Distributed unmanned aerial vehicle cluster network security communication implementation method
A technology of secure communication and cluster network, which is applied in the field of realizing secure communication of distributed drone cluster network, can solve problems such as drone intrusion and interference, inaccurate information transmission, and inability to complete operational tasks, etc., to achieve high mobility , small information flow, prevent the effect of change
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
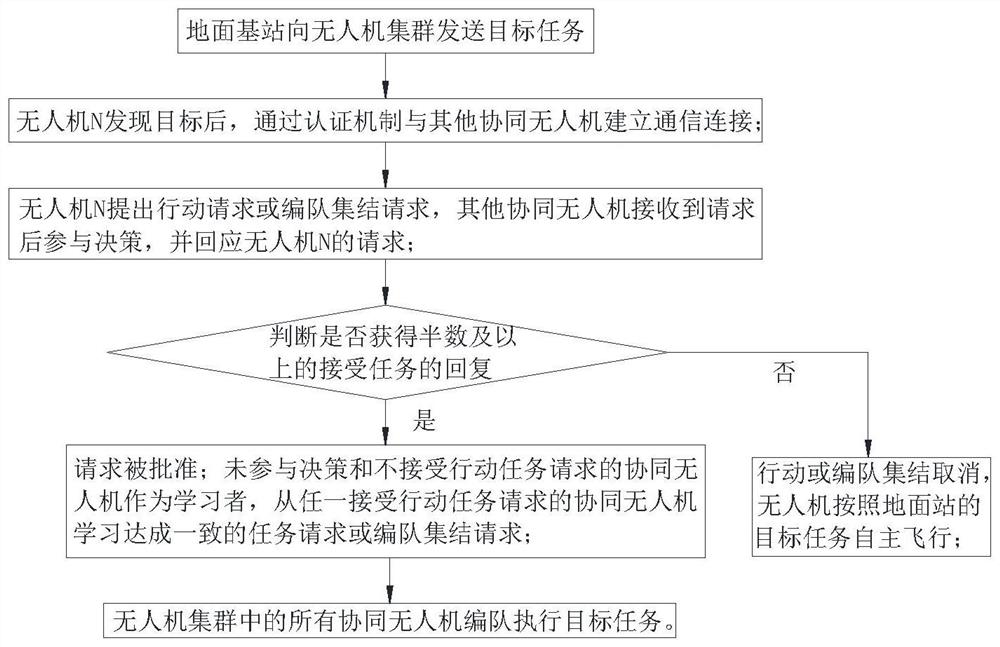
[0019] see figure 1 , a method for implementing secure communication in a distributed UAV cluster network. The UAV cluster includes multiple cooperative UAVs that use their own sensors to perceive environmental information and make autonomous decisions. The ground base station sends target tasks to the UAV cluster.
[0020] Each collaborative UAV is equipped with an authentication server, and the authentication server has a built-in user name database of all UAVs in the UAV cluster, which is used to issue identity authentication to the other party’s authentication server during the information transfer process between two UAVs request; the specific authentication mechanism includes the following steps:
[0021] B1. Before the UAV N needs to send information to the UAV M, the UAV N sends an authentication request to the UAV M for identity authentication, and the authentication server of the UAV M queries the UAV N from the user name database. Whether the user is a legal user, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com