Zero-knowledge verification method based on block chain
A verification method, blockchain technology, applied in the field of zero-knowledge verification based on blockchain, can solve the problems of easy tampering of transaction privacy, information leakage, information leakage, etc., and achieve resistance to system structure erosion, high security performance, and improved The effect of modularity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
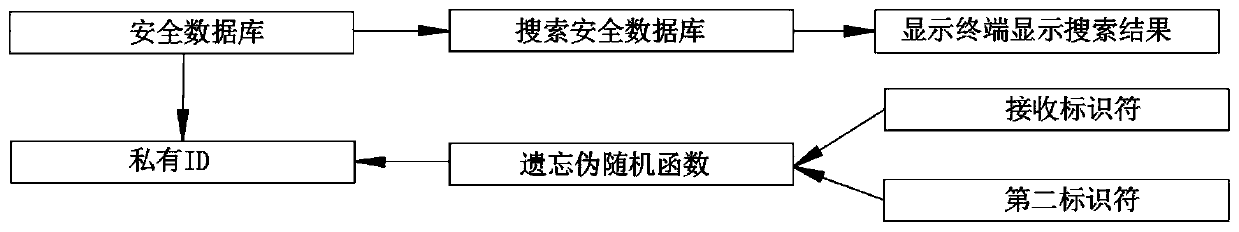
[0038] Embodiment 1: A zero-knowledge verification method based on blockchain, comprising:
[0039] obtaining a receipt identifier from the provider by the blockchain, wherein the receipt identifier corresponds to access to the blockchain authentication provider;
[0040] said blockchain acquires a second identifier, said second identifier corresponding to said received identifier, said received identifier being different from said second identifier;
[0041]accessing by said blockchain a secure database containing a stored private identifier, wherein the stored private identifier is a combination of the received identifier and the retrieved second identifier, said secure database comprising a blockchain search A security database, the search security database is based on the input received from the display terminal to obtain the corresponding search results; the corresponding second identifier is generated by the block chain based on the received identifier, and the area The...
