Private domain flow management method and device and storage medium
A traffic management and private domain technology, which is applied in the field of private domain traffic management, can solve the problems of lack of fans and other private domain traffic management methods, inconvenient fan standardization management, inability to use fan economy reasonably and efficiently, etc., to achieve efficient use Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0019] According to this embodiment, an embodiment of a method for private domain traffic management is also provided. It should be noted that the steps shown in the flow charts of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions , and, although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
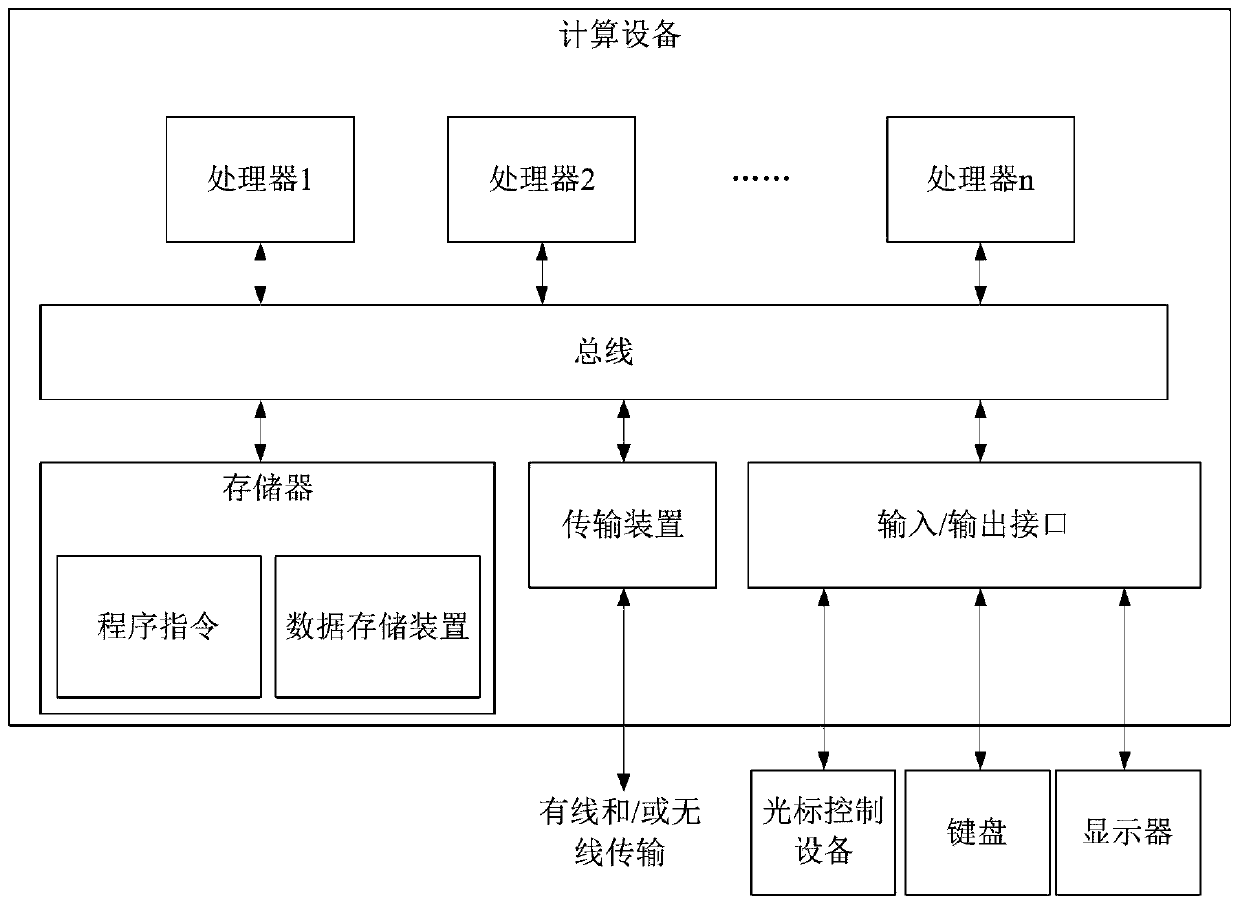
[0020] The method embodiments provided in this embodiment can be executed in mobile terminals, computer terminals, servers or similar computing devices. figure 1 A block diagram of a hardware structure of a computing device for implementing a method for managing traffic in a private domain is shown. Such as figure 1 As shown, the computing device may include one or more processors (processors may include but not limited to processing devices such as microprocessors MCUs or programmable logic devices FPGAs), me...
