Industrial control intrusion detection method for hierarchical dependency relationship modeling
A dependency and intrusion detection technology, applied in the direction of neural learning methods, transmission systems, biological neural network models, etc., can solve problems such as narrow detection range, unsatisfactory detection effect, and failure to consider multiple dependencies of traffic flow, etc., to achieve expansion Range, the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to have a clearer understanding of the technical features, purposes and effects of the present invention, the specific implementation manners of the present invention will now be described in detail with reference to the accompanying drawings.
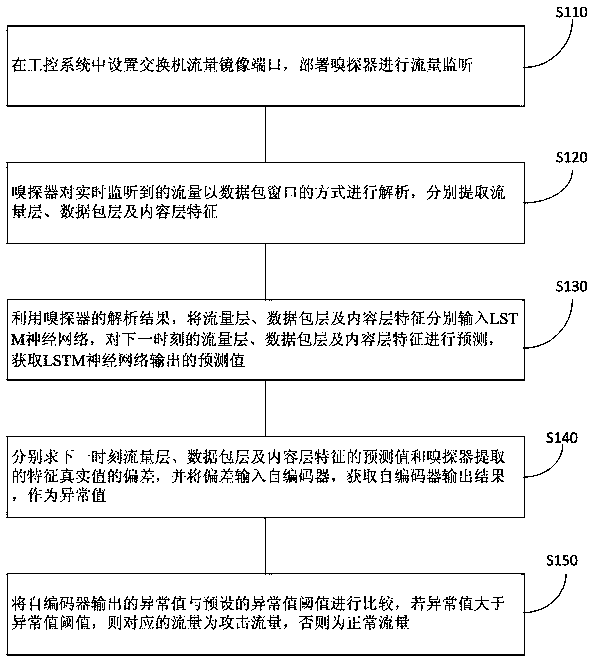
[0036] like figure 1As shown, the industrial control intrusion detection method of a kind of hierarchical dependency modeling of the present invention comprises steps:
[0037] S110: Set a switch traffic mirroring port in the industrial control system, and deploy a sniffer to monitor traffic.
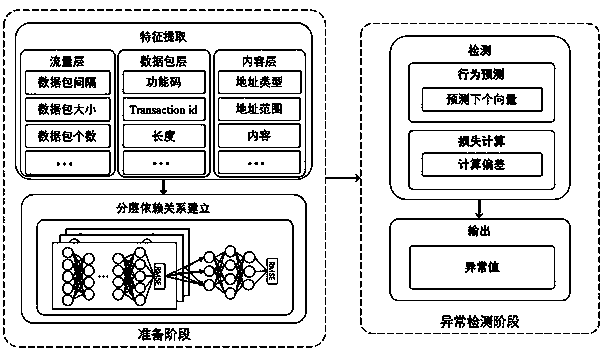
[0038] S120: The sniffer analyzes the traffic monitored in real time in the form of a data packet window, and extracts characteristics of a traffic layer, a data packet layer, and a content layer respectively.
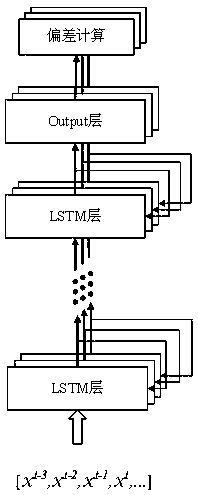
[0039] S130: Using the analysis results of the sniffer, input the characteristics of the traffic layer, data packet layer and content layer into the LSTM neural network respectively, predict the characteristics of the tr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com