Embodiment 2
[0042] Embodiment 2: A zero-knowledge verification method based on blockchain, comprising:
[0043] obtaining a receipt identifier from the provider by the blockchain, wherein the receipt identifier corresponds to access to the blockchain authentication provider;
[0044] said blockchain acquires a second identifier, said second identifier corresponding to said received identifier, said received identifier being different from said second identifier;
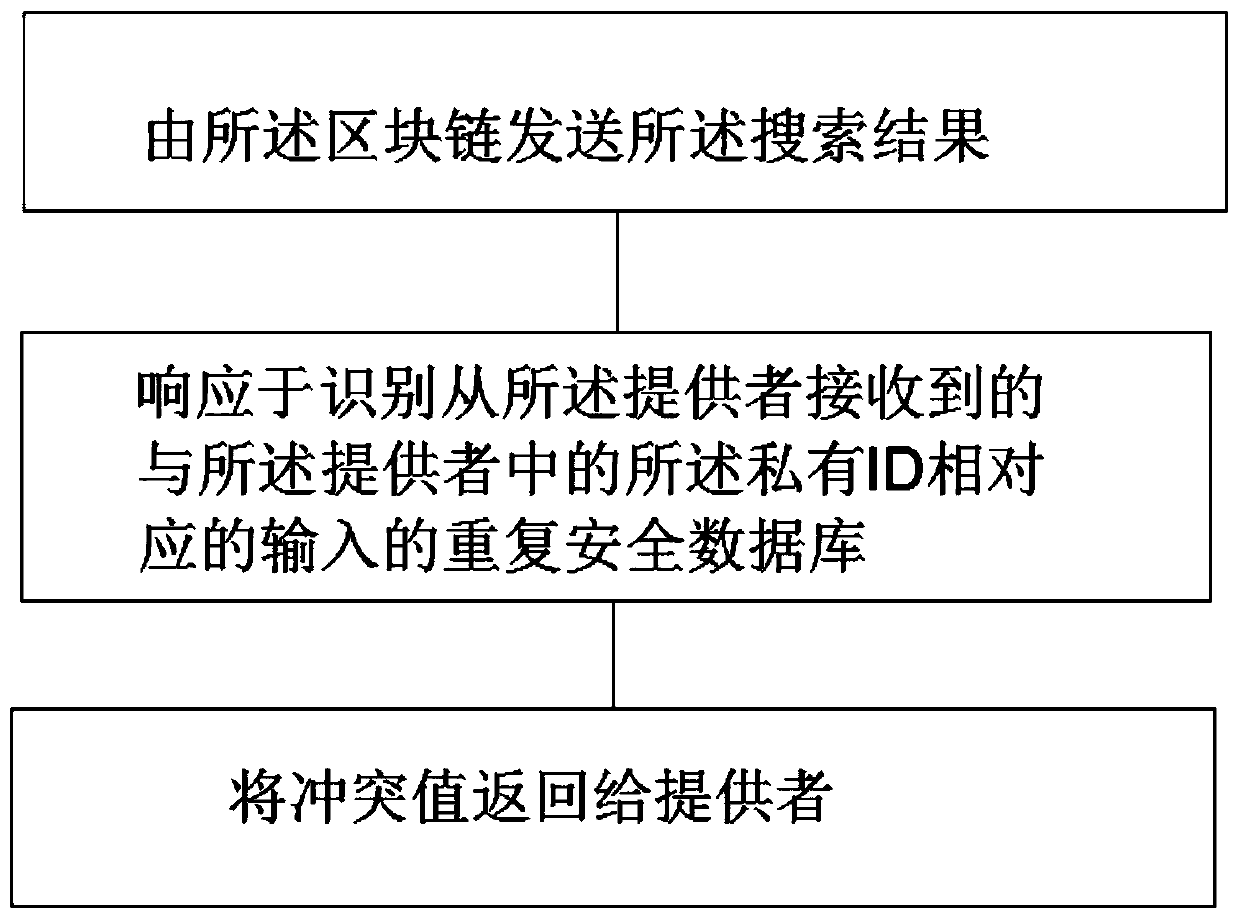
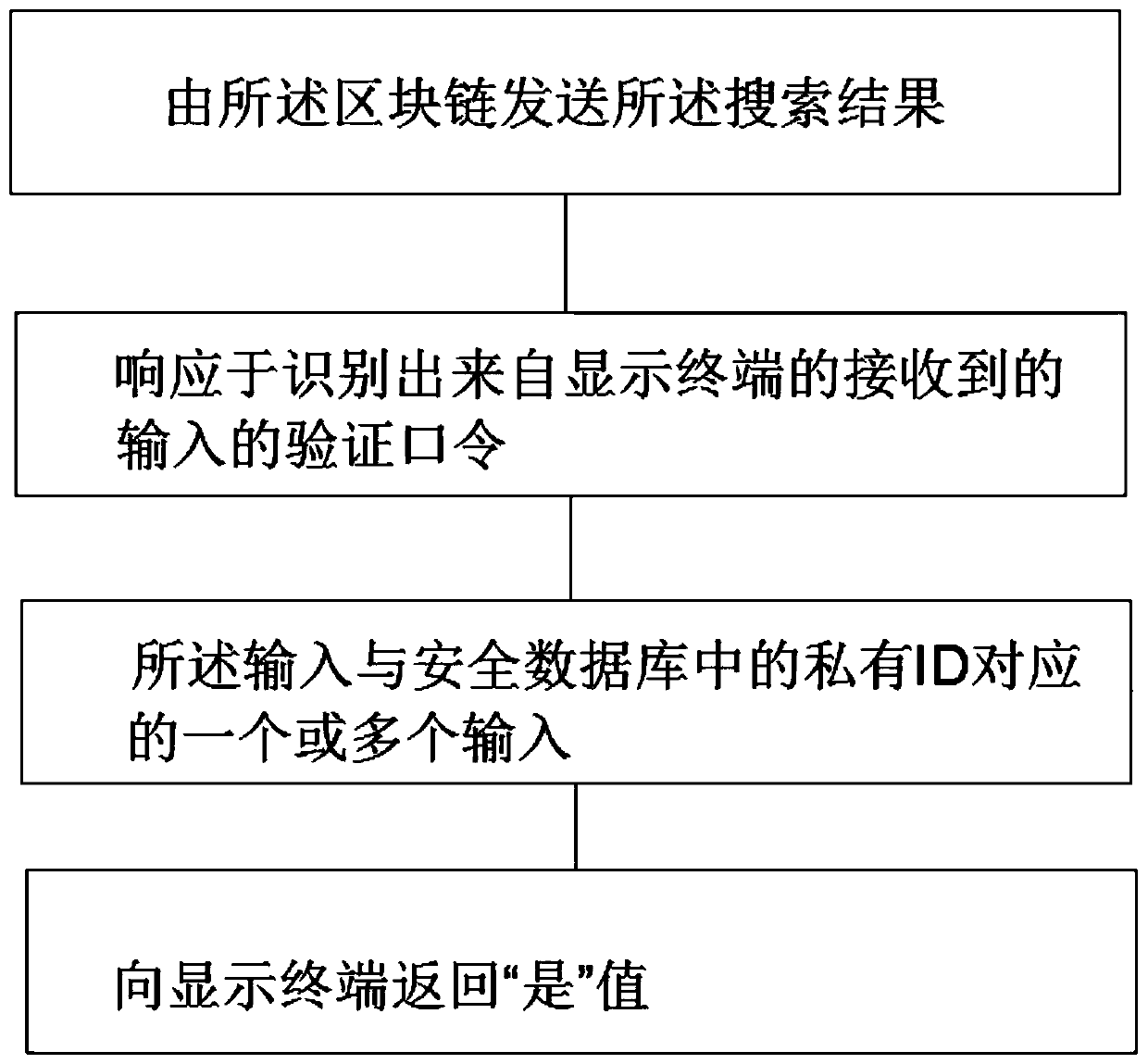
[0045] accessing by said blockchain a secure database containing a stored private identifier, wherein the stored private identifier is a combination of the received identifier and the retrieved second identifier, said secure database comprising a blockchain search a secure database, said searching the secure database to obtain corresponding search results based on input received from the display terminal;
[0046] The blockchain sends the search results to the display terminal and displays them on the display terminal. Specifi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com