Serialization method of binary file penetration reverse isolation device
A technology of reverse isolation device and binary file, applied in secure communication devices, electrical components, user identity/authority verification, etc., can solve problems such as data transmission obstacles in information areas
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described below in conjunction with the examples. The description of the following examples is provided only to aid the understanding of the present invention. It should be pointed out that for those skilled in the art, some modifications can be made to the present invention without departing from the principles of the present invention, and these improvements and modifications also fall within the protection scope of the claims of the present invention.
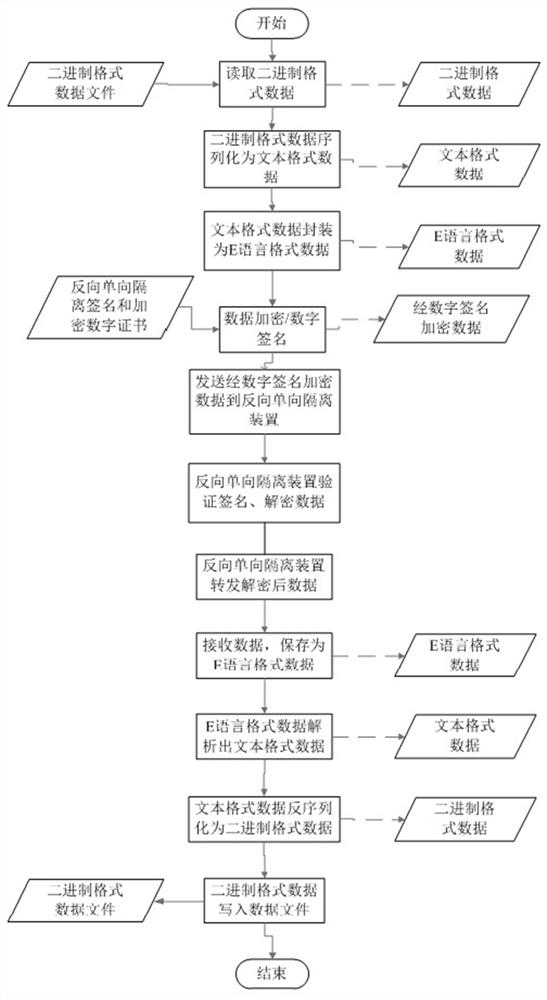
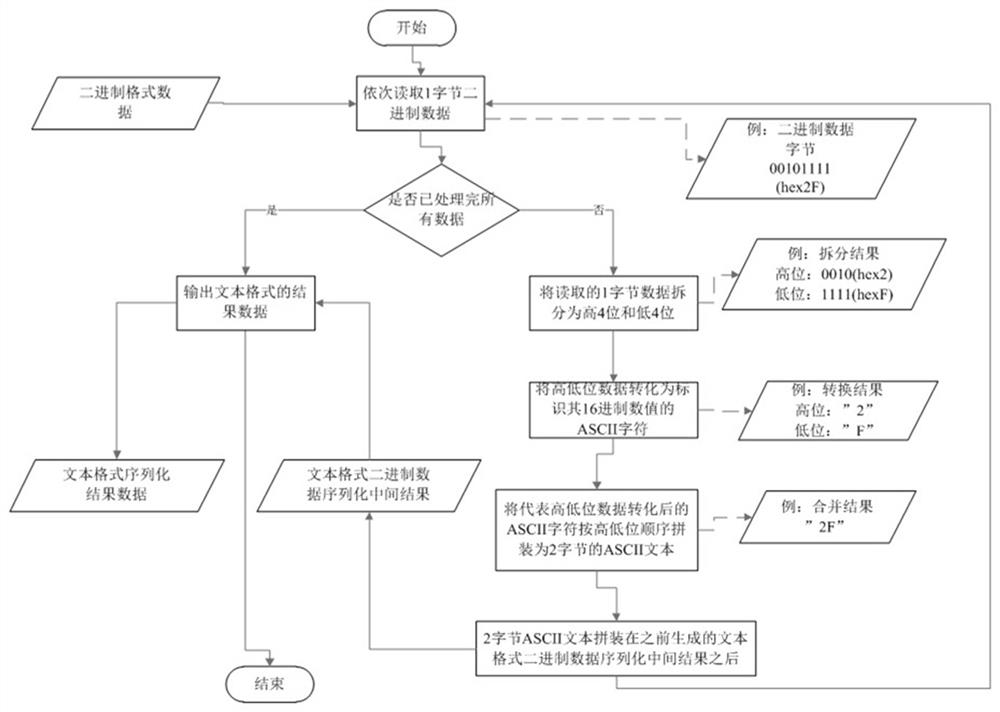
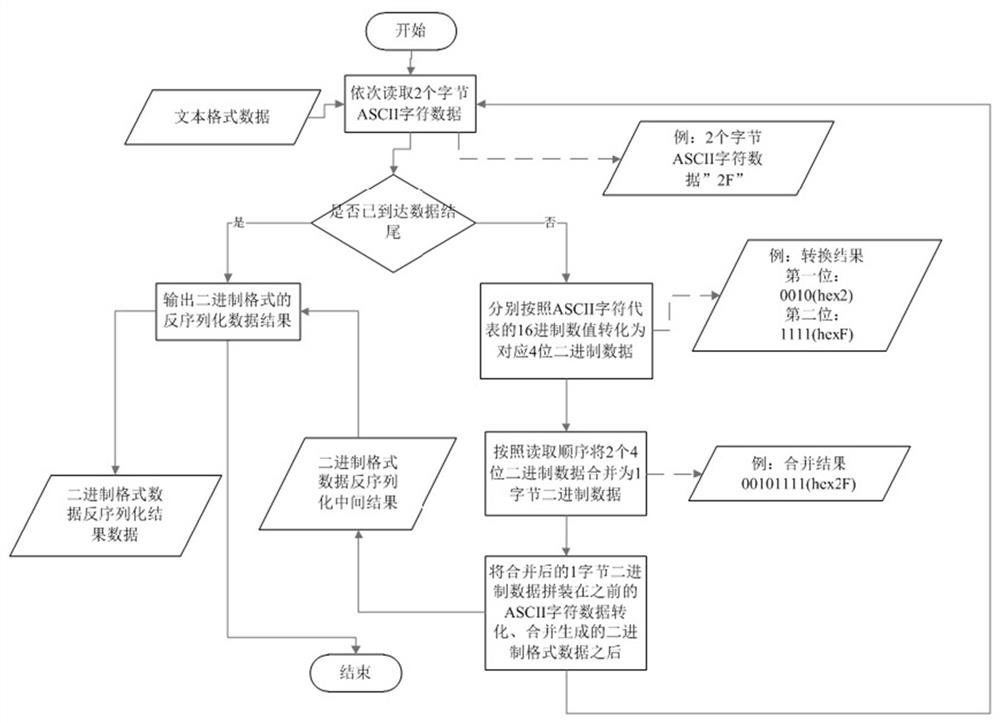
[0037] The present invention first reads the data of the binary format file on the disk through the external network side sending program. Subsequently, the sending program on the external network side serializes the binary format data into text format data, and encapsulates the serialized text format data into E language format data. After encryption and decryption, the internal network side receiving program receives the data and saves it as E language format data, and parse ou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com