Target partition verification method and device, storage medium and computer equipment
A verification method and technology of a verification device, which are applied in the field of data security, can solve the problems of equipment performance degradation and particularly obvious performance degradation, and achieve the effects of improving security, saving calculation amount, and saving running space.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
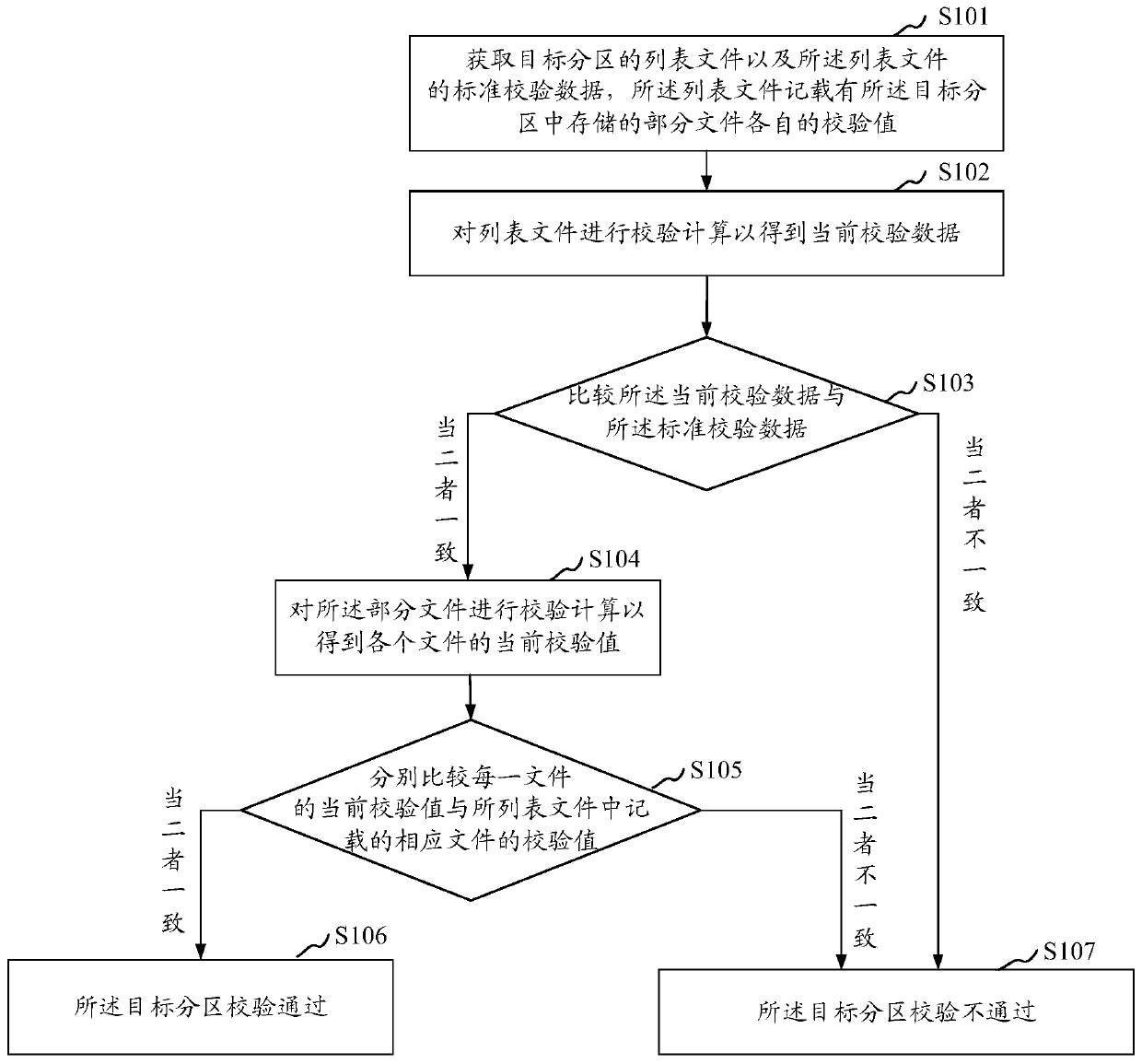
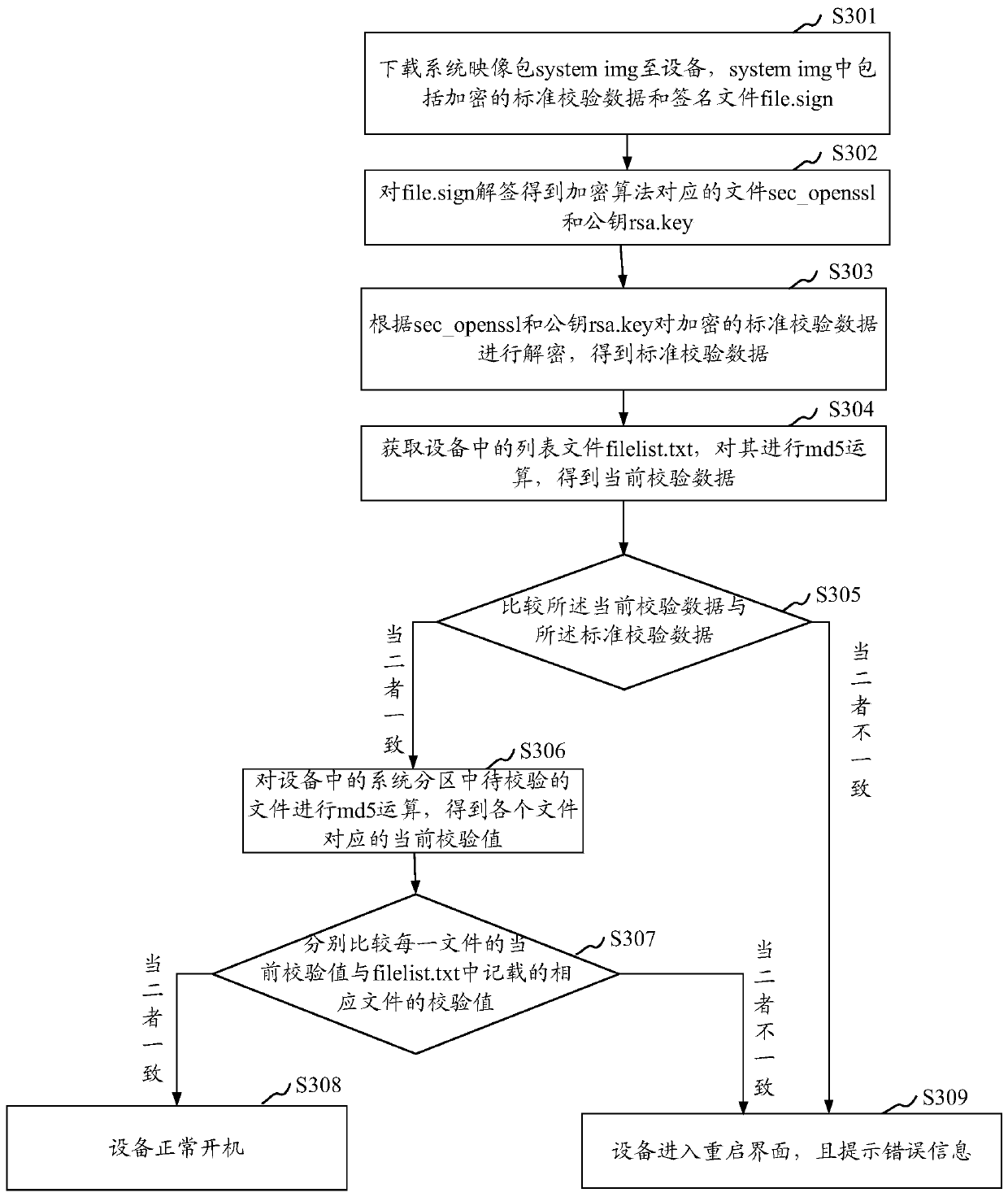
[0031] As mentioned in the background art, in the prior art, when the system partition of the Android device performs security verification, it is impossible to ensure the integrity of the system partition without affecting the performance of the device.
[0032] Traditionally, the device-mapper-verity (abbreviated dm-verity) kernel function performs a verified boot for transparent integrity checking of block devices. A block device is virtualized in dm-verity. When the block data is read, the hash calculation will be performed first, and it will be checked against the pre-calculated hash tree. If it matches, the read is successful, otherwise a Read I / O errors, so as to achieve the purpose of data integrity verification. This pre-calculated hash tree contains all the blocks of the target device to be verified. For each block (generally 4k in size), there is a SHA256 hash (32 bytes), which is stored at the leaf node of the tree. The middle node of the tree is the re-SHA256 has...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com