Active and safe SM2 digital signature two-party generation method
A digital signature and active security technology, which is applied to the public key of secure communication, digital transmission system, secure communication device, etc. It can solve the problems of only considering security, high communication and calculation costs, and unforgeable security of signature schemes. , to achieve the effects of enhanced security, low calculation cost, and low communication cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
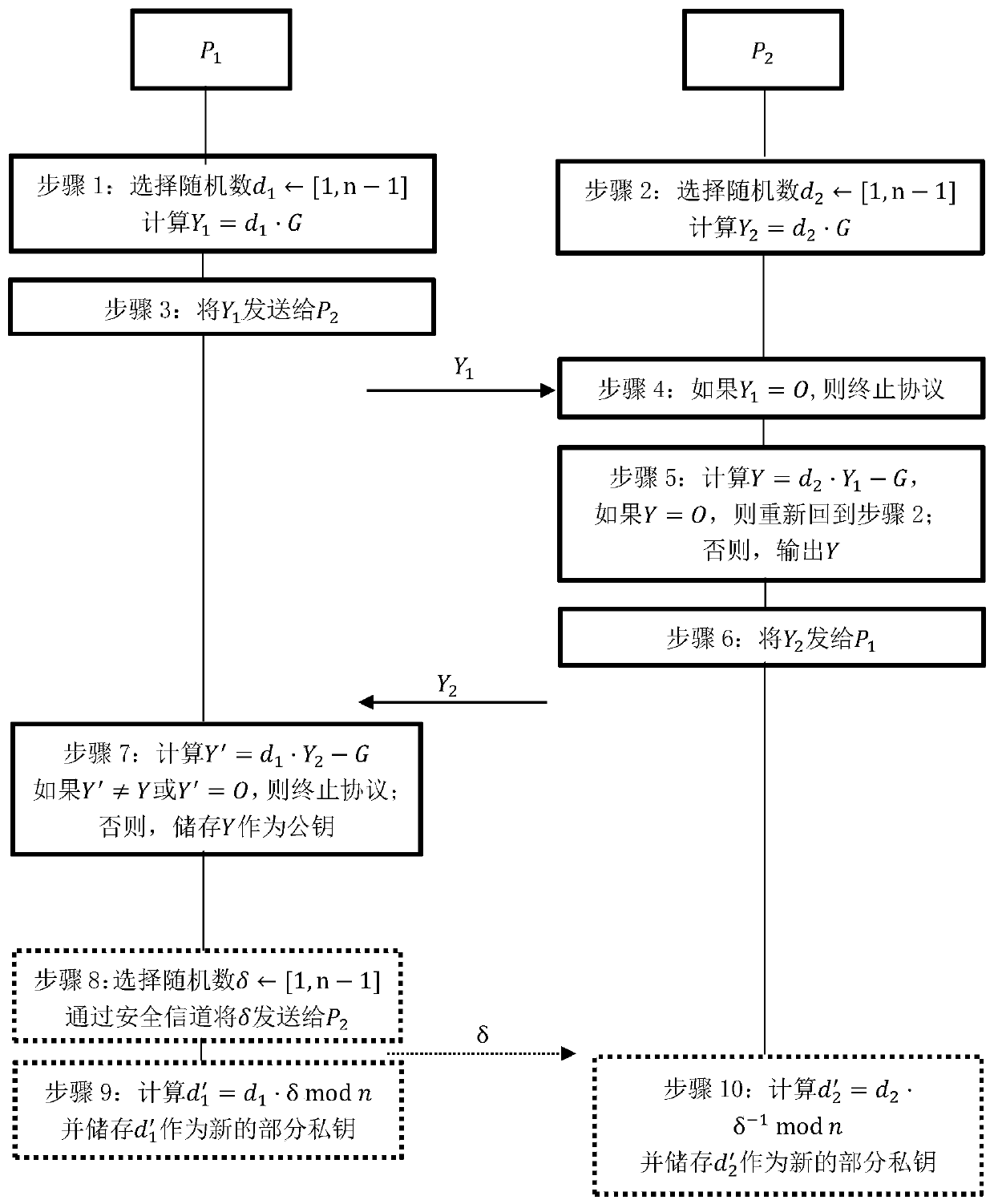
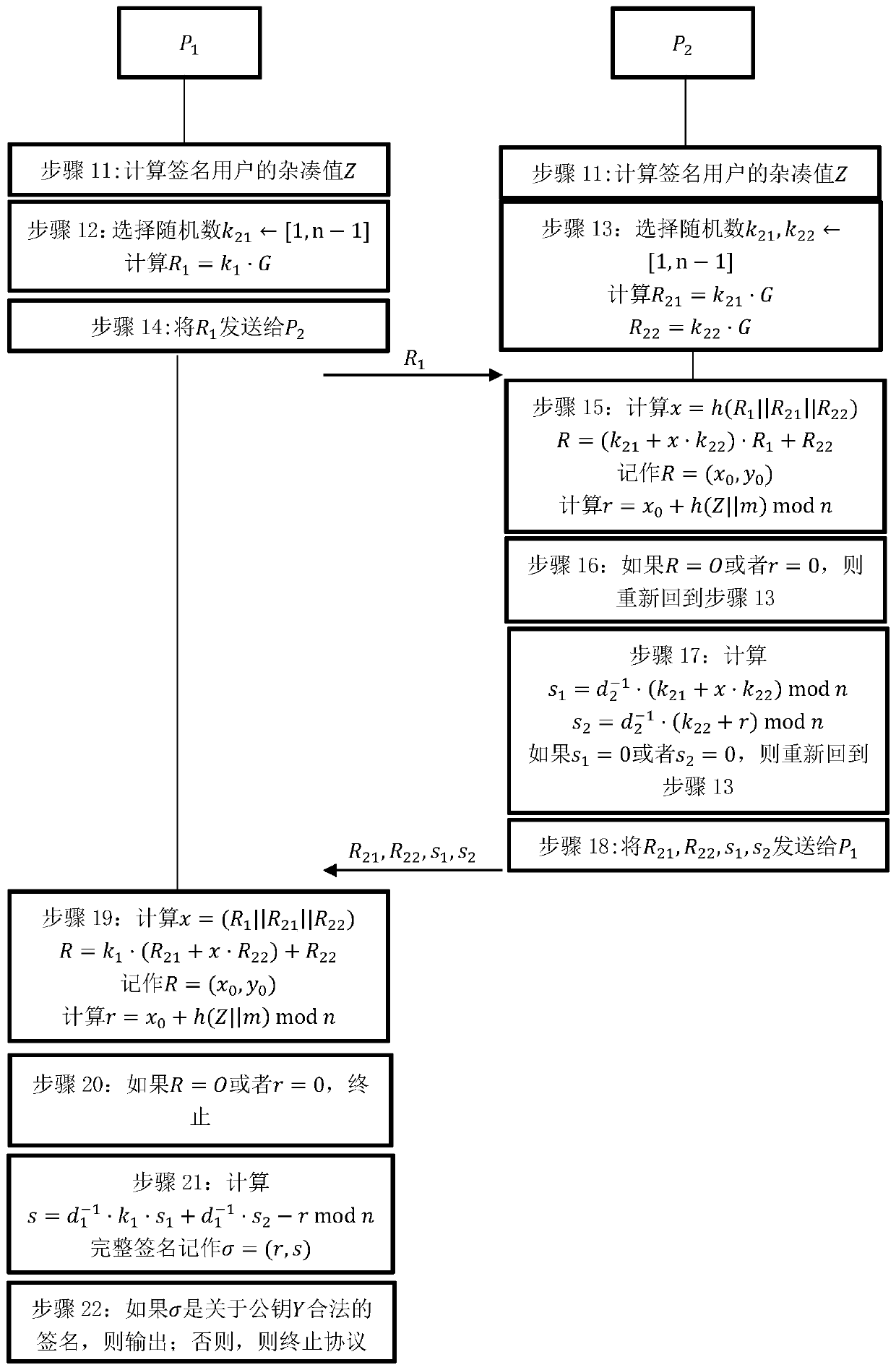
[0024] 1. Participant P 1 with P 2 Jointly generate the key of the SM2 digital signature algorithm as follows
[0025] Step 1: P 1 Choose a random number d between [1,n-1] 1 , to calculate the partial public key Y 1 = d 1 ·G.
[0026] Step 2: P 2 Choose a random number d between [1,n-1] 2 , to calculate the partial public key Y 2 = d 2 ·G.
[0027] Step 3: P 1 Will Y 1 send to P 2 .
[0028] Step 4: P 2 check if Y 1 =O, the agreement is terminated.
[0029] Step 5: P 2 Calculate Y=d 2 ·Y 1 -G, if Y=O, then P 2 Return to step 2; otherwise, output Y as the user's public key.
[0030] Step 6: P 2 Will Y 2 send to P 1 .
[0031] Step 7: P 1 Calculate Y'=d 1 ·Y 2 -G, if Y'≠Y or Y'=O, then P 1 terminate the agreement; otherwise, P 1 Store Y as the public key of the SM2 signature algorithm.
[0032] 2. Participant P 1 with P 2 Actively update some private keys of the SM2 digital signature algorithm as follows.
[0033] Step 8: P 1 Choose a random nu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com