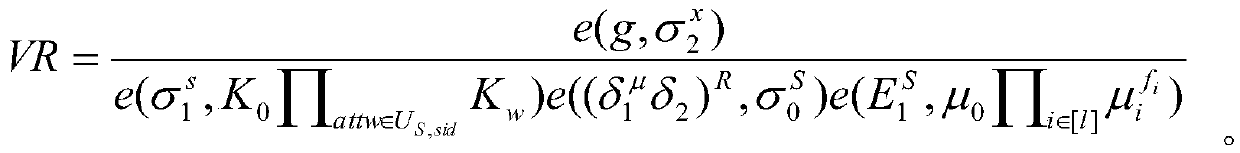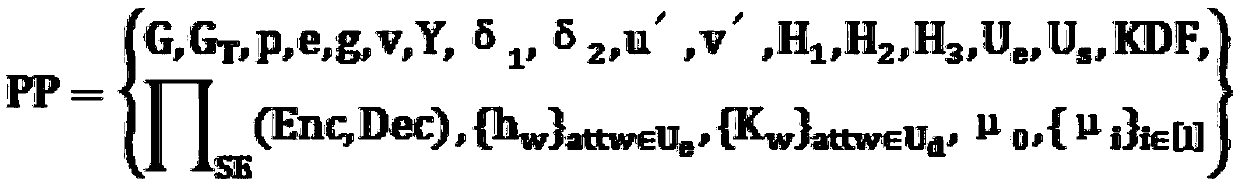Lightweight attribute-based signcryption method for cloud and fog assisted Internet of Things
An Internet of Things, lightweight technology, applied in user identity/authority verification, key distribution, and can solve problems such as difficult load, difficult mathematical assumptions about attribute encryption security, and access control rights are not directly handed over.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
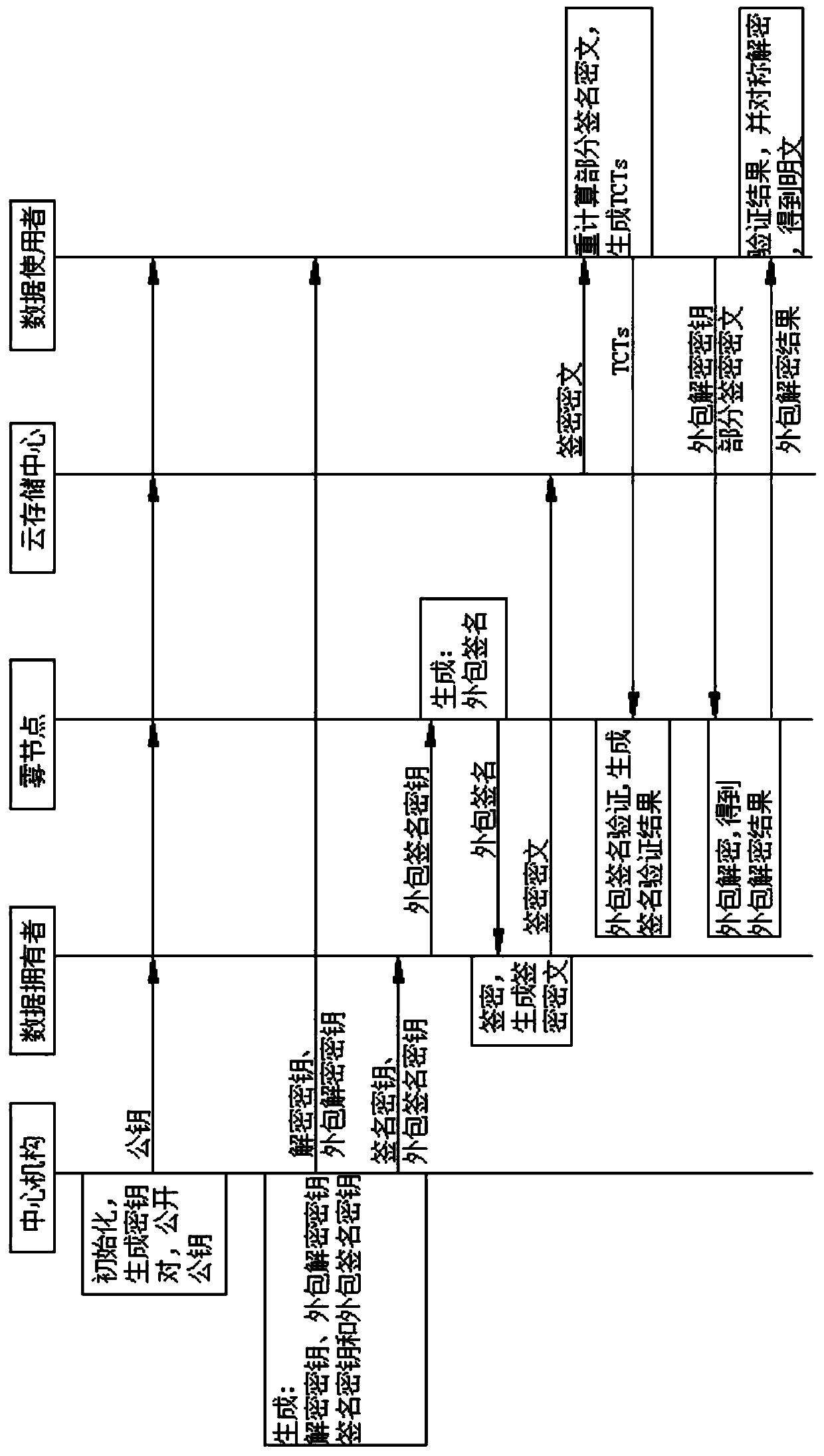
[0120] as attached figure 1 As shown, the light-weight attribute-based signcryption method for the cloud and fog to assist the Internet of Things of the present invention includes the following steps:
[0121] S100, the central organization performs system initialization, generates a system key pair, and discloses the public key, and the public key includes a symmetric encryption algorithm and a key generation function;
[0122] S200. The central agency specifies a decryption attribute set for the registered data user, and generates a decryption key and an outsourced decryption key corresponding to the data user based on the decryption attribute set, and the central agency specifies a signature for the data owner access structure, and generate a signature key and an outsourced signature key corresponding to the data owner based on the signature access structure;
[0123] S300. The data owner selects a set of attributes that satisfy the signature access structure, and calls th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com