Method and device for training event prediction model
A technology for predicting models and events, applied in computing models, neural learning methods, biological neural network models, etc., can solve problems such as limited evaluation accuracy and single evaluation methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
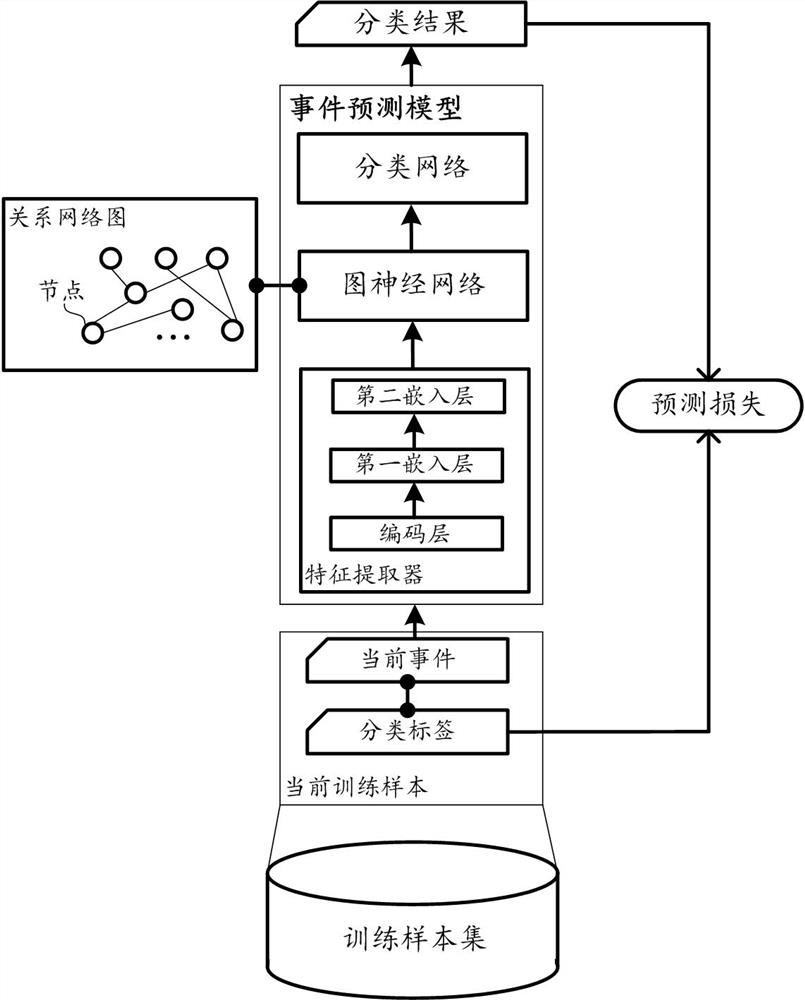
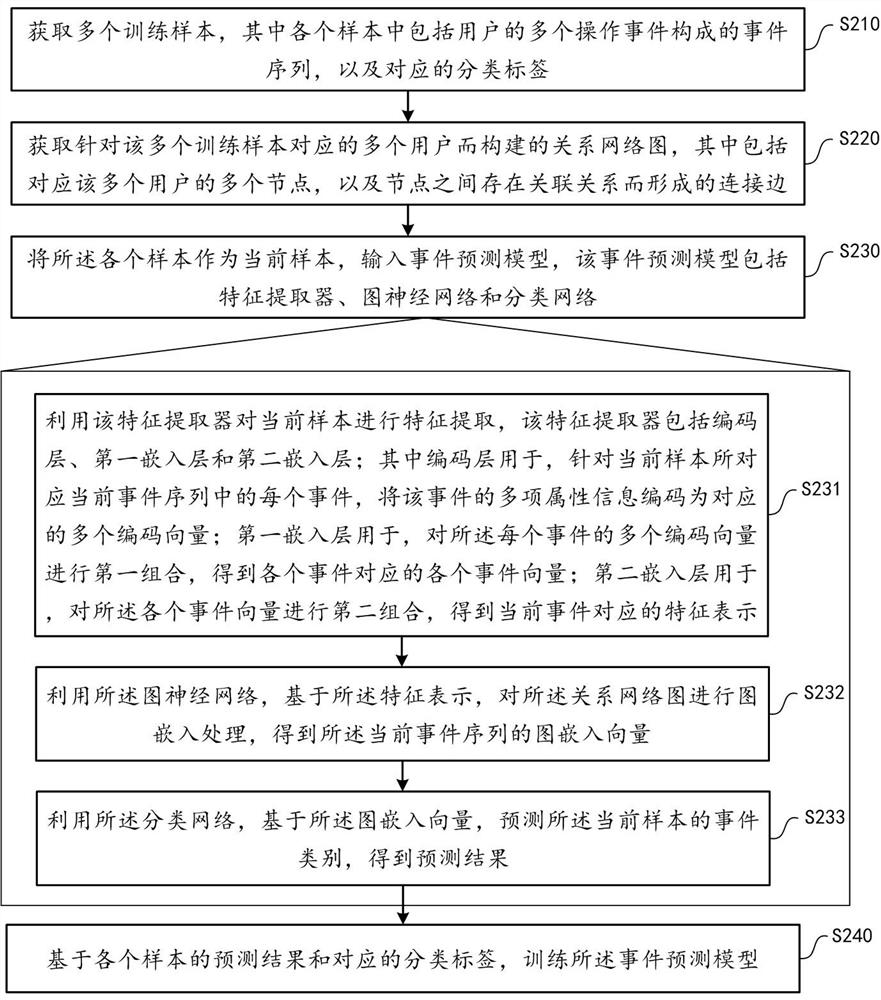
[0064] According to an implementation manner, the above-mentioned first combination further includes an N-order inter-vector combination operation involving multiplication of N coded vectors, where N>=2.
[0065] It can be understood that the combination of feature vectors in conventional neural networks generally adopts a linear combination method. However, when an event contains multiple attribute information, sometimes the attribute information is not completely independent, but there is a certain dependency or correlation, and a simple linear combination is not enough to discover and process such a correlation. Therefore, in one embodiment, referring to the framework of the FM factorization machine, a high-order inter-vector combination operation is introduced in the first embedding layer.
[0066] The N-order inter-vector combination operation involves the multiplication operation of N coded vectors, so that the association relationship between the N coded vectors can be ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com