SSH remote connection method of mimicry system, mimicry architecture and readable storage medium
A remote connection and mimic system technology, applied in the field of readable storage media, can solve problems such as inability to directly adapt to SSH remote connections
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The technical solutions of the present invention will be described in further detail below through specific implementation methods.
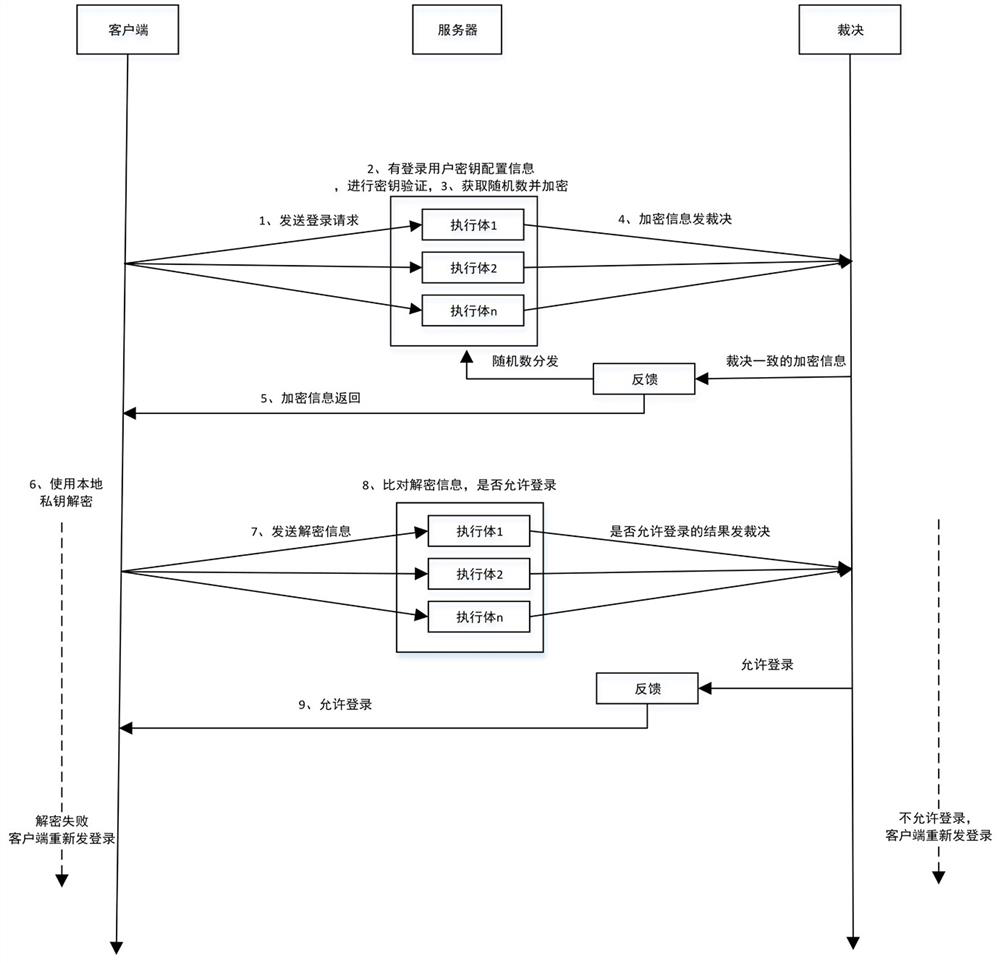
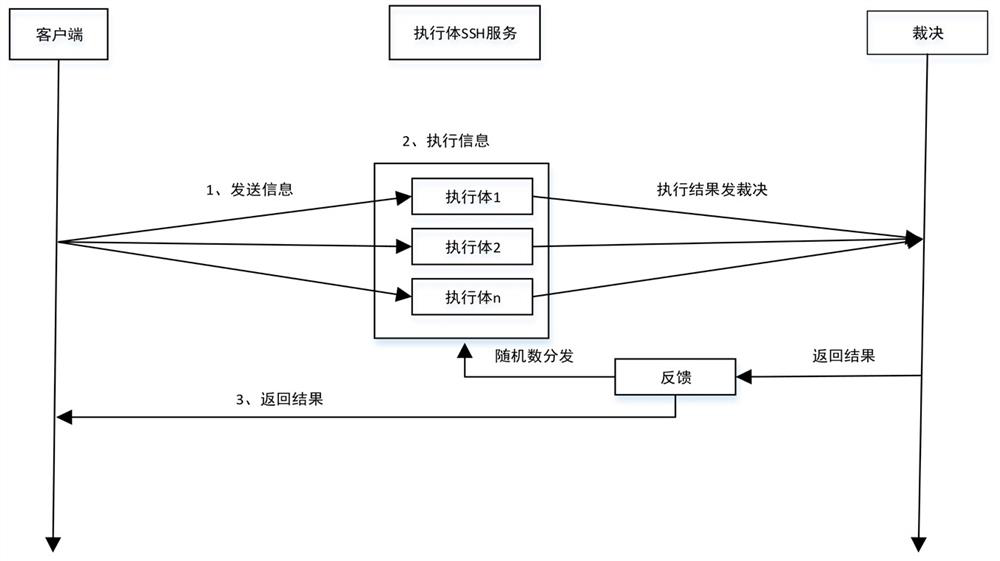
[0033] An SSH remote connection method of a mimic system, which is used to realize login and communication between an SSH client and multiple heterogeneous executives.
[0034] This application is based on the key-based authentication method provided by SSH. The biggest advantage is that it can avoid man-in-the-middle attacks. Its biggest feature is that there is a server-side query process during the verification process, and the encrypted information will be added during the query. A set of random numbers is used to verify the security of data, which leads to obstacles in application in a mimic system with multiple heterogeneous executives. This embodiment solves this problem through the following methods.
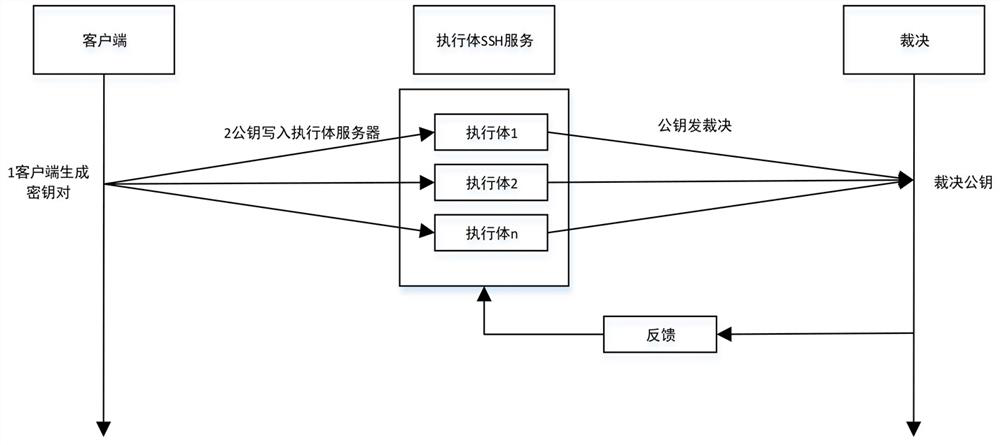
[0035] like figure 1 As shown, the preparation stage:
[0036] Step 1): Generate a pair of keys, public key and private key in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com