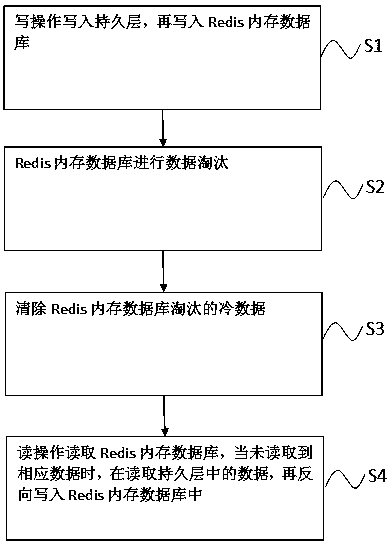
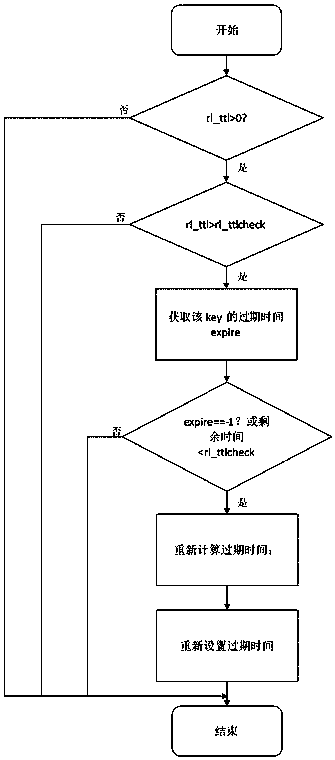
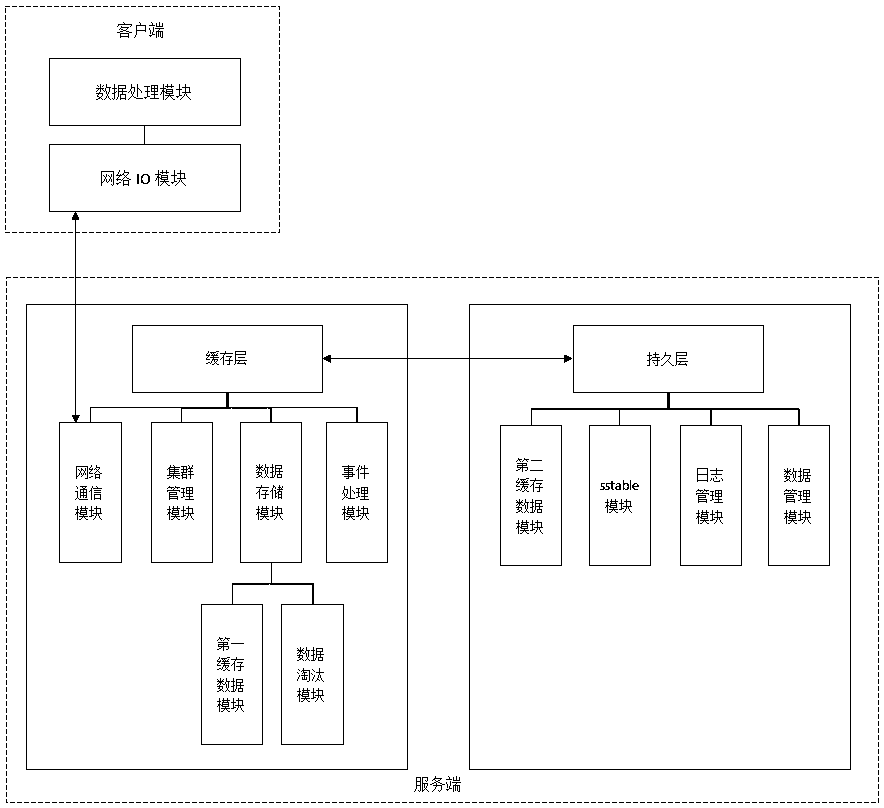
Method for realizing persistence of memory database
A database and persistent technology, applied in the input/output process of data processing, electrical digital data processing, instruments, etc., can solve problems such as limitation and achieve the effect of improving data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0072] Embodiment 1 is the data security test of this system:
[0073] Data security means that when the system encounters accidents, such as sudden system crashes, power failures, etc., data will not be lost, errors will not occur, and data integrity will be maintained. Therefore, in the test process, the situation of unexpected power failure of the system is simulated to test the data security. First write the data key to the system as key_safe, the value is value_safe, and return the result successfully, then query the key key_safe, and successfully return the value value_safe. The test process is as Figure 4 shown;
[0074] At this time, the power supply of the hardware device is suddenly cut off, resulting in a power failure of the database system. Then restart the hardware device, restart the database, query the key key_safe, and successfully return the result value_safe. After restarting, the test process is as follows Figure 5 shown;
[0075] As shown above, th...
Embodiment 2
[0077] Embodiment 2 is the read and write performance test of this system:
[0078] In this example, the workload test scenario is used to compare the original Redis with the Redis after persistence using the cold data elimination mechanism. The size of each test data is 1KB, and the size of each field is 100B. In the 100% read operation scenario, the comparison performance is as follows: Figure 7 ;
[0079] pass Figure 7 As a result, it can be concluded that in the case of low data volume, the read performance is basically the same. But in the case of a large number, part of the data is cleared from the memory by the cold data elimination mechanism, and then it can only be read from the persistence layer, which will cause a certain delay, but by adopting the method of the present invention, in the Redis native system The delay caused by AOF and RDB data backup is canceled, improving some performance. Overall performance is not much different. However, the method of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com