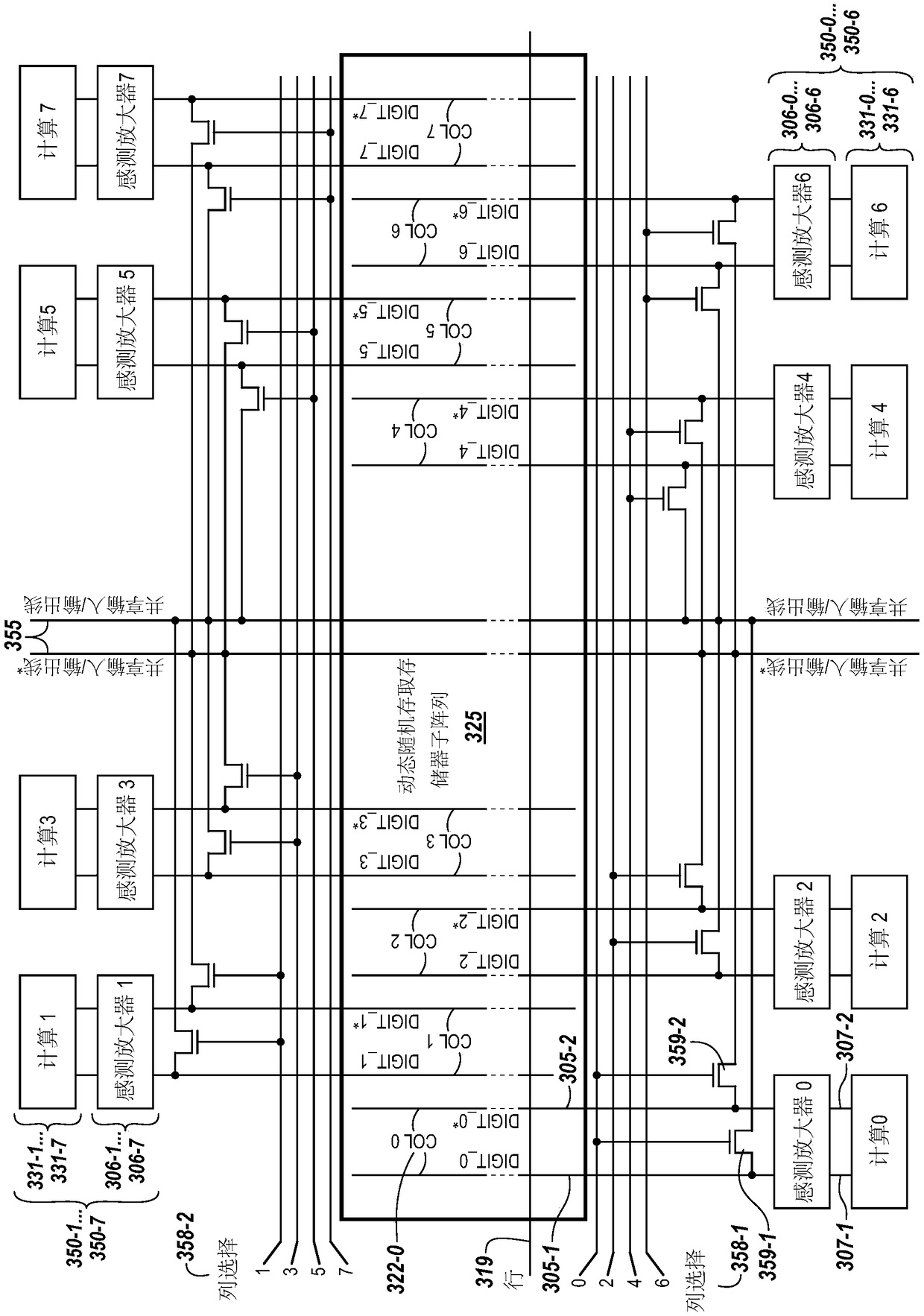
Data replication
ActiveCN109003635ADigital storageInput/output processes for data processingComputer hardwareAudio power amplifier
The present invention includes apparatuses and methods for data replication. An example apparatus includes a plurality of sensing circuitries comprising respective sense amplifiers and computing components; and a controller. The controller may be configured to cause replication of a data value stored in a first computing component such that the data value is propagated to a second computing component.
Owner:MICRON TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com