Embodiment 2
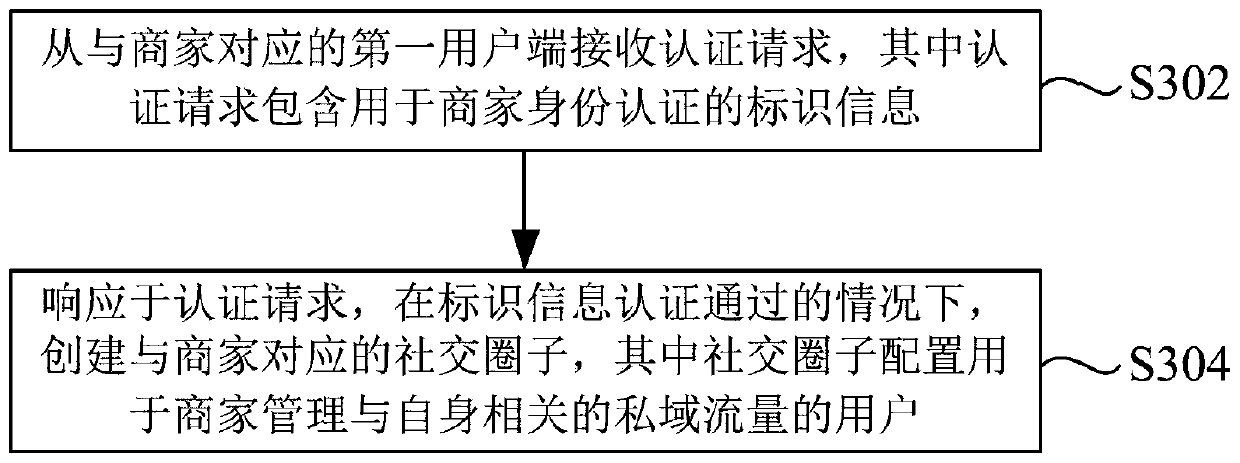
[0052] Figure 4 The apparatus 400 for private domain traffic management according to this embodiment is shown, and the apparatus 400 corresponds to the method according to the first aspect of Embodiment 1. refer to Figure 4 As shown, the device 400 includes: an identity authentication module 410, configured to receive an authentication request from a first client corresponding to a merchant, wherein the authentication request includes identification information for identity authentication of the merchant; and a circle creation module 420, configured to respond to Based on the authentication request, if the identification information authentication is passed, a social circle corresponding to the merchant is created, wherein the social circle is configured for the merchant to manage users related to its own private domain traffic.
[0053] Optionally, the device 400 further includes: a participation request receiving module, configured to receive a request to join a specified...
Embodiment 3
[0060] Figure 5 An apparatus 500 for private domain traffic management according to this embodiment is shown, and the apparatus 500 corresponds to the method according to the first aspect of Embodiment 1. refer to Figure 5 As shown, the device 500 includes: a processor 510; and a memory 520, connected to the processor 510, for providing the processor 510 with instructions for processing the following processing steps: receiving an authentication request from a first client corresponding to a merchant, wherein The authentication request includes identification information for merchant identity authentication; and in response to the authentication request, if the identification information is authenticated, create a social circle corresponding to the merchant, wherein the social circle is configured for the merchant to manage private domain traffic related to itself User.
[0061] Optionally, the memory 520 is also used to provide the processor 510 with instructions for proc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com