An automatic scoring method and device for offensive and defensive confrontation platforms based on video recognition
An automatic scoring and video recognition technology, which is applied in the field of network security, can solve problems such as difficult to distinguish and inability to intuitively review the score operation of rehearsal personnel, and achieve the effects of avoiding data differences, easy collection and identification, and convenient replay analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
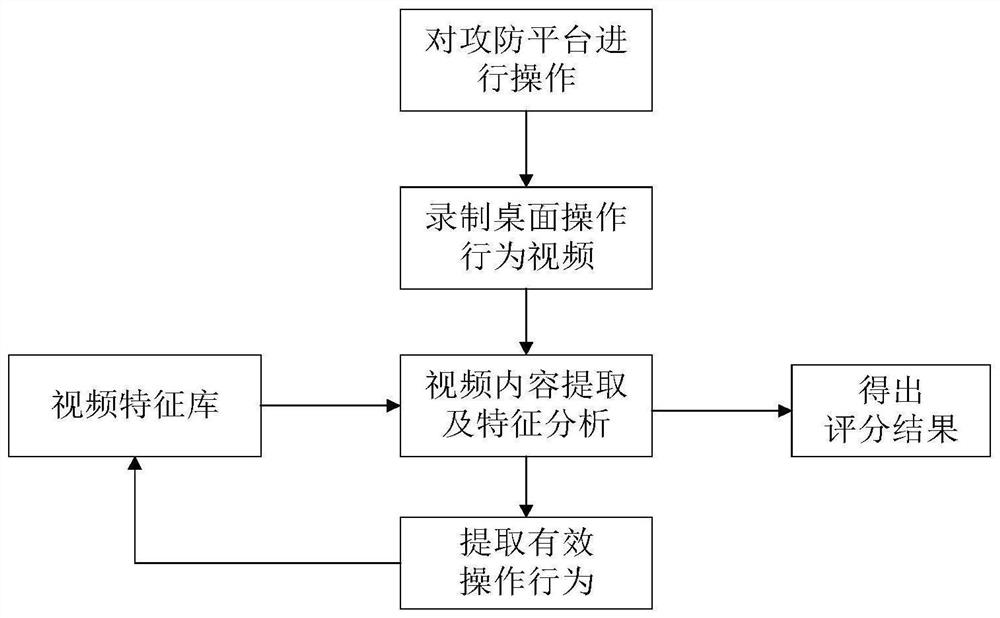
[0064] According to a specific embodiment of the present invention, when carrying out multiple offensive and defensive drills, comprise the following steps:
[0065] S1: Add the video data of key operational behaviors including successful access to the target host, accessing sensitive files, querying sensitive data, modifying system configuration, attacking the system, or exploiting application vulnerabilities in the video feature library as targets;
[0066] The key operational behaviors are a set of operational behaviors defined before the start of the offensive and defensive confrontation that can be judged as scoring in this offensive and defensive confrontation.
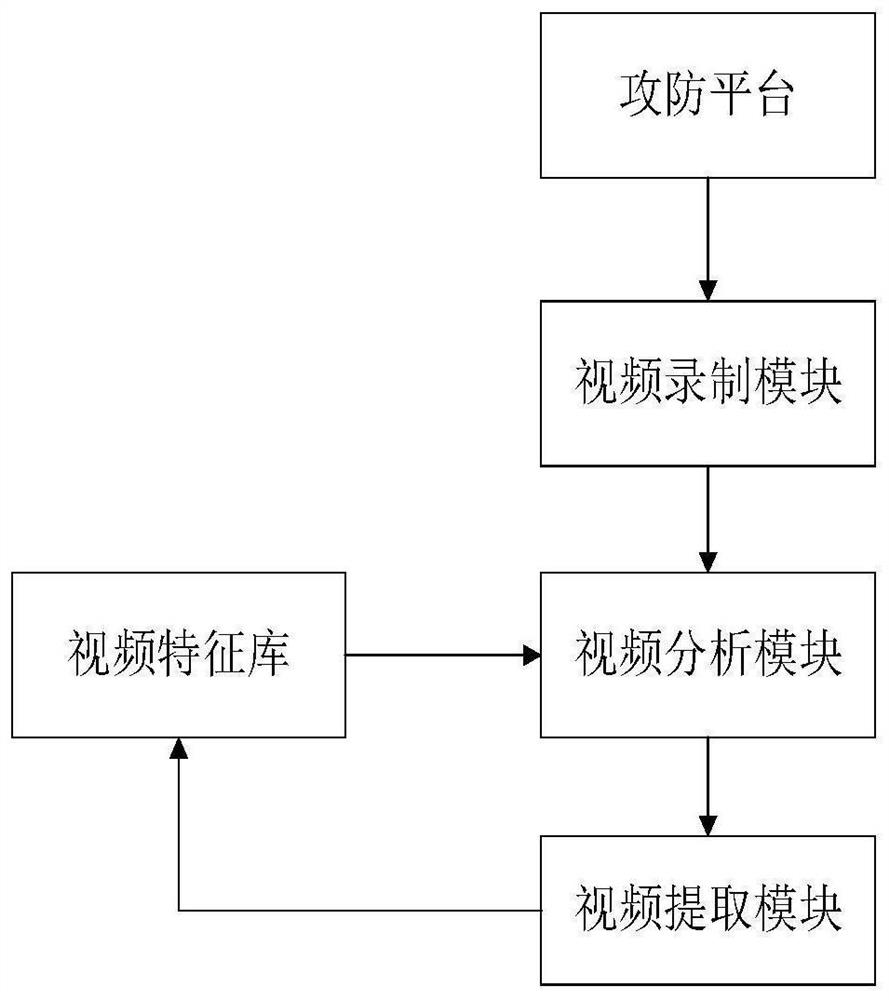
[0067] S2: Record all desktop operation videos of offensive and defensive drillers. Desktop operations include: mouse movement, input cursor movement, desktop window element changes, etc.;
[0068] S3: Extract the video data recorded in step S2 frame by frame, perform feature analysis, read the content of the vi...
example 2
[0081] According to a specific embodiment of the present invention, taking the offensive and defensive confrontation of database sensitive data acquisition as an example, the method includes the following steps:
[0082] S1: Add the video data of accessing the database, querying the database, and querying sensitive data in the video feature library as targets;
[0083] S2: Record all desktop operation videos of offensive and defensive drillers. Desktop operations include: mouse movement, input cursor movement, desktop window element changes, etc.;
[0084] S3: Extract the video data recorded in step S2 frame by frame, perform feature analysis, read the content of the video frame and the content of the previous and subsequent video frames, and judge the desktop operation behavior of the driller according to the change of the content of the video frame. By positioning the two-dimensional coordinates of the mouse and the input cursor in the video, the data of the keyboard and the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com