Data processing method and system, access control method and system, device, equipment and storage medium
A data processing and data storage area technology, applied in the computer field, can solve problems such as memory data being tampered with
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
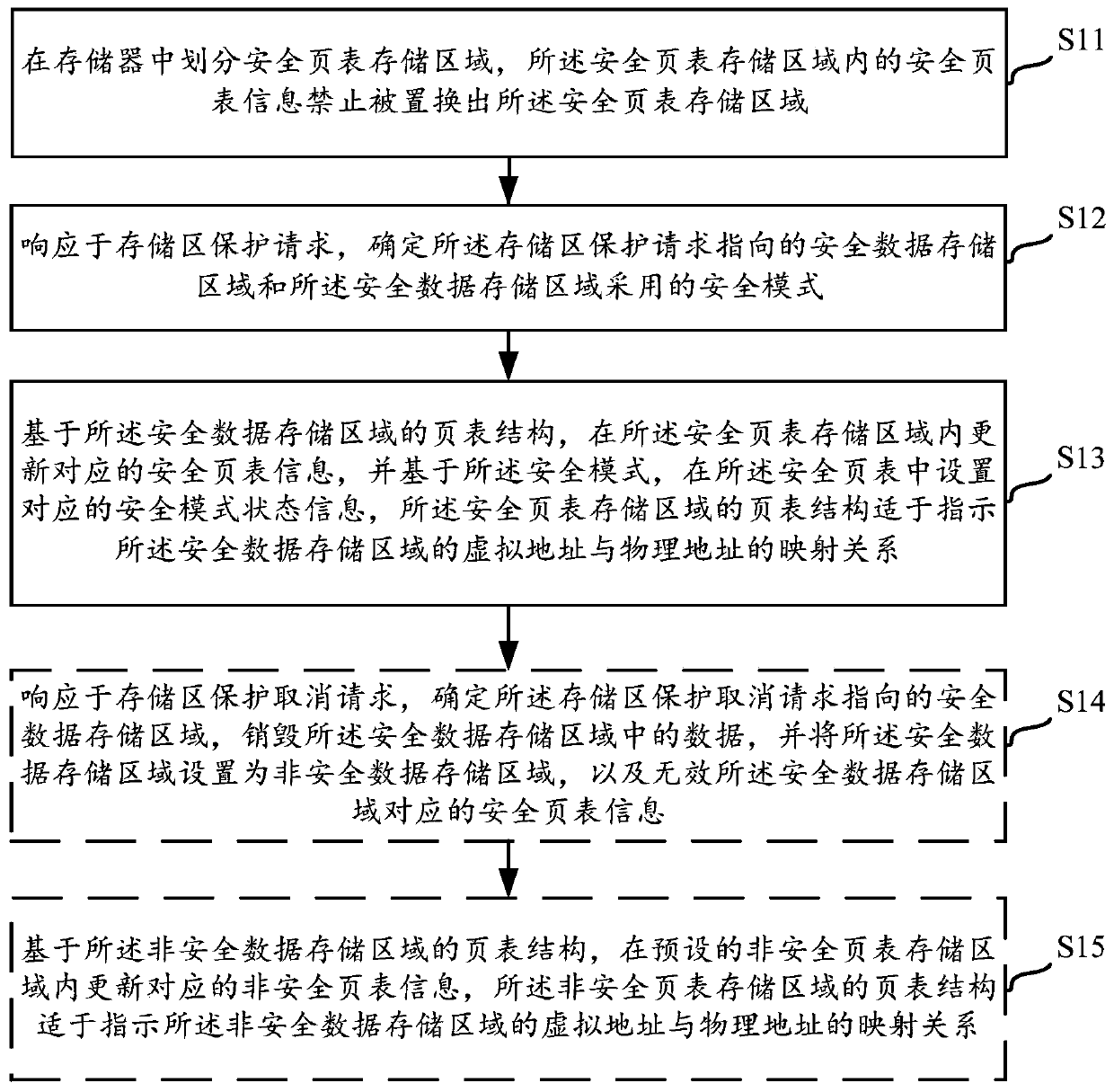
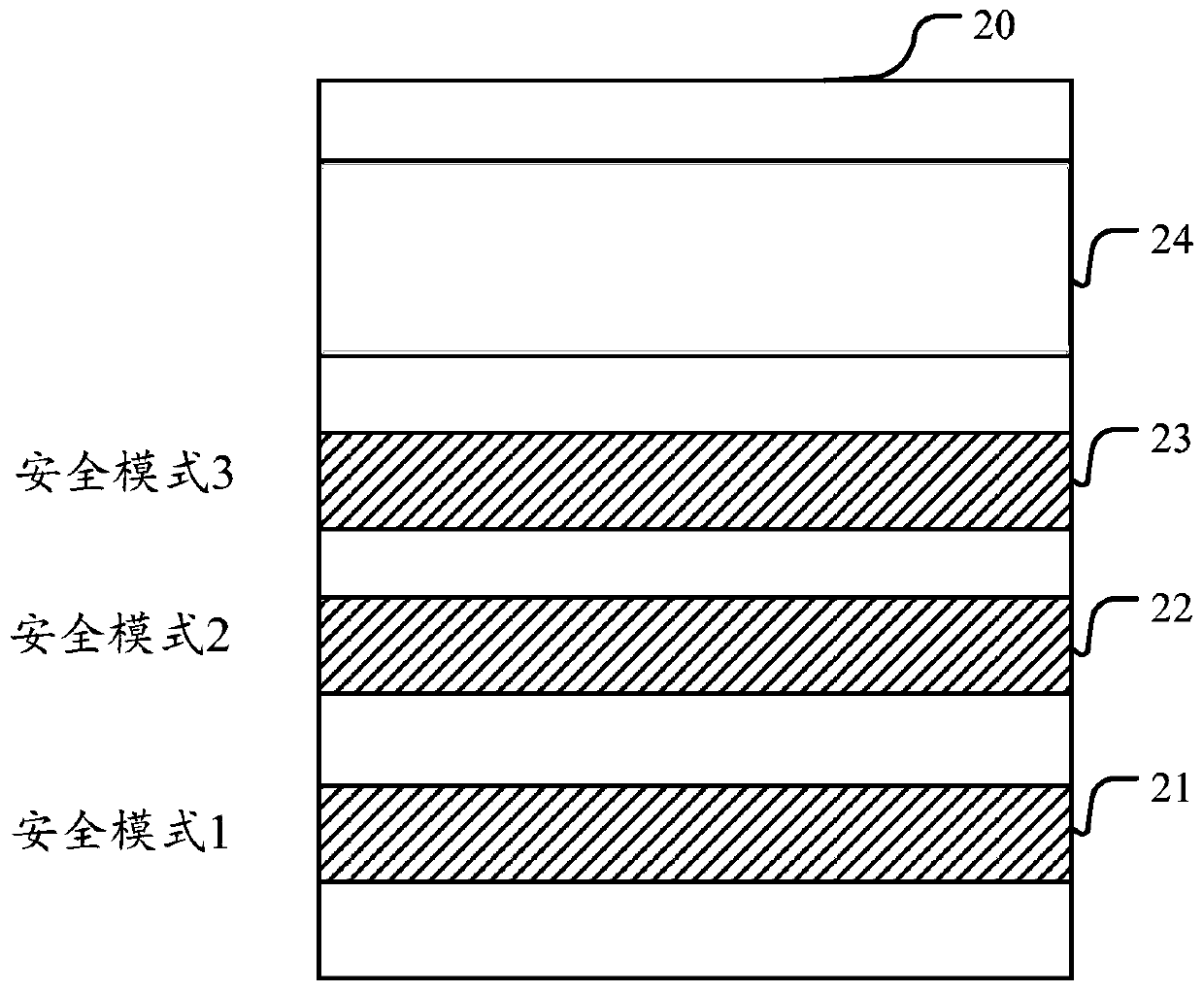
[0084] As mentioned above, in order to prevent malicious programs from obtaining the plaintext information in the memory, the relevant hardware architecture and software architecture can be designed on the SOC according to the actual data security protection scheme to realize the security protection of the data in the memory. For example, the storage security encryption (Secure Memory Encryption, SME) technology may be used to implement encryption control on the memory, and encrypt the data in the storage, thereby protecting the plaintext information in the storage.
[0085] However, the inventor found through research that although there are various data security protection schemes, the data in the memory still has a security risk of being tampered with. For example, although the memory adopts SME technology, the security status attribute of the memory data may be tampered with, so that the data in the memory still has the risk of leakage.
[0086]In view of the above problem...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com