Face recognition security system based on Internet of Things and operation method
A face recognition and security system technology, applied in the field of face recognition security systems, can solve the problems of uncertain data timeliness, low efficiency, and low security, and achieve high security prevention and tracking capabilities, improved comparison speed, The effect of safety improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0036] Embodiment 1: The operation method of the face recognition security system based on the Internet of Things comprises the following steps:
[0037] Step 1: Collect face feature values:
[0038] Upload and store all applicant data on the cloud server through the face collection device and client;
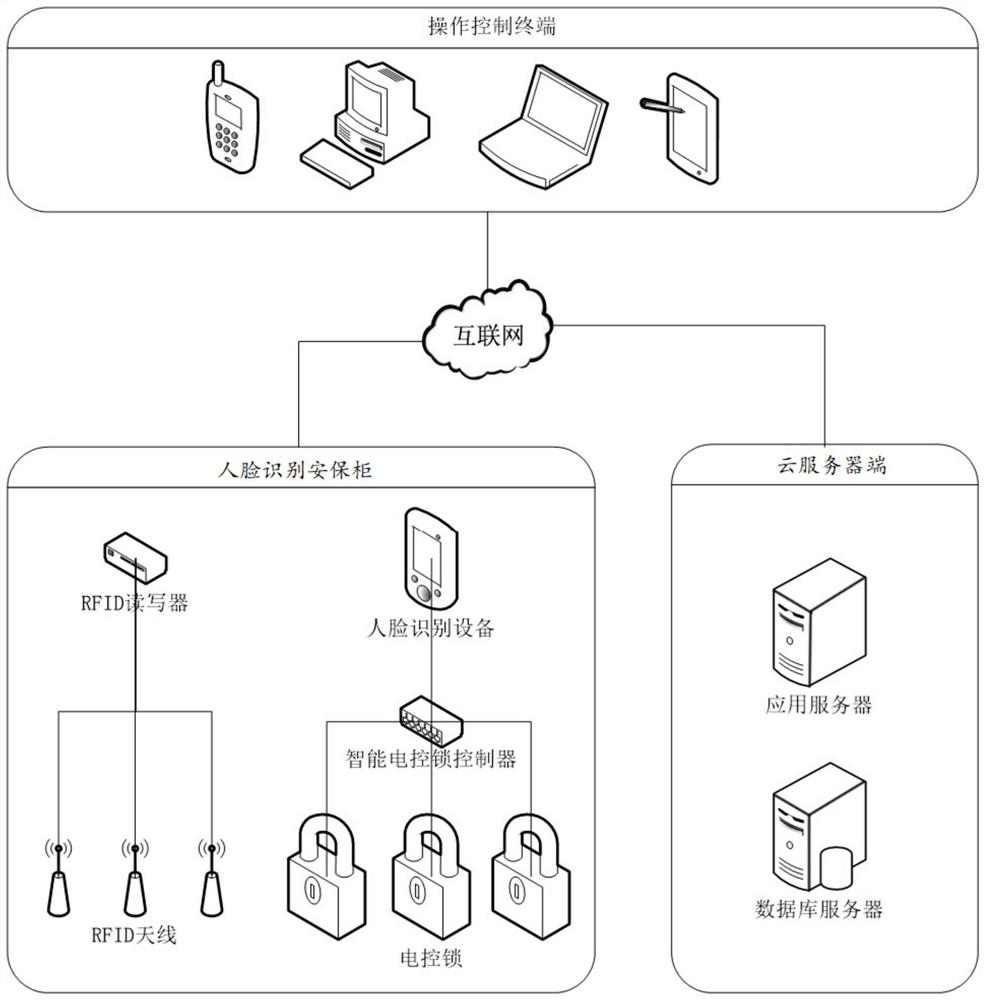
[0039] Step 2: Operation control terminal application identification:
[0040] When the applicant uses the operation control terminal to send a request for unlocking the security cabinet with a seal to the cloud server, the cloud server carries out identity verification to the applicant, and checks whether the applicant has the authority to open the storage drawer and to be returned. Verify the legitimacy of the seal. The legitimacy of the seal is whether the currently applied seal has the right to be applied by the applicant, and whether the seal is being used by others. If the verification is valid, the cloud server side judges whether the storage drawer requested by the app...
Embodiment 2
[0054] Embodiment 2: as figure 1 , 2 As shown, the operation method of the face recognition safe based on the Internet of Things comprises the following steps:
[0055] Step 1: Collect face feature values; when it is necessary to add or update applicant data in a business scenario, the manager will lead the newly added or updated applicants to the face recognition device for collection, and use the collection immediately after each collection The obtained face features are compared with the face of the current applicant. After the comparison is successful, the applicant data is encrypted and uploaded to the cloud server through the client. The applicant data includes: name, number, face data, access Face recognition security cabinet number and storage drawer number, seal number, face data and the corresponding parameters and timeout time of the face recognition security cabinet number accessed, the face collection device collects multiple face data for the same person, and th...
Embodiment 3
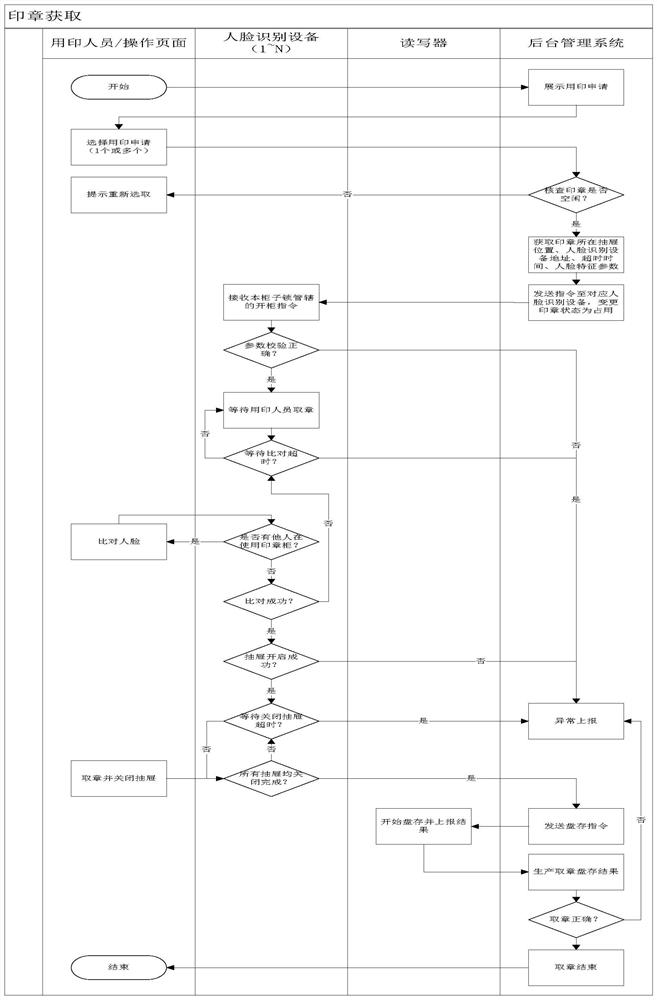
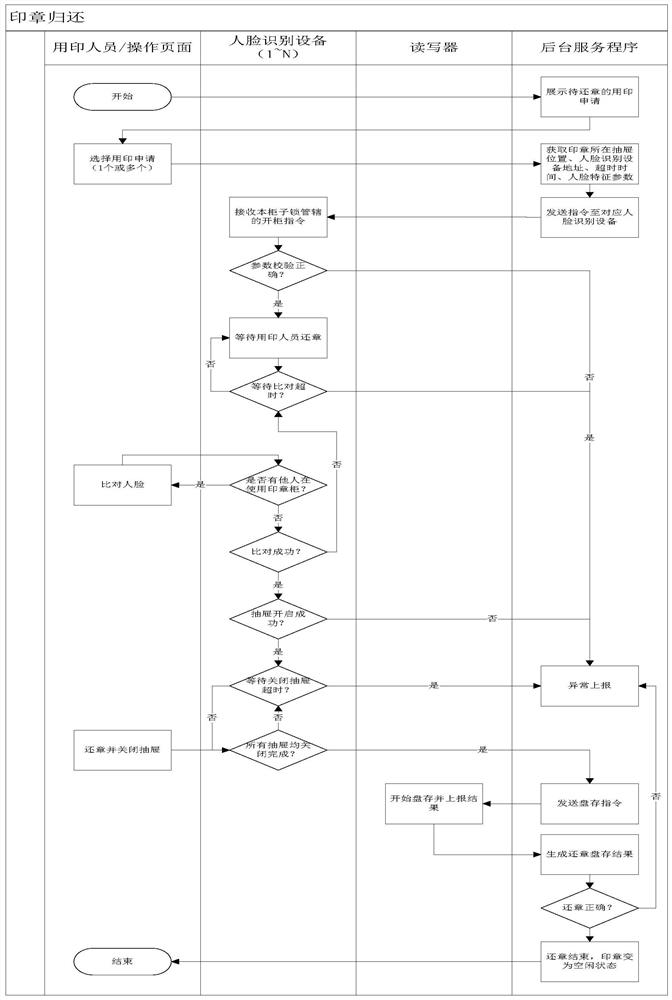
[0071] Embodiment 3: as figure 1 , 3 As shown, the operation method of the face recognition safe based on the Internet of Things comprises the following steps:
[0072] Step 1: Collect facial feature values; upload and store all applicant data on the cloud server through the face collection device and client;
[0073] Step 2: The operator applies for identification;
[0074] When the applicant uses the operation control terminal to send a request to the cloud server to unlock the security cabinet for storing the seal, the cloud server acquires the position of the drawer where the seal is located, the address of the face recognition device, the timeout time and face data, and executes Step 3, when the face data comparison of the face recognition device queue is timed out, delete the timed out face data, and the cloud server side records timeout information and business processing data;
[0075] Step 3: Identify and operate the safe:
[0076] The face recognition device judg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com